Practice Free FCP_FGT_AD-7.6 Exam Online Questions
Which two statements are correct about SLA targets? (Choose two.)
- A . You can configure only two SLA targets per one Performance SLA.
- B . SLA targets are optional.
- C . SLA targets are required for SD-WAN rules with a Best Quality strategy.
- D . SLA targets are used only when referenced by an SD-WAN rule.
B,D
Explanation:
B. SLA targets are optional.
D. SLA targets are used only when referenced by an SD-WAN rule.
Incorrect:
Which two statements are true about an HA cluster? (Choose two.)
- A . An HA cluster cannot have both in-band and out-of-band management interfaces at the same time.
- B . Link failover triggers a failover if the administrator sets the interface down on the primary device.
- C . When sniffing the heartbeat interface, the administrator must see the IP address 169.254.0.2.
- D . HA incremental synchronization includes FIB entries and IPsec SAs.
B, D
Explanation:
Setting an interface down on the primary device triggers a failover due to link failover detection.
HA incremental synchronization includes forwarding information base (FIB) entries and IPsec security associations (SAs) to maintain session continuity.
Refer to the exhibit.
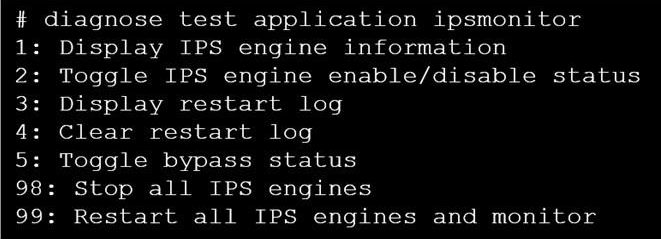
Examine the intrusion prevention system (IPS) diagnostic command.
Which statement is correct If option 5 was used with the IPS diagnostic command and the outcome was a decrease in the CPU usage?
- A . The IPS engine was inspecting high volume of traffic.
- B . The IPS engine was unable to prevent an intrusion attack.
- C . The IPS engine was blocking all traffic.
- D . The IPS engine will continue to run in a normal state.
A
Explanation:
If there are high-CPU use problems caused by the IPS, you can use the diagnose test application ipsmonitor command with option 5 to isolate where the problem might be. Option 5 enables IPS bypass mode.
In this mode, the IPS engine is still running, but it is not inspecting traffic.
If the CPU use decreases after that, it usually indicates that the volume of traffic being inspected is too high for that FortiGate model.
If the CPU use remains high after enabling IPS bypass mode, it usually indicates a problem in the IPS engine, which you must report to Fortinet Support.
If there are high-CPU use problems caused by the IPS, you can use the diagnose test application ipsmonitor command with option 5 to isolate where the problem might be. Option 5 enables IPS bypass mode. In this mode, the IPS engine is still running, but it is not inspecting traffic. If the CPU use decreases after that, it usually indicates that the volume of traffic being inspected is too high for that FortiGate model.
Which two statements are true when FortiGate is in transparent mode? (Choose two.)
- A . By default, all interfaces are part of the same broadcast domain.
- B . The existing network IP schema must be changed when installing a transparent mode FortiGate in the network.
- C . Static routes are required to allow traffic to the next hop.
- D . FortiGate forwards frames without changing the MAC address.
A,D
Explanation:
The correct statements regarding FortiGate in transparent mode are:
Refer to the exhibit, which contains a session list output.
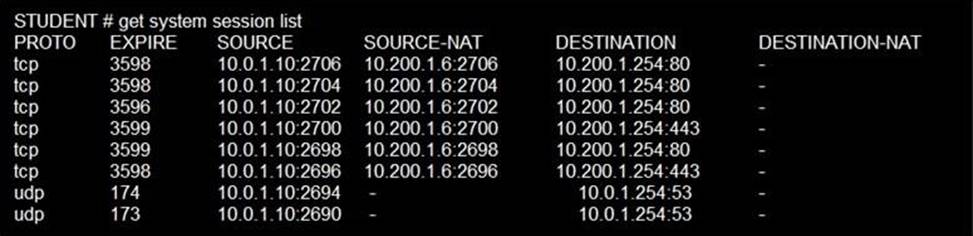
Based on the information shown in the exhibit, which statement is true?
- A . Port block allocation IP pool is used in the firewall policy
- B . Destination NAT is disabled in the firewall policy
- C . Overload NAT IP pool is used in the firewall policy
- D . One-to-one NAT IP pool is used in the firewall policy
D
Explanation:
One-to-one NAT IP pool is used in the firewall policy.
In one-to-one, PAT is not required.
In the one-to-one pool type, an internal IP address is mapped with an external address on a first-come, first-served basis.
There is a single mapping of an internal address to an external address. Mappings are not fixed and, if there are no more addresses available, a connection will be refused.
Also, in one-to-one, PAT is not required. In the example on this slide, you can see the same source port is shown for both the ingress and egress address.
Refer to the exhibits.
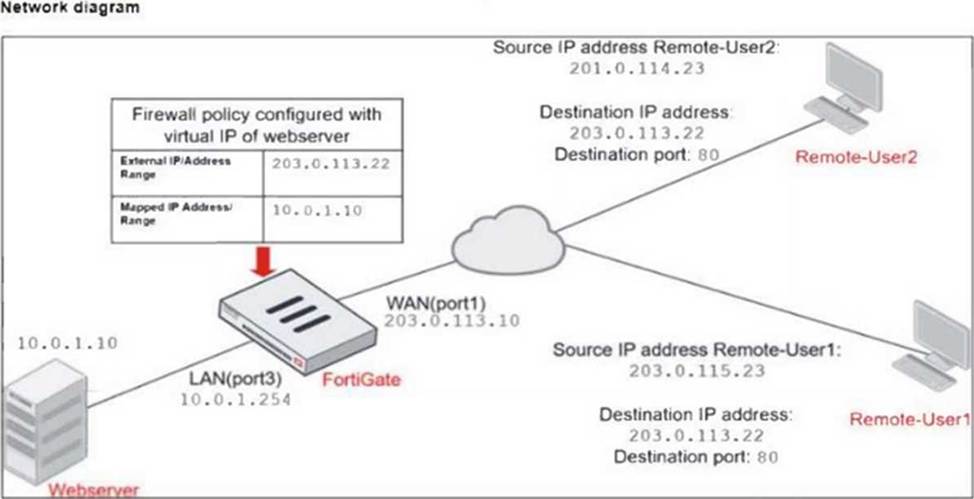
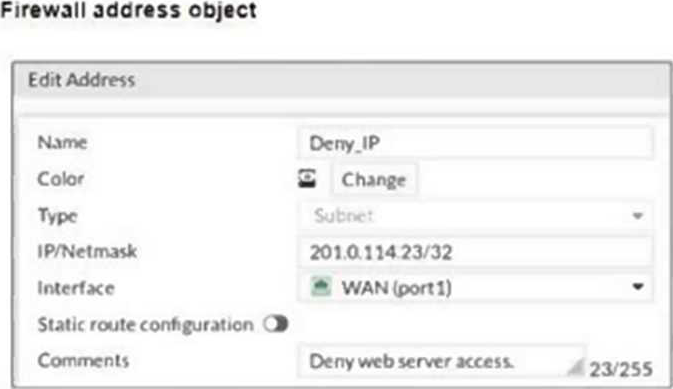
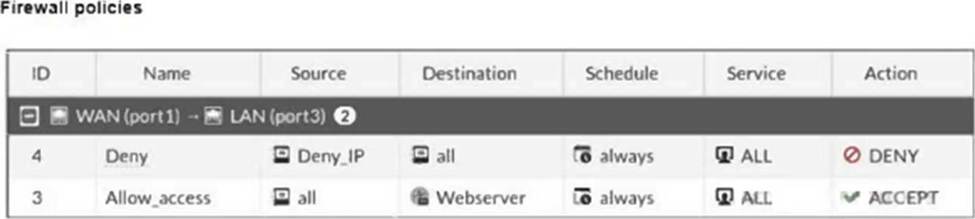
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2.
The policy should work such that Remote-User1 must be able to access the Webserver while preventing Remote-User2 from accessing the Webserver.
Which two configuration changes can the administrator make to the policy to deny Webserver access for Remote-User2? (Choose two.)
- A . Enable match-vip in the Deny policy.
- B . Set the Destination address as Webserver in the Deny policy.
- C . Disable match-vip in the Deny policy.
- D . Set the Destination address as Deny_IP in the Allow_access policy.
A, B
Explanation:
To deny access to the web server for Remote-User2 while allowing Remote-User1 to access the same web server, two configuration changes can be made:
Enable match-vip in the Deny policy:
By enabling the match-vip option in the Deny policy, the FortiGate will check for virtual IP (VIP) objects during policy matching. This setting allows the firewall policy to correctly identify and block traffic directed to a specific mapped IP address, such as the web server, when using a VIP configuration.
Set the Destination address as Webserver in the Deny policy:
Setting the Destination address to "Webserver" in the Deny policy ensures that the policy specifically targets traffic attempting to reach the web server. This configuration helps to precisely control which traffic should be blocked, focusing the Deny policy on the intended destination.
Reference: FortiOS 7.4.1 Administration Guide: Deny matching with a policy with a virtual IP applied
FortiOS 7.4.1 Administration Guide: Configuring Policies with VIPs
An administrator has configured the following settings:
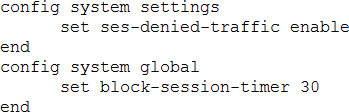
What are the two results of this configuration? (Choose two.)
- A . Device detection on all interfaces is enforced for 30 minutes
- B . Denied users are blocked for 30 minutes
- C . A session for denied traffic is created
- D . The number of logs generated by denied traffic is reduced
C, D
Explanation:
C. A session for denied traffic is created.
D. The number of logs generated by denied traffic is reduced.
During the session, if a security profile detects a violation, FortiGate records the attack log immediately. To reduce the number of log messages generated and improve performance, you can enable a session table entry of dropped traffic. This creates the denied session in the session table and, if the session is denied, all packets of that session are also denied. This ensures that FortiGate does not have to do a policy lookup for each new packet matching the denied session, which reduces CPU usage and log generation.
This option is in the CLI, and is called ses-denied-traffic. You can also set the duration for block sessions. This determines how long a session will be kept in the session table by setting block-sessiontimer in the CLI. By default, it is set to 30 seconds.
What are two features of collector agent advanced mode? (Choose two.)
- A . In advanced mode, FortiGate can be configured as an LDAP client and group filters can be configured on FortiGate.
- B . Advanced mode supports nested or inherited groups.
- C . In advanced mode, security profiles can be applied only to user groups, not individual users.
- D . Advanced mode uses the Windows convention ―NetBios: DomainUsername.
A, B
Explanation:
Advanced mode allows for configuration as an LDAP client and supports group filtering directly on the FortiGate, as well as nested or inherited groups.
A new administrator is configuring FSSO authentication on FortiGate using DC Agent Mode.
Which step is NOT part of the expected process?
- A . The DC agent sends login event data directly to FortiGate.
- B . The user logs into the windows domain.
- C . The collector agent forwards login event data to FortiGate.
- D . FortiGate determines user identity based on the IP address in the FSSO list.
C
Explanation:
In DC Agent Mode, the DC agent sends login event data directly to FortiGate without involving a collector agent.
On FortiGate, which type of logs record information about traffic directly to and from the FortiGate management IP addresses?
- A . Forward traffic logs
- B . Local traffic logs
- C . Security logs
- D . System event logs
B
Explanation:
Local traffic logs
Local traffic logs contain information about traffic directly to and from the FortiGate management IP addresses. They also include connections to the GUI and FortiGuard queries.
