Practice Free FCP_FGT_AD-7.6 Exam Online Questions
Refer to the exhibit.
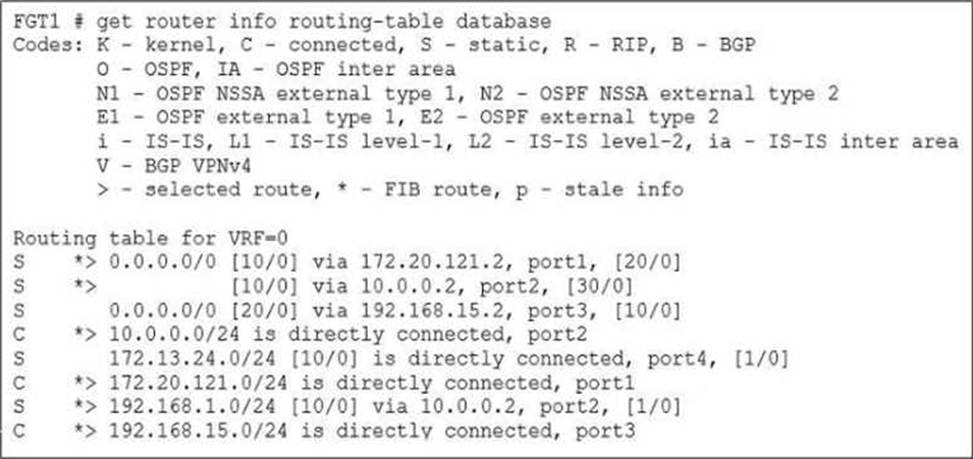
Based on the routing database shown in the exhibit which two conclusions can you make about the routes? (Choose two.)
- A . There will be eight routes active in the routing table
- B . The port1 and port2 default routes are active in the routing table
- C . The port3 default route has the highest distance
- D . The port3 default route has the lowest metric
B, C
Explanation:
The port1 and port2 default routes are active in the routing table
The routes with 0.0.0.0/0 for both port1 and port2 are marked with an asterisk * and > symbol, which indicates that these routes are active and selected in the routing table. The port3 default route has the highest distance
The route via port3 has a distance of [20/0], which is higher than the distances for the routes via port1 [10/0] and port2 [30/0]. This indicates that the port3 default route has the highest distance.
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
- A . It limits the scanning of application traffic to the browser-based technology category only.
- B . It limits the scanning of application traffic to the DNS protocol only.
- C . It limits the scanning of application traffic to use parent signatures only.
- D . It limits the scanning of application traffic to the application category only.
A
Explanation:
Which two statements are correct regarding FortiGate FSSO agentless polling mode? (Choose two.)
- A . FortiGate uses the AD server as the collector agent
- B . FortiGate uses the SMB protocol to read the event viewer logs from the DCs
- C . FortiGate points the collector agent to use a remote LDAP server
- D . FortiGate queries AD by using the LDAP to retrieve user group information
B,D
Explanation:
The two correct statements regarding FortiGate FSSO agentless polling mode are:
B. FortiGate uses the SMB protocol to read the event viewer logs from the DCs.
In agentless polling mode, FortiGate uses the Server Message Block (SMB) protocol to access and read event viewer logs from the Domain Controllers (DCs).
D. FortiGate queries AD by using the LDAP to retrieve user group information.
In agentless polling mode, FortiGate queries Active Directory (AD) using the Lightweight Directory Access Protocol (LDAP) to retrieve user group information. So, the correct choices are B and D.
Refer to the exhibit.
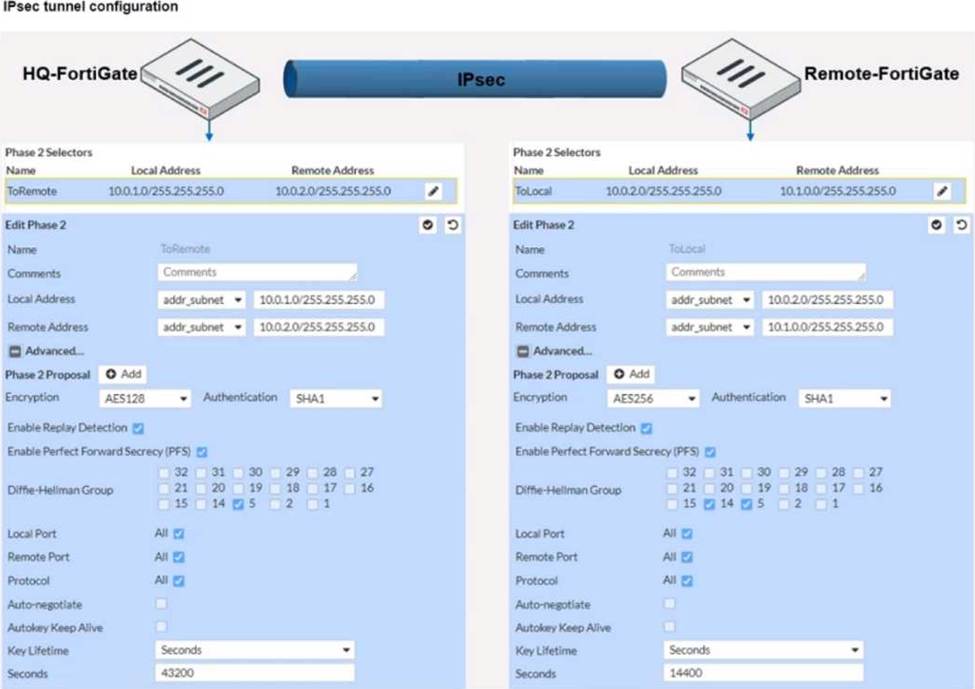
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 status is up, but phase 2 fails to come up.
Based on the phase 2 configuration shown in the exhibit, which two configuration changes will bring phase 2 up? (Choose two.)
- A . On Remote-FortiGate, set Seconds to 43200.
- B . On HQ-FortiGate, enable Diffie-Hellman Group 2.
- C . On HQ-FortiGate, set Encryption to AES256.
- D . On Remote-FortiGate, set Remote Address to 10.0.1.0/255.255.255.0.
Refer to the exhibit.
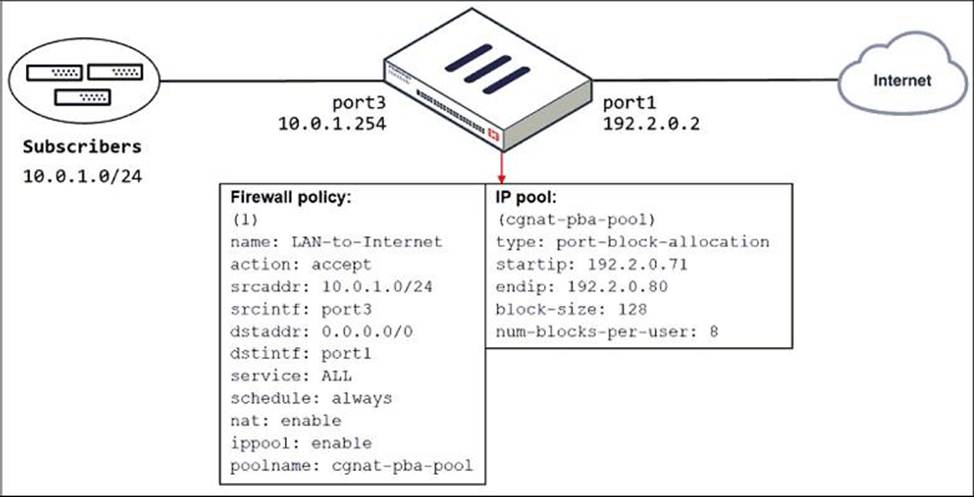
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)
- A . FortiGate allocates port blocks per user, based on the configured range of internal IP addresses.
- B . FortiGate allocates port blocks on a first-come, first-served basis.
- C . FortiGate generates a system event log for every port block allocation made per user.
- D . FortiGate allocates 128 port blocks per user.
B,C
Explanation:
B: FortiGate allocates port blocks on a first-come, first-served basis
C: For logging purposes, when FortiGate allocates a port block to a host, it generates a system event log to inform the administrator
Not A: FortiGate allocates a block size and number per host for a range of external addresses
Not D: It allows 8 blocks of 128 ports per host
FortiGate allocates port blocks on a first-come, first-served basis.
For logging purposes, when FortiGate allocates a port block to a host, it generates a system event log to inform the administrator.
Refer to the exhibit to view the application control profile.
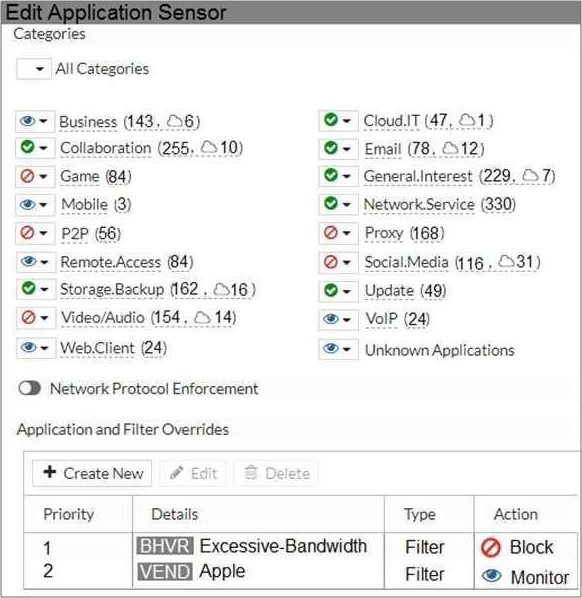
Users who use Apple FaceTime video conferences are unable to set up meetings.
In this scenario, which statement is true?
- A . Apple FaceTime belongs to the custom monitored filter.
- B . The category of Apple FaceTime is being monitored.
- C . Apple FaceTime belongs to the custom blocked filter.
- D . The category of Apple FaceTime is being blocked.
C
Explanation:
Apple FaceTime belongs to the custom blocked filter.
FaceTime categorized (filtered) under "Excessive-Bandwidth" and custom filter override set to block this.
Also we know that users can’t use FaceTime.
Apple FaceTime falls under (VoIP Catagory), (Excessive-Bandwidth Behavior) and (Vendor as Apple).
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and does not block the file, allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
- A . The website is exempted from SSL inspection.
- B . The EICAR test file exceeds the protocol options oversize limit.
- C . The selected SSL inspection profile has certificate inspection enabled.
- D . The browser does not trust the FortiGate self-signed CA certificate.
A,C
Explanation:
Two possible explanations for FortiGate’s failure to detect the virus are:
Refer to the exhibit.
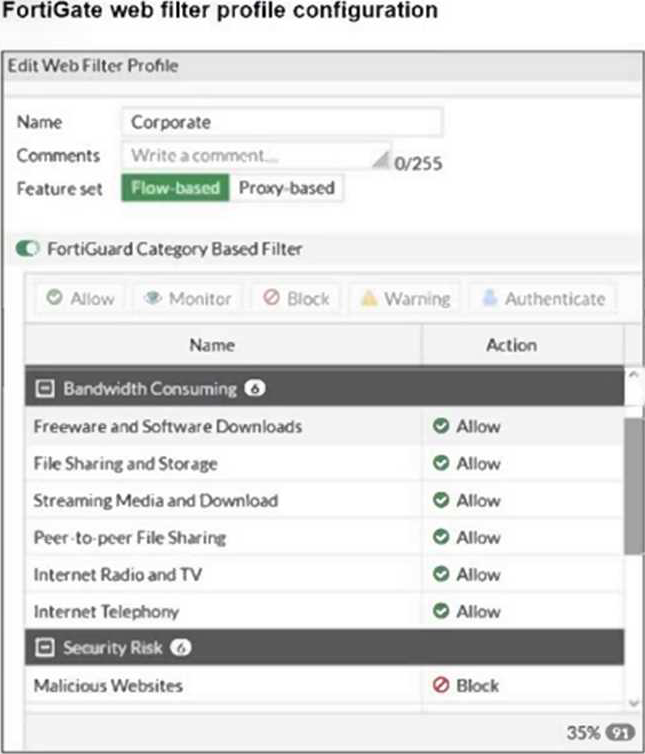
The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.
What are two solutions for satisfying the requirement? (Choose two.)
- A . Configure a separate firewall policy with action Deny and an FQDN address object for *. download, com as destination address.
- B . Set the Freeware and Software Downloads category Action to Warning
- C . Configure a web override rating for download, com and select Malicious Websites as the subcategory.
- D . Configure a static URL filter entry for download, com with Type and Action set to Wildcard and Block, respectively.
Refer to the exhibits.
An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).
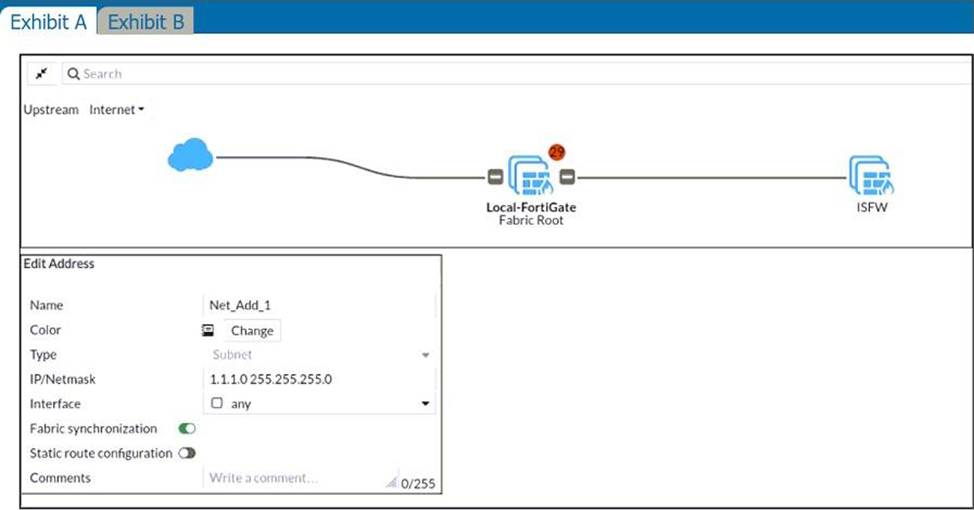
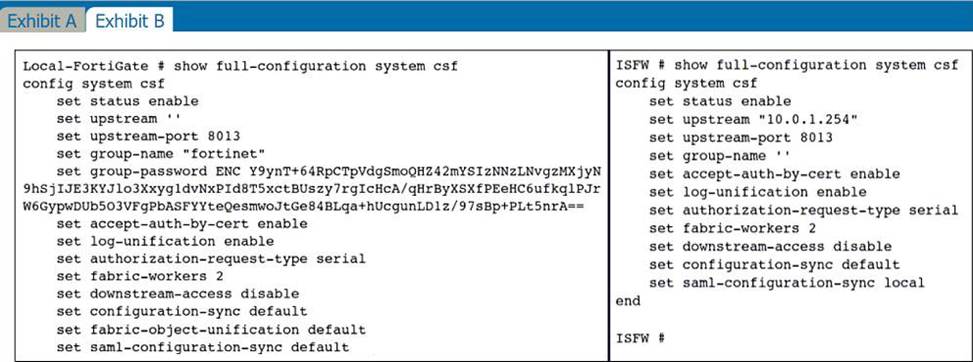
What must the administrator do to synchronize the address object?
- A . Change the csf setting on ISFW (downstream) to set configuration-sync local.
- B . Change the csf setting on ISFW (downstream) to set authorization-request-type certificate.
- C . Change the csf setting on both devices to set downstream-access enable.
- D . Change the csf setting on Local-FortiGate (root) to set fabric-object-unification default.
C
Explanation:
C is correct because D is already set to default (Global CMDB objects will be synchronized in Security Fabric.)
The root device has downstream access disabled, so it needs to be enabled to sync the object.
downstream-access – Enable/disable downstream device access to this device’s configuration and data.
disable – Disable downstream device access to this device’s configuration and data.
The CLI command "set fabric-object-unification" is only available on the root FortiGate.
Which statement regarding the firewall policy authentication timeout is true?
- A . It is an idle timeout. The FortiGate considers a user to be "idle" if it does not see any packets coming from the user’s source IP.
- B . It is a hard timeout. The FortiGate removes the temporary policy for a user’s source IP address after this timer has expired.
- C . It is an idle timeout. The FortiGate considers a user to be "idle" if it does not see any packets coming from the user’s source MAC.
- D . It is a hard timeout. The FortiGate removes the temporary policy for a user’s source MAC address
after this timer has expired.
A
Explanation:
