Practice Free D-ISM-FN-01 Exam Online Questions
What is an accurate statement about a continuous data protection (CDP) remote replication solution?
- A . Write splitter is only implemented at the compute system running on the remote site
- B . Appliances are present at both the source and remote sites
- C . Replica and journal volume should be of the same size
- D . Journal and production volumes must be of the same size
Which process is represented in the graphic?
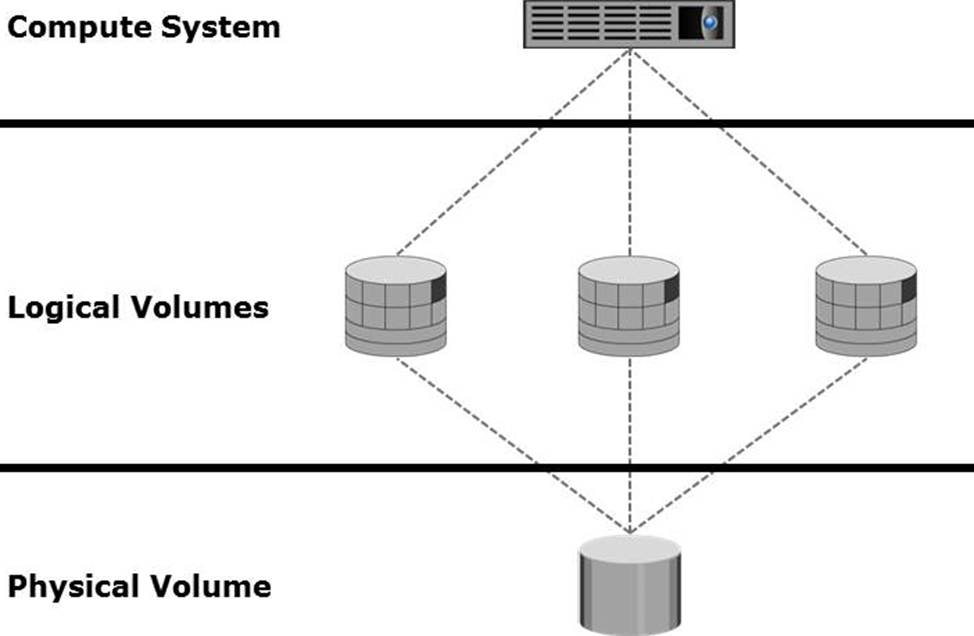
- A . Concatenation
- B . Partitioning
- C . Striping
- D . Shredding
An organization plans to deploy a new backup device in their data center. The organization wants the new backup device to support their legacy backup software without requiring any changes to the software. In addition, the organization wants the backup device to provide random data access for better performance.
Which backup device should be recommended?
- A . Virtual tape library
- B . Tape-based backup appliance
- C . Tape library
- D . Optical juke box
An organization performs a full back up every Sunday and incremental back ups on the remaining days at 9:00 AM. However, at 10 PM on Friday, a data corruption occurs that requires a data restoration from the backup copies.
How many backup copies are required to perform this restoration?
- A . 2
- B . 4
- C . 5
- D . 6
Which of the following are key characteristics of Big Data? (Choose two)
- A . Variety
- B . Velocity
- C . Veracity
- D . Vulnerability
Which security mechanism ensures secure access to internal assets while enabling Internet-based access to selected resources?
- A . Virtual local area network
- B . Demilitarized zone
- C . Virtual private network
- D . Discovery domain
What is provided by performing an infrastructure discovery?
- A . Creating a list of infrastructure components and their related information
- B . Classifying, organizing, and analyzing all infrastructure management best practices stored in data lakes
- C . Standardizing on-going infrastructure management activities to maintain the storage infrastructure using automation
- D . Gathering issues and tracking movement of data and services across the infrastructure
Which attack is carried out by sending a spoofing e-mail and redirecting a user to a false website?
- A . Phishing
- B . Man-in-the-middle
- C . Denial-of-service
- D . Repudiation
What accurately describes the scale-out storage architecture?
- A . Scales the capacity only within a single storage system.
- B . Provides a fixed capacity ceiling that limits scalability beyond a storage system.
- C . Provides the capability to maximize its capacity by adding nodes to the cluster.
- D . Restricts scalability to the limits of the storage controllers.
What is true about an iSCSI HBA?
- A . Requires a software adapter with built-in iSCSI functionality
- B . Enables transmission of data through iSCSI tunneling
- C . Requires CPU cycles for TCP/IP processing
- D . Performs both iSCSI and TCP/IP processing
