Practice Free MS-102 Exam Online Questions
You plan to use Azure Sentinel and Microsoft Cloud App Security. You need to connect Cloud App Security to Azure Sentinel.
What should you do in the Cloud App Security admin center?
- A . From Automatic log upload, add a log collector.
- B . From Automatic log upload, add a data source.
- C . From Connected apps, add an app connector.
- D . From Security extension, add a SIEM agent.
You have a Microsoft 365 tenant that is signed up for Microsoft Store for Business and contains a user named User1.
You need to ensure that User1 can perform the following tasks in Microsoft Store for Business:
• Assign licenses to users.
• Procure apps from Microsoft Store.
• Manage private store availability for all items.
The solution must use the principle of least privilege.
Which Microsoft Store for Business role should you assign to User1?
- A . Basic Purchaser
- B . Device Guard signer
- C . Admin
- D . Purchaser
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-store/microsoft-store-for-business-overview
You have a Microsoft 365 subscription. You have a user named User1.
You need to ensure that Used can place a hold on all mailbox content.
What permission should you assign to User1?
- A . the Information Protection administrator ide from the Azure Active Directory admin center.
- B . the eDiscovery Manager tote from the Microsoft 365 compliance center.
- C . the Compliance Management role from the Exchange admin center.
- D . the User management administrator role from the Microsoft 365 admin center.
You purchase a new computer that has Windows 10, version 2004 preinstalled.
You need to ensure that the computer is up-to-date. The solution must minimize the number of updates installed.
What should you do on the computer?
- A . Install all the feature updates released since version 2004 and all the quality updates released since version 2004 only.
- B . install the West feature update and the latest quality update only.
- C . install all the feature updates released since version 2004 and the latest quality update only.
- D . install the latest feature update and all the quality updates released since version 2004.
You have a Microsoft 365 E5 subscription.
From the Microsoft 365 Defender portal, you plan to export a detailed report of compromised users.
What is the longest time range that can be included in the report?
- A . 1 day
- B . 7 days
- C . 30 days
- D . 90 days
C
Explanation:
View email security reports in the Microsoft 365 Defender portal
The aggregate view shows data for the last 90 days and the detail view shows data for the last 30 days
Reference: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/reports-email-security
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint site named site1.
You need to ensure that site1 meets the following requirements:
• Retains all data for 10 years
• Prevents the sharing of data outside the organization
Which two items should you create and apply to site1? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . a retention policy
- B . a sensitive info type
- C . a data loss prevention (DLP) policy
- D . a sensitivity label
- E . a retention label
- F . a retention label policy
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Endpoint Management admin center, you create a device configuration profile.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
You need to create a trusted location and a conditional access policy.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Endpoint Management admin center, you create a device configuration profile.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
You need to create a trusted location and a conditional access policy.
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
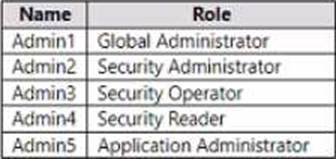
You ate implementing Microsoft Defender for Endpoint
You need to enable role-based access control (RBAQ to restrict access to the Microsoft 365 Defender portal.
Which users can enable RBAC, and winch users will no longer have access to the Microsoft 365 Defender portal after RBAC is enabled? To answer, select the appropriate options in the answer area.
NOTE Each correct selection is worth one point.
Your company has a Microsoft 365 E5 subscription.
Users in the research department work with sensitive data.
You need to prevent the research department users from accessing potentially unsafe websites by using hyperlinks embedded in email messages and documents. Users in other departments must not be restricted.
What should you do?
- A . Create a data loss prevention (DLP) policy that has a Content is shared condition.
- B . Modify the safe links policy Global settings.
- C . Create a data loss prevention (DLP) policy that has a Content contains condition.
- D . Create a new safe links policy.
D
Explanation:
Use the Microsoft 365 Defender portal to create Safe Links policies
In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Email & Collaboration > Policies & Rules > Threat policies > Safe Links in the Policies section. Or, to go directly to the Safe Links page, use https://security.microsoft.com/safelinksv2.
