Practice Free FCP_FWB_AD-7.4 Exam Online Questions
Refer to the exhibit.
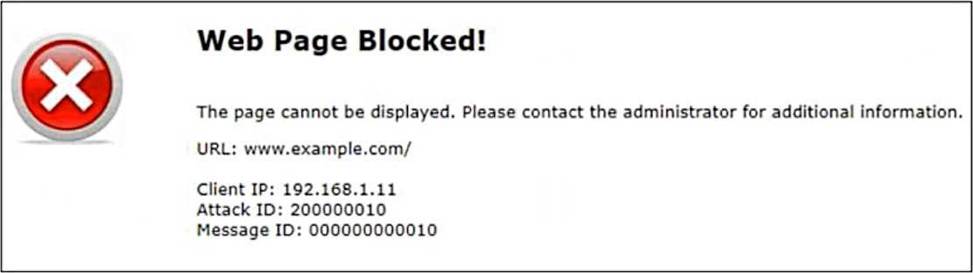
Attack ID 20000010 is brute force logins.
Which statement is accurate about the potential attack?
- A . The attacker has successfully retrieved the credentials to www.example.com.
- B . www.example.com is running attacks against the client 192.168. 1. 1 1.
- C . The attack has happened 10 times.
- D . 192.168. 1. 11 is sending suspicious traffic to FortiWeb.
D
Explanation:
The Attack ID of 20000010 refers to a brute force login attempt, which typically indicates that the client IP (192.168. 1. 11) is sending suspicious or malicious traffic to the FortiWeb. FortiWeb detected and blocked this suspicious activity, which is why the page is shown as blocked.
Which technology is commonly used for machine learning-based threat detection in web applications?
- A . Blockchain
- B . Artificial Intelligence (AI)
- C . Internet of Things (IoT)
- D . Virtual Private Network (VPN)
Which three stages are part of creating a machine learning (ML) bot detection algorithm? (Choose three.)
- A . Model building
- B . Model running
- C . Model verification
- D . Sample collecting
- E . Model Bayesian analysis
A, C, D
Explanation:
Model building: In this stage, you design and develop the ML model, which involves selecting appropriate algorithms and features to detect bot activity.
Model verification: This is where you test and evaluate the model’s performance to ensure it can accurately detect bots without false positives or negatives.
Sample collecting: Gathering relevant data samples (e.g., bot and non-bot traffic) to train the machine learning model is crucial to ensure it can learn from various scenarios.
What is a common technique to mitigate Cross-Site Scripting (XSS) attacks in web applications?
- A . Input validation and escaping
- B . Encryption of user passwords
- C . Captcha verification for login forms
- D . SSL/TLS encryption
Which three security features must you configure on FortiWeb to protect API connections? (Choose three.)
- A . Single sign-on (SSO) authentication with Active Directory (AD)
- B . Machine learning (ML)-based API protection
- C . API schema validation
- D . API user authentication with SAML
- E . API user key enforcement
B, C, E
Explanation:
Machine learning (ML)-based API protection: ML-based API protection helps detect and mitigate abnormal behavior in API traffic, such as bot attacks or abuse, by learning and adapting to normal traffic patterns.
API schema validation: API schema validation ensures that the API requests conform to the defined schema (e.g., checking the structure, fields, and types in the API calls). This helps prevent attacks like XML or JSON injection by ensuring only valid requests are processed.
API user key enforcement: Enforcing API user key authentication requires clients to provide valid API keys, ensuring only authorized users can access the API. This is crucial for controlling access to the API.
Refer to the exhibit.

A FortiWeb device is deployed upstream of a device performing source network address translation (SNAT) or load balancing.
What configuration must you perform on FortiWeb to preserve the original IP address of the client?
- A . Enable and configure the Preserve Client IP setting.
- B . Use a transparent operating mode on FortiWeb.
- C . Enable and configure the Add X-Forwarded-For setting.
- D . Turn off NAT on the FortiWeb.
A
Explanation:
When FortiWeb is deployed upstream of a device performing source network address translation (SNAT) or load balancing, the original client IP address may be lost. To preserve the original client IP address, you must enable and configure the Preserve Client IP setting on FortiWeb. This allows FortiWeb to retain and pass the client’s original IP address to the backend servers for accurate logging and processing.
Refer to the exhibit.
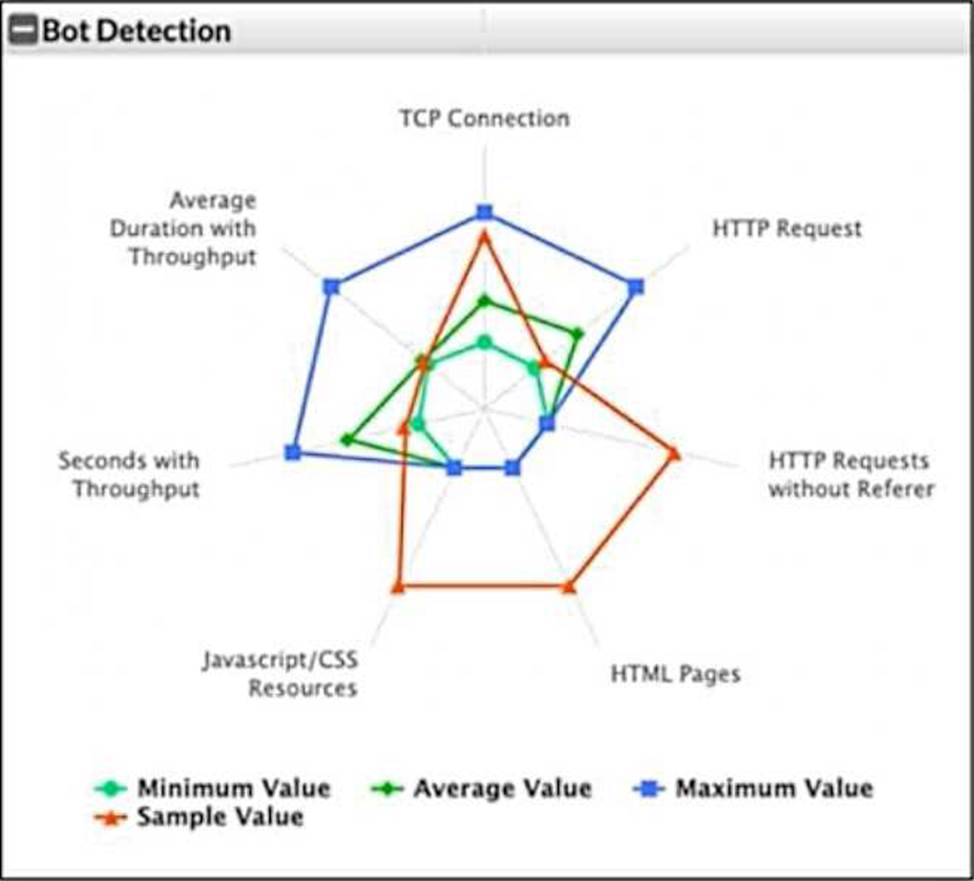
What can you conclude from this support vector machine (SVM) plot of a potential bot connection?
- A . The connection is normal and within the expected averages.
- B . The connection uses too much bandwidth.
- C . The connection uses an excessive amount of TCP connections, but is harmless.
- D . The connection is possibly a bot.
D
Explanation:
In the SVM plot of potential bot activity, you can see that the sample value (orange) is significantly different from the average value (green) and the maximum value (blue) in most of the metrics. This suggests unusual or abnormal behavior, indicating that the connection might be a bot. Typically, bots exhibit patterns that diverge from normal user activity, such as higher frequencies of certain types of requests, abnormal throughput, or an unusual pattern of HTTP requests (such as requests without referers or excessive TCP connections).
You are deploying FortiWeb 5.6.0 in an Amazon Web Services cloud.
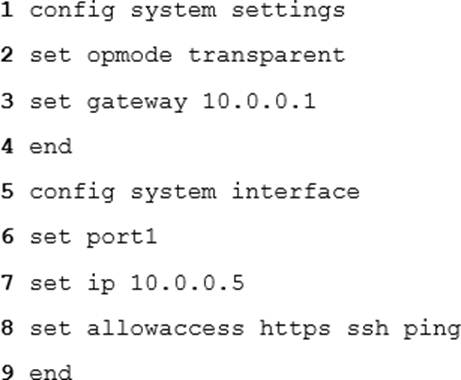
Which 2 lines of this initial setup via CLI are incorrect? (Choose two.)
- A . 6
- B . 9
- C . 3
- D . 2
What role does FortiWeb play in ensuring PCI DSS compliance?
- A . PCI specifically requires a WAF
- B . Provides credit card processing capabilities
- C . Provide ability to securely process cash transactions
- D . Provides load balancing between multiple web servers
When configuring access control for a web application, which methods can be used to enforce security? (Select all that apply)
- A . Role-based access control (RBAC)
- B . Two-factor authentication (2FA)
- C . Captcha verification
- D . IP whitelisting
