Practice Free CAS-004 Exam Online Questions
loCs were missed during a recent security incident due to the reliance on a signature-based detection platform. A security engineer must recommend a solution that can be implemented to address this shortcoming.
Which of the following would be the most appropriate recommendation?
- A . FIM
- B . SASE
- C . UEBA
- D . CSPM
- E . EAP
An organization does not have visibility into when company-owned assets are off network or not connected via a VPN. The lack of visibility prevents the organization from meeting security and operational objectives.
Which of the following cloud-hosted solutions should the organization implement to help mitigate the risk?
- A . Antivirus
- B . UEBA
- C . EDR
- D . HIDS
C
Explanation:
Endpoint Detection and Response (EDR) solutions provide continuous monitoring and response to advanced threats. They can help mitigate the risk of not having visibility into off-network activities by detecting, investigating, and responding to suspicious activities on endpoints, regardless of their location.
A Chief Information Officer (CIO) wants to implement a cloud solution that will satisfy the following requirements:
Support all phases of the SDLC.
Use tailored website portal software.
Allow the company to build and use its own gateway software.
Utilize its own data management platform.
Continue using agent-based security tools.
Which of the following cloud-computing models should the CIO implement?
- A . SaaS
- B . PaaS
- C . MaaS
- D . IaaS
D
Explanation:
Reference: https://www.bmc.com/blogs/saas-vs-paas-vs-iaas-whats-the-difference-and-how-to-choose/
An employee’s device was missing for 96 hours before being reported. The employee called the help desk to ask for another device.
Which of the following phases of the incident response cycle needs improvement?
- A . Containment
- B . Preparation
- C . Resolution
- D . Investigation
B
Explanation:
The incident response cycle’s preparation phase includes establishing policies and procedures for reporting lost or stolen devices promptly. If an employee’s device was missing for 96 hours before being reported, this indicates a lack of awareness or clear procedures on the employee’s part, pointing to inadequacies in the preparation phase of the incident response.
A security analyst is reviewing the following output from a vulnerability scan from an organization’s internet-facing web services:
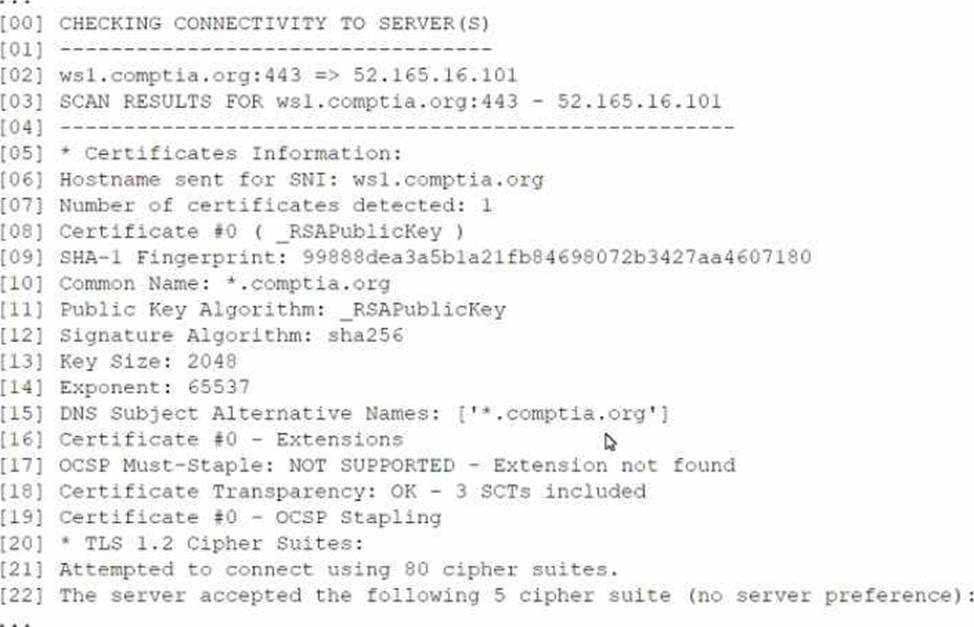
Which of the following indicates a susceptibility whereby an attacker can take advantage of the trust relationship between the client and the server?
- A . Line 06
- B . Line 10
- C . Line 13
- D . Line 17
A
Explanation:
The scan output in line 06 indicates that OCSP Must-Staple is not supported. This vulnerability exposes the application to attacks where an attacker can exploit the trust relationship between the client and the server by forging certificate revocation statuses. When OCSP stapling is not enforced, a client cannot reliably check if a certificate has been revoked, potentially allowing attackers to exploit this gap. CASP+ discusses the importance of certificate validation mechanisms such as OCSP (Online Certificate Status Protocol) to prevent man-in-the-middle and trust-exploiting attacks.
Reference: CASP+ CAS-004 Exam Objectives: Domain 2.0 C Enterprise Security Operations (Certificate Validation, OCSP)
CompTIA CASP+ Study Guide: Secure Web Services and Trust Relationships
Which of the following is record-level encryption commonly used to do?
- A . Protect database fields
- B . Protect individual files
- C . Encrypt individual packets
- D . Encrypt the master boot record
A
Explanation:
Record-level encryption is primarily used to protect sensitive information stored in specific fields within a database, such as personal data, financial information, or health records. This encryption method ensures that individual data entries are encrypted, providing a high level of security and privacy by making the data unreadable to unauthorized users or in the event of a database breach, while still allowing the database to be functional for authorized queries and operations.
A company wants to protect its intellectual property from theft. The company has already applied ACLs and DACs.
Which of the following should the company use to prevent data theft?
- A . Watermarking
- B . DRM
- C . NDA
- D . Access logging
B
Explanation:
DRM (digital rights management) is a technology that can protect intellectual property from theft by restricting the access, use, modification, or distribution of digital content or devices. DRM can use encryption, authentication, licensing, watermarking, or other methods to enforce the rights and permissions granted by the content owner or provider to authorized users or devices. DRM can prevent unauthorized copying, sharing, or piracy of digital content, such as software, music, movies, or books. Watermarking is not a technology that can protect intellectual property from theft by itself, but a technique that can embed identifying information or marks in digital content or media, such as images, audio, or video. Watermarking can help prove ownership or origin of digital content, but it does not prevent unauthorized access or use of it. NDA (non-disclosure agreement) is not a technology that can protect intellectual property from theft by itself, but a legal contract that binds parties to keep certain information confidential and not disclose it to unauthorized parties. NDA can help protect sensitive or proprietary information from exposure or misuse, but it does not prevent unauthorized access or use of it. Access logging is not a technology that can protect intellectual property from theft by itself, but a technique that can record the activities or events related to accessing data or resources. Access logging can help monitor or audit access to data or resources, but it does not prevent unauthorized access or use of them.
Verified Reference:
https://www.comptia.org/blog/what-is-drm
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A security administrator wants to detect a potential forged sender claim in tt-e envelope of an email.
Which of the following should the security administrator implement? (Select TWO).
- A . MX record
- B . DMARC
- C . SPF
- D . DNSSEC
- E . S/MIME
- F . TLS
B,C
Explanation:
DMARC (Domain-based Message Authentication, Reporting and Conformance) and SPF (Sender Policy Framework) are two mechanisms that can help detect and prevent email spoofing, which is the creation of email messages with a forged sender address. DMARC allows a domain owner to publish a policy that specifies how receivers should handle messages that fail authentication tests, such as SPF or DKIM (DomainKeys Identified Mail). SPF allows a domain owner to specify which mail servers are authorized to send email on behalf of their domain. By checking the DMARC and SPF records of the sender’s domain, a receiver can verify if the email is from a legitimate source or not.
Verified Reference:
https://en.wikipedia.org/wiki/Email_spoofing https://en.wikipedia.org/wiki/DMARC https://en.wikipedia.org/wiki/Sender_Policy_Framework
A security architect needs to enable a container orchestrator for DevSecOps and SOAR initiatives.
The engineer has discovered that several Ansible YAML files used for the automation of configuration management have the following content:
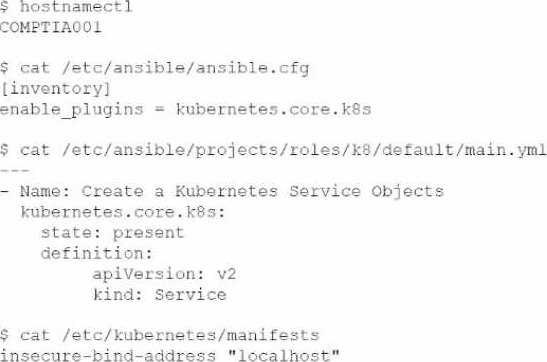
Which of the following should the engineer do to correct the security issues presented within this content?
- A . Update the kubernetes.core. k8s module to kubernetes.core.k8s_service in the main.yml file.
- B . Update the COMPTIACOI hostname to localhost using the hostnamectl command.
- C . Update the state: present module to state: absent in the main.yml file.
- D . Update or remove the ansible. cf g file.
Company A is merging with Company B Company A is a small, local company Company B has a large, global presence The two companies have a lot of duplication in their IT systems processes, and procedures On the new Chief Information Officer’s (ClO’s) first day a fire breaks out at Company B’s mam data center.
Which of the following actions should the CIO take first?
- A . Determine whether the incident response plan has been tested at both companies, and use it to respond
- B . Review the incident response plans, and engage the disaster recovery plan while relying on the IT leaders from both companies.
- C . Ensure hot. warm, and mobile disaster recovery sites are available, and give an update to the companies’ leadership teams
- D . Initiate Company A’s IT systems processes and procedures, assess the damage, and perform a BIA
B
Explanation:
In the event of a fire at the main data center, the immediate action should be to review and engage the disaster recovery plan. This is to ensure the continuity of business operations. The CIO should coordinate with IT leaders from both companies to ensure a unified response. Assessing the damage and planning for recovery are crucial, and leveraging the expertise from both companies can help streamline the process.
