Practice Free CAS-004 Exam Online Questions
A security engineer is reviewing event logs because an employee successfully connected a personal Windows laptop to the corporate network, which is against company policy. Company policy allows all Windows 10 and 11 laptops to connect to the system as long as the MDM agent installed by IT is running.
Only compliant devices can connect, and the logic in the system to evaluate compliant laptops is as follows:
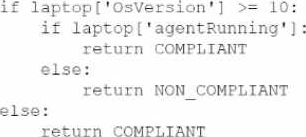
Which of the following most likely occurred when the employee connected a personally owned Windows laptop and was allowed on the network?
- A . The agent was not running on the laptop, which triggered a false positive.
- B . The OS was a valid version, but the MDM agent was not installed, triggering a true positive.
- C . The OS was running a Windows version below 10 and triggered a false negative.
- D . The OS version was higher than 11. and the MDM agent was running, triggering a true negative.
An energy company is required to report the average pressure of natural gas used over the past quarter. A PLC sends data to a historian server that creates the required reports.
Which of the following historian server locations will allow the business to get the required reports in an ОТ and IT environment?
- A . In the ОТ environment, use a VPN from the IT environment into the ОТ environment.
- B . In the ОТ environment, allow IT traffic into the ОТ environment.
- C . In the IT environment, allow PLCs to send data from the ОТ environment to the IT environment.
- D . Use a screened subnet between the ОТ and IT environments.
D
Explanation:
A screened subnet is a network segment that separates two different environments, such as ОТ (operational technology) and IT (information technology), and provides security controls to limit and monitor the traffic between them. This would allow the business to get the required reports from the historian server without exposing the ОТ environment to unnecessary risks. Using a VPN, allowing IT traffic, or allowing PLCs to send data are less secure options that could compromise the ОТ environment.
Verified Reference:
https://www.comptia.org/blog/what-is-operational-technology
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A security engineer needs to recommend a solution that will meet the following requirements:
Identify sensitive data in the provider’s network
Maintain compliance with company and regulatory guidelines
Detect and respond to insider threats, privileged user threats, and compromised accounts Enforce datacentric security, such as encryption, tokenization, and access control
Which of the following solutions should the security engineer recommend to address these requirements?
- A . WAF
- B . CASB
- C . SWG
- D . DLP
D
Explanation:
DLP (data loss prevention) is a solution that can meet the following requirements: identify sensitive data in the provider’s network, maintain compliance with company and regulatory guidelines, detect and respond to insider threats, privileged user threats, and compromised accounts, and enforce data-centric security, such as encryption, tokenization, and access control. DLP can monitor, classify, and protect data in motion, at rest, or in use, and prevent unauthorized disclosure or exfiltration. WAF (web application firewall) is a solution that can protect web applications from common attacks, such as SQL injection or cross-site scripting, but it does not address the requirements listed. CASB (cloud access security broker) is a solution that can enforce policies and controls for accessing cloud services and applications, but it does not address the requirements listed. SWG (secure web gateway) is a solution that can monitor and filter web traffic to prevent malicious or unauthorized access, but it does not address the requirements listed.
Verified Reference:
https://www.comptia.org/blog/what-is-data-loss-prevention
https://partners.comptia.org/docs/default-source/resources/casp-content-guid
An enterprise is undergoing an audit to review change management activities when promoting code to production.
The audit reveals the following:
• Some developers can directly publish code to the production environment.
• Static code reviews are performed adequately.
• Vulnerability scanning occurs on a regularly scheduled basis per policy.
Which of the following should be noted as a recommendation within the audit report?
- A . Implement short maintenance windows.
- B . Perform periodic account reviews.
- C . Implement job rotation.
- D . Improve separation of duties.
A software development company wants to ensure that users can confirm the software is legitimate when installing it.
Which of the following is the best way for the company to achieve this security objective?
- A . Code signing
- B . Non-repudiation
- C . Key escrow
- D . Private keys
A
Explanation:
Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed. This provides users with the assurance that the software is legitimate and safe to install.
A security engineer needs 10 implement a CASB to secure employee user web traffic. A Key requirement is mat relevant event data must be collected from existing on-premises infrastructure components and consumed by me CASB to expand traffic visibility. The solution must be nighty resilient to network outages.
Which of the following architectural components would BEST meet these requirements?
- A . Log collection
- B . Reverse proxy
- C . AWAF
- D . API mode
After a cybersecurity incident, a judge found that a company did not conduct a proper forensic investigation. The company was ordered to pay penalties.
Which of the following forensic steps would be best to prevent this from happening again?
- A . Evidence preservation
- B . Evidence verification
- C . Evidence collection
- D . Evidence analysis
A
Explanation:
Proper forensic investigation requires that evidence is preserved in a manner that maintains its integrity and reliability. To prevent legal issues such as penalties for not conducting a proper forensic investigation, the first and most crucial step is to ensure that evidence is preserved so that it can be verified, collected, and analyzed correctly. This involves making sure that the evidence is not tampered with or altered from the time it is identified until it is presented in a legal proceeding.
A company recently acquired a SaaS company and performed a gap analysis. The results of the gap analysis indicate security controls are absent throughout the SDLC and have led to several vulnerable production releases.
Which of the following security tools best reduces the risk of vulnerable code being pushed to production in the future?
- A . Static application security testing
- B . Regression testing
- C . Code signing
- D . Sandboxing
A developer wants to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users.
Which of the following would be BEST for the developer to perform? (Choose two.)
- A . Utilize code signing by a trusted third party.
- B . Implement certificate-based authentication.
- C . Verify MD5 hashes.
- D . Compress the program with a password.
- E . Encrypt with 3DES.
- F . Make the DACL read-only.
A,F
Explanation:
Utilizing code signing by a trusted third party and making the DACL (discretionary access control list) read-only are actions that the developer can perform to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users. Code signing is a technique that uses digital signatures to verify the authenticity and integrity of code, preventing unauthorized modifications or tampering. A trusted third party, such as a certificate authority, can issue and validate digital certificates for code signing. A DACL is an attribute of an object that defines the permissions granted or denied to users or groups for accessing or modifying the object. Making the DACL read-only can prevent unauthorized users or groups from changing the permissions or accessing the code. Implementing certificate-based authentication is not an action that the developer can perform to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users, but a method for verifying the identity of users or devices based on digital certificates, preventing unauthorized access or impersonation. Verifying MD5 hashes is not an action that the developer can perform to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users, but a method for checking the integrity of files based on cryptographic hash functions, detecting accidental or intentional changes or corruption. Compressing the program with a password is not an action that the developer can perform to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users, but a method for reducing the size of files and protecting them with a password, preventing unauthorized access or extraction. Encrypting with 3DES is not an action that the developer can perform to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users, but a method for protecting the confidentiality of data based on symmetric-key encryption algorithms, preventing unauthorized disclosure or interception.
Verified Reference:
https://www.comptia.org/blog/what-is-code-signing
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
Immediately following the report of a potential breach, a security engineer creates a forensic image
of the server in question as part of the organization incident response procedure.
Which of the must occur to ensure the integrity of the image?
- A . The image must be password protected against changes.
- B . A hash value of the image must be computed.
- C . The disk containing the image must be placed in a seated container.
- D . A duplicate copy of the image must be maintained
