Practice Free D-PDD-DY-23 Exam Online Questions
A backup administrator is tasked with verifying the compression savings of a PowerProtect DD3300
Which compression algorithm will they see enabled by default?
- A . LZ
- B . Gzfast
- C . LZW
- D . Gz
With DSP enabled on a PowerProtect DD appliance, which functions are performed on the backup host?
- A . Recording references to previous data and segmenting
- B . Segmenting fingerprinting, and sending the fingerprints
- C . Compressing segmenting, and fingerprinting
- D . Sending the data, segmenting, and compressing
What is the correct order for the DDOS Deduplication process?
- A . Compress, Filter, Fingerprint, and Segment
- B . Fingerprint, Segment, Filter, and Compress
- C . Segment, Fingerprint, Filter, and Compress
- D . Filter, Compress, Segment, and Fingerprint
A PowerProtect DD appliance with two expansion shelves is being installed in a customer-provided rack.
When cabling the controller to the shelves, what is connected to the host port on the last shelf in the chain?
- A . Expansion port of the upstream shelf
- B . Host port of the controller
- C . Expansion port of the controller
- D . Host port of the downstream shelf
For third-party backup applications that do not natively support DD Boost, where does the DD Boost plug-in need to be installed?
- A . On the backup server
- B . On each media server
- C . On the PowerProtect DD
- D . On each backup client
B
Explanation:
The DD Boost plug-in must be installed on each media server to enable optimized data deduplication and efficient data transfer, especially for applications that do not natively support DD Boost integration.
What is required to configure a cloud file system in a PowerProtect DD environment?
- A . Active tier encryption using the embedded Key Manager
- B . Active tier encryption using an external Key Manager
- C . Local store for a local copy of the cloud metadata
- D . Global store for a global copy of the cloud metadata
A customer needs a backup system to protect 100 TB of mission-critical data.
What should be used to back up the system?
- A . cloud tier
- B . DD6900
- C . DD3300
- D . DDVE
What is a key differentiator of Dell PowerProtect DD systems in terms of data handling during the write process?
- A . Data is deduplicated after it is written to disk.
- B . Data is encrypted after it is written to disk.
- C . Data is stored in its original format without any optimization.
- D . Data is deduplicated and encrypted inline as it is written to disk.
DRAG DROP
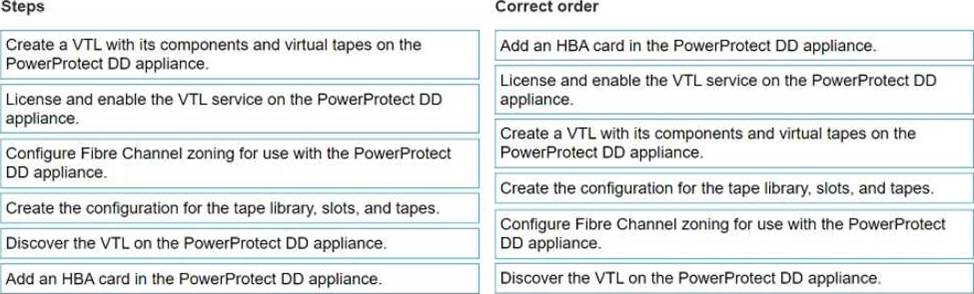
Which is the correct implementation order for a VTL environment?
Explanation:
The correct order for implementing a Virtual Tape Library (VTL) environment on a PowerProtect DD appliance is as follows:
Add an HBA card in the PowerProtect DD appliance.
License and enable the VTL service on the PowerProtect DD appliance.
Create a VTL with its components and virtual tapes on the PowerProtect DD appliance.
Create the configuration for the tape library, slots, and tapes.
Configure Fibre Channel zoning for use with the PowerProtect DD appliance.
Discover the VTL on the PowerProtect DD appliance.
Add an HBA Card: The Host Bus Adapter (HBA) card is required to connect the PowerProtect DD appliance to the Fibre Channel network, which is essential for the VTL configuration.
License and Enable VTL Service: The VTL functionality needs to be licensed and enabled on the PowerProtect DD appliance to allow the configuration of virtual tape drives and libraries.
Create the VTL: This involves setting up the virtual tape library components and creating virtual tapes on the appliance, establishing a simulated tape environment.
Configure Tape Library Settings: Set up the logical structure of the tape library, including the number of slots, tape drives, and tapes, as this information is critical for the backup application.
Configure Fibre Channel Zoning: Proper zoning must be configured in the Fibre Channel environment to ensure the backup servers can access the virtual tape drives and libraries on the PowerProtect DD appliance.
Discover the VTL: After setting up the environment, discover the VTL on the PowerProtect DD appliance to make it available for backup operations.
This ordered process ensures a structured and functional VTL setup within the PowerProtect DD environment, enabling optimized data protection workflows.
What is the result of using the filesys clean skip schedule estimate-percent-used 30 days 10 command?
- A . Cleaning is run every 10 days when the system is over 30% capacity.
- B . Cleaning is run every 10 days using no more than 30% system resources.
- C . Cleaning is run every 10 days using more than 30% system resources.
- D . Cleaning is run every 10 days when the system is under 30% capacity.
