Practice Free FCP_FCT_AD-7.2 Exam Online Questions
Refer to the exhibit.
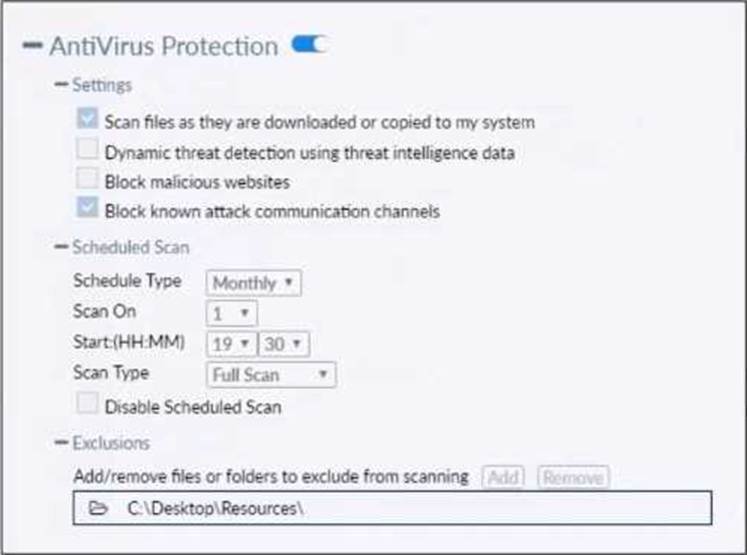
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
- A . FortiClient quarantines infected files and reviews later, after scanning them.
- B . FortiClient blocks and deletes infected files after scanning them.
- C . FortiClient scans infected files when the user copies files to the Resources folder
- D . FortiClient copies infected files to the Resources folder without scanning them.
A
Explanation:
Action On Virus Discovery Warn the User If a Process Attempts to Access Infected Files Quarantine Infected Files. You can use FortiClient to view, restore, or delete the quarantined file, as well as view the virus name, submit the file to FortiGuard, and view logs. Deny Access to Infected Files Ignore Infected Files
Which two statements are true about the ZTNA rule? (Choose two.)
- A . It applies security profiles to protect traffic
- B . It applies SNAT to protect traffic.
- C . It defines the access proxy.
- D . It enforces access control.
AD
Explanation:
Understanding ZTNA Rule Configuration:
The ZTNA rule configuration shown in the exhibit defines how traffic is managed and controlled based on specific tags and conditions.
Evaluating Rule Components:
The rule includes security profiles to protect traffic by applying various security checks (A).
The rule also enforces access control by determining which endpoints can access the specified resources based on the ZTNA tag (D).
Eliminating Incorrect Options:
SNAT (Source Network Address Translation) is not mentioned as part of this ZTNA rule. The rule does not define the access proxy but uses it to enforce access control. Conclusion:
The correct statements about the ZTNA rule are that it applies security profiles to protect traffic (A) and enforces access control (D).
Reference: ZTNA rule configuration documentation from the study guides.
An administrator needs to connect FortiClient EMS as a fabric connector to FortiGate.
What is the prerequisite to get FortiClient EMS lo connect to FortiGate successfully?
- A . Import and verify the FortiClient EMS tool CA certificate on FortiGate.
- B . Revoke and update the FortiClient client certificate on EMS.
- C . Import and verify the FortiClient client certificate on FortiGate.
- D . Revoke and update the FortiClient EMS root CA.
A
Explanation:
Connecting FortiClient EMS to FortiGate:
The administrator needs to establish a connection between FortiClient EMS and FortiGate as a fabric connector.
Prerequisites for Connection:
A key prerequisite is the import and verification of the FortiClient EMS tool CA certificate on
FortiGate to ensure a trusted connection.
Conclusion:
The correct prerequisite for a successful connection is to import and verify the FortiClient EMS tool
CA certificate on FortiGate.
Reference: FortiClient EMS and FortiGate connection and certificate management documentation from the study guides.
An administrator is required to maintain a software vulnerability on the endpoints, without showing the feature on the FortiClient.
What must the administrator do to achieve this requirement?
- A . Select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
- B . Disable select the vulnerability scan feature in the deployment package
- C . Click the hide icon on the vulnerability scan profile assigned to endpoint
- D . Use the default endpoint profile
C
Explanation:
Requirement Analysis:
The administrator needs to maintain a software vulnerability scan on endpoints without showing the feature on FortiClient.
Evaluating Options:
Disabling the feature in the deployment package or endpoint profile would remove the functionality entirely, which is not desired.
Using the default endpoint profile may not meet the specific requirement of hiding the feature. Clicking the hide icon on the vulnerability scan profile assigned to the endpoint will keep the feature active but hidden from the user’s view.
Conclusion:
The correct action is to click the hide icon on the vulnerability scan profile assigned to the endpoint (C).
Reference: FortiClient EMS feature configuration and management documentation from the study guides.
Which two VPN types can a FortiClient endpoint user inmate from the Windows command prompt? (Choose two)
- A . L2TP
- B . PPTP
- C . IPSec
- D . SSL VPN
C, D
Explanation:
FortiClient supports initiating the following VPN types from the Windows command prompt: IPSec VPN: FortiClient can establish IPSec VPN connections using command line instructions. SSL VPN: FortiClient also supports initiating SSL VPN connections from the Windows command prompt.
These two VPN types can be configured and initiated using specific command line parameters provided by FortiClient.
Reference
FortiClient EMS 7.2 Study Guide, VPN Configuration Section
Fortinet Documentation on Command Line Options for FortiClient VPN
An administrator installs FortiClient on Windows Server.
What is the default behavior of real-time protection control?
- A . Real-time protection must update AV signature database
- B . Real-time protection sends malicious files to FortiSandbox when the file is not detected locally
- C . Real-time protection is disabled
- D . Real-time protection must update the signature database from FortiSandbox
C
Explanation:
When FortiClient is installed on a Windows Server, the default behavior for real-time protection control is:
Real-time protection is disabled: By default, FortiClient does not enable real-time protection on server installations to avoid potential performance impacts and because servers typically have different security requirements compared to client endpoints.
Thus, real-time protection is disabled by default on Windows Server installations.
Reference
FortiClient EMS 7.2 Study Guide, Real-time Protection Section
Fortinet Documentation on FortiClient Default Settings for Server Installations
An administrator installs FortiClient on Windows Server.
What is the default behavior of real-time protection control?
- A . Real-time protection must update AV signature database
- B . Real-time protection sends malicious files to FortiSandbox when the file is not detected locally
- C . Real-time protection is disabled
- D . Real-time protection must update the signature database from FortiSandbox
C
Explanation:
When FortiClient is installed on a Windows Server, the default behavior for real-time protection control is:
Real-time protection is disabled: By default, FortiClient does not enable real-time protection on server installations to avoid potential performance impacts and because servers typically have different security requirements compared to client endpoints.
Thus, real-time protection is disabled by default on Windows Server installations.
Reference
FortiClient EMS 7.2 Study Guide, Real-time Protection Section
Fortinet Documentation on FortiClient Default Settings for Server Installations
Refer to the exhibit.
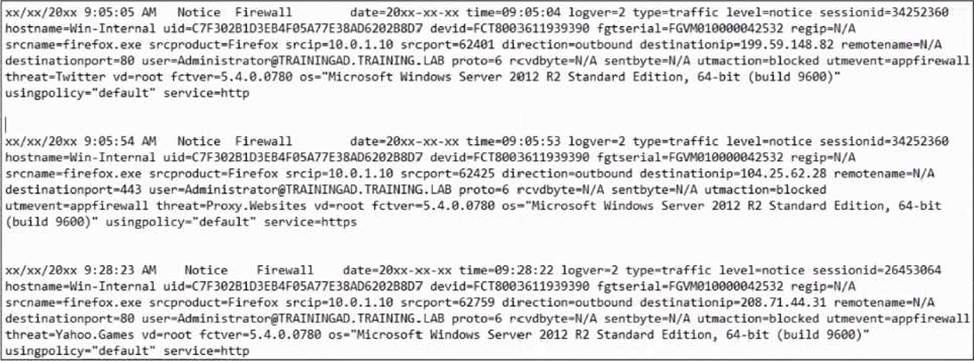
Based on the FortiClient logs shown in the exhibit which application is blocked by the application firewall?
- A . Twitter
- B . Facebook
- C . Internet Explorer
- D . Firefox
D
Explanation:
Based on the FortiClient logs shown in the exhibit:
The first log entry shows the application "firefox.exe" trying to access a destination IP, with the threat identified as "Twitter."
The action taken by the application firewall is "blocked" with the event type "appfirewall."
This indicates that the application firewall has blocked access to Twitter.
Reference
FortiClient EMS 7.2 Study Guide, Application Firewall Logs Section Fortinet Documentation on Interpreting FortiClient Logs
