Practice Free FCP_FML_AD-7.4 Exam Online Questions
Which two statements about how FortiMail behaves when using transparent proxies to process email in transparent mode, are true? (Choose two.)
- A . The inbound proxy supports message queuing and DSNs.
- B . FortiMail ignores the destination set by the sender, and uses its own MX record lookup to deliver email.
- C . The outbound proxy supports DSNs, but not message queuing.
- D . If you disable the transparent proxies, FortiMail will use its built-in MTA to process email.
Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).
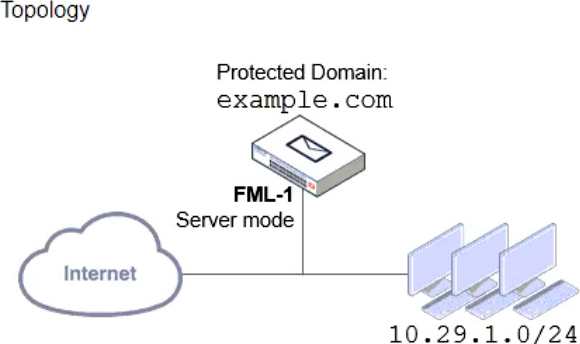
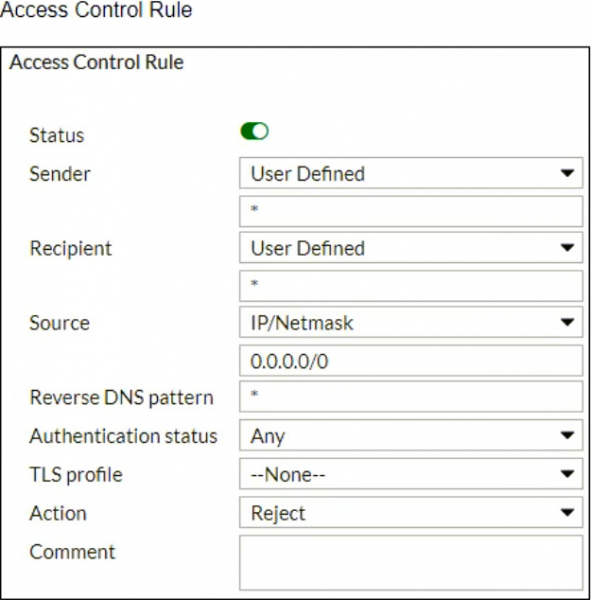
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)
- A . The Sender IP/netmask should be set to 10.29.1.0/24.
- B . The Action should be set to Reject.
- C . The Recipient pattern should be set to *@example.com.
- D . The Authentication status should be set to Authenticated.
Refer to the exhibit, which displays the Mail Settings page of a FortiMail device running in gateway mode.
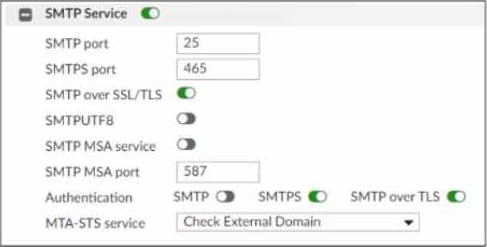
In addition to selecting Check External Domain in the MTA-STS service field, what else must an administrator do to enable MTA-STS?
- A . Enable MTA-STS in the associated TLS profile.
- B . Enable SMTPUTF8 support in the mail server settings.
- C . Enable secure authentication in the associated SMTP authentication profile.
- D . Enable MTA-STS action in the appropriate inbound recipient policy.
Which three configuration steps must you set to enable DKIM signing for outbound messages on FortiMail? (Choose three.}
- A . Generate a public/private key pair in the protected domain configuration.
- B . Enable the DKIM checker in a matching session profile.
- C . Publish the public key as a TXT record in a public DNS server.
- D . Enable the DKIM checker in a matching antispam profile.
- E . Enable DKIM signing for outgoing messages in a matching session profile.
When deploying FortiMail in transparent mode, what role does FortiMail play in the email flow?
- A . FortiMail serves as the primary mail server.
- B . FortiMail decrypts all incoming emails.
- C . FortiMail operates as a transparent proxy for incoming and outgoing emails.
- D . FortiMail exclusively handles email encryption.
What must be configured on FortiMail to allow for the automatic encryption of outgoing emails?
- A . SSL/TLS certificates
- B . Encryption profiles
- C . Access control rules
- D . IP whitelisting
When would you typically deploy FortiMail in Transparent Mode?
- A . When you need FortiMail to act as the primary mail server.
- B . When you want to enforce strict email encryption policies.
- C . When you want FortiMail to filter emails without changing DNS records.
- D . When you need to manage email storage and retrieval.
What is the primary function of content-based email filtering?
- A . Sorting emails based on sender addresses
- B . Analyzing email attachments for size
- C . Filtering emails based on keywords, patterns, or specific content
- D . Encrypting email traffic between servers
What is the role of IBE users in FortiMail?
- A . To manage the encryption keys for all users.
- B . To receive and decrypt encrypted emails.
- C . To configure encryption policies.
- D . To monitor email traffic for security threats.
In which FortiMail configuration object can you assign an outbound session profile?
- A . Outbound recipient policy
- B . Inbound recipient policy
- C . IP policy
- D . Access delivery rule
