Practice Free FCP_FGT_AD-7.6 Exam Online Questions
If the Issuer and Subject values are the same in a digital certificate, to which type of entity was the certificate issued?
- A . A subordinate CA
- B . A root CA
- C . A user
- D . A CRL
B
Explanation:
If the Issuer and Subject values are the same in a digital certificate, it typically indicates that the certificate is a self-signed certificate.
Therefore, the correct answer is:
B. A root CA (Certificate Authority)
A self-signed certificate is one where the entity that issued the certificate is also the entity identified by the certificate. In the context of a Certificate Authority (CA), this is often referred to as a root CA certificate. Root CA certificates are at the top of the certificate hierarchy and are used to sign other certificates, creating a chain of trust in a Public Key Infrastructure (PKI).
Refer to the exhibit, which shows a partial configuration from the remote authentication server.

Why does the FortiGate administrator need this configuration?
- A . To authenticate only the Training user group.
- B . To set up a RADIUS server Secret
- C . To authenticate and match the Training OU on the RADIUS server.
- D . To authenticate Any FortiGate user groups.
A
Explanation:
The configuration shown in the exhibit indicates that the FortiGate is using a Fortinet-specific RADIUS attribute (Fortinet-Group-Name) with the value "Training." This setup allows the FortiGate to authenticate users against the RADIUS server and match them to the "Training" Organizational Unit (OU). By doing so, only users within this specific group or OU can be authenticated and allowed access through the FortiGate.
Reference: FortiOS 7.4.1 Administration Guide: RADIUS Server Configuration
Refer to exhibit.
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
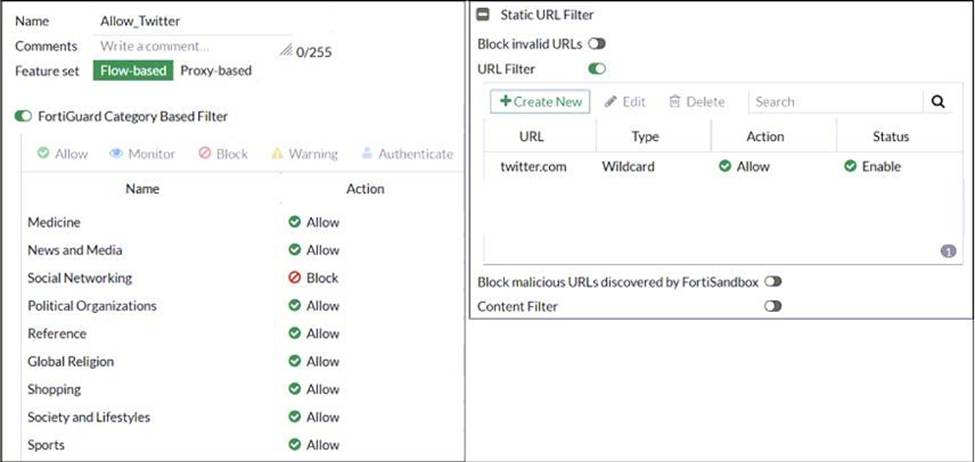
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
- A . On the FortiGuard Category Based Filter configuration, set Action to Warning for Social Networking.
- B . On the Static URL Filter configuration, set Type to Simple.
- C . On the Static URL Filter configuration, set Action to Exempt.
- D . On the Static URL Filter configuration, set Action to Monitor.
C
Explanation:
C. On the Static URL Filter configuration, set Action to Exempt.
Based on the exhibit, the administrator has configured the FortiGuard Category Based Filter to block access to all social networking sites, and has also configured a Static URL Filter to block access to twitter.com. As a result, users are being redirected to a block page when they try to access twitter.com.
To allow users to access twitter.com while blocking all other social networking sites, the administrator can make the following configuration change:
On the Static URL Filter configuration, set Action to Exempt: By setting the Action to Exempt, the administrator can override the block on twitter.com that was specified in the FortiGuard Category Based Filter. This will allow users to access twitter.com, while all other social networking sites will still be blocked.
Note:
Tested this in a lab environment and to make this work as stated in the question the Exempt action is the only way to go, and also *.twimg.com will has to be added to the URL Filter with an Exempt action for this situation to really work!
Allow: Access is permitted. Traffic is passed to remaining operations, including FortiGuard web filter, web content filter, web script filters, and antivirus scanning.
Exempt: Allows traffic from trusted sources to bypass all security inspections.
What are two features of the NGFW profile-based mode? (Choose two.)
- A . NGFW profile-based mode can only be applied globally and not on individual VDOMs.
- B . NGFW profile-based mode must require the use of central source NAT policy
- C . NGFW profile-based mode policies support both flow inspection and proxy inspection.
- D . NGFW profile-based mode supports applying applications and web filtering profiles in a firewall policy.
C, D
Explanation:
NGFW (Next Generation Firewall) profile-based mode in FortiGate allows policies to use both flow-based and proxy-based inspection modes, providing flexibility depending on security and performance requirements. Additionally, profile-based mode supports applying applications and web filtering profiles directly in a firewall policy, allowing granular control over the traffic.
Reference: FortiOS 7.4.1 Administration Guide: NGFW Mode Configuration
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
- A . Both interfaces must have the interface role assigned
- B . Both interfaces must have directly connected routes on the routing table
- C . Both interfaces must have DHCP enabled
- D . Both interfaces must have IP addresses assigned
B, D
Explanation:
Both interfaces must have directly connected routes on the routing table
In NAT mode, each interface must have a corresponding entry in the routing table, typically as a directly connected route, to route traffic between them effectively. Both interfaces must have IP addresses assigned
In NAT mode, each interface must have an IP address to participate in routing and NAT operations.
The IP addresses allow the FortiGate to forward traffic between different network segments.
In consolidated firewall policies, IPv4 and IPv6 policies are combined in a single consolidated policy.
Instead of separate policies.
Which three statements are true about consolidated IPv4 and IPv6 policy configuration? (Choose three.)
- A . The policy table in the GUI can be filtered to display policies with IPv4, IPv6 or IPv4 and IPv6 sources and destinations.
- B . The IP version of the sources and destinations in a firewall policy must be different.
- C . The Incoming Interface. Outgoing Interface. Schedule, and Service fields can be shared with both IPv4 and IPv6.
- D . The policy table in the GUI will be consolidated to display policies with IPv4 and IPv6 sources and destinations.
- E . The IP version of the sources and destinations in a policy must match.
C,D,E
Explanation:
C. The Incoming Interface, Outgoing Interface, Schedule, and Service fields can be shared with both IPv4 and IPv6.
This statement is true. In a consolidated IPv4 and IPv6 policy, these fields can be shared, making it more efficient to manage and configure policies.
D. The policy table in the GUI will be consolidated to display policies with IPv4 and IPv6 sources and destinations.
This statement is true. In consolidated firewall policies, the policy table in the graphical user interface (GUI) is consolidated to display policies with both IPv4 and IPv6 sources and destinations.
E. The IP version of the sources and destinations in a policy must match.
This statement is true. While certain fields can be shared, the IP version of the sources and destinations in a policy must match. If it’s an IPv4 policy, the sources and destinations must be IPv4, and if it’s an IPv6 policy, the sources and destinations must be IPv6.
So, statements C, D, and E are correct
Which two statements correctly describe auto discovery VPN (ADVPN)? (Choose two.)
- A . IPSec tunnels are negotiated dynamically between spokes.
- B . ADVPN is supported only with IKEv2.
- C . It recommends the use of dynamic routing protocols, so that spokes can learn the routes to other spokes.
- D . Every spoke requires a static tunnel to be configured to other spokes, so that phase 1 and phase 2
proposals are defined in advance.
A,C
Explanation:
The correct statements describing auto discovery VPN (ADVPN) are:
A team manager has decided that, while some members of the team need access to a particular website, the majority of the team does not.
Which configuration option is the most effective way to support this request?
- A . Implement web filter quotas for the specified website
- B . Implement a DNS filter for the specified website.
- C . Implement a web filter category override for the specified website
- D . Implement web filter authentication for the specified website.
D
Explanation:
Implement web filter authentication for the specified website.
Only some members can authenticated by providing their credentials.
– DNS filter & Web Filter Category Overide = Nobody can reach the site
– Web Filter Quotas = Everybody can reach
A could be a solution if you set custom categories and specify a webfilter to the group with access.. but B is the most efective and simple solution.
Since both C and D are working options, answer C needs one more Web filter profile – the one that will allow access to the category in which resides website’s domain name. In both cases a custom category is needed and a rating override, which will assign the website to that category. The question is "Which configuration option is the most effective way to support this request" in that case this is answer D
Refer to the exhibits.
Exhibit A shows system performance output.
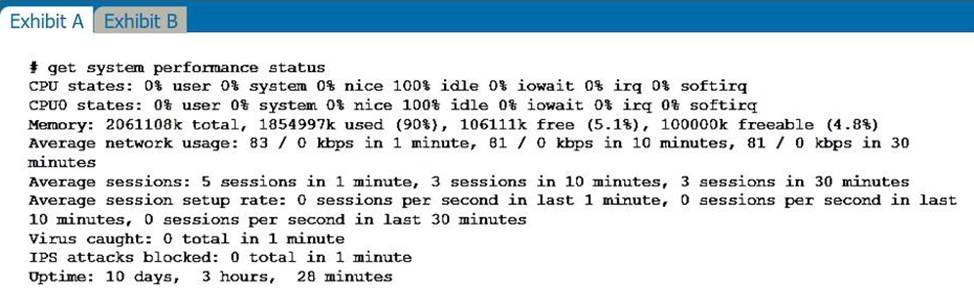
Exhibit B shows a FortiGate configured with the default configuration of high memory usage thresholds.

Based on the system performance output, which two results are correct? (Choose two.)
- A . FortiGate will start sending all files to FortiSandbox for inspection.
- B . FortiGate has entered conserve mode.
- C . Administrators cannot change the configuration.
- D . Administrators can access FortiGate only through the console port.
B,C
Explanation:
What actions does FortiGate take to preserve memory while in conserve mode?
• FortiGate does not accept configuration changes, because they might increase memory usage.
• FortiGate does not run any quarantine action, including forwarding suspicious files to FortiSandbox.
• You can configure the fail-open setting under config ips global to control how the IPS engine behaves when the IPS socket buffer is full.
Based on the system performance output, it appears that FortiGate has entered conserve mode and administrators cannot change the configuration.
FortiGate has entered conserve mode: When FortiGate enters conserve mode, it reduces its operational capacity in order to conserve resources and improve performance. This may be necessary if the system is experiencing high levels of traffic or if there are issues with resource utilization.
Administrators cannot change the configuration: When the system is in conserve mode, administrators may not be able to change the configuration. This is because the system is prioritizing resource conservation over other activities, and making changes to the configuration may require additional resources that are not available.
It is important to note that FortiGate will not start sending all files to FortiSandbox for inspection, and administrators may still be able to access FortiGate through other means besides the console port. "If memory usage goes above the percentage of total RAM defined as the red threshold, FortiGate enters conserve mode."
"FortiGate does not accept configuration changes, because they might increase memory usage."
Reference: https://community.fortinet.com/t5/FortiGate/Technical-Tip-How-conserve-mode-is-triggered/ta-p/198580
Which two IP pool types are useful for carrier-grade NAT deployments? (Choose two.)
- A . Port block allocation
- B . Fixed port range
- C . One-to-one
- D . Overload
A,B
Explanation:
The two IP pool types that are useful for carrier-grade NAT (CGNAT) deployments are:
