Practice Free CAS-004 Exam Online Questions
A security architect is designing a solution for a new customer who requires significant security capabilities in its environment.
The customer has provided the architect with the following set of requirements:
* Capable of early detection of advanced persistent threats.
* Must be transparent to users and cause no performance degradation.
+ Allow integration with production and development networks seamlessly.
+ Enable the security team to hunt and investigate live exploitation techniques.
Which of the following technologies BEST meets the customer’s requirements for security capabilities?
- A . Threat Intelligence
- B . Deception software
- C . Centralized logging
- D . Sandbox detonation
B
Explanation:
Deception software is a technology that creates realistic but fake assets (such as servers, applications, data, etc.) that mimic the real environment and lure attackers into interacting with them. By doing so, deception software can help detect advanced persistent threats (APTs) that may otherwise evade traditional security tools12. Deception software can also provide valuable insights into the attacker’s tactics, techniques, and procedures (TTPs) by capturing their actions and behaviors on the decoys13.
Deception software can meet the customer’s requirements for security capabilities because:
It is capable of early detection of APTs by creating attractive targets for them and alerting security teams when they are engaged12.
It is transparent to users and causes no performance degradation because it does not interfere with legitimate traffic or resources13.
It allows integration with production and development networks seamlessly because it can create decoys that match the network topology and configuration13.
It enables the security team to hunt and investigate live exploitation techniques because it can record and analyze the attacker’s activities on the decoys13.
A recent data breach stemmed from unauthorized access to an employee’s company account with a cloud-based productivity suite. The attacker exploited excessive permissions granted to a third-party OAuth application to collect sensitive information.
Which of the following BEST mitigates inappropriate access and permissions issues?
- A . SIEM
- B . CASB
- C . WAF
- D . SOAR
C
Explanation:
Reference: https://www.cloudflare.com/en-gb/learning/ddos/glossary/web-application-firewall-waf/
Signed applications reduce risks by:
- A . encrypting the application’s data on the device.
- B . requiring the developer to use code-level hardening techniques.
- C . providing assurance that the application is using unmodified source code.
- D . costing the developer money to publish, which reduces the likelihood of malicious intent.
C
Explanation:
Signed applications ensure the integrity of the application by verifying that the source code has not been tampered with. Digital signatures provide a cryptographic guarantee that the software is exactly as the developer released it.
Which of the following is the reason why security engineers often cannot upgrade the security of embedded facility automation systems?
- A . They are constrained by available compute.
- B . They lack X86-64 processors.
- C . They lack EEPROM.
- D . They are not logic-bearing devices.
A
Explanation:
Embedded facility automation systems are often difficult to upgrade because they are constrained by available compute. These systems typically have limited processing power, memory, and storage, which restricts the ability to implement modern security measures, such as encryption, software updates, or advanced security controls. Security engineers may be unable to apply patches or updates without exceeding the system’s capacity. CASP+ discusses the challenges posed by resource-constrained devices, particularly in embedded systems and IoT environments, where upgrading security can be difficult due to hardware limitations.
Reference: CASP+ CAS-004 Exam Objectives: Domain 3.0 C Enterprise Security Architecture (Embedded System Security and Constraints)
CompTIA CASP+ Study Guide: Managing Security for Resource-Constrained Embedded Systems
A security analyst notices a number of SIEM events that show the following activity:
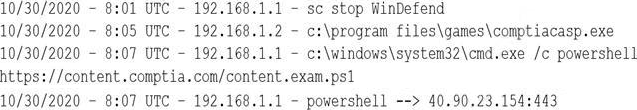
Which of the following response actions should the analyst take FIRST?
- A . Disable powershell.exe on all Microsoft Windows endpoints.
- B . Restart Microsoft Windows Defender.
- C . Configure the forward proxy to block 40.90.23.154.
- D . Disable local administrator privileges on the endpoints.
C
Explanation:
The SIEM events show that powershell.exe was executed on multiple endpoints with an outbound connection to 40.90.23.154, which is an IP address associated with malicious activity. This could indicate a malware infection or a command-and-control channel. The best response action is to configure the forward proxy to block 40.90.23.154, which would prevent further communication with the malicious IP address. Disabling powershell.exe on all endpoints may not be feasible or effective, as it could affect legitimate operations and not remove the malware. Restarting Microsoft Windows Defender may not detect or stop the malware, as it could have bypassed or disabled it. Disabling local administrator privileges on the endpoints may not prevent the malware from running or communicating, as it could have escalated privileges or used other methods.
Verified Reference:
https://www.comptia.org/blog/what-is-a-forward-proxy
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
As part of the customer registration process to access a new bank account, customers are required to upload a number of documents, including their passports and driver’s licenses. The process also requires customers to take a current photo of themselves to be compared against provided documentation.
Which of the following BEST describes this process?
- A . Deepfake
- B . Know your customer
- C . Identity proofing
- D . Passwordless
C
Explanation:
Reference: https://auth0.com/blog/what-is-identity-proofing-and-why-does-it-matter/
An IT administrator is reviewing all the servers in an organization and notices that a server is missing crucial practice against a recent exploit that could gain root access.
Which of the following describes the administrator’s discovery?
- A . A vulnerability
- B . A threat
- C . A breach
- D . A risk
A
Explanation:
Reference: https://www.beyondtrust.com/blog/entry/privilege-escalation-attack-defense-explained
A company hired a third party to develop software as part of its strategy to be quicker to market.
The company’s policy outlines the following requirements: https://i.postimg.cc/8P9sB3zx/image.png
The credentials used to publish production software to the container registry should be stored in a secure location.
Access should be restricted to the pipeline service account, without the ability for the third-party developer to read the credentials directly.
Which of the following would be the BEST recommendation for storing and monitoring access to these shared credentials?
- A . TPM
- B . Local secure password file
- C . MFA
- D . Key vault
D
Explanation:
Reference: https://docs.microsoft.com/en-us/windows/security/information-protection/tpm/tpm-fundamentals
A key vault is a service that provides secure storage and management of keys, secrets, and certificates. It can be used to store credentials used to publish production software to the container registry in a secure location, and restrict access to the pipeline service account without allowing the third-party developer to read the credentials directly. A TPM (trusted platform module) is a hardware device that provides cryptographic functions and key storage, but it is not suitable for storing shared credentials. A local secure password file is a file that stores passwords in an encrypted format, but it is not as secure or scalable as a key vault. MFA (multi-factor authentication) is a method of verifying the identity of a user or device by requiring two or more factors, but it does not store credentials.
Verified Reference:
https://www.comptia.org/blog/what-is-a-key-vault
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A company hired a third party to develop software as part of its strategy to be quicker to market.
The company’s policy outlines the following requirements: https://i.postimg.cc/8P9sB3zx/image.png
The credentials used to publish production software to the container registry should be stored in a secure location.
Access should be restricted to the pipeline service account, without the ability for the third-party developer to read the credentials directly.
Which of the following would be the BEST recommendation for storing and monitoring access to these shared credentials?
- A . TPM
- B . Local secure password file
- C . MFA
- D . Key vault
D
Explanation:
Reference: https://docs.microsoft.com/en-us/windows/security/information-protection/tpm/tpm-fundamentals
A key vault is a service that provides secure storage and management of keys, secrets, and certificates. It can be used to store credentials used to publish production software to the container registry in a secure location, and restrict access to the pipeline service account without allowing the third-party developer to read the credentials directly. A TPM (trusted platform module) is a hardware device that provides cryptographic functions and key storage, but it is not suitable for storing shared credentials. A local secure password file is a file that stores passwords in an encrypted format, but it is not as secure or scalable as a key vault. MFA (multi-factor authentication) is a method of verifying the identity of a user or device by requiring two or more factors, but it does not store credentials.
Verified Reference:
https://www.comptia.org/blog/what-is-a-key-vault
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
An organization has a secure manufacturing facility that is approximately 10mi (16km) away from its corporate headquarters. The organization’s management team is concerned about being able to track personnel who utilize the facility.
Which of the following would best help to prevent staff from being tracked?
- A . Ensuring that all staff use covered parking so they cannot be seen from outside the perimeter.
- B . Configuring geofencing to disable mobile devices and wearable devices near the secure facility.
- C . Constructing a tunnel between headquarters and the facility to allow more secure access.
- D . Enforcing physical security controls like access control vestibules and appropriate fencing.
B
Explanation:
Geofencing to disable mobile and wearable devices prevents the tracking of staff by disabling GPS and other location-based services. This measure aligns with CASP+ objective 3.2, which includes protecting sensitive facilities against surveillance and unauthorized tracking.
