Practice Free CAS-004 Exam Online Questions
A security architect examines a section of code and discovers the following:
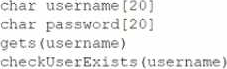
Which of the following changes should the security architect require before approving the code for release?
- A . Allow only alphanumeric characters for the username.
- B . Make the password variable longer to support more secure passwords.
- C . Prevent more than 20 characters from being entered.
- D . Add a password parameter to the checkUserExists function.
C
Explanation:
The code snippet presents a buffer size risk where the user input (username) is accepted without limiting the number of characters, potentially leading to buffer overflow vulnerabilities. The best solution is to implement input validation that limits the input to a maximum of 20 characters, matching the buffer size defined in the code. This prevents overflow attacks by ensuring that user input does not exceed the allocated memory space. Other options, like adding more parameters or allowing alphanumeric characters, do not directly address the root cause of buffer overflow vulnerabilities. CASP+ stresses the importance of proper input validation and bounds checking as critical security measures.
Reference: CASP+ CAS-004 Exam Objectives: Domain 2.0 C Enterprise Security Operations (Input Validation and Buffer Overflow Prevention)
CompTIA CASP+ Study Guide: Secure Coding Practices and Input Validation Techniques
A security team is concerned with attacks that are taking advantage of return-oriented programming against the company’s public-facing applications.
Which of the following should the company implement on the public-facing servers?
- A . IDS
- B . ASLR
- C . TPM
- D . HSM
B
Explanation:
Address Space Layout Randomization (ASLR) is a security feature that randomizes the memory addresses used by system and application processes, making return-oriented programming (ROP) attacks more difficult to exploit. ROP relies on predictable memory locations, and ASLR disrupts this predictability by randomizing memory locations at runtime. Implementing ASLR on public-facing servers helps mitigate this attack vector. CASP+ recommends leveraging memory protection mechanisms like ASLR to defend against advanced exploitation techniques like ROP.
Reference: CASP+ CAS-004 Exam Objectives: Domain 2.0 C Enterprise Security Operations (Memory Protection Mechanisms)
CompTIA CASP+ Study Guide: Memory Exploit Mitigations and ASLR
A company is moving most of its customer-facing production systems to the cloud-facing production systems to the cloud. IaaS is the service model being used. The Chief Executive Officer is concerned about the type of encryption available and requires the solution must have the highest level of security.
Which of the following encryption methods should the cloud security engineer select during the implementation phase?
- A . Instance-based
- B . Storage-based
- C . Proxy-based
- D . Array controller-based
B
Explanation:
We recommend that you encrypt your virtual hard disks (VHDs) to help protect your boot volume and data volumes at rest in storage, along with your encryption keys and secrets. Azure Disk Encryption helps you encrypt your Windows and Linux IaaS virtual machine disks. Azure Disk Encryption uses the industry-standard BitLocker feature of Windows and the DM-Crypt feature of Linux to provide volume encryption for the OS and the data disks. The solution is integrated with Azure Key Vault to help you control and manage the disk-encryption keys and secrets in your key vault subscription. The solution also ensures that all data on the virtual machine disks are encrypted at rest in Azure Storage. https://docs.microsoft.com/en-us/azure/security/fundamentals/iaas
A software development company is building a new mobile application for its social media platform. The company wants to gain its Users’ rust by reducing the risk of on-path attacks between the mobile client and its servers and by implementing stronger digital trust.
To support users’ trust, the company has released the following internal guidelines:
* Mobile clients should verify the identity of all social media servers locally.
* Social media servers should improve TLS performance of their certificate status.
* Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Select TWO).
- A . Quick UDP internet connection
- B . OCSP stapling
- C . Private CA
- D . DNSSEC
- E . CRL
- F . HSTS
- G . Distributed object model
B,F
Explanation:
OCSP stapling and HSTS are the best options to meet the requirements of reducing the risk of on-path attacks and implementing stronger digital trust. OCSP stapling allows the social media servers to improve TLS performance by sending a signed certificate status along with the certificate, eliminating the need for the client to contact the CA separately. HSTS allows the social media servers to inform the client to only use HTTPS and prevent downgrade attacks.
A penetration tester inputs the following command:
![]()
This command will allow the penetration tester to establish a:
- A . port mirror
- B . network pivot
- C . reverse shell
- D . proxy chain
C
Explanation:
The command depicted is indicative of a reverse shell, which is a type of shell where the target system initiates an outgoing connection to a remote host, and then standard input and output of the command line interface on the target system is redirected through this connection to the remote host. This is typically used by an attacker after exploitation to open a remote command line interface to control the compromised machine.
A systems engineer needs to develop a solution that uses digital certificates to allow authentication to laptops.
Which of the following authenticator types would be most appropriate for the engineer to include in the design?
- A . TOTP token
- B . Device certificate
- C . Smart card
- D . Biometric
B
Explanation:
Using digital certificates for authentication is a secure method to control access to laptops and other devices. A device certificate can serve as an authenticator by providing a means for the device to prove its identity in a cryptographic manner. This certificate-based authentication is commonly used in enterprise environments for strong authentication.
A company is rewriting a vulnerable application and adding the inprotect () system call in multiple parts of the application’s code that was being leveraged by a recent exploitation tool.
Which of the following should be enabled to ensure the application can leverage the new system call against similar attacks in the future?
- A . TPM
- B . Secure boot
- C . NX bit
- D . HSM
The findings from a recent penetration test report indicate a systematic issue related to cross-site scripting (XSS). A security engineer would like to prevent this type of issue for future reports.
Which of the following mitigation strategies should the engineer use to best resolve the issue?
- A . Implement static analysis with blocking capabilities in the CI/CD system.
- B . Request resources to develop a secure library to address encoding issues.
- C . Leverage an API management system to filter information.
- D . Configure a DAST tool for all applications.
- E . Require all developers to take secure coding training that focuses on OWASP principles.
E
Explanation:
Secure coding training focused on OWASP principlesis the most comprehensive long-term solution to address the root cause of XSS vulnerabilities by ensuring developers understand how to write secure code, including proper encoding and input validation.
Option A (Static analysis): This helps identify vulnerabilities in code but does not address the root
cause.
Option B (Secure library): While useful, it does not tackle inconsistent secure coding practices across the team.
Option C (API management): This is more relevant for API-related security but does not resolve broader XSS issues.
Option D (DAST tool): Dynamic testing identifies issues in runtime but does not prevent them in
development.
Reference: CompTIA CASP+ Exam Objective 4.1: Analyze application vulnerabilities and implement secure coding best practices.
CASP+ Study Guide, 5th Edition, Chapter 8, Secure Application Development.
A security analyst is configuring an IPSec tunnel to use the strongest encryption currently available.
Which of the following algorithms should be deployed to provide the most secure initial key exchange?
- A . 3DES
- B . ECDSA
- C . ECDH
- D . AES
After the latest risk assessment, the Chief Information Security Officer (CISO) decides to meet with the development and security teams to find a way to reduce the security task workload
The CISO would like to:
* Have a solution that uses API to communicate with other security tools
* Use the latest technology possible
* Have the highest controls possible on the solution
Which of following is the best option to meet these requirements?
- A . EDR
- B . CSP
- C . SOAR
- D . CASB
C
Explanation:
Security Orchestration, Automation, and Response (SOAR) solutions are designed to automate and streamline security operations in complex environments. By utilizing APIs, SOAR platforms can integrate with various security tools to enhance incident response processes, automate tasks, and improve overall efficiency. This aligns with the requirements of using the latest technology and having high control over the solution. SOAR’s ability to orchestrate between different security solutions and automate responses to threats makes it the best option to reduce the security task workload while maintaining high controls.
