Practice Free FCP_FML_AD-7.4 Exam Online Questions
What is the primary goal of encryption in email communication?
- A . Increasing email attachment size limits
- B . Reducing email delivery time
- C . Securing the content of emails from unauthorized access
- D . Preventing email spoofing
A mail user wants the ability to subscribe or publish to and from their FortiMail calendar using Thunderbird as their mail user agent (MUA).
What information does this mail user need from their webmail User Preferences section?
- A . Free busy URL
- B . Service URLs
- C . Secondary account configurations
- D . Message tags
What are two benefits of enabling the header manipulation feature? (Choose two.)
- A . It hides internal network information.
- B . It reduces overall message size by removing header content.
- C . It detects common spamming techniques.
- D . It detects spoofed SMTP header addresses.
Refer to the exhibit, which displays an encryption profile configuration.
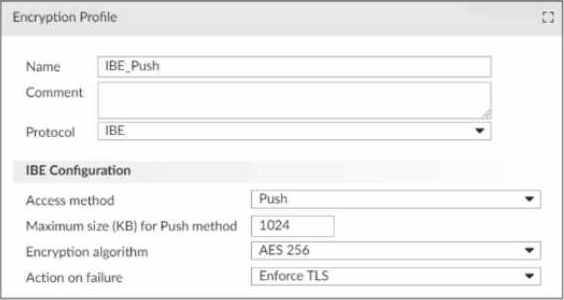
What happens if the attachment size of an IBE email exceeds 1024 KB?
- A . Pull delivery will be used.
- B . The email message will not be delivered.
- C . OTLS will be used.
- D . AES 256 will be used.
Which two types of remote authentication are supported for FortiMail administrator accounts? (Choose two.)
- A . Single Sign-on
- B . TACACS
- C . Kerberos
- D . RADIUS
What are the key considerations when deploying FortiMail in Transparent Mode? (Choose all that apply)
- A . Ensuring network compatibility for email traffic relay.
- B . Configuring FortiMail to bypass encryption checks.
- C . Setting up FortiMail to monitor email traffic without altering it.
- D . Ensuring FortiMail can handle email attachments efficiently.
Which actions can help monitor and troubleshoot email flow issues in FortiMail? (Choose all that apply)
- A . Reviewing log files and message tracking
- B . Analyzing SMTP transaction logs
- C . Checking IP whitelisting configurations
- D . Verifying recipient policies
What does an IP whitelist in FortiMail allow you to do?
- A . Block all incoming emails from specific senders.
- B . Allow emails only from a list of approved IP addresses.
- C . Automatically send suspicious emails to quarantine.
- D . Encrypt all outgoing emails.
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks.
What option can the administrator configure to prevent these types of attacks?
- A . Impersonation analysis
- B . Dictionary profile with predefined smart identifiers
- C . Bounce tag verification
- D . Content disarm and reconstruction
Which deployment scenarios are suitable for using Server Mode in FortiMail? (Choose all that apply)
- A . Small businesses with minimal email traffic.
- B . Organizations needing full control over email processing.
- C . Environments where FortiMail will act as the sole mail server.
- D . High-traffic environments requiring rapid email delivery.
