Practice Free JN0-232 Exam Online Questions
Click the Exhibit button.
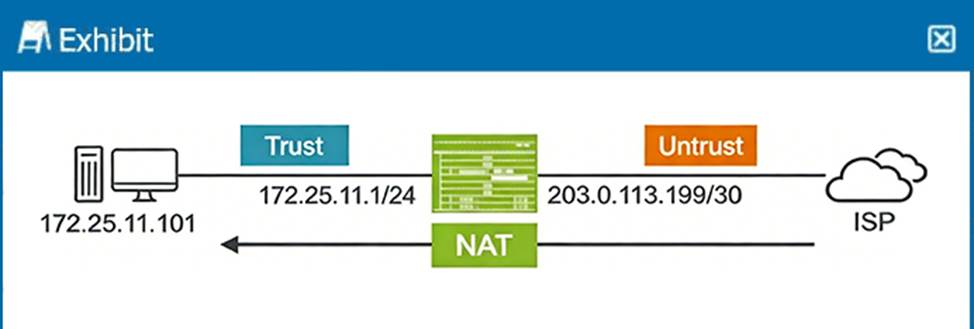
You must ensure that sessions can only be established from the external device.
Referring to the exhibit, which type of NAT is being performed?
- A . destination NAT only
- B . source NAT only
- C . static PAT only
- D . static NAT and source NAT
A
Explanation:
From the exhibit:
The internal host (172.25.11.101) is located in the Trust zone.
The external address (203.0.113.199/30) is used for communication with the ISP.
The requirement is that sessions can only be initiated from the external device (the ISP or untrust side) toward the internal host.
This requirement matches the behavior of Destination NAT:
Destination NAT only (Option A): Maps the external/public IP (203.0.113.199) to the internal/private IP (172.25.11.101). This allows inbound connections to be translated and sent to the internal host. The internal host cannot initiate outbound sessions, since the translation only applies to inbound traffic.
Source NAT only (Option B): Used for outbound sessions from internal private IPs to the Internet.
This does not meet the requirement.
Static PAT (Option C): Maps a single port of a public IP to a private IP/port. The exhibit does not indicate a port-based translation.
Static NAT and source NAT (Option D): Would provide bidirectional communication, allowing sessions to be initiated in both directions. This contradicts the requirement.
Correct NAT Type: Destination NAT only
Reference: Juniper Networks CNAT Types (Source NAT, Destination NAT, Static NAT), Junos OS Security Fundamentals.
Which two criteria would be used for matching in security policies? (Choose two.)
- A . MAC address
- B . source address
- C . interface name
- D . applications
B D
Explanation:
Security policies in Junos OS match traffic based on specific criteria:
Source and destination addresses (Option B).
Application (Option D), which may be defined as services (e.g., tcp/80) or recognized through AppID.
Other options:
MAC addresses (Option A) are not used in policy matching; policies operate at Layer 3/4.
Interface name (Option C) is used in firewall filters, not in security policy definitions. Correct Criteria: Source address and Applications
Reference: Juniper Networks CSecurity Policy Match Conditions, Junos OS Security Fundamentals.
You must monitor security policies on SRX Series devices dispersed throughout locations in your organization using a ‘single pane of glass’ cloud-based solution.
Which solution satisfies the requirement?
- A . Juniper Sky Enterprise
- B . J-Web
- C . Junos Secure Connect
- D . Junos Space
D
Explanation:
Junos Space is a management platform that provides a single pane of glass view of SRX Series devices dispersed throughout locations in your organization. It provides visibility into the security policies of the devices, allowing you to quickly identify and respond to security threats. Additionally, it provides the ability to manage multiple devices remotely and in real-time, enabling you to quickly deploy and update security policies on all devices. For more information, please refer to the Juniper Networks Junos Space Network Director User Guide, which can be found on Juniper’s website.
Which two statements are correct about the default behavior on SRX Series devices? (Choose two.)
- A . The SRX Series device is in flow mode.
- B . The SRX Series device supports stateless firewalls filters.
- C . The SRX Series device is in packet mode.
- D . The SRX Series device does not support stateless firewall filters.
You are troubleshooting first path traffic not passing through an SRX Series Firewall. You have determined that the traffic is ingressing and egressing the correct interfaces using a route lookup.
In this scenario, what is the next step in troubleshooting why the device may be dropping the traffic?
- A . Verify that the interfaces are in the correct security zones.
- B . Verify the routing protocol being used.
- C . Verify that source NAT is occurring.
- D . Verify that the correct ALG is being used.
A
Explanation:
After confirming correct routing:
The next step is to verify security zone assignments (Option A). If interfaces are not correctly assigned to zones, traffic will not be evaluated against proper inter-zone or intra-zone security policies, causing drops.
Option B: The routing protocol is irrelevant once the correct route lookup is confirmed.
Option C: NAT is checked later in the flow, not the immediate next step after routing.
Option D: ALG is only needed for specific applications (FTP, SIP), not general troubleshooting.
Correct Next Step: Verify that interfaces are assigned to the correct security zones.
Reference: Juniper Networks CPacket Flow and Zone-Based Policy Evaluation, Junos OS Security Fundamentals.
Which two statements are correct about security zones and functional zones? (Choose two.)
- A . Traffic entering an interface in a functional zone cannot exit any other transit interface.
- B . Traffic entering transit interfaces can exit an interface in a functional zone.
- C . Traffic entering an interface in a functional zone can exit any other transit interface.
- D . Traffic entering transit interfaces cannot exit an interface in a functional zone.
A D
Explanation:
Functional zones (e.g., junos-host, management, null) are not used for forwarding transit traffic. They are used to manage traffic destined to or from the SRX device itself.
Option A: Correct. If traffic enters through a functional zone interface, it is meant for the SRX, not for transit, so it cannot exit another interface.
Option D: Correct. Transit interfaces handle forwarding traffic, but they cannot send that traffic out through a functional zone interface.
Option B and C: Incorrect, because functional zones are strictly control-plane, not transit forwarding zones.
Correct Statements: A and D
Reference: Juniper Networks CSecurity Zones vs. Functional Zones, Junos OS Security Fundamentals.
When traffic enters an interface, which two results does a route lookup determine? (Choose two.)
- A . ingress interface
- B . egress interface
- C . DNS name
- D . egress security zone
B D
Explanation:
When a packet enters an SRX interface, a route lookup is performed:
It determines the egress interface (Option B) by checking the destination IP against the routing table.
Once the egress interface is known, its associated egress security zone (Option D) is also determined.
The ingress interface (Option A) is already known when the packet arrives, so the route lookup does not determine it.
DNS name (Option C): DNS is unrelated to routing lookups.
Correct Results: egress interface, egress security zone
Reference: Juniper Networks CPacket Flow and Route Lookup, Junos OS Security Fundamentals.
Which two security policies are installed by default on SRX 300 Series Firewalls? (Choose two.)
- A . a security policy to allow all traffic from the untrust zone to the trust zone
- B . a security policy to allow all traffic from the trust zone to the untrust zone
- C . a security policy to allow all traffic from the management zone to the trust zone
- D . a security policy to allow all traffic from the trust zone to the trust zone
B D
Explanation:
By default, SRX 300 Series Firewalls come with predefined security policies:
Trust-to-Untrust (Option B): A default policy exists to permit all traffic from the trust zone to the untrust zone.
Trust-to-Trust (Option D): Intra-zone traffic is permitted by default; hence, a trust-to-trust policy is installed automatically.
Untrust-to-Trust (Option A): Not allowed by default, since external traffic must be explicitly permitted by an administrator.
Management-to-Trust (Option C): No such default policy exists.
Correct Policies: Trust-to-Untrust and Trust-to-Trust
Reference: Juniper Networks CDefault Security Policies and Intra-zone Rules, Junos OS Security Fundamentals.
What is the purpose of a feature profile in a UTM configuration?
- A . It applies a UTM feature to a security policy.
- B . It applies a UTM feature to protocol traffic.
- C . It defines the operation of a specific UTM feature.
- D . It defines an object list.
C
Explanation:
A feature profile in a UTM (Unified Threat Management) configuration defines how a specific UTM feature should operate. Examples include:
An antivirus feature profile that specifies the type of scanning to perform (streaming or full file-based).
A web filtering feature profile that defines filtering methods, categories, and actions.
An antispam profile that defines how spam detection and actions are performed.
Feature profiles do not directly apply to traffic or policies. Instead, they are referenced inside a UTM policy, and then that policy is applied to a security policy.
Therefore, a feature profile’s purpose is to define the operation of a specific UTM feature.
Reference: Juniper Networks CJunos OS Security Fundamentals, UTM Profiles and Policies.
You are assigned a project to configure SRX Series devices to allow connections to your webservers. The webservers have a private IP address, and the packets must use NAT to be accessible from the Internet. The webservers must use the same address for both connections from the Internet and communication with update servers.
Which NAT type must be used to complete this project?
- A . source NAT
- B . destination NAT
- C . static NAT
- D . hairpin NAT
C
Explanation:
Only static NAT with pool ensures both traffic initiated from inside and outside networks use the same IP address.
