Practice Free HPE7-A01 Exam Online Questions
A company deployed Dynamic Segmentation with their CX switches and Gateways After performing a security audit on their network, they discovered that the tunnels built between the CX switch and the Aruba Gateway are not encrypted. The company is concerned that bad actors could try to insert spoofed messages on the Gateway to disrupt communications or obtain information about the network.
Which action must the administrator perform to address this situation?
- A . Enable Secure Mode Enhanced
- B . Enable Enhanced security
- C . Enable Enhanced PAPI security
- D . Enable GRE security
What is used to retrieve data stored in a Management Information Base (MIS)?
- A . SNMPv3
- B . DSCP
- C . TLV
- D . CDP
A
Explanation:
SNMPv3.
SNMPv3 is a protocol that is used to retrieve data stored in a Management Information Base (MIB), which is a database of managed objects in a network. SNMPv3 provides security and access control features that are not available in earlier versions of SNMP. SNMPv3 can also use encryption to protect the data from unauthorized access or modification.
According to the Aruba Certified Professional – Campus Access document1, one of the skills that this certification validates is:
Implement and Analyze the output from common network monitoring tools Configure Port Mirroring to collect PCAPs
Configure NAE agents 9.4
Configure UXI sensors for internal and external tests
Describe how API scan be used to configure, manage, monitor, and troubleshoot your network The document also mentions that the candidate should have a distinguished understanding of different protocols across vendors, which implies that they should be familiar with SNMPv3 and how it can be used to access MIB data.
With the Aruba CX 6100 48G switch with uplinks of 1/1/47 and 1/1/48.
H ow do you automate the process of resuming the port operational state once a loop on a client port is cleared?
- A . Configure int 1/1/1-1/1/52 loop-protect disable timer.
- B . Configure global loop-protect disable timer.
- C . Configure int 1/1/1-1/1/46 loop-protect re-enable-timer.
- D . Configure global loop-protect re-enable-timer.
D
Explanation:
In the Aruba CX 6100 48G switch, to automate the resumption of the operational state of a client port once a loop is cleared, the loop protection re-enable timer should be used. This timer setting allows for the automatic re-enabling of the port after a specified time once it has been automatically disabled due to the detection of a loop.
By configuring the global loop-protect re-enable timer, the process of automatically resuming the port’s operation can be automated across the entire switch. When any port detects a loop and then the loop is cleared, the port will automatically return to operational status after the set time.
With the Aruba CX switch configuration, what is the Active Gateway feature that is used for and is unique to VSX configuration?
- A . VRRP and Active gateway are mutually exclusive on a VLAN
- B . VRID is set automatically as SVI vlan id
- C . VRIDs need to be non-overlapping with VRRP
- D . VRRP and Active Gateway can be configured on a single VLAN for interoperability
A
Explanation:
Active gateway is a first hop redundancy protocol that eliminates a single point of failure. The active gateway feature is used to increase the availability of the default gateway servicing hosts on the same subnet. An active gateway improves the reliability and performance of the host network by enabling a virtual router to act as the default gateway for that network. If you have enabled active gateway, VRRP is not required3. Active gateway is similar to VRRP in that routed traffic from the VSX node is sourced from the switch interface MAC and not the virtual MAC address (VMAC). Each active gateway sends a periodic broadcast hello packet to avoid VMAC aging on the access switches. The switch views the active gateway IP as a self IP address3. Active gateway is preferable over VRRP because with VRRP traffic is still pushed over the ISL link, resulting in latency in the network3. Therefore, VRRP and active gateway are mutually exclusive on a VLAN, and answer A is correct.
A new network design is being considered to minimize client latency in a high-density environment. The design needs to do this by eliminating contention overhead by dedicating subcamers to clients.
Which technology is the best match for this use case?
- A . OFDMA
- B . MU-MIMO
- C . QWMM
- D . Channel Bonding
A
Explanation:
OFDMA (Orthogonal Frequency Division Multiple Access) is a technology that can minimize client latency in a high-density environment by eliminating contention overhead by dedicating subcarriers to clients. OFDMA allows multiple clients to transmit simultaneously on different subcarriers within the same channel, reducing contention and increasing efficiency. MU-MIMO (Multi-User Multiple Input Multiple Output) is a technology that allows multiple clients to transmit simultaneously on different spatial streams within the same channel, but it does not eliminate contention overhead.
QWMM (Quality of Service Wireless Multimedia) is a technology that prioritizes traffic based on four access categories, but it does not eliminate contention overhead. Channel Bonding is a technology that combines two adjacent channels into one wider channel, increasing bandwidth but not eliminating contention overhead.
References:
https://www.arubanetworks.com/assets/ds/DS_AP510Series.pdf
https://www.arubanetworks.com/assets/wp/WP_WiFi6.pdf
Two AOS-CX switches are configured with VSX at the the Access-Aggregation layer where servers attach to them An SVI interface is configured for VLAN 10 and serves as the default gateway for VLAN 10. The ISL link between the switches fails, but the keepalive interface functions. Active gateway has been configured on the VSX switches.
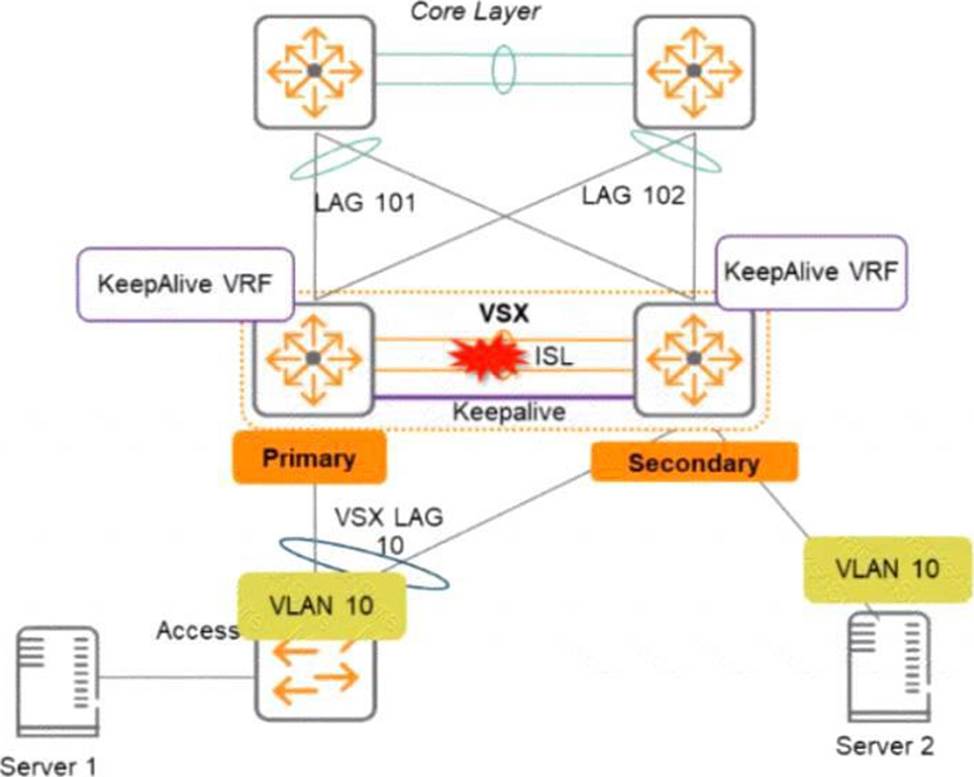
What is correct about access from the servers to the Core? (Select two.)
- A . Server 1 can access the core layer via the keepalrve link
- B . Server 2 can access the core layer via the keepalive link
- C . Server 2 cannot access the core layer.
- D . Server 1 can access the core layer via both uplinks
- E . Server 1 and Server 2 can communicate with each other via the core layer
- F . Server 1 can access the core layer on only one uplink
D E
Explanation:
These are the correct statements about access from the servers to the Core when the ISL link between the switches fails, but the keepalive interface functions. Server 1 can access the core layer via both uplinks because it is connected to VSX-A, which is still active for VLAN 10. Server 2 can also access the core layer via its uplink to VSX-B, which is still active for VLAN 10 because of Active Gateway feature. Server 1 and Server 2 can communicate with each other via the core layer because they are in the same VLAN and subnet, and their traffic can be routed through the core switches. The other statements are incorrect because they either describe scenarios that are not possible or not relevant to the question.
References: https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/bk01-
You are setting up a customer’s 15 headless loT devices that do not support 802.1X..
What should you use?
- A . Multiple Pre-Shared Keys (MPSK) Local
- B . Clearpass with WPA3-PSK
- C . Clearpass with WPA3-AES
- D . Multiple Pre-Shared Keys (MPSK) with WPA3-AES
A
Explanation:
MPSK Local is a feature that can be used to set up 15 headless IoT devices that do not support 802.1X authentication. MPSK Local allows the switch to automatically generate and assign unique pre-shared keys for devices based on their MAC addresses, without requiring any configuration on the devices or an external authentication server. The other options are incorrect because they either require 802.1X authentication, which is not supported by the IoT devices, or WPA3 encryption, which is not supported by Aruba CX switches.
References:
https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/bk01-ch05.html
https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/bk01-ch06.html
What is a primary benefit of BSS coloring?
- A . BSS color tags improve performance by allowing clients on the same channel to share airtime.
- B . BSS color tags are applied to client devices and can reduce the threshold for interference
- C . BSS color tags are applied to Wi-Fi channels and can reduce the threshold for interference
- D . BSS color tags improve security by identifying rogue APs and removing them from the network.
Your customer is having connectivity issues with a newly-deployed Microbranch group The access points in this group are online in Aruba Central, but no VPN tunnels are forming..
What is the most likely cause of this issue?
- A . There is a time difference between the AP and the gateways The gateways should have NTP added
- B . The SSL certificate on the gateway used to encrypt the connection has not been added to the APs trust list
- C . There may be a firewall blocking GRE tunneling between the AP and the gateway
- D . The gateway group is running in automatic cluster mode and should be in manual cluster mode
C
Explanation:
This is the most likely cause of the issue where the access points in a Microbranch group are online in Aruba Central, but no VPN tunnels are forming. A Microbranch group is a group that contains both APs and Gateways and allows them to form VPN tunnels for secure communication. The VPN tunnels use GRE (Generic Routing Encapsulation) as the encapsulation protocol and IPSec as the encryption protocol. If there is a firewall blocking GRE traffic between the AP and the gateway, the VPN tunnels cannot be established. The other options are incorrect because they either do not affect the VPN tunnel formation or do not apply to a Microbranch group.
References:
https://www.arubanetworks.com/techdocs/ArubaOS_86_Web_Help/Content/arubaos-solutions/gateways/microb
https://www.arubanetworks.com/assets/tg/TB_ArubaGateway.pdf
Your customer is interested in hearing more about how roles can help keep consistent policy enforcement in a distributed overlay fabric
How would you explain this concept to them”
- A . Group Based Policy ID is applied on egress VTEP after device authentication and policy is enforced on ingress VTEP
- B . Role-based policies are tied to IP addresses which have an advantage over IP-based policies and role names are sent between VTEPs
- C . Group Based Policy ID is applied on ingress VTEP after device authentication and policy is enforced on egress VTEP
- D . Role-based policies enhance User Based Tunneling across the campus network and the policy traffic is protected with iPsec
C
Explanation:
This is the correct explanation of how roles can help keep consistent policy enforcement in a distributed overlay fabric. Roles are used to assign group based policy IDs (GBPs) to devices after they authenticate with ClearPass or a local database. GBPs are then used to tag the traffic from the devices and send them to the ingress VTEP, which applies the GBP on the VXLAN header. The egress VTEP then enforces the policy based on the GBP and the destination device. The other options are incorrect because they either do not describe the correct sequence of events or do not use the correct terms.
References:
https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/bk01-ch03.html
https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/bk01-ch05.html
