Practice Free FCP_FGT_AD-7.6 Exam Online Questions
Refer to the exhibits.
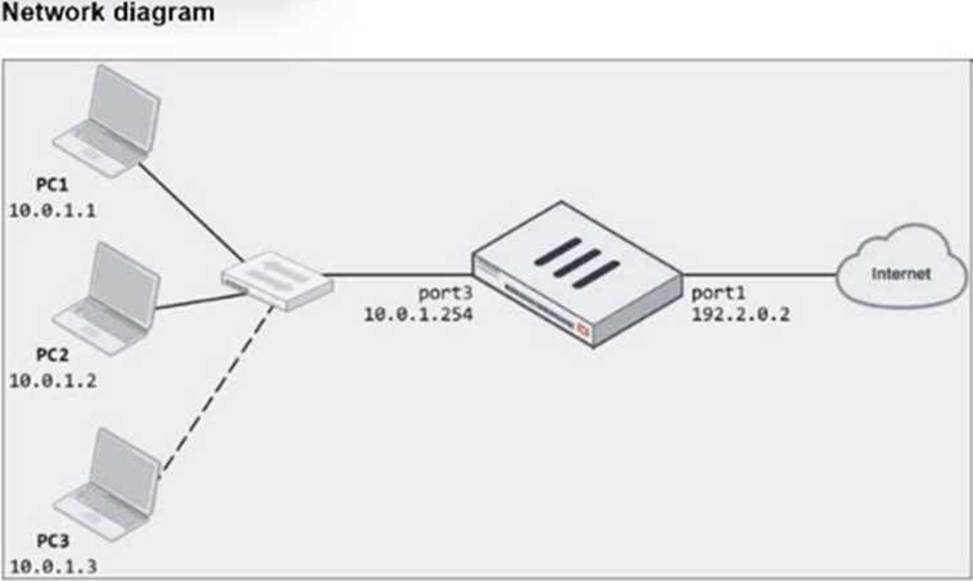
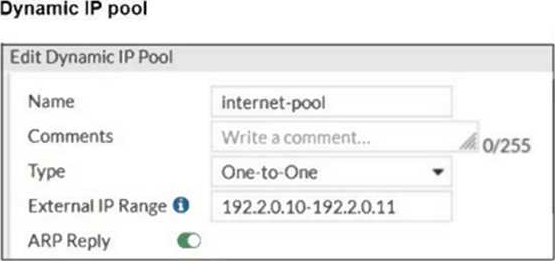
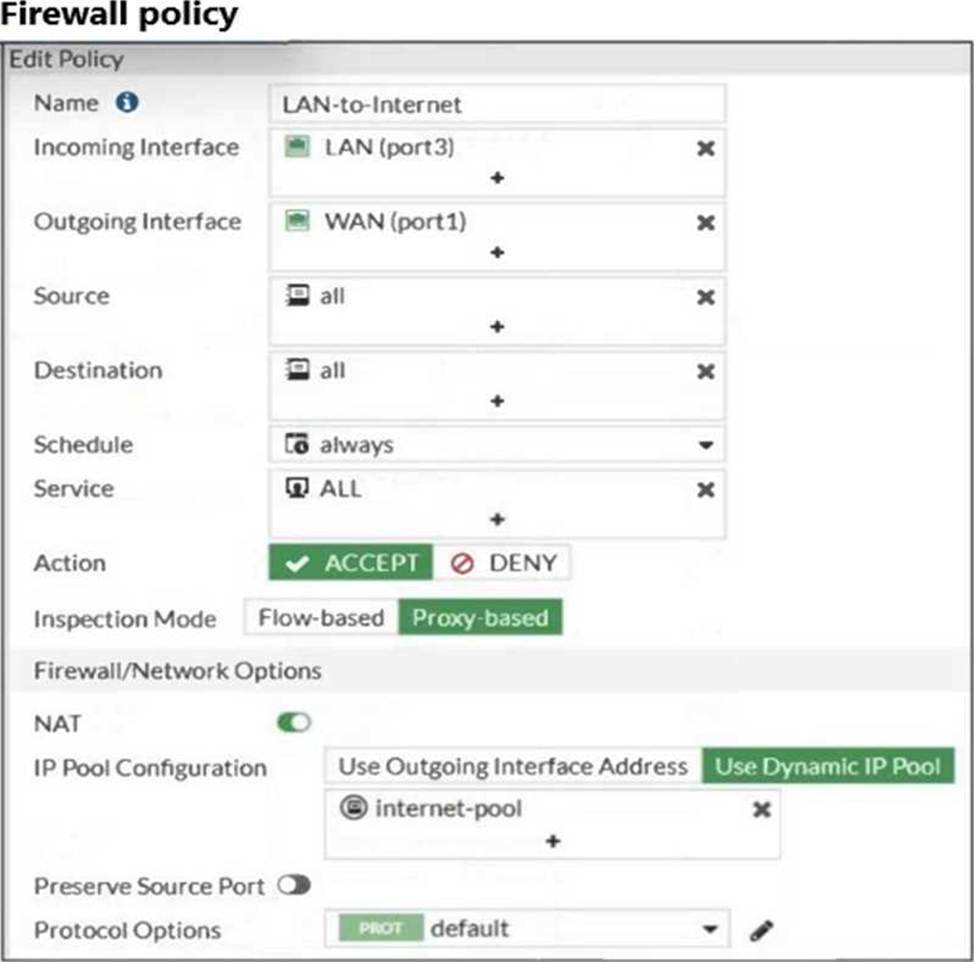
The exhibits show a diagram of a FortiGate device connected to the network, as well as the firewall policy and IP pool configuration on the FortiGate device.
Two PCs, PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet.
Based on the information shown in the exhibit, which two configuration options can the administrator use to fix the connectivity issue for PC3? (Choose two.)
- A . In the firewall policy configuration, add 10. o. l. 3 as an address object in the source field.
- B . In the IP pool configuration, set endig to 192.2.0.12.
- C . Configure another firewall policy that matches only the address of PC3 as source, and then place the policy on top of the list.
- D . In the IP pool configuration, set cype to overload.
B, D
Explanation:
To resolve the issue of PC3 not being able to access the internet, the administrator needs to adjust the IP pool configuration or the firewall policy.
The following two options will fix the connectivity issue:
B. In the IP pool configuration, set the ending IP to 192.2.0.12: The current IP pool range is 192.2.0.10-192.2.0.11, which only provides two IP addresses for network address translation (NAT). To allow PC3 to access the internet, the IP pool should be expanded to include an additional IP address by changing the end of the range to 192.2.0.12.
D. In the IP pool configuration, set type to overload: Instead of using a one-to-one NAT, changing the type to overload will allow multiple internal addresses (such as PC1, PC2, and PC3) to share a single external IP address. This will solve the issue without needing additional public IP addresses. The other options are not suitable:
When configuring a firewall virtual wire pair policy, which following statement is true?
- A . Any number of virtual wire pairs can be included, as long as the policy traffic direction is the same.
- B . Only a single virtual wire pair can be included in each policy.
- C . Any number of virtual wire pairs can be included in each policy, regardless of the policy traffic direction settings.
- D . Exactly two virtual wire pairs need to be included in each policy.
C
Explanation:
Any number of virtual wire pairs can be included in each policy, regardless of the policy traffic direction settings.
We tested to create a policy. We can use any number of virtual wire pairs. We can select 3 options in traffic direction: in/out/both.
Firewall virtual wire pair policies can include more than a single virtual wire pair. This capability can streamline the policy management process by eliminating the need to create multiple, similar policies for each virtual wire pair. When creating or modifying a policy, you can select the traffic direction for each VWP included in the policy.
Which of statement is true about SSL VPN web mode?
- A . The external network application sends data through the VPN
- B . It assigns a virtual IP address to the client
- C . It supports a limited number of protocols
- D . The tunnel is up while the client is connected
C
Explanation:
C. It supports a limited number of protocols
SSL VPN web mode typically supports a limited number of protocols compared to the full SSL VPN tunnel mode. This limitation is due to the nature of web-based applications and the restrictions of running within a web browser.
Web mode requires only a web browser, but supports a limited number of protocols.
A is incorrect – External network applications running on the user’s PC cannot send data across the VPN.
C is correct – Web mode requires only a web browser, but supports a limited number of protocols.
Refer to the exhibit.
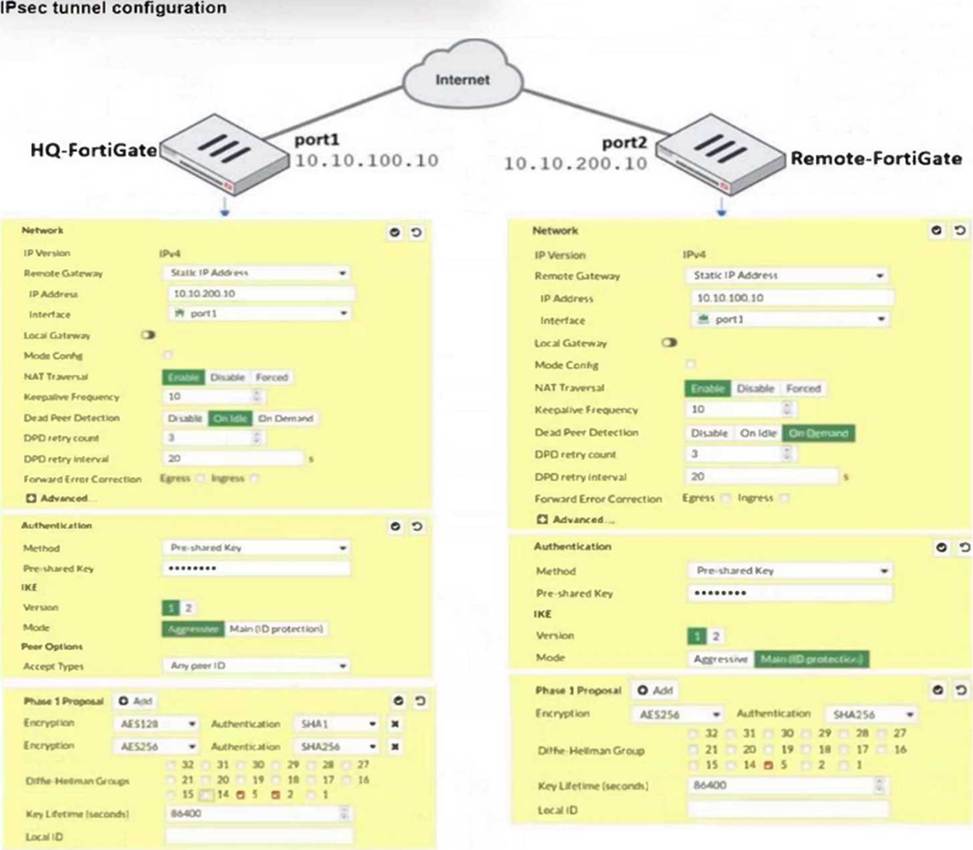
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 failed to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes can the administrator make to bring phase 1 up? (Choose two.)
- A . On HQ-FortiGate, disable Diffie-Helman group 2.
- B . On Remote-FortiGate, set port2 as Interface.
- C . On both FortiGate devices, set Dead Peer Detection to On Demand.
- D . On HQ-FortiGate, set IKE mode to Main (ID protection).
B, D
Explanation:
Based on the phase 1 configuration and the diagram shown in the exhibit, the administrator can make the following two configuration changes to bring phase 1 up:
B. On Remote-FortiGate, set port2 as Interface: The diagram indicates that port2 is currently not selected under ‘Interface’ for Remote-FortiGate. Aligning this setting with HQ-FortiGate, which has port1 set as Interface, might resolve inconsistencies.
D. On HQ-FortiGate, set IKE mode to Main (ID protection): The current setting on HQ-FortiGate is Aggressive for IKE mode, while Remote-FortiGate is set to Main mode. Matching these settings may help in establishing phase 1 of the IPsec tunnel.
Refer to the exhibit.

A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 failed to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes can the administrator make to bring phase 1 up? (Choose two.)
- A . On HQ-FortiGate, disable Diffie-Helman group 2.
- B . On Remote-FortiGate, set port2 as Interface.
- C . On both FortiGate devices, set Dead Peer Detection to On Demand.
- D . On HQ-FortiGate, set IKE mode to Main (ID protection).
B, D
Explanation:
Based on the phase 1 configuration and the diagram shown in the exhibit, the administrator can make the following two configuration changes to bring phase 1 up:
B. On Remote-FortiGate, set port2 as Interface: The diagram indicates that port2 is currently not selected under ‘Interface’ for Remote-FortiGate. Aligning this setting with HQ-FortiGate, which has port1 set as Interface, might resolve inconsistencies.
D. On HQ-FortiGate, set IKE mode to Main (ID protection): The current setting on HQ-FortiGate is Aggressive for IKE mode, while Remote-FortiGate is set to Main mode. Matching these settings may help in establishing phase 1 of the IPsec tunnel.
An administrator needs to inspect all web traffic (including Internet web traffic) coming from users connecting to the SSL-VPN.
How can this be achieved?
- A . Assigning public IP addresses to SSL-VPN users
- B . Configuring web bookmarks
- C . Disabling split tunneling
- D . Using web-only mode
C
Explanation:
The correct answer is: C. Disabling split tunneling
Split tunneling allows VPN users to access both local and remote networks simultaneously. However, if you want to inspect all web traffic, including Internet traffic, coming from users connecting to the SSL-VPN, you should disable split tunneling. Disabling split tunneling forces all user traffic through the VPN tunnel, allowing you to inspect and control the traffic more effectively.
Refer to the exhibit.
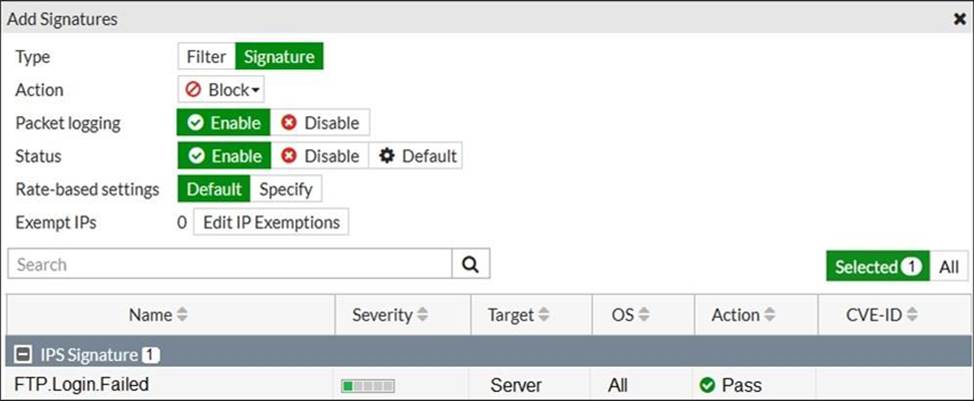
Review the Intrusion Prevention System (IPS) profile signature settings.
Which statement is correct in adding the FTP .Login.Failed signature to the IPS sensor profile?
- A . Traffic matching the signature will be silently dropped and logged.
- B . The signature setting uses a custom rating threshold.
- C . The signature setting includes a group of other signatures.
- D . Traffic matching the signature will be allowed and logged.
A
Explanation:
"pass" is only default action.
The Pass action on the specific signature would only be chosen, if the Action (on the top) was set to Default. But instead its set to Block, se the action is will be to block and drop.
Select Allow to allow traffic to continue to its destination. Select Monitor to allow traffic to continue to its destination and log the activity. Select Block to silently drop traffic matching any of the signatures included in the entry. Select Reset to generate a TCP RST packet whenever the signature is triggered. Select Default to use the default action of the signatures.
If you enable Packet logging, FortiGate saves a copy of the packet that matches the signature.
An administrator manages a FortiGate model that supports NTurbo.
How does NTurbo enhance performance for flow-based inspection?
- A . NTurbo offloads traffic to the content processor.
- B . NTurbo creates two inspection sessions on the FortiGate device.
- C . NTurbo buffers the whole file and then sends it to the antivirus engine.
- D . NTurbo creates a special data path to redirect traffic between the IPS engine its ingress and egress interfaces.
D
Explanation:
NTurbo enhances performance for flow-based inspection by offloading traffic to the content processor.
Refer to the exhibit.
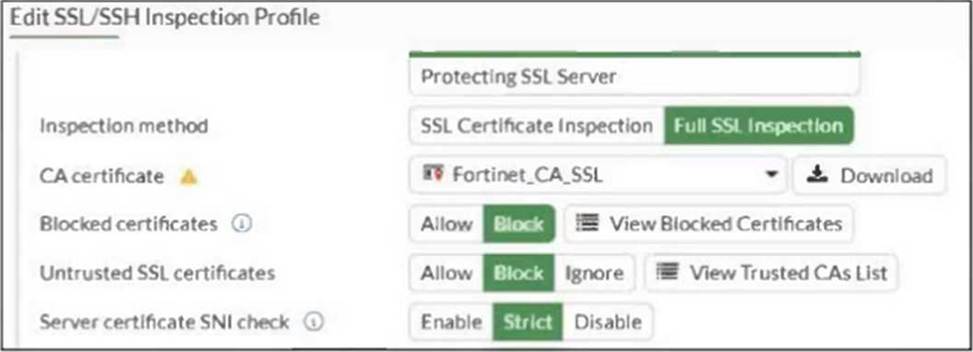
What would be the impact of these settings on the Server certificate SNI check configuration on FortiGate?
- A . FortiGate will accept and use the CN in the server certificate for URL filtering if the SNI does not match the CN or SAN fields.
- B . FortiGate will accept the connection with a warning if the SNI does not match the CN or SAN fields.
- C . FortiGate will close the connection if the SNI does not match the CN or SAN fields.
- D . FortiGate will close the connection if the SNI does not match the CN and SAN fields
D
Explanation:
With the Server certificate SNI check set to Strict, FortiGate enforces that the SNI must match either the Common Name (CN) or Subject Alternative Name (SAN) in the server certificate; otherwise, it closes the connection.
Refer to the exhibit.
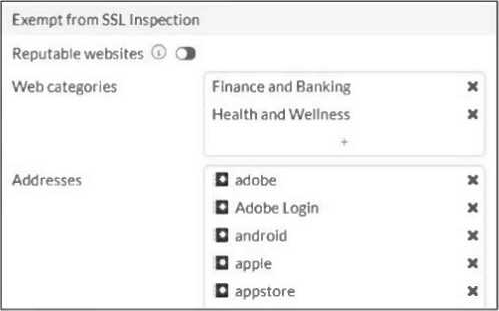
The predefined deep-inspection and custom-deep-inspection profiles exclude some web categories from SSL inspection, as shown in the exhibit.
For which two reasons are these web categories exempted? (Choose two.)
- A . The FortiGate temporary certificate denies the browser’s access to websites that use HTTP Strict Transport Security.
- B . These websites are in an allowlist of reputable domain names maintained by FortiGuard.
- C . The resources utilization is optimized because these websites are in the trusted domain list on FortiGate.
- D . The legal regulation aims to prioritize user privacy and protect sensitive information for these websites.
A, D
Explanation:
FortiGate’s temporary SSL certificate may cause access denial to sites using HTTP Strict Transport Security (HSTS), so such sites are exempted from deep SSL inspection.
Legal regulations require exemption of certain categories to protect user privacy and sensitive information, so these web categories are excluded from SSL inspection.
