Practice Free FCP_FGT_AD-7.6 Exam Online Questions
Refer to the exhibits.
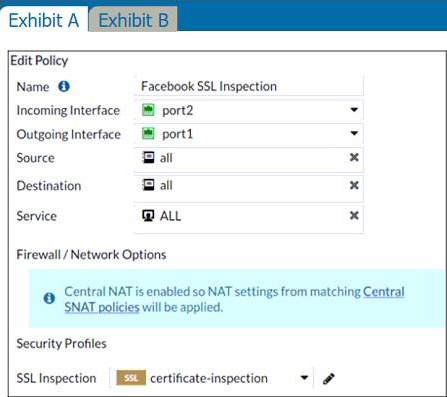
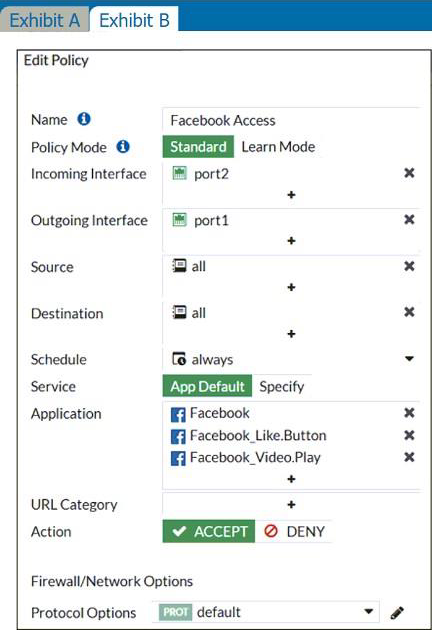
The exhibits show the SSL and authentication policy (Exhibit A) and the security policy (Exhibit B) for Facebook.
Users are given access to the Facebook web application. They can play video content hosted on Facebook, but they are unable to leave reactions on videos or other types of posts.
Which part of the policy configuration must you change to resolve the issue?
- A . Force access to Facebook using the HTTP service.
- B . Make the SSL inspection a deep content inspection.
- C . Add Facebook in the URL category in the security policy.
- D . Get the additional application signatures required to add to the security policy.
B
Explanation:
Needs SSL full inspection.
They can play video (tick) content hosted on Facebook, but they are unable to leave reactions on videos or other types of posts.
This indicate that the rule are partially working as they can watch video but can’t react, i.e. liking the content. So, must be an issue with the SSL inspection rather then adding an app rule.
The lock logo behind Facebook_like.Button indicates that SSL Deep Inspection is Required. All other Application Signatures Facebook and Facebook_Video.Play does not require SSL inspection. Hence that the users can play video content. If you look up the Application Signature for Facebook_like.Button it will say "Requires SSL Deep Inspection".
FortiGate needs to perform full SSL inspection. Without full SSL inspection, FortiGate cannot inspect encrypted traffic.
When FortiGate performs SSL/SSH full inspection, you can decide how it should react when it detects an invalid certificate.
Which three actions are valid actions that FortiGate can perform when it detects an invalid certificate? (Choose three.)
- A . Allow & Warning
- B . Trust & Allow
- C . Allow
- D . Block & Warning
- E . Block
B,C,E
Explanation:
When FortiGate performs SSL/SSH full inspection and detects an invalid certificate, there are three valid actions it can take:
Allow & Warning: This action allows the session but generates a warning.
Block & Warning: This action blocks the session and generates a warning.
Block: This action blocks the session without generating a warning.
Actions such as "Trust & Allow" or just "Allow" without additional configurations are not applicable in the context of handling invalid certificates.
Reference: FortiOS 7.4.1 Administration Guide: Configuring SSL/SSH inspection profile
Which two statements are true regarding FortiGate HA configuration synchronization? (Choose two.)
- A . Checksums of devices are compared against each other to ensure configurations are the same.
- B . Incremental configuration synchronization can occur only from changes made on the primary FortiGate device.
- C . Incremental configuration synchronization can occur from changes made on any FortiGate device within the HA cluster
- D . Checksums of devices will be different from each other because some configuration items are not synced to other HA members.
A, C
Explanation:
In FortiGate HA (High Availability) configuration, checksums of device configurations are compared to ensure they are synchronized and identical across the cluster. Incremental synchronization can only happen from changes made on the primary device to ensure consistency and integrity across the cluster members. Changes made on non-primary devices do not initiate synchronization.
Reference: FortiOS 7.4.1 Administration Guide: HA Configuration Synchronization
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile.
What order must FortiGate use when the web filter profile has features enabled, such as safe search?
- A . DNS-based web filter and proxy-based web filter
- B . Static URL filter, FortiGuard category filter, and advanced filters
- C . Static domain filter, SSL inspection filter, and external connectors filters
- D . FortiGuard category filter and rating filter
B
Explanation:
The correct order for the HTTP inspection process in web filtering, specifically when features like safe search are enabled in the web filter profile, is:
B. Static URL filter, FortiGuard category filter, and advanced filters
This means that the FortiGate device will first check against the Static URL filter, followed by the FortiGuard category filter, and then any additional advanced filters configured in the web filter profile. This sequence allows for a systematic evaluation of the URL against different criteria, ensuring comprehensive web filtering.
The HTTP Inspection Order (Static URL Filter -> FortiGuard Category Filter -> Advanced Filters)
Which two statements describe characteristics of automation stitches? (Choose two.)
- A . Actions involve only devices included in the Security Fabric.
- B . An automation stitch can have multiple triggers.
- C . Multiple actions can run in parallel.
- D . Triggers can involve external connectors.
C, D
Explanation:
Automation stitches can execute multiple actions concurrently (in parallel).
Triggers for automation stitches can come from external connectors beyond just Fortinet devices.
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
- A . udp-echo
- B . DNS
- C . TWAMP
- D . ping
A,C
Explanation:
The correct answers are:
Refer to the exhibit.
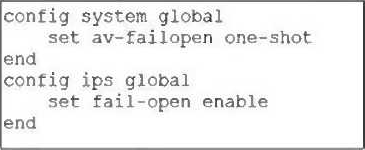
Based on this partial configuration, what are the two possible outcomes when FortiGate enters conserve mode? (Choose two.)
- A . Administrators cannot change the configuration.
- B . FortiGate skips quarantine actions.
- C . Administrators must restart FortiGate to allow new session.
- D . FortiGate drops new sessions requiring inspection.
B, D
Explanation:
In fail-open mode, FortiGate skips quarantine actions to maintain traffic flow despite IPS or antivirus failures.
FortiGate drops new sessions that require inspection when in conserve mode and fail-open is enabled, to protect the network from potentially harmful traffic.
You have configured an application control profile, set peer-to-peer traffic to Block under the Categories tab, and applied it to the firewall policy. However, your peer-to-peer traffic on known ports is passing through the FortiGate without being blocked.
What FortiGate settings should you check to resolve this issue?
- A . FortiGuard category ratings
- B . Application and Filter Overrides
- C . Network Protocol Enforcement
- D . Replacement Messages for UDP-based Applications
C
Explanation:
Network Protocol Enforcement settings control how FortiGate inspects and enforces protocols on traffic, including peer-to-peer applications on known ports. If not properly enabled, peer-to-peer traffic may bypass blocking despite the application control profile.
You have created a web filter profile named restrict_media-profile with a daily category usage quota.
When you are adding the profile to the firewall policy, the restrict_media-profile is not listed in the available web profile drop down.
What could be the reason?
- A . The firewall policy is in no-inspection mode instead of deep-inspection.
- B . The inspection mode in the firewall policy is not matching with web filter profile feature set.
- C . The web filter profile is already referenced in another firewall policy.
- D . The naming convention used in the web filter profile is restricting it in the firewall policy.
B
Explanation:
Web filter profiles with category usage quotas require the firewall policy to be in proxy-based (deep) inspection mode; if the inspection mode does not match this requirement, the profile will not appear in the drop-down list.
A FortiGate administrator is required to reduce the attack surface on the SSL VPN portal.
Which SSL timer can you use to mitigate a denial of service (DoS) attack?
- A . SSL VPN dcls-hello-timeout
- B . SSL VPN http-request-header-timeout
- C . SSL VPN login-timeout
- D . SSL VPN idle-timeout
B
Explanation:
The SSL VPN http-request-header-timeout timer is used to mitigate denial of service (DoS) attacks by limiting the amount of time the FortiGate waits for the client to send an HTTP request header after a connection is established. This helps reduce the attack surface by preventing potential attacks that exploit prolonged connection times without fully completing requests.
