Practice Free FCSS_SDW_AR-7.4 Exam Online Questions
What are three key routing principles of SD-WAN? (Choose three.)
- A . Directly connected routes have precedence over SD-WAN rules.
- B . Policy routes have precedence over SD-WAN rules.
- C . SD-WAN rules are skipped if the best route to the destination is a static route
- D . SD-WAN rules are skipped if the best route to the destination is not an SD-WAN member.
- E . SD-WAN members are skipped if they do not have a valid route to the destination.
Refer to the exhibits.
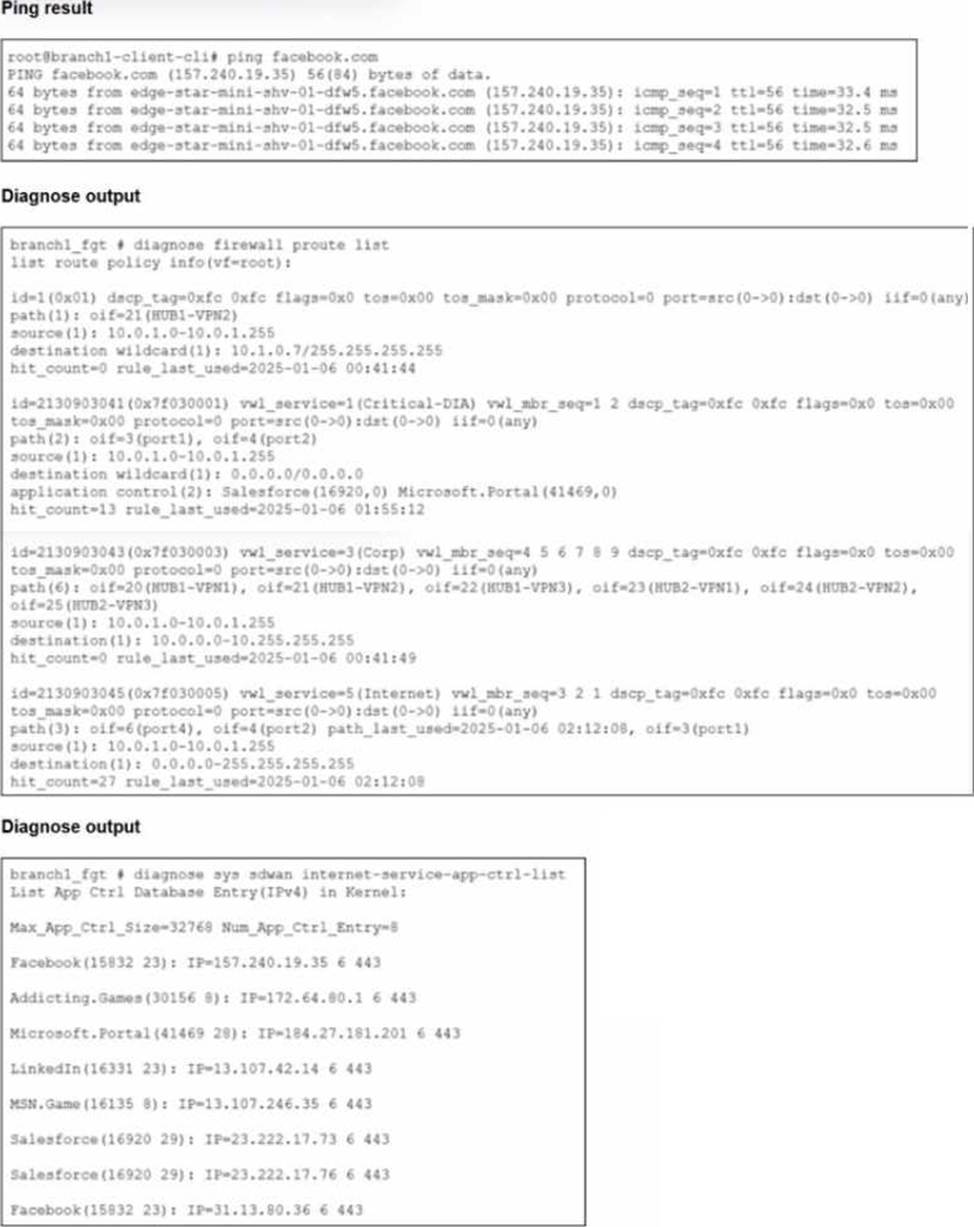
You connect to a device behind a branch FortiGate device and initiate a ping test. The device is part of the LAN subnet and its IP address is 10.0.1.101.
Based on the exhibits, which interface uses branch 1_fgt to steer the test traffic?
- A . port4
- B . HUB1-VPN1
- C . port1
- D . port2
Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule? (Choose two.)
- A . The session information output displays no SD-WAN service id.
- B . Traffic is load balanced using the algorithm set for the v4-ecmp-mode setting.
- C . The traffic is distributed, regardless of weight, through all available static routes.
- D . Traffic does not match any of the entries in the policy route table.
- E . FortiGate flags the session with may_dirty and vwl_def ault.
Refer to the exhibit.
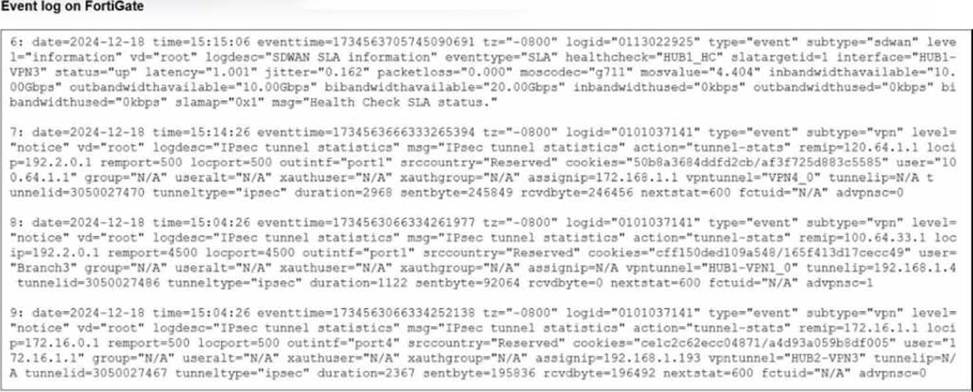
Refer to the exhibit that shows event logs on FortiGate.
Based on the output shown in the exhibit, what can you say about the tunnels on this device?
- A . The master tunnel HU82-VPN3 cannot accept ADVPN shortcuts.
- B . The device steers voice traffic through the VPN tunnel HUB1-VPN3.
- C . The VPN tunnel HUB1-VPN1_0 is a shortcut tunnel.
- D . There is one shortcut tunnel built from master tunnel VPN4.
Exhibit.
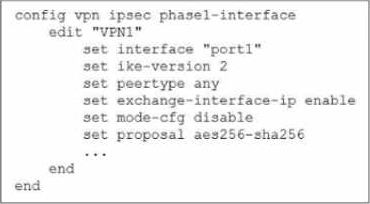
The administrator configured the IPsec tunnel VPN1 on a FortiGate device with the parameters shown in exhibit.
Based on the configuration, which three conclusions can you draw about the characteristics and requirements of the VPN tunnel? (Choose three.)
- A . The tunnel interface IP address on the spoke side is provided by the hub.
- B . The remote end can be a third-party IPsec device.
- C . The administrator must manually assign the tunnel interface IP address on the hub side
- D . The remote end must support IKEv2.
- E . This configuration allows user-defined overlay IP addresses.
Refer to the exhibit.
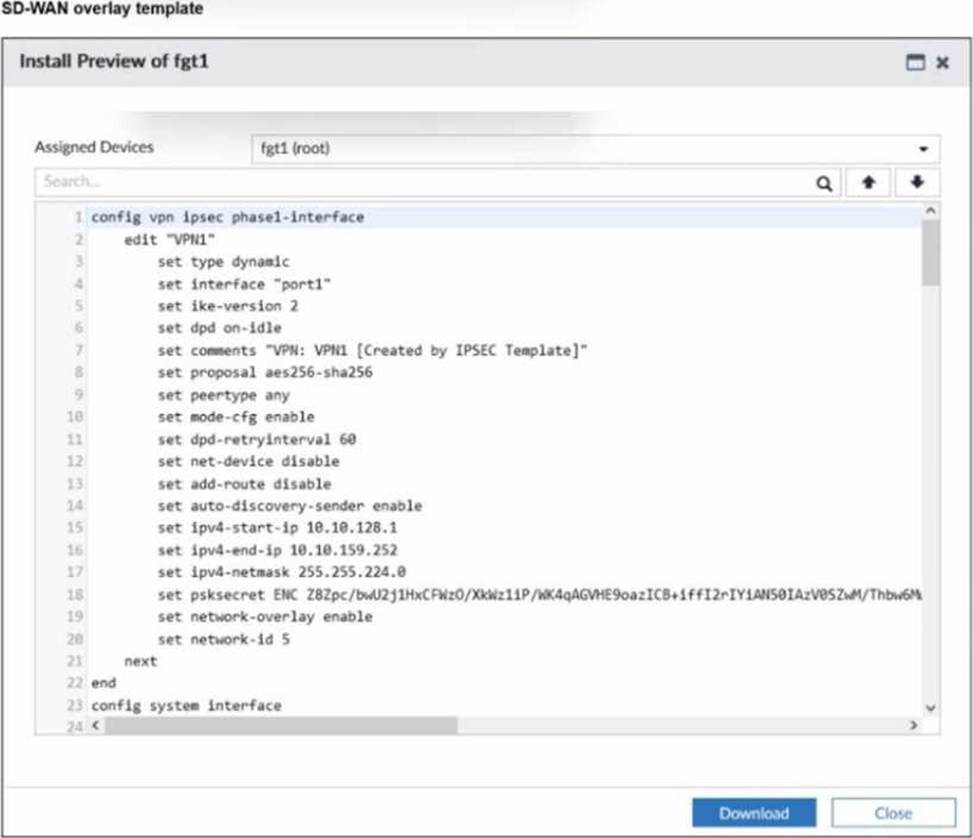
The administrator used the SD-WAN overlay template to prepare an IPsec tunnels configuration for a hub-and-spoke SD-WAN topology. The exhibit shows the FortiManager installation preview for one FortiGate device.
Based on the exhibit, which statement best describes the configuration applied to the FortiGate device?
- A . It is a spoke device that establishes dynamic IPsec tunnels to the hub. The local subnet range is 10.10.128.0/23.
- B . It is a hub device. It can send ADVPN shortcut offers.
- C . It is a hub device. It will automatically discover the spoke devices and add them to the SD-WAN topology.
- D . It is a spoke device that establishes dynamic IPsec tunnels to the hub It can send ADVPN shortcut requests.
Refer to the exhibit.
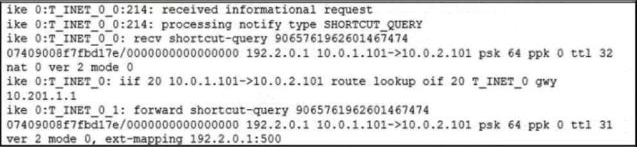
Which statement about the role of the ADVPN device in handling traffic is true?
- A . This is a spoke that has received a query from a remote hub and has forwarded the response to its hub.
- B . Two hubs, 10.0.1.101 and 10.0.2.101, are receiving and forwarding queries between each other.
- C . This is a hub that has received a query from a spoke and has forwarded it to another spoke.
- D . Two spokes, 192.2.0.1 and 10.0.2.101, forward their queries to their hubs.
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
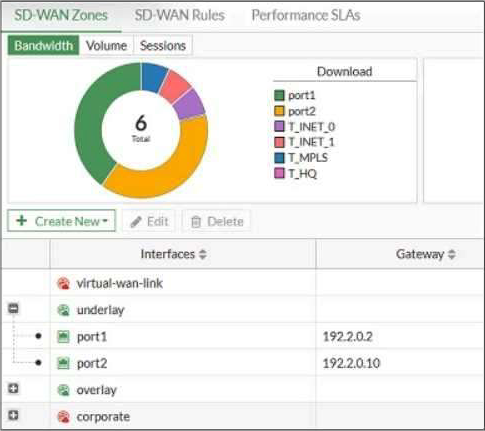
Based on the exhibit, which statement is true?
- A . You can delete the virtual-wan-link zone because it contains no member.
- B . The corporate zone contains no member.
- C . You can move port1 from the underlay zone to the overlay zone.
- D . The overlay zone contains four members.
C
Explanation:
Based on the exhibit, the "corporate" zone contains no member (B). In the FortiGate GUI, zones without members do not display any interfaces listed under them, which is the case for the corporate zone in the exhibit.
Reference: This conclusion is based on standard Fortinet GUI interpretation and the operational logic of SD-WAN zones as per Fortinet’s guidelines and user interface standards.
Which two statements about the SD-WAN zone configuration are true? (Choose two.)
- A . The service-sla-tie-break setting enables you to configure preferred member selection based on the best route to the destination.
- B . You can delete the default zones.
- C . The default zones are virtual-wan-link and SASE.
- D . An SD-WAN member can belong to two or more zones.
Exhibit A shows the firewall policy and exhibit B shows the traffic shaping policy.
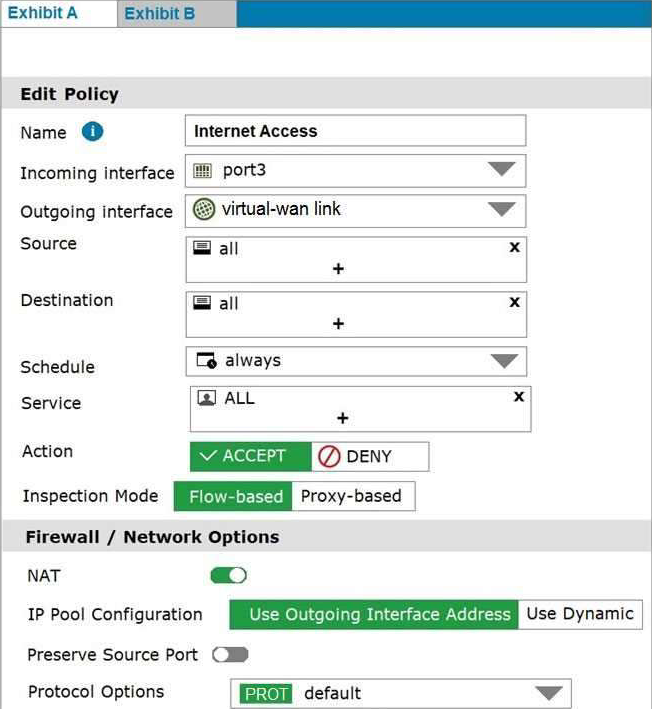
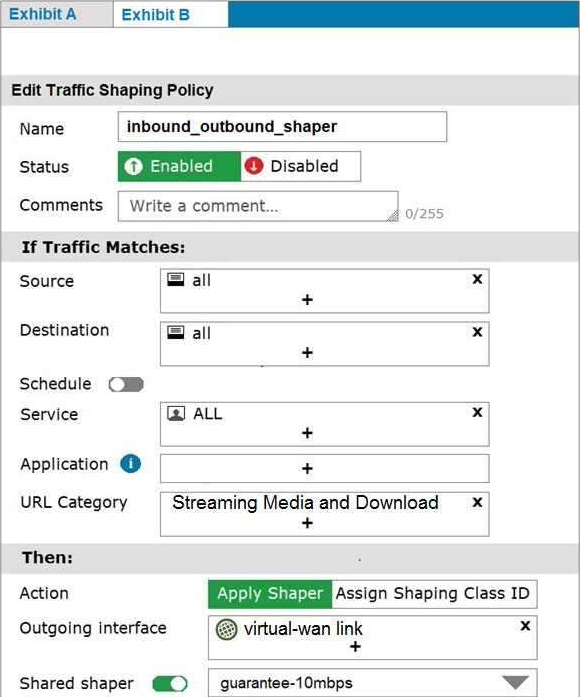
The traffic shaping policy is being applied to all outbound traffic; however, inbound traffic is not being evaluated by the shaping policy.
Based on the exhibits, what configuration change must be made in which policy so that traffic shaping can be applied to inbound traffic?
- A . Create a new firewall policy, and the select the SD-WAN zone as Incoming Interface.
- B . In the traffic shaping policy, select Assign Shaping Class ID as Action.
- C . In the firewall policy, select Proxy-based as Inspection Mode.
- D . In the traffic shaping policy, enable Reverse shaper, and then select the traffic shaper to use.
