Practice Free FCSS_NST_SE-7.4 Exam Online Questions
What are two reasons you might see iprope_in_check() check failed, drop when using the debug flow? (Choose two.)
- A . Packet was dropped because of policy route misconfiguration.
- B . Packet was dropped because of traffic shaping.
- C . Trusted host list misconfiguration.
- D . VIP or IP pool misconfiguration.
Refer to the exhibit, which shows the modified output of the routing kernel.
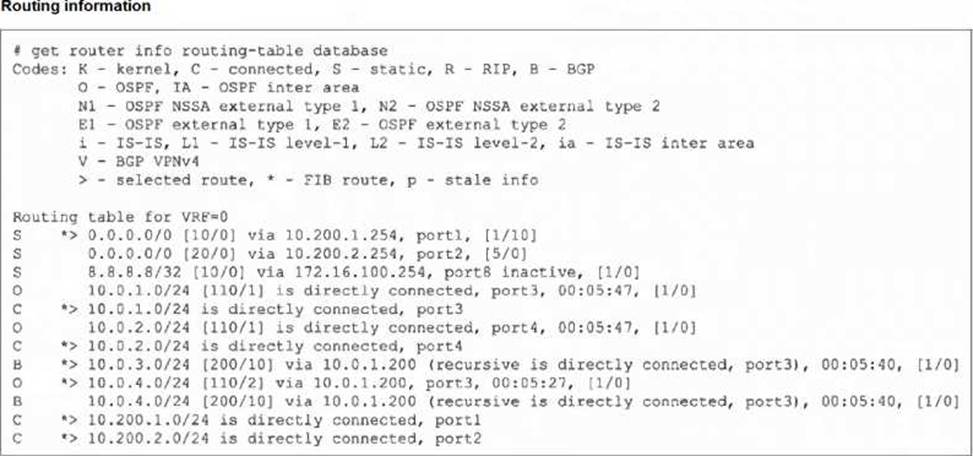
Which statement is true?
- A . The egress interface associated with static route 8.8.8.8/32 is administratively up.
- B . The default static route through 10.200.1.254 is not in the forwarding information base.
- C . The default static route through port2 is in the forwarding information base.
- D . The BGP route to 10.0.4.0/24 is not in the forwarding information base.
Refer to the exhibit, which shows the output of the command get router info bgp neighbors 100.64.2.254 advertised-routes.
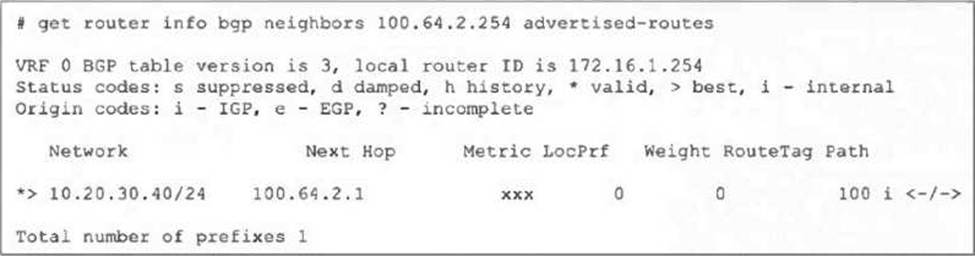
What can you conclude from the output?
- A . The BGP state of the two BGP participants is OpenConfirm.
- B . The router ID of the neighbor is 100.64.2.254.
- C . The BGP neighbor is advertising the 10.20.30.40/24 network to the local router.
- D . The local router is advertising the 10.20.30.40/24 network to its BGP neighbor.
Exhibit.
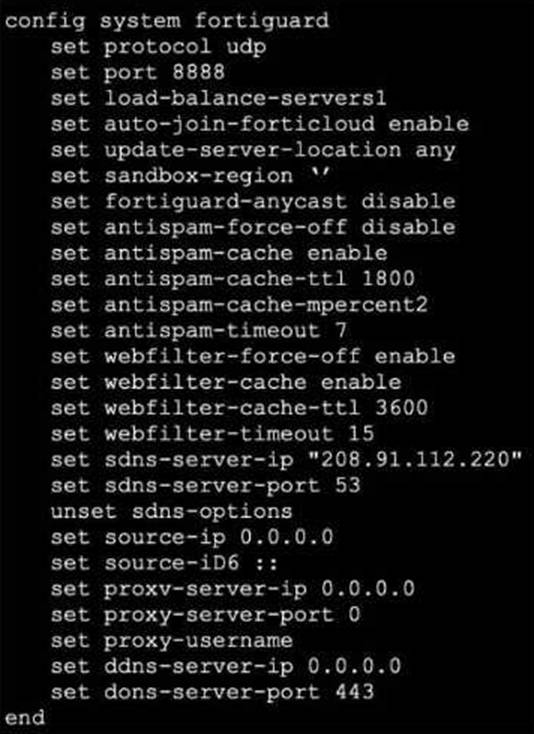
Refer to the exhibit, which shows a FortiGate configuration.
An administrator is troubleshooting a web filter issue on FortiGate. The administrator has configured a web filter profile and applied it to a policy; however the web filter is not inspecting any traffic that is passing through the policy.
What must the administrator do to fix the issue?
- A . Disable webfilter-force-off.
- B . Increase webfilter-timeout.
- C . Enable fortiguard-anycast.
- D . Change protocol to TCP.
Refer to the exhibit, which contains partial output from an IKE real-time debug.
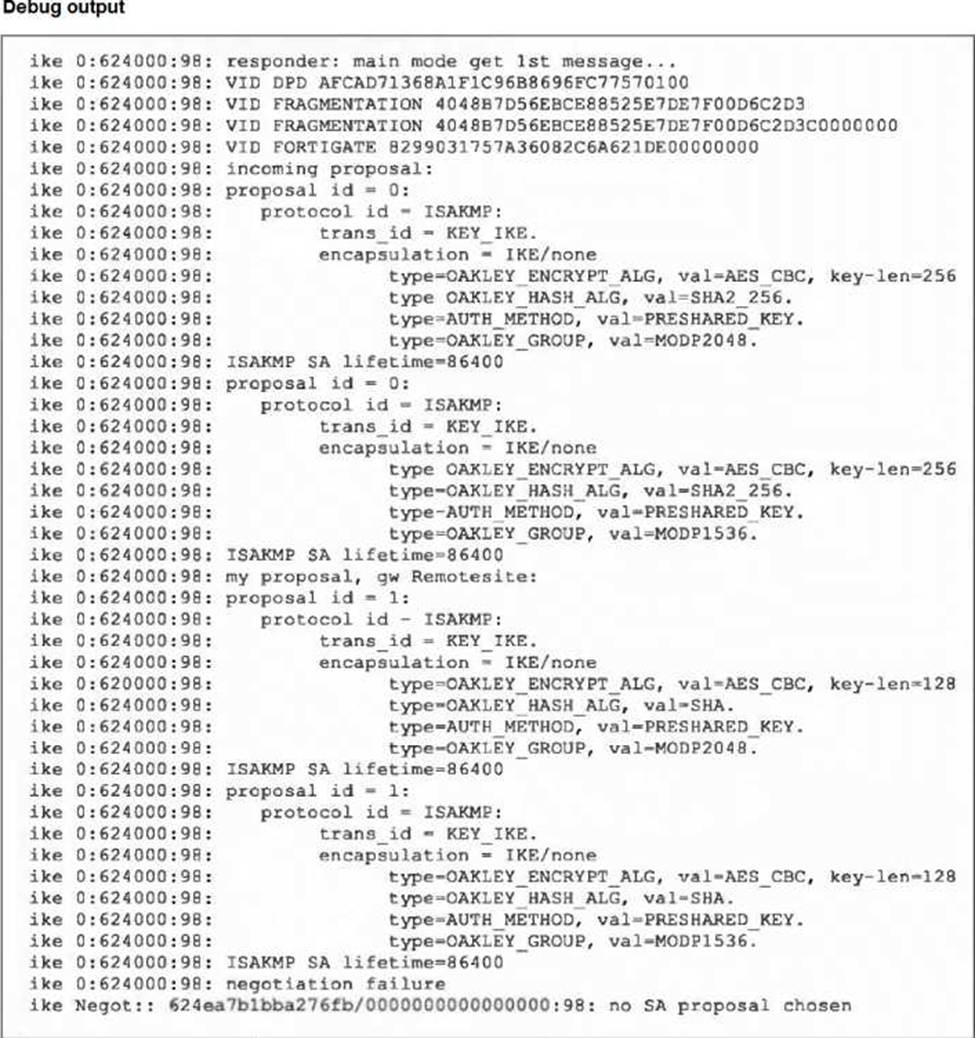
The administrator does not have access to the remote gateway.
Based on the debug output, which configuration change the administrator make to the local gateway to resolve the phase 1 negotiation error?
- A . In the phase 1 proposal configuration, add AES256-SHA256 to the list of encryption algorithms.
- B . In the phase 1 proposal configuration, add AESCBC-SHA2 to the list of encryption algorithms.
- C . In the phase 1 network configuration, set the IKE version to 2.
- D . In the phase 1 proposal configuration, add AES128-SHA128 to the list of encryption algorithms.
Refer to the exhibit, which shows the partial output of command diagnose debug rating.

In this exhibit, which FDS server will the FortiGate algorithm choose?
- A . 66.117.56.37
- B . 208.91.112.194
- C . 209.22.147.36
- D . 64.26.151.37
Refer to the exhibit.
The exhibit shows the output from using the command diagnose debug application samld -1 to diagnose a SAML connection.
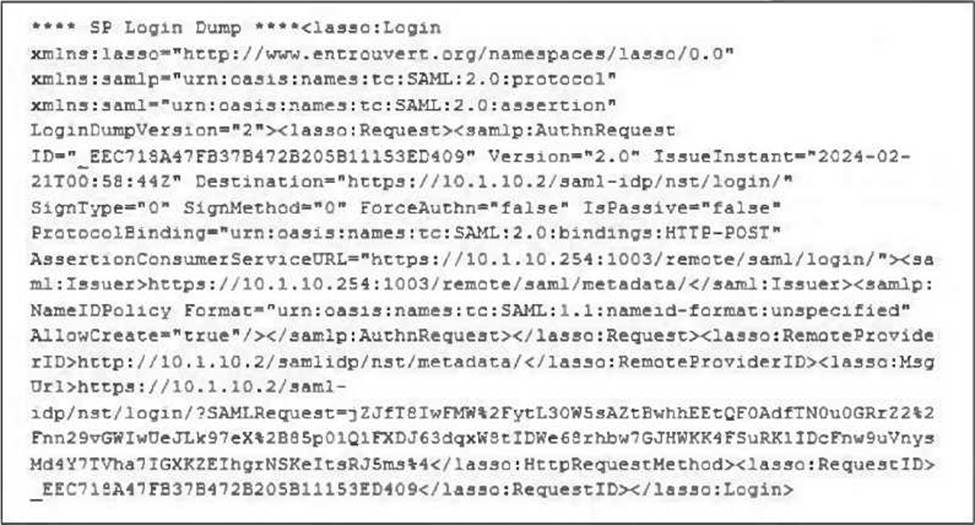
Based on this output, what can you conclude?
- A . Active Directory is used for authentication.
- B . The authentication request is for an SSL VPN connection.
- C . The IdP IP address is 10.1.10.254.
- D . The IdP IP address is 10.1.10.2.
Refer to the exhibit, which shows a partial output of the fssod daemon real-time debug command.
![]()
What two conclusions can you draw Itom the output? (Choose two.)
- A . The workstation with IP 10.124.2.90 will be polled frequently using TCP port 445 to see if the user is still logged on.
- B . The logon event can be seen on the collector agent installed on Windows.
- C . FSSO is using DC agent mode to detect logon events.
- D . FSSO is using agentless polling mode to detect logon events.
Refer to the exhibit, which shows the output of get router info ospf neighbor.
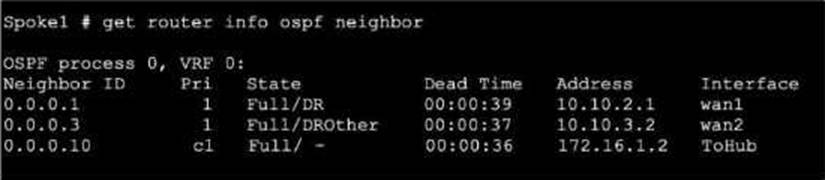
What can you conclude from the command output?
- A . The network type connecting the local Fortigate and OSPF neighbor 0.0.0.10 is point-to-point.
- B . All neighbors are in area 0.0.0.0.
- C . The local FortiGate is the BDR.
- D . The local FortiGate is not a DROther.
Refer to the exhibit, which shows a partial output of a real-time LDAP debug.
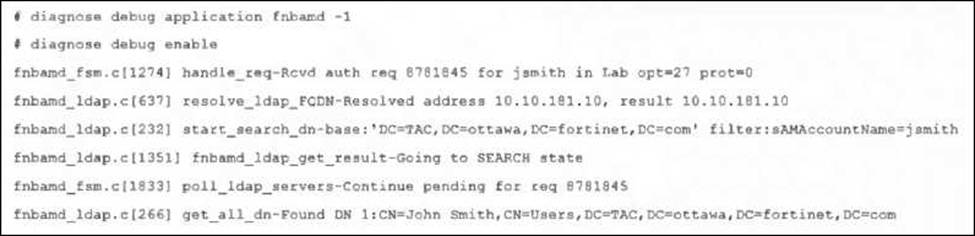
What two conclusions can you draw from the output? (Choose two.)
- A . The user was found in the LDAP tree, whose root is TAC.ottawa.fortinet.com.
- B . FortiOS performs a bind to the LDAP server using the user’s credentials.
- C . FortiOS collects the user group information.
- D . FortiOS is performing the second step (Search Request) in the LDAP authentication process.
