Practice Free FCSS_SASE_AD-24 Exam Online Questions
Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
- A . FortiSASE CA certificate
- B . proxy auto-configuration (PAC) file
- C . FortiSASE invitation code
- D . FortiClient installer
A,B
Explanation:
Onboarding a Secure Web Gateway (SWG) endpoint involves several components to ensure secure and effective integration with FortiSASE. Two key components are the FortiSASE CA certificate and the proxy auto-configuration (PAC) file.
FortiSASE CA Certificate:
The FortiSASE CA certificate is essential for establishing trust between the endpoint and the FortiSASE infrastructure.
It ensures that the endpoint can securely communicate with FortiSASE services and inspect SSL/TLS traffic.
Proxy Auto-Configuration (PAC) File:
The PAC file is used to configure the endpoint to direct web traffic through the FortiSASE proxy.
It provides instructions on how to route traffic, ensuring that all web requests are properly inspected and filtered by FortiSASE.
Reference: FortiOS 7.2 Administration Guide: Details on onboarding endpoints and configuring SWG. FortiSASE 23.2 Documentation: Explains the components required for integrating endpoints with FortiSASE and the process for deploying the CA certificate and PAC file.
Refer to the exhibits.
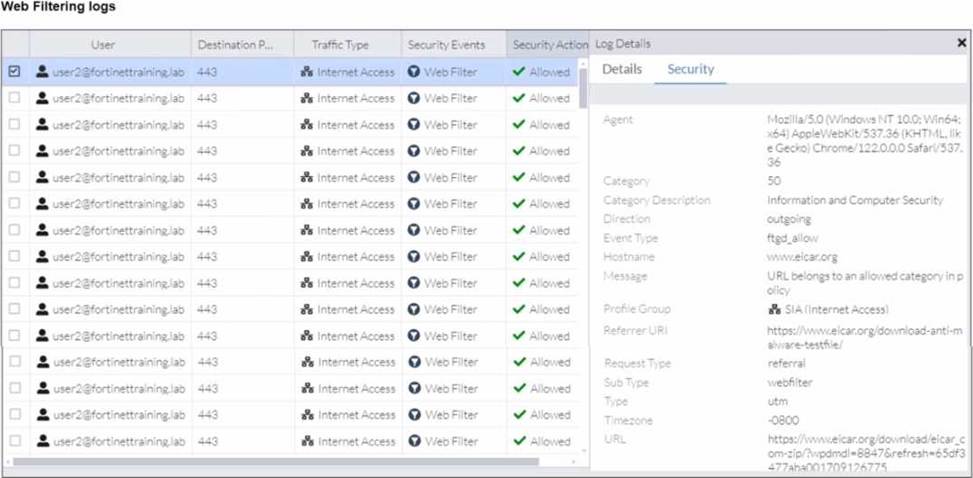
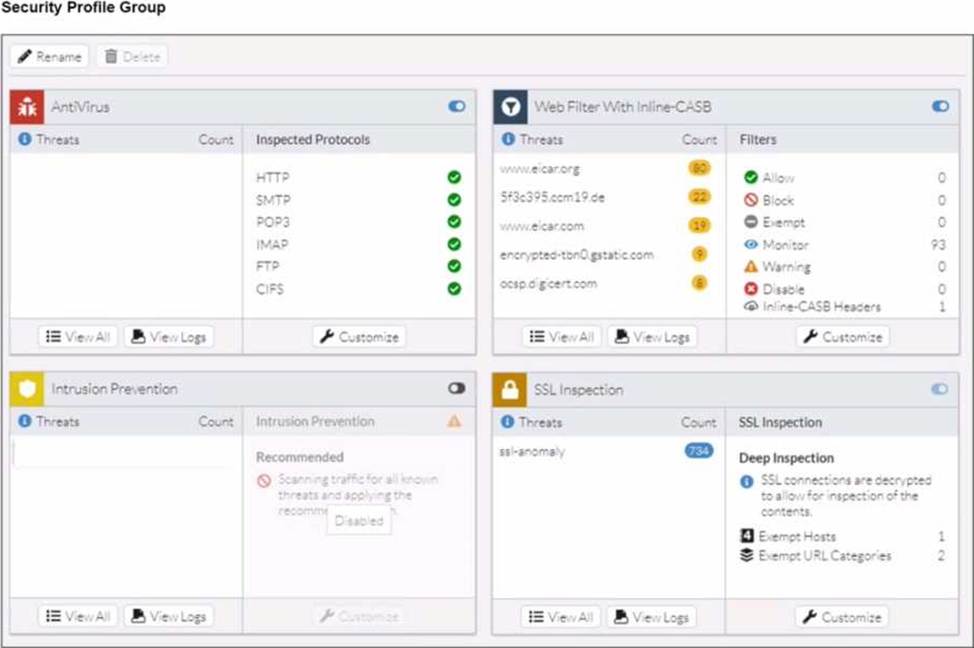
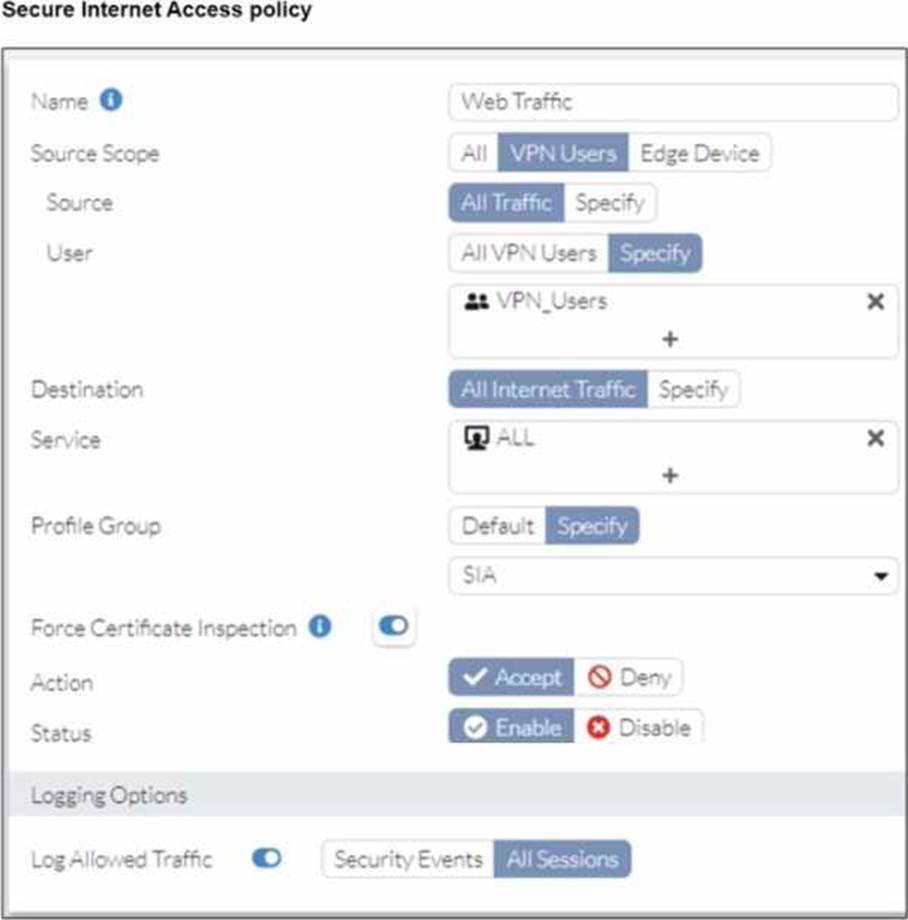
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org. Traffic logs show traffic is allowed by the policy.
Which configuration on FortiSASE is allowing users to perform the download?
- A . Web filter is allowing the traffic.
- B . IPS is disabled in the security profile group.
- C . The HTTPS protocol is not enabled in the antivirus profile.
- D . Force certificate inspection is enabled in the policy.
D
Explanation:
https://community.fortinet.com/t5/FortiSASE/Technical-Tip-Force-Certificate-Inspection-option-in-FortiSASE/ta-p/302617
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which three setups will achieve the above requirements? (Choose three.)
- A . Configure ZTNA servers and ZTNA policies on FortiGate.
- B . Configure private access policies on FortiSASE with ZTNA.
- C . Configure ZTNA tags on FortiGate.
- D . Configure FortiGate as a zero trust network access (ZTNA) access proxy.
- E . Sync ZTNA tags from FortiSASE to FortiGate.
A,D,E
Explanation:
Reference: Fortinet FCSS FortiSASE Documentation – Zero Trust Network Access (ZTNA) Deployment FortiGate Administration Guide – ZTNA Configuration
In a FortiSASE secure web gateway (SWG) deployment, which three features protect against web-based threats? (Choose three)
- A . Intrusion prevention system (IPS) for web traffic
- B . SSL deep inspection for encrypted web traffic
- C . Malware protection with sandboxing capabilities
- D . Data loss prevention (DLP) for web traffic
- E . Web application firewall (WAF) for web applications
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
- A . 3
- B . 4
- C . 2
- D . 1
C
Explanation:
https://docs.fortinet.com/document/fortisase/latest/administration-guide/751044/appendix-a-fortisase-data-centers#Number
What access point communication protocol does FortiAP use to communicate with FortiSASE in a micro branch deployment?
- A . Wireless Application Protocol (WAP)
- B . Control and Provisioning of Wireless Access Points (CAPWAP)
- C . Lightweight Access Point Protocol (LWAPP)
- D . Inter-Access Point Protocol (IAPP)
In The Secure Private Access (SPA) use case, which two FortiSASE features facilitate access to corporate applications? (Choose two.)
- A . SD-WAN
- B . Thin edge
- C . Cloud access security broker (CASB)
- D . Zero trust network access (ZTNA)
Which of the following describes the FortiSASE inline-CASB component?
- A . It provides visibility for unmanaged locations and devices.
- B . It is placed directly in the traffic path between the endpoint and cloud applications.
- C . It uses API to connect to the cloud applications.
- D . It detects data at rest.
B
Explanation:
TheFortiSASE inline-CASB (Cloud Access Security Broker) component is designed to provide real-time security and visibility by beingplaced directly in the traffic path between the endpoint and cloud applications. Inline-CASB inspects traffic as it flows to and from cloud applications, enabling enforcement of security policies, detection of threats, and prevention of unauthorized access. This approach ensures that all interactions with cloud applications are monitored and controlled in real time.
Here’s why the other options are incorrect:
You are designing a new network for Company X and one of the new cybersecurity policy requirements is that all remote user endpoints must always be connected and protected.
Which FortiSASE component facilitates this always-on security measure?
- A . site-based deployment
- B . thin-branch SASE extension
- C . unified FortiClient
- D . inline-CASB
C
Explanation:
The unified FortiClient component of FortiSASE facilitates the always-on security measure required for ensuring that all remote user endpoints are always connected and protected.
Unified FortiClient:
FortiClient is a comprehensive endpoint security solution that integrates with FortiSASE to provide continuous protection for remote user endpoints.
It ensures that endpoints are always connected to the FortiSASE infrastructure, even when users are off the corporate network.
Always-On Security:
The unified FortiClient maintains a persistent connection to FortiSASE, enforcing security policies and protecting endpoints against threats at all times.
This ensures compliance with the cybersecurity policy requiring constant connectivity and protection for remote users.
Reference: FortiOS 7.2 Administration Guide: Provides information on configuring and managing FortiClient for endpoint security.
FortiSASE 23.2 Documentation: Explains how FortiClient integrates with FortiSASE to deliver always-on security for remote endpoints.
A FortiSASE administrator is configuring a Secure Private Access (SPA) solution to share endpoint information with a corporate FortiGate.
Which three configuration actions will achieve this solution? (Choose three.)
- A . Add the FortiGate IP address in the secure private access configuration on FortiSASE.
- B . Use the FortiClient EMS cloud connector on the corporate FortiGate to connect to FortiSASE
- C . Register FortiGate and FortiSASE under the same FortiCloud account.
- D . Authorize the corporate FortiGate on FortiSASE as a ZTNA access proxy.
- E . Apply the FortiSASE zero trust network access (ZTNA) license on the corporate FortiGate.
B,C,D
Explanation:
Reference: FortiOS 7.2 Administration Guide: Provides details on configuring Secure Private Access and integrating with FortiGate.
FortiSASE 23.2 Documentation: Explains how to set up and manage connections between FortiSASE and corporate FortiGate.
