Practice Free CAS-005 Exam Online Questions
Question #101
Due to an infrastructure optimization plan, a company has moved from a unified architecture to a federated architecture divided by region. Long-term employees now have a better experience, but new employees are experiencing major performance issues when traveling between regions.
The company is reviewing the following information:
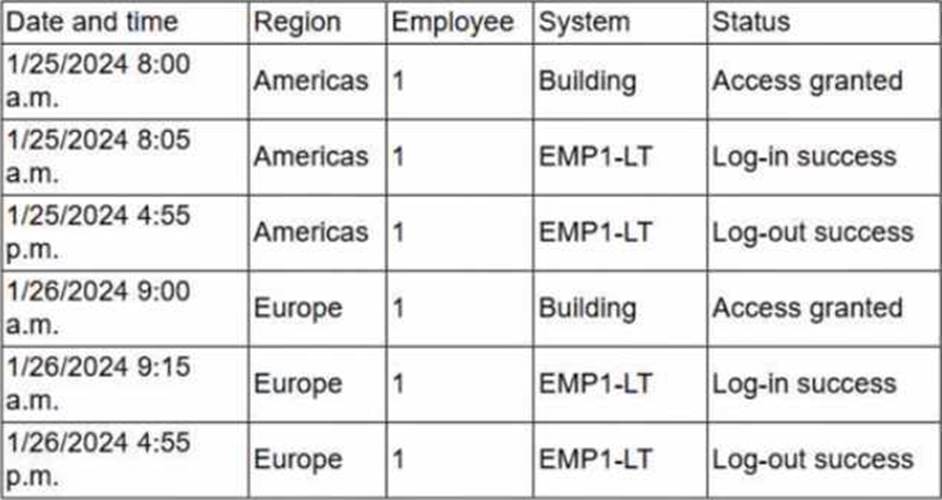
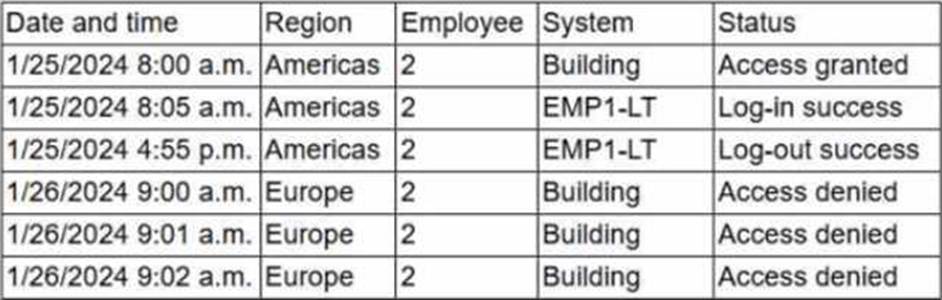
Which of the following is the most effective action to remediate the issue?
- A . Creating a new user entry in the affected region for the affected employee
- B . Synchronizing all regions* user identities and ensuring ongoing synchronization
- C . Restarting European region physical access control systems
- D . Resyncing single sign-on application with connected security appliances
Correct Answer: B
B
Explanation:
In a federated environment divided by region, if user identities are not synchronized across regions, authentication may be slow or fail when employees travel. CAS-005 IAM guidance states that identity synchronization ensures user attributes and credentials are consistently available in all regions, reducing latency and login issues.
Option A creates separate identities, which breaks single identity management.
Option C is unrelated to the login performance issue.
Option D may resolve SSO appliance sync but not cross-region identity data availability.
B
Explanation:
In a federated environment divided by region, if user identities are not synchronized across regions, authentication may be slow or fail when employees travel. CAS-005 IAM guidance states that identity synchronization ensures user attributes and credentials are consistently available in all regions, reducing latency and login issues.
Option A creates separate identities, which breaks single identity management.
Option C is unrelated to the login performance issue.
Option D may resolve SSO appliance sync but not cross-region identity data availability.
Question #102
Which of the following best describes a common use case for homomorphic encryption?
- A . Processing data on a server after decrypting in order to prevent unauthorized access in transit
- B . Maintaining the confidentiality of data both at rest and in transit to and from a CSP for processing
- C . Transmitting confidential data to a CSP for processing on a large number of resources without
revealing information - D . Storing proprietary data across multiple nodes in a private cloud to prevent access by unauthenticated users
Correct Answer: C
C
Explanation:
Homomorphic encryption allows computations to be performed directly on encrypted data without decrypting it first. This technology is particularly useful for securely transmitting confidential data to a cloud service provider (CSP) and allowing the CSP to process the data without having any visibility into its content. This maintains data confidentiality even during processing. It is not about securing data at rest and in transit or simply storing data across nodes.
Reference: CompTIA SecurityX CAS-005, Domain 3.0: Implement secure protocols and encryption technologies including homomorphic encryption for cloud and external processing.
C
Explanation:
Homomorphic encryption allows computations to be performed directly on encrypted data without decrypting it first. This technology is particularly useful for securely transmitting confidential data to a cloud service provider (CSP) and allowing the CSP to process the data without having any visibility into its content. This maintains data confidentiality even during processing. It is not about securing data at rest and in transit or simply storing data across nodes.
Reference: CompTIA SecurityX CAS-005, Domain 3.0: Implement secure protocols and encryption technologies including homomorphic encryption for cloud and external processing.
Question #103
A user reports application access issues to the help desk.
The help desk reviews the logs for the user
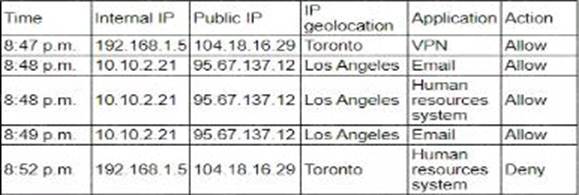
Which of the following is most likely the reason for the issue?
- A . The user inadvertently tripped the impossible travel security rule in the SSO system.
- B . A threat actor has compromised the user’s account and attempted to lop, m
- C . The user is not allowed to access the human resources system outside of business hours
- D . The user did not attempt to connect from an approved subnet
Correct Answer: A
A
Explanation:
Based on the provided logs, the user has accessed various applications from different geographic locations within a very short timeframe. This pattern is indicative of the "impossible travel" security rule, a common feature in Single Sign-On (SSO) systems designed to detect and prevent fraudulent access attempts.
Analysis of Logs:
At 8:47 p.m., the user accessed a VPN from Toronto.
At 8:48 p.m., the user accessed email from Los Angeles.
At 8:48 p.m., the user accessed the human resources system from Los Angeles.
At 8:49 p.m., the user accessed email again from Los Angeles.
At 8:52 p.m., the user attempted to access the human resources system from Toronto, which was denied.
These rapid changes in location are physically impossible and typically trigger security measures to prevent unauthorized access. The SSO system detected these inconsistencies and likely flagged the activity as suspicious, resulting in access denial.
Reference: CompTIA SecurityX Study Guide
NIST Special Publication 800-63B, "Digital Identity Guidelines"
"Impossible Travel Detection," Microsoft Documentation
A
Explanation:
Based on the provided logs, the user has accessed various applications from different geographic locations within a very short timeframe. This pattern is indicative of the "impossible travel" security rule, a common feature in Single Sign-On (SSO) systems designed to detect and prevent fraudulent access attempts.
Analysis of Logs:
At 8:47 p.m., the user accessed a VPN from Toronto.
At 8:48 p.m., the user accessed email from Los Angeles.
At 8:48 p.m., the user accessed the human resources system from Los Angeles.
At 8:49 p.m., the user accessed email again from Los Angeles.
At 8:52 p.m., the user attempted to access the human resources system from Toronto, which was denied.
These rapid changes in location are physically impossible and typically trigger security measures to prevent unauthorized access. The SSO system detected these inconsistencies and likely flagged the activity as suspicious, resulting in access denial.
Reference: CompTIA SecurityX Study Guide
NIST Special Publication 800-63B, "Digital Identity Guidelines"
"Impossible Travel Detection," Microsoft Documentation
