Practice Free FCSS_SASE_AD-25 Exam Online Questions
Refer to the exhibits.
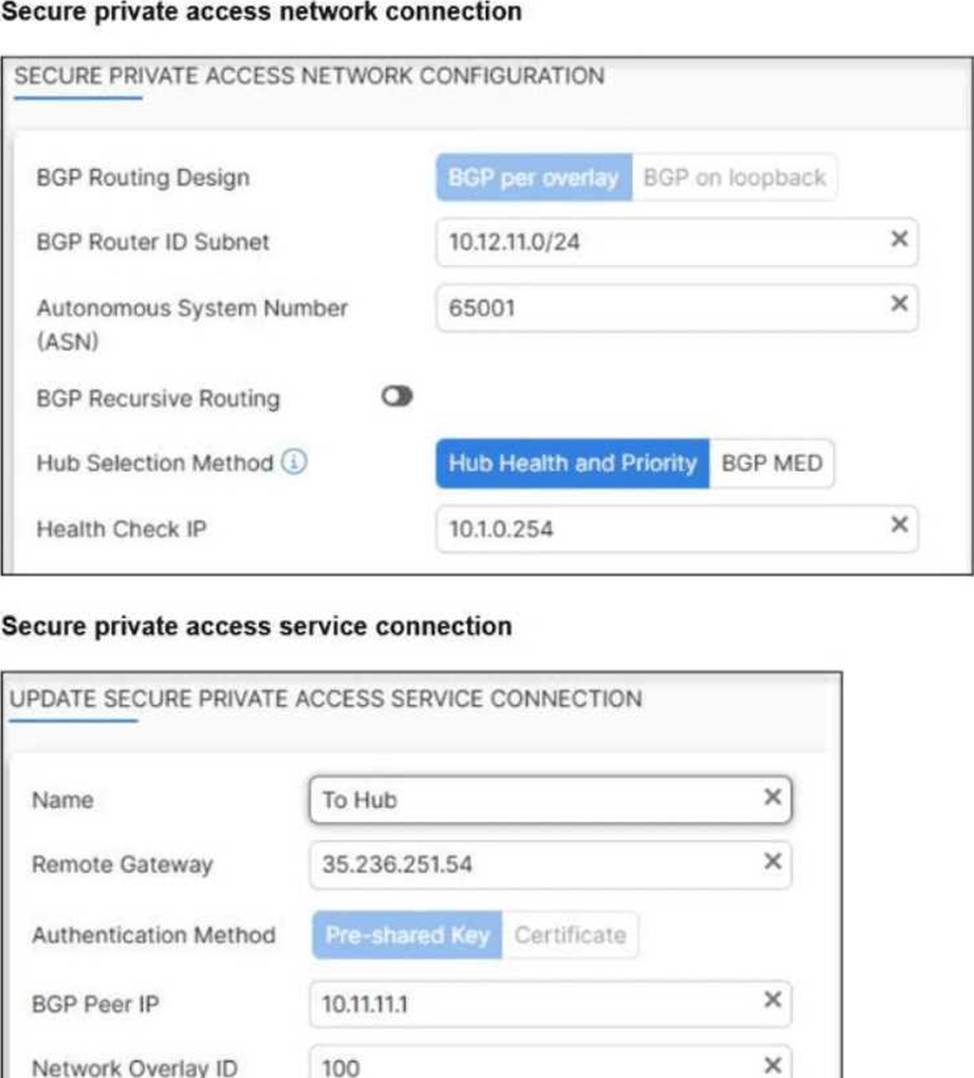
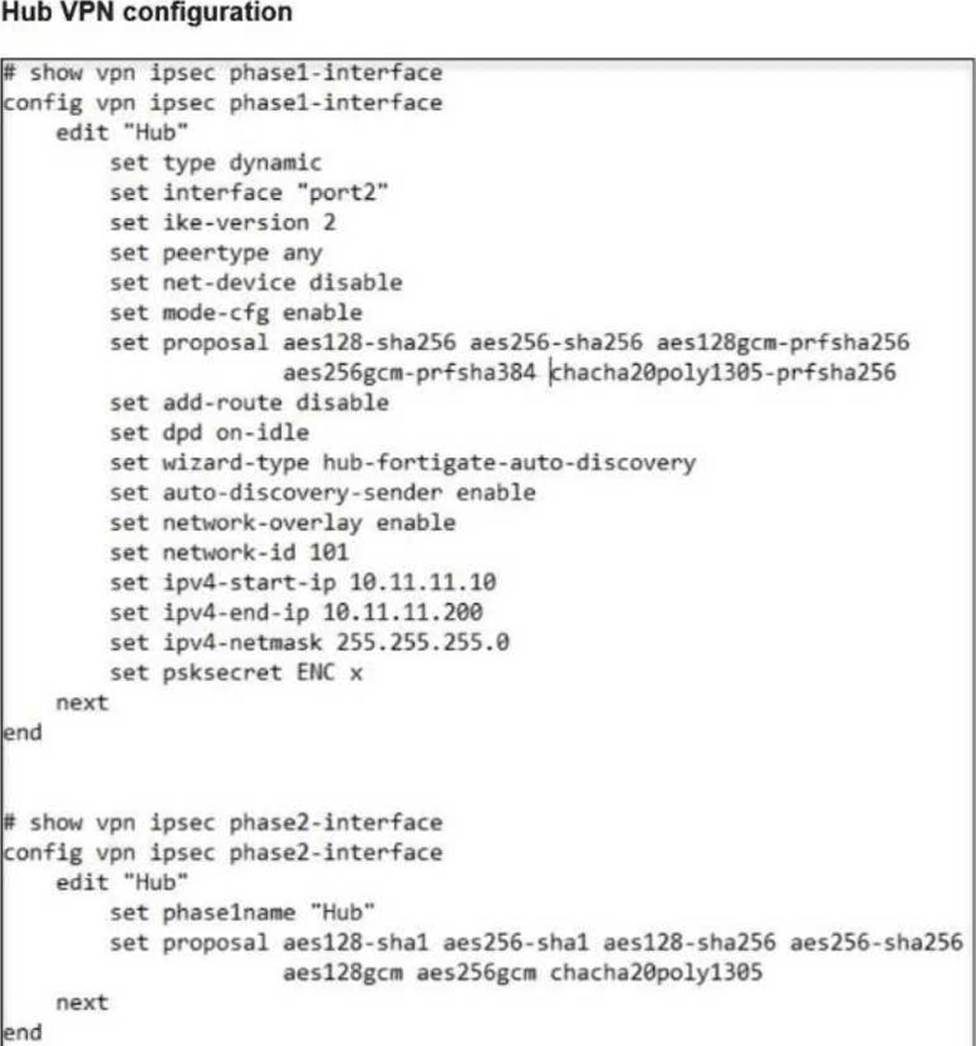
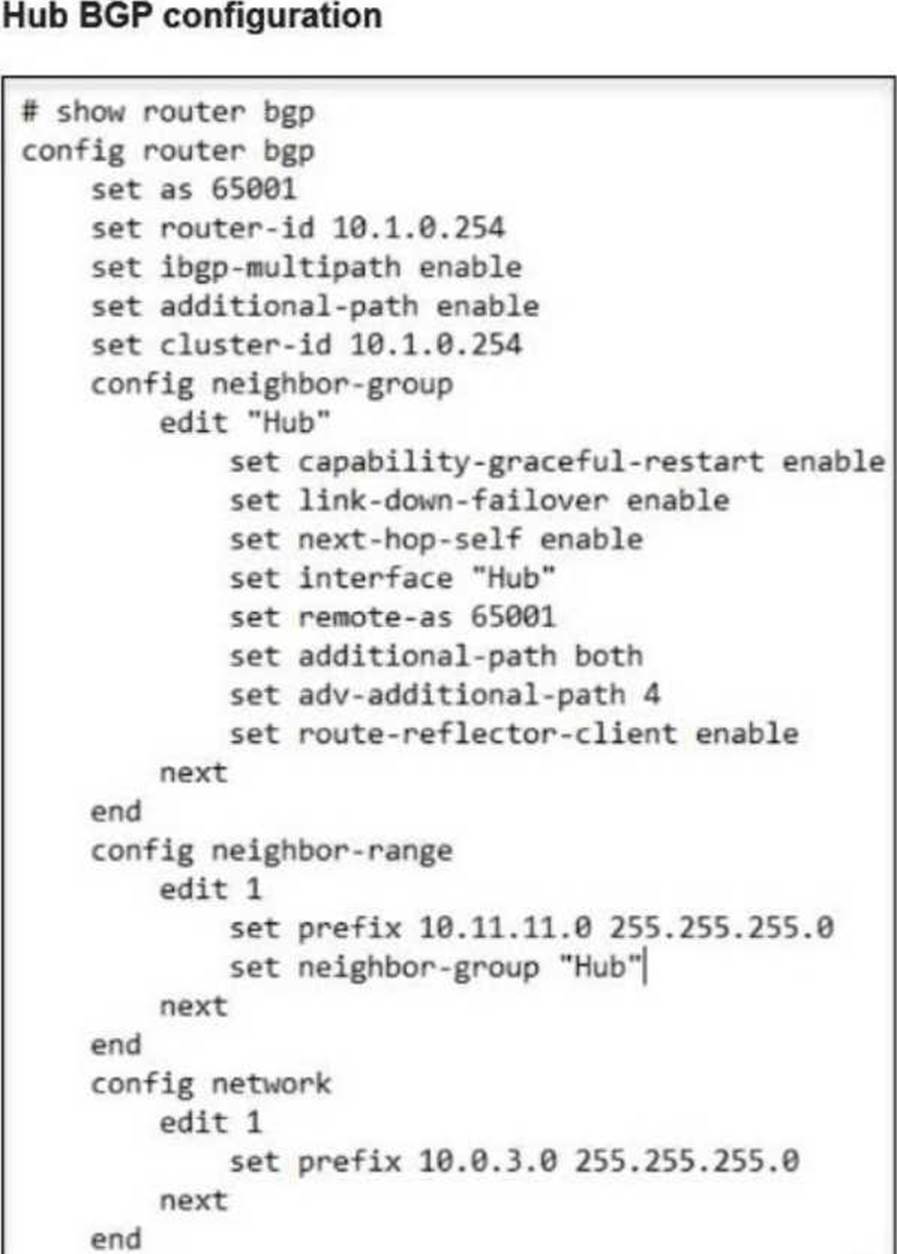
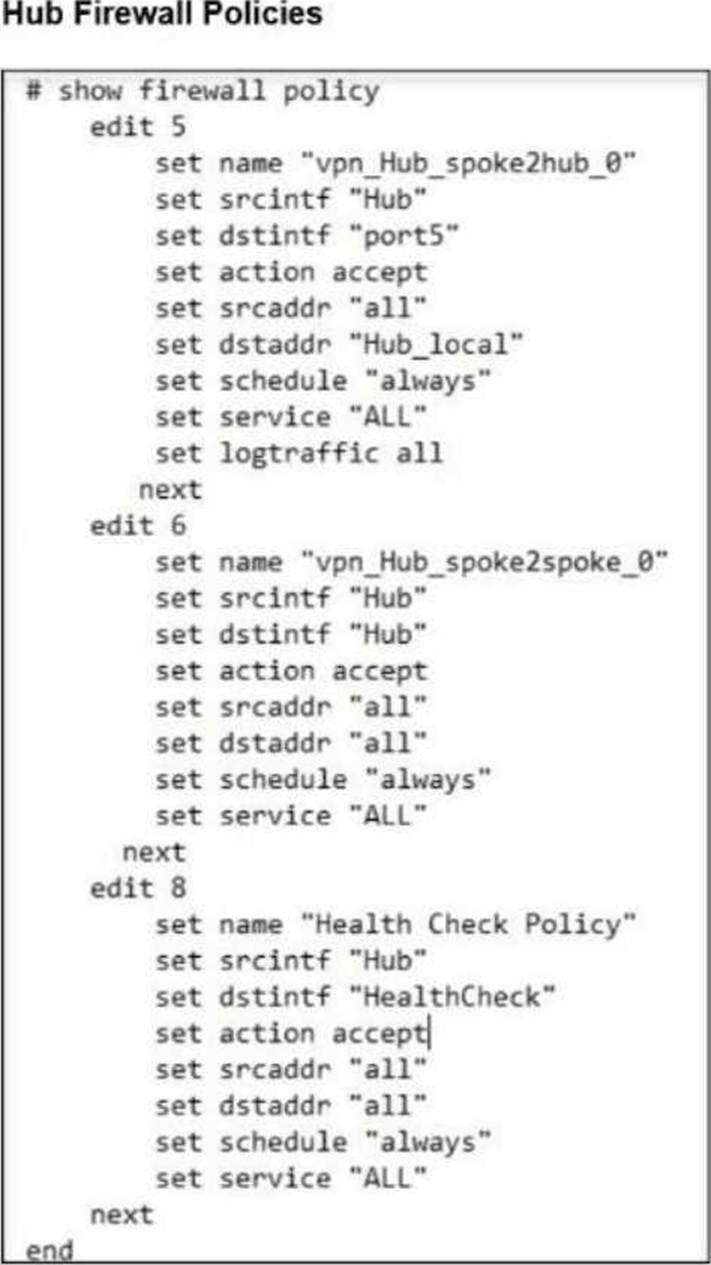
A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub.
The VPN tunnel does not establish.
Which configuration needs to be modified to bring the tunnel up?
- A . FortiSASE spoke devices do not support mode config.
- B . The network overlay ID must match on FortiSASE and the hub.
- C . The BGP router ID must match on the hub and FortiSASE.
- D . Auto-discovery-sender must be disabled on IPsec phase1 settings.
B
Explanation:
Fortinet documentation makes clear that overlay IDs must be identical on hub and spoke for ADVPN to establish correctly:
“When configuring the root and downstream FortiGates the Fabric Overlay Orchestrator configures… IPsec overlay configuration (hub and spoke ADVPN tunnels).”
“The Fabric root will be the hub and any first-level downstream devices from the Fabric root will be spokes.”
In the scenario:
FortiSASE overlay ID = 100
FortiGate hub overlay ID = 101
Mismatch prevents tunnel establishment. Therefore, the fix is: B. The network overlay ID must match on FortiSASE and the hub.
Which information can an administrator monitor using reports generated on FortiSASE?
- A . sanctioned and unsanctioned Software-as-a-Service (SaaS) applications usage
- B . FortiClient vulnerability assessment
- C . SD-WAN performance
- D . FortiSASE administrator and system events
A
Explanation:
FortiSASE reporting provides visibility into the usage of sanctioned and unsanctioned SaaS applications, enabling administrators to monitor cloud application activity and enforce security policies.
For monitoring potentially unwanted applications on endpoints, which information is available on the FortiSASE software installations page?
- A . the vendor of the software
- B . the endpoint the software is installed on
- C . the license status of the software
- D . the usage frequency of the software
B
Explanation:
The FortiSASE software installations page shows which endpoints have specific software installed, allowing administrators to monitor potentially unwanted applications across the network.
Refer to the exhibits.
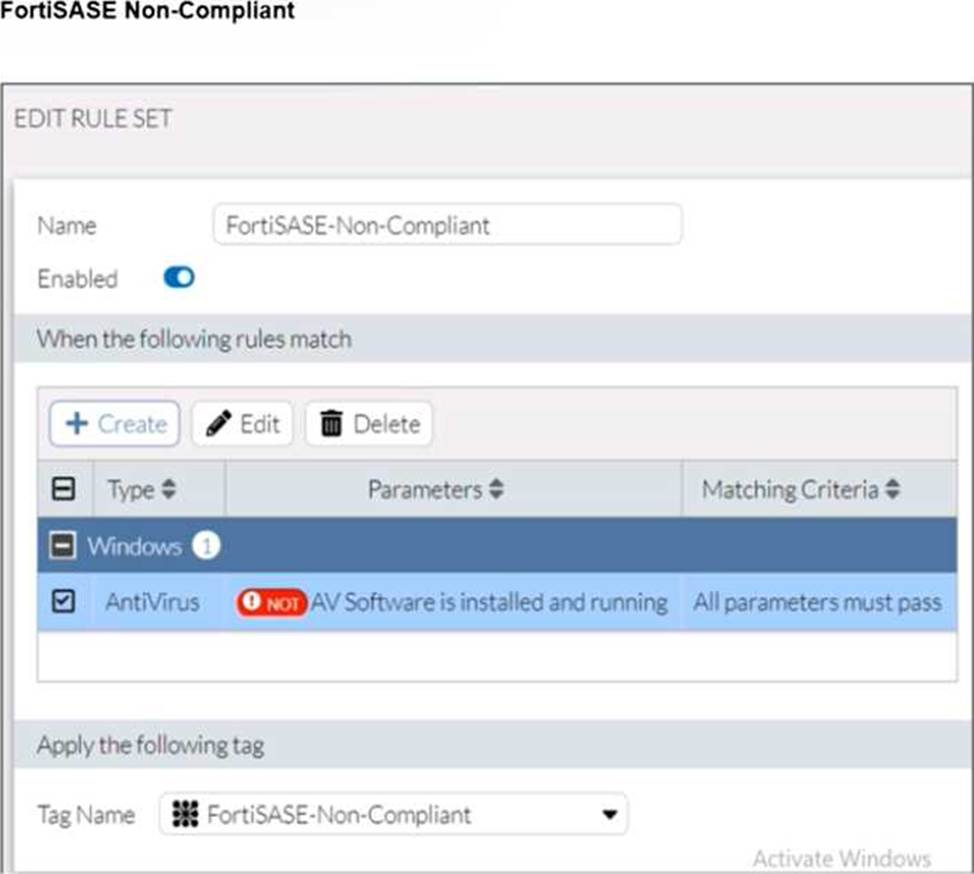
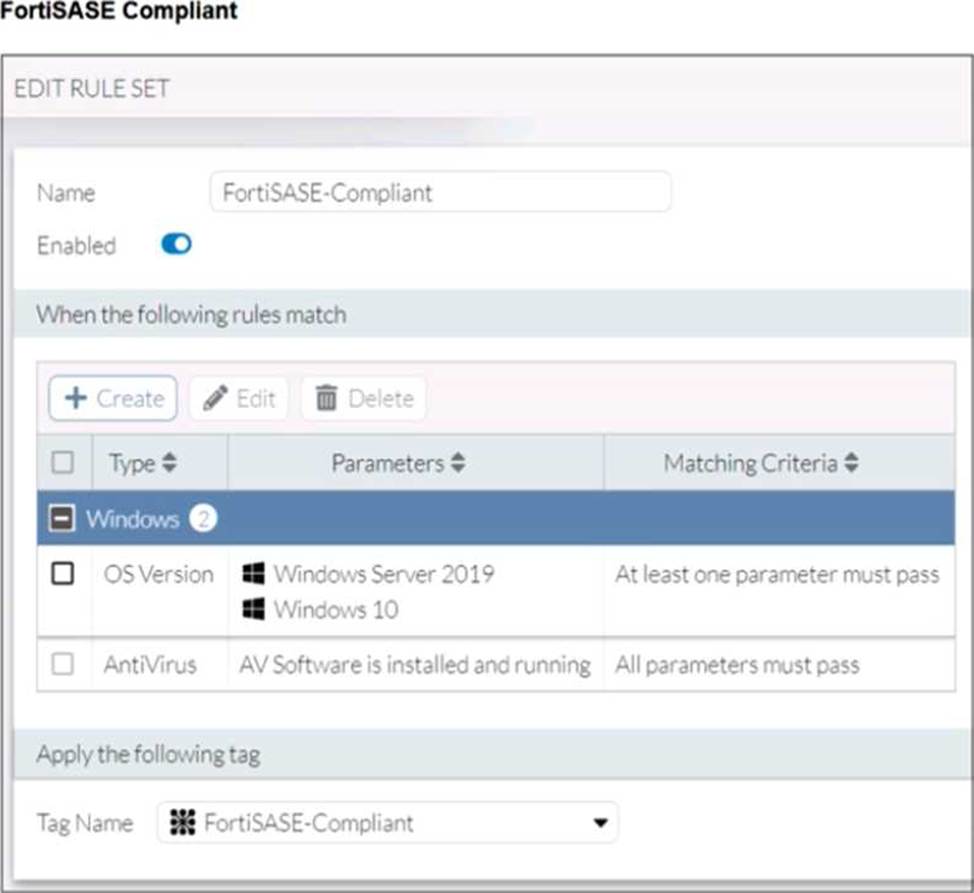
Antivirus is installed on a Windows 10 endpoint, but the windows application firewall is stopping it from running.
What will the endpoint security posture check be?
- A . FortiClient will tag the endpoint as FortiSASE-Non-Compliant.
- B . FortiClient will be unmanaged from FortiSASE due to failed compliance.
- C . FortiClient will trigger network lockdown on the endpoint.
- D . FortiClient will prompt the user to enable antivirus.
A
Explanation:
Although the antivirus is installed, it is not running due to the Windows application firewall blocking it. According to the FortiSASE-Non-Compliant rule, antivirus software must be both installed and running. Since this condition fails, FortiClient assigns the FortiSASE-Non-Compliant tag to the endpoint.
What happens to the logs on FortiSASE that are older than the configured log retention period?
- A . The logs are deleted from FortiSASE.
- B . The logs are indexed and can be stored in a SQL database.
- C . The logs are backed up on FortiCloud.
- D . The logs are compressed and archived.
A
Explanation:
Once the configured log retention period expires, FortiSASE automatically deletes the older logs to free up storage and maintain compliance with retention policies.
What are two benefits of deploying secure private access with SD-WAN? (Choose two.)
- A . a direct access proxy tunnel from FortiClient to the on-premises FortiGate
- B . ZTNA posture check performed by the hub FortiGate
- C . support of both TCP and UDP applications
- D . inline security inspection by FortiSASE
B,C
Explanation:
Deploying secure private access with SD-WAN enables the hub FortiGate to perform ZTNA posture checks, and supports both TCP and UDP applications over the tunnel, allowing for flexible and secure access to internal resources.
