Practice Free CAS-004 Exam Online Questions
A small business would like to provide guests who are using mobile devices encrypted WPA3 access without first distributing PSKs or other credentials.
Which of the following features will enable the business to meet this objective?
- A . Simultaneous Authentication of Equals
- B . Enhanced open
- C . Perfect forward secrecy
- D . Extensible Authentication Protocol
A cybersecurity analyst discovered a private key that could have been exposed.
Which of the following is the BEST way for the analyst to determine if the key has been compromised?
- A . HSTS
- B . CRL
- C . CSRs
- D . OCSP
C
Explanation:
Reference: https://www.ssl.com/faqs/compromised-private-keys/
Which of the following controls primarily detects abuse of privilege but does not prevent it?
- A . Off-boarding
- B . Separation of duties
- C . Least privilege
- D . Job rotation
A vulnerability assessment endpoint generated a report of the latest findings. A security analyst needs to review the report and create a priority list of items that must be addressed.
Which of the following should the analyst use to create the list quickly?
- A . Business impact rating
- B . CVE dates
- C . CVSS scores
- D . OVAL
In a shared responsibility model for PaaS, which of the following is a customer’s responsibility?
- A . Network security
- B . Physical security
- C . OS security
- D . Host infrastructure
C
Explanation:
In a shared responsibility model for PaaS, the customer’s responsibility is OS security. PaaS stands for Platform as a Service, which is a cloud service model that provides a platform for customers to develop, run, and manage applications without having to deal with the underlying infrastructure.
The cloud provider is responsible for the physical security, network security, and host infrastructure of the platform, while the customer is responsible for the security of the operating system, the application, and the data. The customer needs to ensure that the operating system is patched, configured, and protected from malware and unauthorized access.
Verified Reference:
https://learn.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
https://www.techtarget.com/searchcloudcomputing/feature/The-cloud-shared-responsibility-model-for-IaaS-PaaS-and-SaaS
https://www.splunk.com/en_us/blog/learn/shared-responsibility-model.html
A satellite communications ISP frequently experiences outages and degraded modes of operation over one of its legacy satellite links due to the use of deprecated hardware and software. Three days per week, on average, a contracted company must follow a checklist of 16 different high-latency commands that must be run in serial to restore nominal performance. The ISP wants this process to be automated.
Which of the following techniques would be BEST suited for this requirement?
- A . Deploy SOAR utilities and runbooks.
- B . Replace the associated hardware.
- C . Provide the contractors with direct access to satellite telemetry data.
- D . Reduce link latency on the affected ground and satellite segments.
A
Explanation:
Deploying SOAR (Security Orchestration Automation and Response) utilities and runbooks is the best technique for automating the process of restoring nominal performance on a legacy satellite link due to degraded modes of operation caused by deprecated hardware and software.
Users from the marketing department (192.168.0.1/24) are reporting performance issues with an on-premises application server (192.168.0.9). The application server should only be accessed internally.
A security analyst reviews various logs and finds the following information:
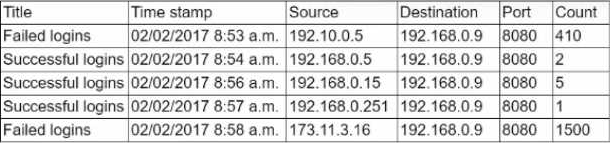
Which of the following should the security analyst perform next to improve performance and ensure the application server is secured as required?
- A . Configure NGFW to deny access from subnets not in 192.168.0.0/24.
- B . Modify the cloud security group rules to deny all external traffic to 192.168.0.9.
- C . Update the IDS/IPS software with the latest OS/firmware to ensure all brute-force attacks are prevented.
- D . Update the DLP system to include policies for data exfiltration attempts on the application server.
A system administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server.
Which of the following steps should the administrator take NEXT?
- A . Isolate all of the PHI on its own VLAN and keep it segregated at Layer 2.
- B . Take an MD5 hash of the server.
- C . Delete all PHI from the network until the legal department is consulted.
- D . Consult the legal department to determine the legal requirements.
An organization is assessing the security posture of a new SaaS CRM system that handles sensitive PI I and identity information, such as passport numbers. The SaaS CRM system does not meet the organization’s current security standards.
The assessment identifies the following:
1) There will be a 520,000 per day revenue loss for each day the system is delayed going into production.
2) The inherent risk is high.
3) The residual risk is low.
4) There will be a staged deployment to the solution rollout to the contact center.
Which of the following risk-handling techniques will BEST meet the organization’s requirements?
- A . Apply for a security exemption, as the risk is too high to accept.
- B . Transfer the risk to the SaaS CRM vendor, as the organization is using a cloud service.
- C . Accept the risk, as compensating controls have been implemented to manage the risk.
- D . Avoid the risk by accepting the shared responsibility model with the SaaS CRM provider.
A security architect is improving a healthcare organization’s security posture. Most of the software is cloud-based, but some old applications are still running on a server on-site. Medical devices using such applications require very low latency. The most important consideration isconfidentiality, followed byavailability, and thenintegrity.
Which of the following is thefirst stepthe security architect should implement to protect PII?
- A . Move the application server to a network load balancing cluster.
- B . Move the application to a CSP.
- C . Enable encryption at rest on medical devices.
- D . Install FIM on the application server.
C
Explanation:
Comprehensive and Detailed in-Depth
Context:
Confidentialityis the highest priority, as the primary goal is toprotect PII (Personally Identifiable Information).
Availabilityis the second priority, crucial due to thelow latency requirementof medical devices.
Integrityis the third priority, essential to maintain accurate patient data.
The environment consists ofon-site applicationsinteracting with medical devices, wherecloud migration is not feasibledue to latency concerns.
Why the Correct Answer is C (Enable encryption at rest on medical devices): Sinceconfidentialityis the top priority, enablingencryption at reston devices ensures thatsensitive data is protectedeven if the devices are compromised.
Medical devices can storePII locally, andencryption at restensures that even if physical or unauthorized access occurs, the data remainsconfidential.
Encrypting data at rest mitigates the risk of data leakage in scenarios likedevice theft or unauthorized access.
Given that the primary goal isconfidentiality, this action aligns with theCIA triadpriorities mentioned.
Why the Other Options Are Incorrect:
