Practice Free FCSS_CDS_AR-7.6 Exam Online Questions
Refer to the exhibit.
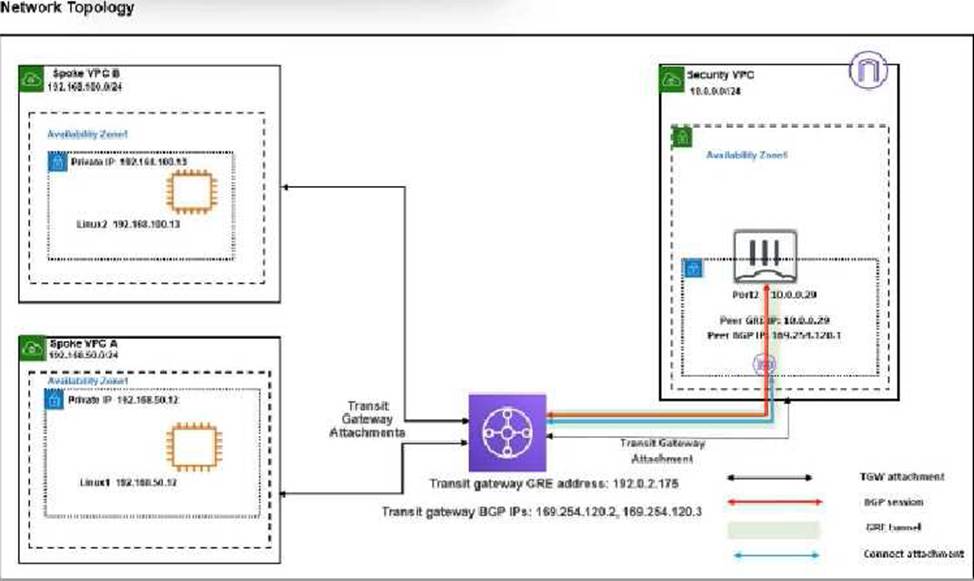
You attempted to access the Linux1 EC2 instance directly from the internet using its public IP address in AWS. However, your connection is not successful.
Given the network topology, what can be the issue?
- A . There is no connection between VPC A and VPC B.
- B . There is no Internet Gateway attached to the Spoke VPC A.
- C . The Transit Gateway BGP IP address is incorrect.
- D . There is no Elastic IP address attached to FortiGate in the Security VPC.
Refer to the exhibit.
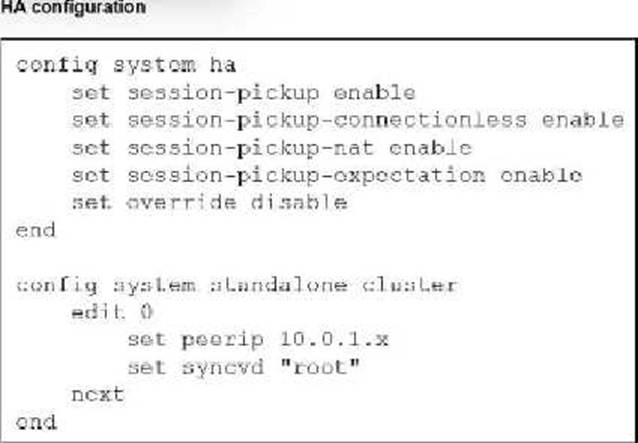
You deployed an HA active-active load balance sandwich with two FortiGate VMs in Microsoft Azure. After the deployment, you prefer to use FGSP to synchronize sessions and allow asymmetric return traffic. In the environment, FortiGate port 1 and port 2 are facing external and internal load balancers respectively.
What IP address must you use in the peering configuration?
- A . The opposite FortiGate port 2 IP address.
- B . The public load balancer port 2 IP address.
- C . The internal load balancer port 1 IP address.
- D . The opposite FortiGate port 1 IP address.
You need a solution to safeguard public cloud-hosted web applications from the OWASP Top 10 vulnerabilities. The solution must support the same region in which your applications reside, with minimum traffic cost.
Which solution meets the requirements?
- A . Use FortiGate
- B . Use FortiCNP
- C . Use FortiWeb
- D . Use FortiADC
Refer to the exhibit.
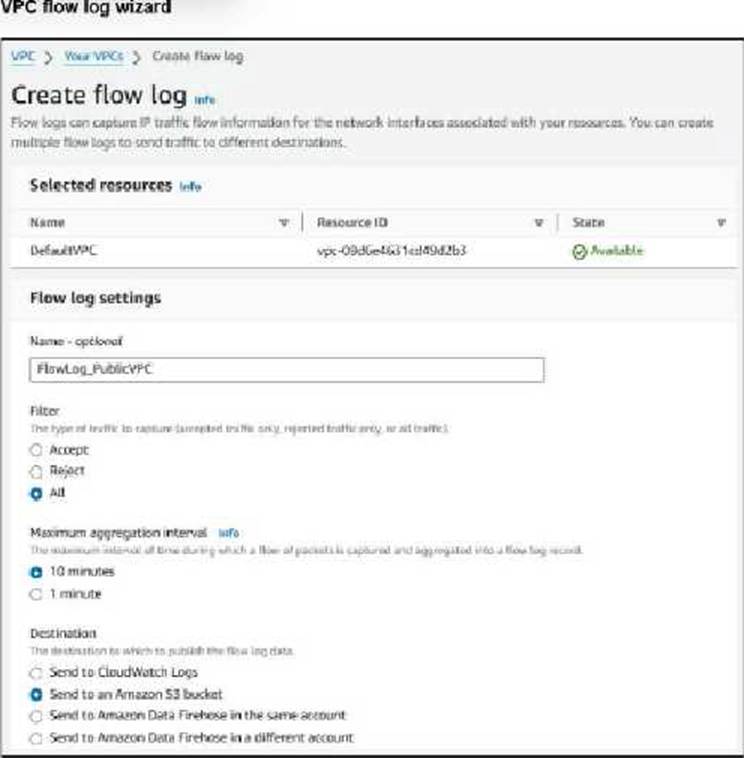
An experienced AWS administrator is creating a new Virtual Private Cloud (VPC) flow log with the settings shown in the exhibit.
What is the purpose of this configuration?
- A . To maximize the number of logs saved
- B . To monitor logs in real time
- C . To retain logs for a long term
- D . To troubleshoot a log flow issue
Refer to the exhibit.
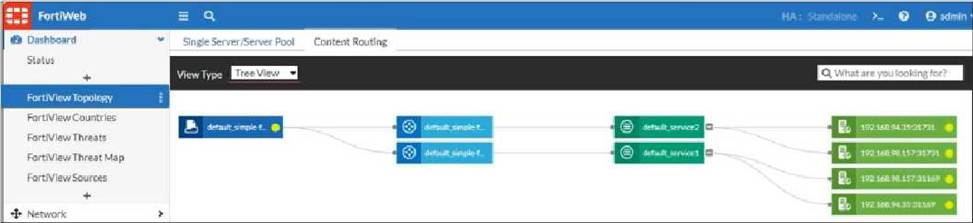
An administrator implements FortiWeb ingress controller to protect containerized web applications in an AWS Elastic Kubernetes Service (EKS) cluster.
What can you conclude about the topology shown in FortiView?
- A . The FortiWeb VM gets the latest cluster information through an SDN connector.
- B . This topology has two services and two ingress controllers deployed.
- C . Both services will be load balanced among the two nodes and the four pods.
- D . Adding a new service will update the FortiWeb configuration automatically.
An organization is deploying FortiDevSec to enhance security for containerized applications, and they need to ensure containers are monitored for suspicious behavior at runtime.
Which FortiDevSec feature is best for detecting runtime threats?
- A . FortiDevSec Software Composition Analysis (SCA)
- B . FortiDevSec Static Application Security Testing (SAST)
- C . FortiDevSec Dynamic Application Security Testing (DAST)
- D . FortiDevSec Container Scanner
An administrator decides to use the Use managed identity option on the FortiGate SDN connector with Microsoft Azure. However, the SDN connector is failing on the connection.
What must the administrator do to correct this issue?
- A . Make sure to add the Client Secret on the FortiGate side of the configuration.
- B . Make sure to add the Tenant ID on the FortiGate side of the configuration.
- C . Make sure to enable the system-assigned managed identity on Azure.
- D . Make sure to set the type to system managed identity on FortiGate SDN connector settings.
Refer to the exhibit.
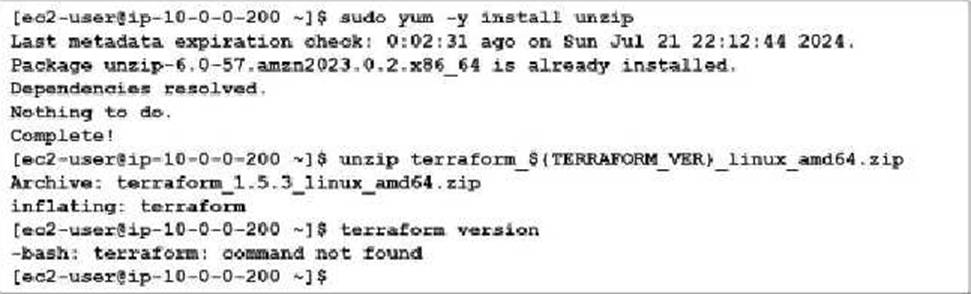
You are tasked with deploying FortiGate using Terraform. When you run the terraform version command during the Terraform installation, you get an error message.
What could you do to resolve the command not found error?
- A . You must move the binary file to the bin directory.
- B . You must reinstall Terraform.
- C . You must change the directory location to the root directory.
- D . You must assign correct permissions to the ec2-user.
Refer to the exhibit.
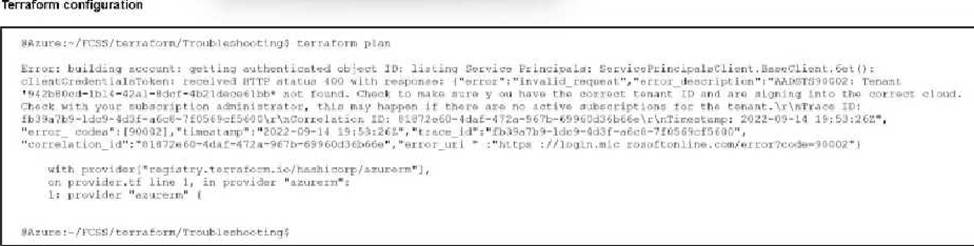
After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run.
Which two statements about running the terraform plan command are true? (Choose two.)
- A . The terraform plan command will deploy the rest of the resources except the service principal details.
- B . You cannot run the terraform apply command before the terraform plan command.
- C . The terraform plan command makes Terraform do a dry run.
- D . You must run the terraform init command once, before the terraform plan command.
Your monitoring team reports performance issues with a web application hosted in Azure. You suspect that the bottleneck might be due to unexpected inbound traffic spikes.
Which method should you use to identify and analyze the traffic pattern?
- A . Deploy Azure Firewall to log traffic by IP address.
- B . Enable Azure DDoS protection to prevent inbound traffic spikes.
- C . Use Azure Traffic Manager to visualize all traffic to the application.
- D . Enable NSG Flow Logs and analyze logs with Azure Monitor.
