Practice Free FCSS_SASE_AD-25 Exam Online Questions
How does analyzing FortiSASE logs help in compliance with regulatory standards?
- A . By ensuring all recreational internet use is logged
- B . By documenting all user login times and durations
- C . By providing evidence of proactive threat detection and response
- D . By tracking the number of emails sent per day
What is the role of Firewall as a Service (FWaaS) in FortiSASE architecture?
- A . To monitor and log all user activities
- B . To perform content inspection and enforce security policies
- C . To handle DNS queries and responses
- D . To encrypt traffic between endpoints
Refer to the exhibit.
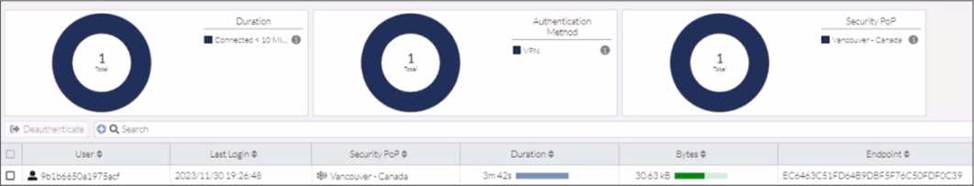
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters.
Which configuration change must the administrator make to get proper user information?
- A . Turn off log anonymization on FortiSASE.
- B . Add more endpoint licenses on FortiSASE.
- C . Configure the username using FortiSASE naming convention.
- D . Change the deployment type from SWG to VPN.
A
Explanation:
In the user connection monitor, the random characters shown for the username indicate that log anonymization is enabled. Log anonymization is a feature that hides the actual user information in the logs for privacy and security reasons. To display proper user information, you need to disable log anonymization.
Log Anonymization:
When log anonymization is turned on, the actual usernames are replaced with random characters to protect user privacy.
This feature can be beneficial in certain environments but can cause issues when detailed user monitoring is required.
Disabling Log Anonymization:
Navigate to the FortiSASE settings.
Locate the log settings section.
Disable the log anonymization feature to ensure that actual usernames are displayed in the logs and user connection monitors.
Reference: FortiSASE 23.2 Documentation: Provides detailed steps on enabling and disabling log anonymization.
Fortinet Knowledge Base: Explains the impact of log anonymization on user monitoring and logging.
Which techniques should be implemented to optimize content inspection within security profiles?
(Choose Two)
- A . Regular updates to inspection algorithms
- B . Use of minimal data sets for testing
- C . Continuous monitoring of inspected content
- D . Application of AI-based analytics tools
When viewing the daily summary report generated by FortiSASE, the administrator notices that the report contains very little data.
What is a possible explanation for this almost empty report?
- A . Log allowed traffic is set to Security Events for all policies.
- B . There are no security profile groups applied to all policies.
- C . The web filter security profile is not set to Monitor.
- D . Digital experience monitoring is not configured.
A
Explanation:
The issue of an almost empty daily summary report in FortiSASE can often be traced back to how logging is configured within the system. Specifically, if "Log Allowed Traffic" is set to "Security Events" for all policies, it means that only security-related events (such as threats or anomalies) are being logged, while normal, allowed traffic is not being recorded. Since most traffic in a typical network environment is allowed, this configuration would result in very little data being captured and subsequently reported in the daily summary.
Here’s a breakdown of why the other options are less likely to be the cause:
B. There are no security profile groups applied to all policies: While applying security profiles is important for comprehensive protection, their absence does not directly affect the volume of data in reports unless specific logging settings are also misconfigured.
C. The web filter security profile is not set to Monitor: This option pertains specifically to web filtering activities. Even if web filtering is not set to monitor mode, other types of traffic and logs should still populate the report.
D. Digital experience monitoring is not configured: Digital Experience Monitoring (DEM) focuses on user experience metrics rather than general traffic logging. Its absence would not lead to an almost empty report.
To resolve this issue, administrators should review the logging settings across all policies and ensure that "Log Allowed Traffic" is appropriately configured to capture the necessary data for reporting purposes.
Reference: Fortinet FCSS FortiSASE Documentation – Reporting and Logging Best Practices FortiSASE Administration Guide – Configuring Logging Settings
Which component of FortiSASE is essential for real-time malware protection in hybrid networks?
- A . Firewall as a Service (FWaaS)
- B . Cloud Access Security Broker (CASB)
- C . Zero Trust Network Access (ZTNA)
- D . Advanced Threat Protection (ATP)
For a SASE deployment, what is a crucial step when configuring security checks for regulatory compliance?
- A . Periodic rollback of security updates
- B . Continuous monitoring and automatic updates of compliance rules
- C . Annual reviews of compliance status
- D . Manual verification by external auditors
What aspects should be considered when configuring logging settings in FortiSASE? (Select all that apply)
- A . Log rotation frequency
- B . Error and event logs
- C . Debug level logs for everyday operations
- D . Privacy settings for sensitive information
Which feature of FortiSASE helps in maintaining consistent security policies across different network environments?
- A . Centralized management interface
- B . Dynamic routing protocols
- C . Role-based access control
- D . Secure Web Gateway (SWG)
What information can be gleaned from a detailed analysis of login attempts logged by FortiSASE to detect potential security threats?
- A . Patterns indicating brute force attacks
- B . Employee login schedules
- C . Frequency of password resets
- D . Duration of user sessions
