Practice Free CAS-004 Exam Online Questions
A company’s Chief Information Security Officer wants to prevent the company from being the target of ransomware. The company’s IT assets need to be protected.
Which of the following are the most secure options to address these concerns? (Select three).
- A . Antivirus
- B . EDR
- C . Sand boxing
- D . Application control
- E . Host-based firewall
- F . IDS
- G . SIEM
- H . Strong authentication
B,C,D
Explanation:
To prevent ransomware attacks and protect IT assets, the most secure options are:
Endpoint Detection and Response (EDR): Provides advanced threat detection, real-time monitoring, and response capabilities, which can help identify and mitigate ransomware attacks before they spread.
Sandboxing: Isolates suspicious files or software in a controlled environment where they can be analyzed for malicious behavior without affecting production systems.
Application Control: Ensures that only whitelisted, trusted applications can run, which can prevent ransomware from executing unauthorized or malicious code.Together, these controls provide a robust defense against ransomware by addressing detection, isolation, and prevention. CASP+ emphasizes the importance of combining detection and prevention strategies to mitigate sophisticated attacks like ransomware.
Reference: CASP+ CAS-004 Exam Objectives: Domain 2.0 C Enterprise Security Operations (Endpoint Protection, Ransomware Mitigation)
CompTIA CASP+ Study Guide: Mitigating Ransomware with EDR, Sandboxing, and Application Control
The CI/CD pipeline requires code to have close to zero defects and zero vulnerabilities. The current process for any code releases into production uses two-week Agile sprints.
Which of the following would BEST meet the requirement?
- A . An open-source automation server
- B . A static code analyzer
- C . Trusted open-source libraries
- D . A single code repository for all developers
B
Explanation:
A static code analyzer is a tool that analyzes computer software without actually running the software. A static code analyzer can help developers find and fix vulnerabilities, bugs, and security risks in their new applications while the source code is in its ‘static’ state. A static code analyzer can help ensure that the code has close to zero defects and zero vulnerabilities by checking the code against a set of coding rules, standards, and best practices. A static code analyzer can also help improve the code quality, performance, and maintainability.
A company’s Chief Information Security Officer is concerned that the company’s proposed move to the cloud could lead to a lack of visibility into network traffic flow logs within the VPC.
Which of the following compensating controls would be BEST to implement in this situation?
- A . EDR
- B . SIEM
- C . HIDS
- D . UEBA
B
Explanation:
Reference: https://runpanther.io/cyber-explained/cloud-based-siem-explained/
A company is experiencing a large number of attempted network-based attacks against its online store.
To determine the best course of action, a security analyst reviews the following logs.
![]()
Which of the following should the company do next to mitigate the risk of a compromise from these attacks?
- A . Restrict HTTP methods.
- B . Perform parameterized queries.
- C . Implement input sanitization.
- D . Validate content types.
A
Explanation:
Restricting HTTP methods can mitigate the risk of network-based attacks against an online store by limiting the types of HTTP requests that the server will accept, thus reducing the attack surface. This is a common method to prevent web-based attacks such as Cross-Site Scripting (XSS) and SQL Injection.
A security architect is implementing a SOAR solution in an organization’s cloud production environment to support detection capabilities.
Which of the following will be the most likely benefit?
- A . Improved security operations center performance
- B . Automated firewall log collection tasks
- C . Optimized cloud resource utilization
- D . Increased risk visibility
A
Explanation:
SOAR solutions (Security Orchestration, Automation, and Response) are designed to help organizations efficiently manage security operations. They can automate the collection and analysis of security data, which improves the performance of a security operations center (SOC) by allowing the security team to focus on more strategic tasks and reduce response times to incidents.
Which of the following objectives BEST supports leveraging tabletop exercises in business continuity planning?
- A . Determine the optimal placement of hot/warm sites within the enterprise architecture.
- B . Create new processes for identified gaps in continuity planning.
- C . Establish new staff roles and responsibilities for continuity of operations.
- D . Assess the effectiveness of documented processes against a realistic scenario.
The results of an internal audit indicate several employees reused passwords that were previously included in a published list of compromised passwords.
The company has the following employee password policy:
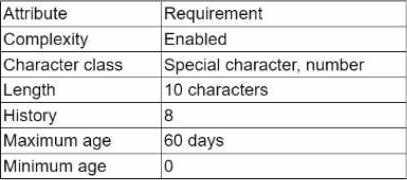
Which of the following should be implemented to best address the password reuse issue? (Select two).
- A . Increase the minimum age to two days.
- B . Increase the history to 20.
- C . Increase the character length to 12.
- D . Add case-sensitive requirements to character class.
- E . Decrease the maximum age to 30 days.
- F . Remove the complexity requirements
A company’s claims processed department has a mobile workforce that receives a large number of email submissions from personal email addresses. An employees recently received an email that approved to be claim form, but it installed malicious software on the employee’s laptop when was
opened.
- A . Impalement application whitelisting and add only the email client to the whitelist for laptop in the claims processing department.
- B . Required all laptops to connect to the VPN before accessing email.
- C . Implement cloud-based content filtering with sandboxing capabilities.
- D . Install a mail gateway to scan incoming messages and strip attachments before they reach the mailbox.
C
Explanation:
Implementing cloud-based content filtering with sandboxing capabilities is the best solution for preventing malicious software installation on the employee’s laptop due to opening an email attachment that appeared to be a claim form. Cloud-based content filtering is a technique that uses acloud service to filter or block web traffic based on predefined rules or policies, preventing unauthorized or malicious access to web resources or services. Cloud-based content filtering canprevent malicious software installation on the employee’s laptop due to opening an email attachment that appeared to be a claim form, as it can scan or analyze email attachments before they reach the mailbox and block or quarantine them if they are malicious. Sandboxing is a technique that uses an isolated or virtualized environment to execute or test suspicious or untrusted code or applications, preventing them from affecting the host system or network. Sandboxing can prevent malicious software installation on the employee’s laptop due to opening an email attachment that appeared to be a claim form, as it can run or detonate email attachments in a safe environment and observe their behavior or impact before allowing them to reach the mailbox. Implementing application whitelisting and adding only the email client to the whitelist for laptops in the claims processing department is not a good solution for preventing malicious software installation on the employee’s laptop due to opening an email attachment that appeared to be a claim form, as it could affect the usability or functionality of other applications on the laptops that may be needed for work purposes, as well as not prevent malicious software from running within the email client. Requiring all laptops to connect to the VPN (virtual private network) before accessing email is not a good solution for preventing malicious software installation on the employee’s laptop due to opening an email attachment that appeared to be a claim form, as it could introduce latency or performance issues for accessing email, as well as not prevent malicious software from reaching or executing on the laptops. Installing a mail gateway to scan incoming messages and strip attachments before they reach the mailbox is not a good solution for preventing malicious software installation on the employee’s laptop due to opening an email attachment that appeared to be a claim form, as it could affect the normal operations or functionality of email communication, as well as not prevent legitimate attachments from reaching the mailbox.
Verified Reference:
https://www.comptia.org/blog/what-is-cloud-based-content-filtering
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
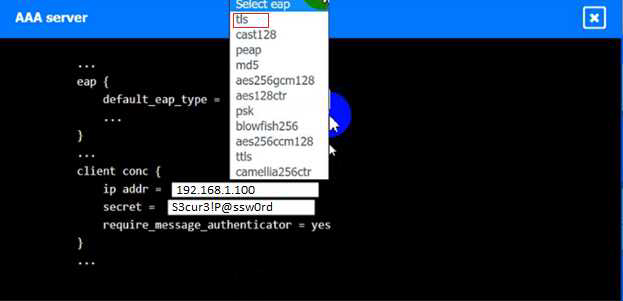
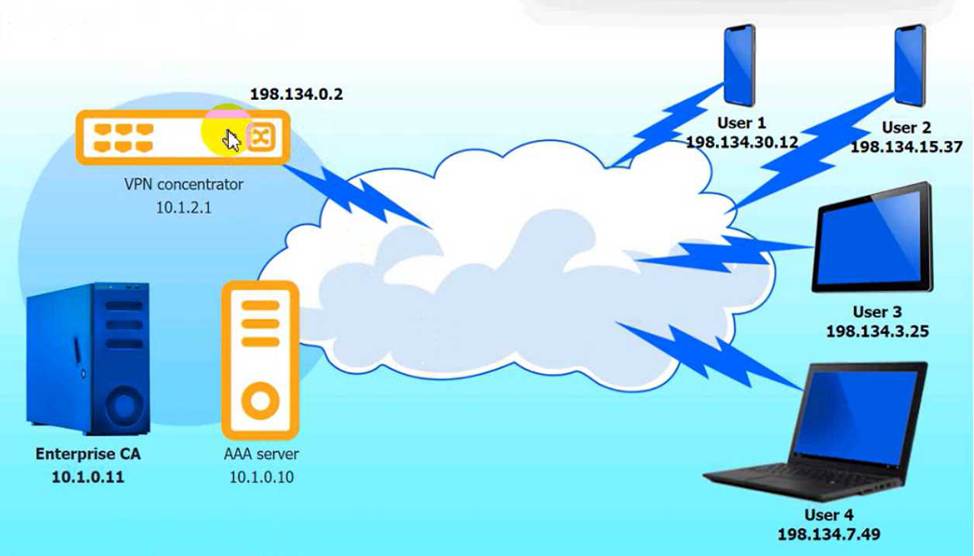
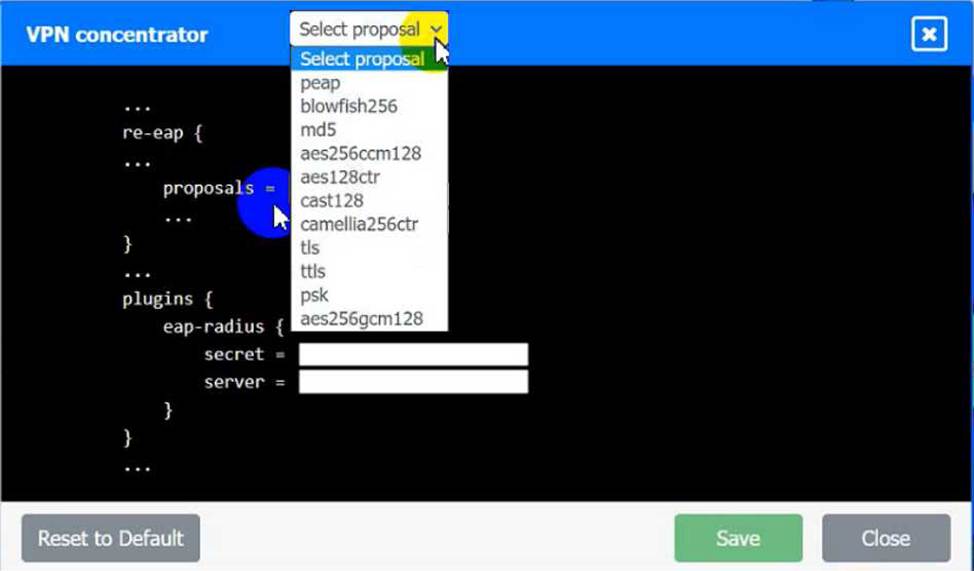
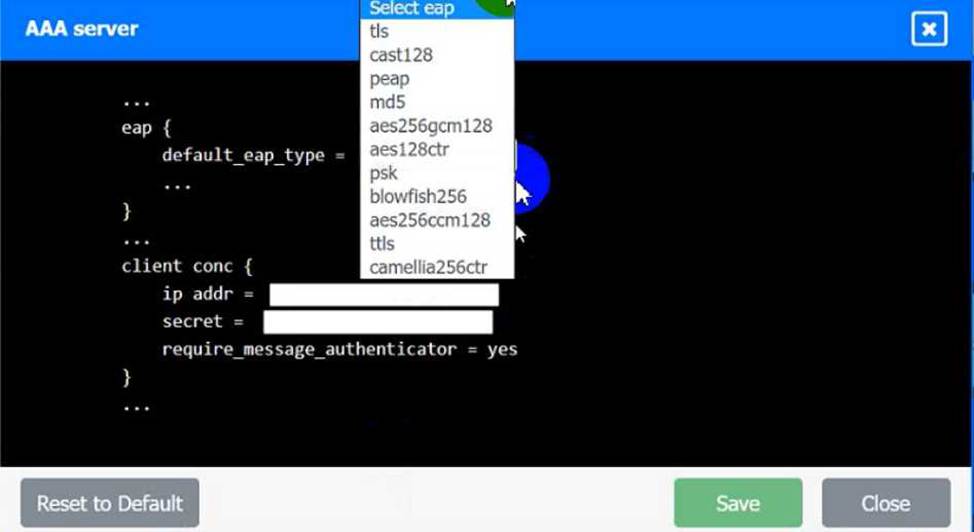
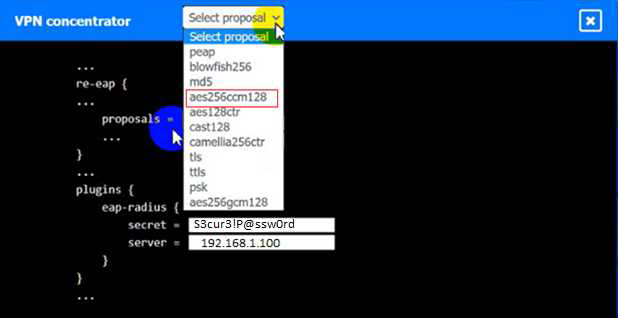
SIMULATION
An IPSec solution is being deployed. The configuration files for both the VPN
concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
• The EAP method must use mutual certificate-based authentication (With issued client certificates).
• The IKEv2 Cipher suite must be configured to the MOST secure authenticated mode of operation,
• The secret must contain at least one uppercase character, one lowercase character, one numeric character, and one special character, and it must meet a minimum length requirement of eight characters,
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration. Fill in the appropriate fields and make selections from the drop-down menus.
VPN Concentrator:
AAA Server:
AAA Server: