Practice Free CAS-004 Exam Online Questions
A company is on a deadline to roll out an entire CRM platform to all users at one time. However, the company is behind schedule due to reliance on third-party vendors.
Which of the following development approaches will allow the company to begin releases but also continue testing and development for future releases?
- A . Implement iterative software releases.
- B . Revise the scope of the project to use a waterfall approach
- C . Change the scope of the project to use the spiral development methodology.
- D . Perform continuous integration.
A security engineer was auditing an organization’s current software development practice and discovered that multiple open-source libraries were Integrated into the organization’s software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the security of the open-source libraries?
- A . Perform additional SAST/DAST on the open-source libraries.
- B . Implement the SDLC security guidelines.
- C . Track the library versions and monitor the CVE website for related vulnerabilities.
- D . Perform unit testing of the open-source libraries.
C
Explanation:
Reference: https://www.whitesourcesoftware.com/resources/blog/application-security-best-practices/
Tracking the library versions and monitoring the CVE (Common Vulnerabilities and Exposures) website for related vulnerabilities is an activity that the organization should incorporate into the SDLC (software development life cycle) to ensure the security of the open-source libraries integrated into its software. Tracking the library versions can help identify outdated or unsupported libraries that may contain vulnerabilities or bugs. Monitoring the CVE website can help discover publicly known vulnerabilities in the open-source libraries and their severity ratings. Performing additional SAST/DAST (static application security testing/dynamic application security testing) on the open-source libraries may not be feasible or effective for ensuring their security, as SAST/DAST are mainly focused on testing the source code or functionality of the software, not the libraries. Implementing the SDLC security guidelines is a general activity that the organization should follow for developing secure software, but it does not specifically address the security of the open-source libraries. Performing unit testing of the open-source libraries may not be feasible or effective for ensuring their security, as unit testing is mainly focused on testing the individual components or modules of the software, not the libraries.
Verified Reference:
https://www.comptia.org/blog/what-is-cve
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A company wants to implement a new website that will be accessible via browsers with no mobile applications available. The new website will allow customers to submit sensitive medical information securely and receive online medical advice. The company already has multiple other websites where it provides various public health data and information.
The new website must implement the following:
• The highest form Of web identity validation
• Encryption of all web transactions
• The strongest encryption in-transit
• Logical separation based on data sensitivity Other things that should be considered include:
• The company operates multiple other websites that use encryption.
• The company wants to minimize total expenditure.
• The company wants to minimize complexity
Which of the following should the company implement on its new website? (Select TWO).
- A . Wildcard certificate
- B . EV certificate
- C . Mutual authentication
- D . Certificate pinning
- E . SSO
- F . HSTS
B,F
Explanation:
The company should implement an EV certificate and HSTS on its new website. An EV certificate provides the highest level of web identity validation by requiring extensive verification of the organization’s identity and domain ownership. HSTS enforces encryption of all web transactions by redirecting HTTP requests to HTTPS and preventing users from accepting invalid certificates. These solutions would enhance the security and trustworthiness of the website without increasing complexity or expenditure significantly.
Verified Reference:
https://www.entrust.com/digital-security/certificate-solutions/products/digital-certificates/tls-ssl-certificates
https://learn.microsoft.com/en-us/azure/active-directory/develop/access-tokens
An application engineer is using the Swagger framework to leverage REST APIs to authenticate endpoints. The engineer is receiving HTTP 403 responses.
Which of the following should the engineer do to correct this issue? (Select two).
- A . Obtain a security token.
- B . Obtain a public key.
- C . Leverage Kerberos for authentication
- D . Leverage OAuth for authentication.
- E . Leverage LDAP for authentication.
- F . Obtain a hash value.
A,D
Explanation:
The HTTP 403 error indicates that the engineer does not have the appropriate permissions to access the endpoint. To correct this, the engineer should obtain a security token and leverage OAuth for authentication. OAuth is a widely used authorization framework for securing API endpoints, and obtaining a security token is a key step in authenticating API requests. These two steps will ensure the correct authentication process is followed, allowing access to the required API resources. CASP+ emphasizes the importance of using secure authentication mechanisms like OAuth for modern web applications and APIs.
Reference: CASP+ CAS-004 Exam Objectives: Domain 3.0 C Enterprise Security Architecture (API Security, OAuth)
CompTIA CASP+ Study Guide: API Security and OAuth for Authentication
A security auditor needs to review the manner in which an entertainment device operates. The auditor is analyzing the output of a port scanning tool to determine the next steps in the security review. Given the following log output.
The best option for the auditor to use NEXT is:
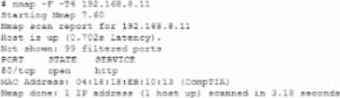
- A . A SCAP assessment.
- B . Reverse engineering
- C . Fuzzing
- D . Network interception.
An application server was recently upgraded to prefer TLS 1.3, and now users are unable to connect their clients to the server.
Attempts to reproduce the error are confirmed, and clients are reporting the following:
ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Which of the following is MOST likely the root cause?
- A . The client application is testing PFS.
- B . The client application is configured to use ECDHE.
- C . The client application is configured to use RC4.
- D . The client application is configured to use AES-256 in GCM.
C
Explanation:
Reference: https://kinsta.com/knowledgebase/err_ssl_version_or_cipher_mismatch/
The client application being configured to use RC4 is the most likely root cause of why users are unable to connect their clients to the server that prefers TLS 1.3. RC4 is an outdated and insecure symmetric-key encryption algorithm that has been deprecated and removed from TLS 1.3, which is the latest version of the protocol that provides secure communication between clients and servers. If the client application is configured to use RC4, it will not be able to negotiate a secure connection with the server that prefers TLS 1.3, resulting in an error message such as ERR_SSL_VERSION_OR_CIPHER_MISMATCH. The client application testing PFS (perfect forward secrecy) is not a likely root cause of why users are unable to connect their clients to the server that prefers TLS 1.3, as PFS is a property that ensures that session keys derived from a set of long-term keys cannot be compromised if one of them is compromised in the future. PFS is supported and recommended by TLS 1.3, which uses ephemeral Diffie-Hellman or elliptic curve Diffie-Hellman key exchange methods to achieve PFS. The client application being configured to use ECDHE (elliptic curve Diffie-Hellman ephemeral) is not a likely root cause of why users are unable to connect their clients to the server that prefers TLS 1.3, as ECDHE is a key exchange method that provides PFS and high performance by using elliptic curve cryptography to generate ephemeral keys for each session.
ECDHE is supported and recommended by TLS 1.3, which uses ECDHE as the default key exchange method. The client application being configured to use AES-256 in GCM (Galois/Counter Mode) is not a likely root cause of why users are unable to connect their clients to the server that prefers TLS 1.3, as AES-256 in GCM is an encryption mode that provides confidentiality and integrity by using AES with a 256-bit key and GCM as an authenticated encryption mode. AES-256 in GCM is supported and recommended by TLS 1.3, which uses AES-256 in GCM as one of the default encryption modes.
Verified Reference:
https://www.comptia.org/blog/what-is-tls-13
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
An organization established an agreement with a partner company for specialized help desk services. A senior security officer within the organization Is tasked with providing documentation required to set up a dedicated VPN between the two entities.
Which of the following should be required?
- A . SLA
- B . ISA
- C . NDA
- D . MOU
B
Explanation:
An ISA, or interconnection security agreement, is a document that should be required to set up a dedicated VPN between two entities that provide specialized help desk services. An ISA defines the technical and security requirements for establishing, operating, and maintaining a secure connection between two or more organizations. An ISA also specifies the roles and responsibilities of each party, the security controls and policies to be implemented, the data types and classifications to be exchanged, and the incident response procedures to be followed.
Reference: [CompTIA CASP+ Study Guide, Second Edition, page 36]
A security analyst received the following finding from a cloud security assessment tool:
Virtual Machine Data Disk is encrypted with the default encryption key.
Because the organization hosts highly sensitive data files, regulations dictate it must be encrypted so it is unreadable to the CSP.
Which of the following should be implemented to remediate the finding and meet the regulatory requirement? (Select two).
- A . Disk encryption with customer-provided keys
- B . Disk encryption with keys from a third party
- C . Row-level encryption with a key escrow
- D . File-level encryption with cloud vendor-provided keys
- E . File-level encryption with customer-provided keys
- F . Disk-level encryption with a cross-signed certificate
UESTION NO: 36
Which of the following is a benefit of using steganalysis techniques in forensic response?
- A . Breaking a symmetric cipher used in secure voice communications
- B . Determining the frequency of unique attacks against DRM-protected media
- C . Maintaining chain of custody for acquired evidence
- D . Identifying least significant bit encoding of data in a .wav file
D
Explanation:
Steganalysis is the process of detecting hidden data in files or media, such as images, audio, or video. One technique of steganalysis is to identify least significant bit encoding, which is a method of hiding data by altering the least significant bits of each byte in a file. For example, a .wav file could contain hidden data encoded in the least significant bits of each audio sample. Steganalysis techniques can help forensic responders to discover hidden evidence or malicious payloads. Breaking a symmetric cipher, determining the frequency of attacks, or maintaining chain of custody are not related to steganalysis.
Verified Reference:
https://www.comptia.org/blog/what-is-steganography https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A security officer is requiring all personnel working on a special project to obtain a security clearance requisite with the level of all information being accessed Data on this network must be protected at the same level of each clearance holder The need to know must be vended by the data owner.
Which of the following should the security officer do to meet these requirements?
- A . Create a rule lo authorize personnel only from certain IPs to access the files
- B . Assign labels to the files and require formal access authorization
- C . Assign attributes to each file and allow authorized users to share the files
- D . Assign roles to users and authorize access to files based on the roles
B
Explanation:
Labeling files and requiring formal access authorization is a method that aligns with the principle of least privilege and the need-to-know basis. By assigning labels to files based on their sensitivity and requiring formal access approval from the data owner, the security officer can ensure that only personnel with the necessary clearance and a legitimate need to access the information can do so. This approach helps in maintaining data confidentiality and integrity in line with the project’s security requirements.
