Practice Free FCSS_SDW_AR-7.4 Exam Online Questions
Refer to the exhibit.
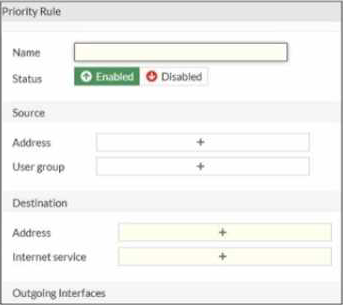
An administrator configures SD-WAN rules for a DIA setup using the FortiGate GUI. The page to configure the source and destination part of the rule looks as shown in the exhibit. The GUI page shows no option to configure an application as the destination of the SD-WAN rule Why?
- A . You cannot use applications as the destination when FortiGate is used for a DIA setup.
- B . FortiGate allows the configuration of applications as the destination of SD-WAN rules only on the CLI.
- C . You must enable the feature on the CLI.
- D . You must enable the feature first using the GUI menu System > Feature Visibility.
Refer to the exhibit.
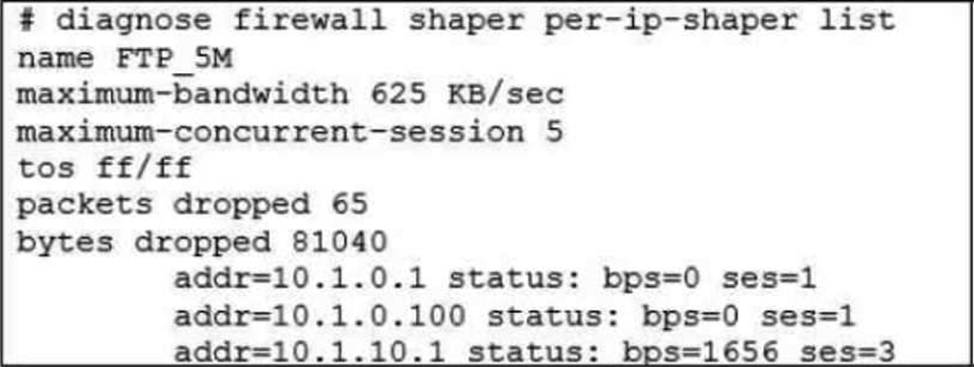
Which are two expected behaviors of the traffic that matches the traffic shaper? (Choose two.)
- A . The number of simultaneous connections among all source IP addresses cannot exceed five connections.
- B . The traffic shaper limits the combined bandwidth of all connections to a maximum of 5 MB/sec.
- C . The number of simultaneous connections allowed for each source IP address cannot exceed five connections.
- D . The traffic shaper limits the bandwidth of each source IP address to a maximum of 625 KB/sec.
Refer to the exhibit.
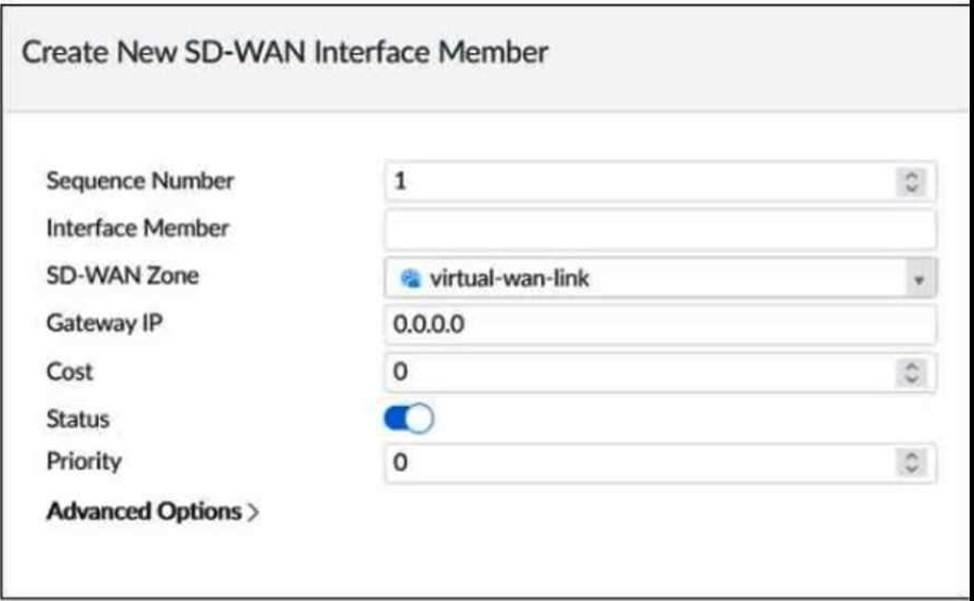
Which two SD-WAN template member settings support the use of FortiManager meta fields? (Choose two.)
- A . Cost
- B . Interface member
- C . Priority
- D . Gateway IP
Which two settings can you configure to speed up routing convergence in BGP? (Choose two.)
- A . update-source
- B . set-route-tag
- C . holdtime-timer
- D . link-down-failover
Refer to the exhibit, which shows the IPsec phase 1 configuration of a spoke.
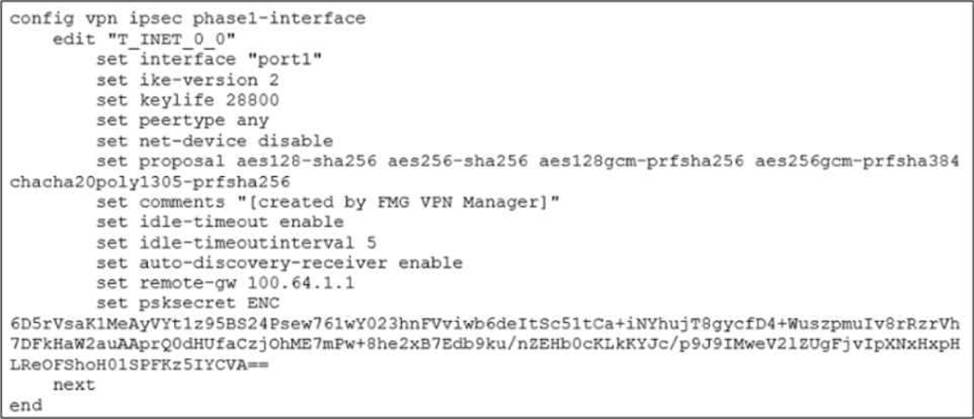
What must you configure on the IPsec phase 1 configuration for ADVPN to work with SD-WAN?
- A . You must set ike-version to 1.
- B . You must enable net-device.
- C . You must enable auto-discovery-sender.
- D . You must disable idle-timeout.
What is a benefit of using application steering in SD-WAN?
- A . The traffic always skips the regular policy routes.
- B . You steer traffic based on the detected application.
- C . You do not need to enable SSL inspection.
- D . You do not need to configure firewall policies that accept the SD-WAN traffic.
What are two common use cases for remote internet access (RIA)? (Choose two.)
- A . Provide direct internet access on spokes
- B . Provide internet access through the hub
- C . Centralize security inspection on the hub
- D . Provide thorough inspection on spokes
BC
Explanation:
B. Provide internet access through the hub: This involves routing branch or remote office internet traffic through a central hub, ensuring consistent security policies and possibly better management of network resources.
C. Centralize security inspection on the hub: With this approach, all internet-bound traffic from various spokes is inspected at the hub, leveraging centralized security mechanisms for thorough inspection and policy enforcement.
Which diagnostic command can you use to show the member utilization statistics measured by performance SLAs for the last 10 minutes?
- A . diagnose sys sdwan sla-log
- B . diagnose ays sdwan health-check
- C . diagnose sys sdwan intf-sla-log
- D . diagnose sys sdwan log
Exhibit.
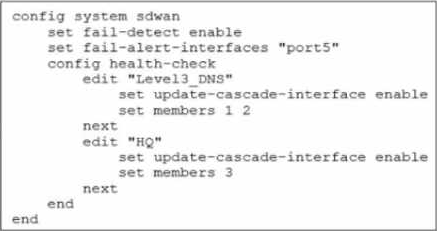
Which action will FortiGate take if it detects SD-WAN members as dead?
- A . FortiGate bounces port5 after it detects all SD-WAN members as dead.
- B . FortiGate fails over to the secondary device after it detects port5 as dead.
- C . FortiGate sends alert messages through poft5 when it detects all SD-WAN members as dead
- D . FortiGate brings down port5 after it detects all SD-WAN members as dead.
What is the route-tag setting in an SD-WAN rule used for?
- A . To indicate the routes for health check probes.
- B . To indicate the destination of a rule based on learned BGP prefixes.
- C . To indicate the routes that can be used for routing SD-WAN traffic.
- D . To indicate the members that can be used to route SD-WAN traffic.
B
Explanation:
"Configure SD-WAN *rules* to steer traffic to members only if routes have a specific route-tag." Agree with Cyril – although A says the largely same thing as D, route-tag specifically get used by the SD-WAN rule to determine next-hop (i.e., destination). SG p 142 shows "how an administrator can use [route-]tags in SD-WAN rules."
