Practice Free CAS-005 Exam Online Questions
A security architect is designing Zero Trust enforcement policies for all end users. The majority of users work remotely and travel frequently for work.
Which of the following controls should the security architect do first?
- A . Switch user MFA from software-based tokens to hardware time-based OTPs.
- B . Implement TLS decryption and inspect inbound and outbound network traffic.
- C . Enforce daily posture compliance checks against the endpoint security controls.
- D . Deploy context-aware reauthentication with UBA baseline deviations.
D
Explanation:
Zero Trust security is based on the principle of “never trust, always verify.” For a mobile and frequently traveling workforce, enforcing rigid access models without adaptability creates friction and hampers productivity. The first priority in Zero Trust design for such a workforce is to deploy context-aware reauthentication combined with User Behavior Analytics (UBA). This ensures that deviations from baseline user behavior―such as unusual geographic access, time of day anomalies, or device changes―trigger additional authentication or session restrictions.
Option A (hardware OTPs) enhances authentication security but does not provide adaptive, risk-based controls for varying user behavior.
Option B (TLS decryption) focuses on network traffic inspection, which is important but secondary to ensuring identity and access enforcement in a Zero Trust model.
Option C (posture compliance checks) is necessary but typically part of ongoing device security enforcement rather than the initial step.
By starting with context-aware reauthentication, the organization ensures its Zero Trust strategy adapts dynamically to user behavior, providing both stronger security and a smoother experience for a global, remote workforce.
A security engineer receives an alert from the SIEM platform indicating a possible malicious action on the internal network.
The engineer generates a report that outputs the logs associated with the incident:
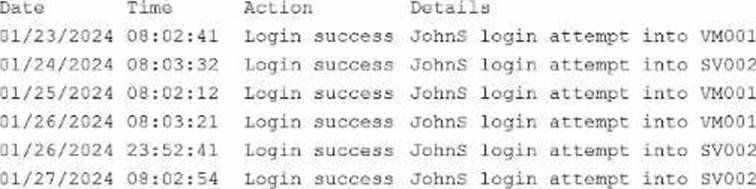
Which of the following actions best enables the engineer to investigate further?
- A . Consulting logs from the enterprise password manager
- B . Searching dark web monitoring resources for exposure
- C . Reviewing audit logs from privileged actions
- D . Querying user behavior analytics data
D
Explanation:
The best step is to query user behavior analytics (UBA) data. SIEM alerts provide potential security events, but without additional context, they may lead to false positives. UBA solutions detect anomalies by comparing user activity against baselines of normal behavior, highlighting unusual login patterns, lateral movement, or privilege escalation.
Option A (password manager logs) focuses only on credential use and lacks behavioral insight.
Option B (dark web monitoring) helps identify compromised accounts but does not investigate the internal incident.
Option C (audit logs for privileged actions) is useful but narrow in scope―it only covers administrator accounts.
By correlating SIEM data with UBA, the engineer can validate whether the flagged activity indicates real malicious behavior or benign anomalies. CAS-005 emphasizes advanced analytics integration (UEBA/UBA) to strengthen investigation and reduce false positives, making Option D the most effective choice.
A systems administrator wants to use existing resources to automate reporting from disparate security appliances that do not currently communicate.
Which of the following is the best way to meet this objective?
- A . Configuring an API Integration to aggregate the different data sets
- B . Combining back-end application storage into a single, relational database
- C . Purchasing and deploying commercial off the shelf aggregation software
- D . Migrating application usage logs to on-premises storage
A
Explanation:
The best way to automate reporting from disparate security appliances that do not currently communicate is to configure an API Integration to aggregate the different data sets.
Here’s why:
Interoperability: APIs allow different systems to communicate and share data, even if they were not originally designed to work together. This enables the integration of various security appliances into a unified reporting system.
Automation: API integrations can automate the process of data collection, aggregation, and reporting, reducing manual effort and increasing efficiency.
Scalability: APIs provide a scalable solution that can easily be extended to include additional security appliances or data sources as needed.
Reference: CompTIA Security+ SY0-601 Study Guide by Mike Chapple and David Seidl NIST Special Publication 800-95: Guide to Secure Web Services OWASP API Security Top Ten
While investigating an email server that crashed, an analyst reviews the following log files:
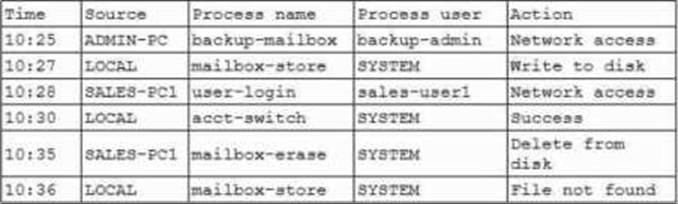
Which of the following is most likely the root cause?
- A . The administrator’s account credentials were intercepted and reused.
- B . The backup process did not complete and caused cascading failure.
- C . A hardware failure in the storage array caused the mailboxes to be inaccessible.
- D . A user with low privileges was able to escalate and erase all mailboxes.
A security analyst wants to use lessons learned from a poor incident response to reduce dwell lime in the future.
The analyst is using the following data points
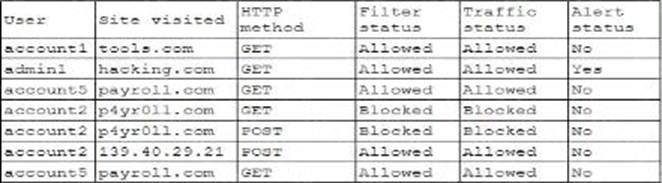
Which of the following would the analyst most likely recommend?
- A . Adjusting the SIEM to alert on attempts to visit phishing sites
- B . Allowing TRACE method traffic to enable better log correlation
- C . Enabling alerting on all suspicious administrator behavior
- D . utilizing allow lists on the WAF for all users using GFT methods
C
Explanation:
In the context of improving incident response and reducing dwell time, the security analyst needs to focus on proactive measures that can quickly detect and alert on potential security breaches.
Here’s a detailed analysis of the options provided:
A security engineer wants to reduce the attack surface of a public-facing containerized application.
Which of the following will best reduce the application’s privilege escalation attack surface?
- A . Implementing the following commands in the Dockerfile:RUN echo user:x:1000:1000iuser:/home/user:/dew/null > /ete/passwd
- B . Installing an EDR on the container’s host with reporting configured to log to a centralized SIFM and Implementing the following alerting rules TF PBOCESS_USEB=rooC ALERT_TYPE=critical
- C . Designing a muiticontainer solution, with one set of containers that runs the mam application, and another set oi containers that perform automatic remediation by replacing compromised containers or disabling compromised accounts
- D . Running the container in an isolated network and placing a load balancer in a public-facing network. Adding the following ACL to the load balancer: PZRKZI HTTES from 0-0.0.0.0/0 pert 443
A
Explanation:
Implementing the given commands in the Dockerfile ensures that the container runs with non-root user privileges. Running applications as a non-root user reduces the risk of privilege escalation attacks because even if anattacker compromises the application, they would have limited privileges and would not be able to perform actions that require root access.
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker’s lateral movement in a recent breach:
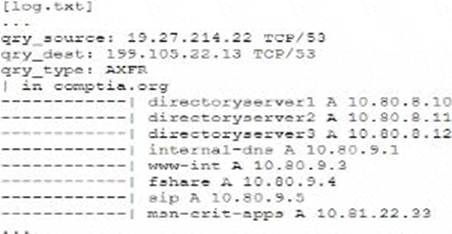
Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
- A . Disabling DNS zone transfers
- B . Restricting DNS traffic to UDP’W
- C . Implementing DNS masking on internal servers
- D . Permitting only clients from internal networks to query DNS
A
Explanation:
The log snippet indicates a DNS AXFR (zone transfer) request, which can be exploited by attackers to gather detailed information about an internal network’s infrastructure. Disabling DNS zone transfers is the best solution to mitigate this risk. Zone transfers should generally be restricted to authorized secondary DNS servers and not be publicly accessible, as they can reveal sensitive network information that facilitates lateral movement during an attack.
Reference: CompTIA SecurityX Study Guide: Discusses the importance of securing DNS configurations, including restricting zone transfers.
NIST Special Publication 800-81, "Secure Domain Name System (DNS) Deployment Guide":
Recommends restricting or disabling DNS zone transfers to prevent information leakage.
An external SaaS solution user reports a bug associated with the role-based access control module. This bug allows users to bypass system logic associated with client segmentation in the multitenant deployment model. When assessing the bug report, the developer finds that the same bug was previously identified and addressed in an earlier release. The developer then determines the bug was reintroduced when an existing software component was integrated from a prior version of the platform.
Which of the following is the best way to prevent this scenario?
- A . Regression testing
- B . Code signing
- C . Automated test and retest
- D . User acceptance testing
- E . Software composition analysis
A
Explanation:
Regression testing is a software testing practice that ensures that recent code changes have not adversely affected existing functionalities. In this scenario, the reintroduction of a previously fixed bug indicates that changes or integrations brought back the old issue. Implementing comprehensive regression testing would help detect such reintroductions by systematically retesting the existing functionalities whenever changes are made to the codebase. This practice is crucial in maintaining the integrity of the application, especially in complex systems where multiple components interact.
Reference: CompTIA SecurityX CAS-005 Official Study Guide, Chapter 8: "Software Development Security," Section 8.3: "Testing and Validation Processes."
During a periodic internal audit, a company identifies a few new, critical security controls that are missing.
The company has a mature risk management program in place, and the following requirements must be met:
The stakeholders should be able to see all the risks.
The risks need to have someone accountable for them.
Which of the following actions should the GRC analyst take next?
- A . Add the risk to the risk register and assign the owner and severity.
- B . Change the risk appetite and assign an owner to it.
- C . Mitigate the risk and change the status to accepted.
- D . Review the risk to decide whether to accept or reject it.
A
Explanation:
A risk register is a tool commonly used in risk management to document all identified risks, their assessment in terms of likelihood and impact, and the actions steps to manage them. By adding the newly identified risks to the risk register and assigning an owner and severity, the organization ensures that each risk is visible to stakeholders and has a designated individual responsible for its management. This aligns with the company’s requirements for transparency and accountability in risk management.
Reference: CompTIA SecurityX CAS-005 Official Study Guide, Chapter 6: "Risk Management," Section 6.4: "Risk Register and Risk Ownership."
An analyst wants to conduct a risk assessment on a new application that is being deployed.
Given the following information:
• Total budget allocation for the new application is unavailable.
• Recovery time objectives have not been set.
• Downtime loss calculations cannot be provided.
Which of the following statements describes the reason a qualitative assessment is the best option?
- A . The analyst has previous work experience in application development.
- B . Sufficient metrics are not available to conduct other risk assessment types.
- C . An organizational risk register tracks all risks and mitigations across business units.
- D . The organization wants to find the monetary value of any outages.
B
Explanation:
Qualitative risk assessment is used when quantitative data (monetary loss, exact downtime cost, RTO) is unavailable or unreliable. The SecurityX CAS-005 GRC objectives note that qualitative methods rely on expert judgment, likelihood scales, and impact ratings rather than financial calculations. In this case, insufficient metrics rule out quantitative analysis.
Option A (work experience) is irrelevant to the choice of assessment type.
Option C (risk register) supports tracking, not selecting the assessment method.
Option D describes a quantitative goal, which is not possible with the given lack of metrics.
