Practice Free CAS-004 Exam Online Questions
A company is deploying multiple VPNs to support supplier connections into its extranet applications.
The network security standard requires:
• All remote devices to have up-to-date antivirus
• An up-to-date and patched OS
Which of the following technologies should the company deploy to meet its security objectives? (Select TWO)
- A . NAC
- B . WAF
- C . NIDS
- D . Reverse proxy
- E . NGFW
- F . Bastion host
The Chief Information Security Officer of a large multinational organization has asked the security risk manager to use risk scenarios during a risk analysis.
Which of the following is the most likely reason for this approach?
- A . To connect risks to business objectives
- B . To ensure a consistent approach to risk
- C . To present a comprehensive view of risk
- D . To provide context to the relevancy of risk
A company that uses AD is migrating services from LDAP to secure LDAP. During the pilot phase, services are not connecting properly to secure LDAP.
Block is an except of output from the troubleshooting session:

Which of the following BEST explains why secure LDAP is not working? (Select TWO.)
- A . The clients may not trust idapt by default.
- B . The secure LDAP service is not started, so no connections can be made.
- C . Danvills.com is under a DDoS-inator attack and cannot respond to OCSP requests.
- D . Secure LDAP should be running on UDP rather than TCP.
- E . The company is using the wrong port. It should be using port 389 for secure LDAP.
- F . Secure LDAP does not support wildcard certificates.
- G . The clients may not trust Chicago by default.
A,F
Explanation:
The clients may not trust idapt by default because it is a self-signed certificate authority that is not in the trusted root store of the clients. Secure LDAP does not support wildcard certificates because they do not match the fully qualified domain name of the server.
Verified Reference:
https://www.professormesser.com/security-plus/sy0-401/ldap-and-secure-ldap/, https://www.comptia.org/training/books/casp-cas-004-study-guide
Which of the following agreements includes no penalties and can be signed by two entities that are working together toward the same goal?
- A . MOU
- B . NDA
- C . SLA
- D . ISA
A security analyst needs to recommend a remediation to the following threat:
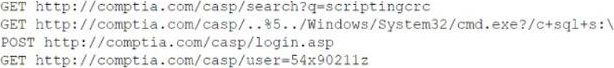
Which of the following actions should the security analyst propose to prevent this successful exploitation?
- A . Patch the system.
- B . Update the antivirus.
- C . Install a host-based firewall.
- D . Enable TLS 1.2.
A developer needs to implement PKI in an autonomous vehicle’s software in the most efficient and labor-effective way possible.
Which of the following will the developer MOST likely implement?
- A . Certificate chain
- B . Root CA
- C . Certificate pinning
- D . CRL
- E . OCSP
B
Explanation:
The developer would most likely implement a Root CA in the autonomous vehicle’s software. A Root CA is the top-level authority in a PKI that issues and validates certificates for subordinate CAs or end entities. A Root CA can be self-signed and embedded in the vehicle’s software, which would reduce the need for external communication and verification. A Root CA would also enable the vehicle to use digital signatures and encryption for secure communication with other vehicles or infrastructure.
Verified Reference:
https://cse.iitkgp.ac.in/~abhij/publications/PKI++.pdf
https://www.digicert.com/blog/connected-cars-need-security-use-pki
https://ieeexplore.ieee.org/document/9822667/
Which of the following are risks associated with vendor lock-in? (Choose two.)
- A . The client can seamlessly move data.
- B . The vendor can change product offerings.
- C . The client receives a sufficient level of service.
- D . The client experiences decreased quality of service.
- E . The client can leverage a multicloud approach.
- F . The client experiences increased interoperability.
B,D
Explanation:
Reference: https://www.cloudflare.com/learning/cloud/what-is-vendor-lock-in/#:~:text=Vendor%20lock%2Din%20can%20become,may%20involve%20reformatting%20the%20data
Vendor lock-in is a situation where a client becomes dependent on a vendor for products or services and cannot easily switch to another vendor without substantial costs or inconvenience. Some of the risks associated with vendor lock-in are that the vendor can change product offerings, such as by discontinuing or modifying features, increasing prices, or reducing support, and that the client experiences decreased quality of service, such as by having poor performance, reliability, or security. These risks could affect the client’s business operations, satisfaction, or competitiveness. The client can seamlessly move data, the client receives a sufficient level of service, and the client can leverage a multicloud approach are not risks associated with vendor lock-in, but potential benefits of avoiding vendor lock-in.
Verified Reference:
https://www.comptia.org/blog/what-is-vendor-lock-in
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
An administrator completed remediation for all the findings of a penetration test and notifies the management team that the systems are ready to be placed back into production.
Which of the following steps should the management team require the analyst to perform immediately before placing the systems back into production?
- A . Rescan for corrections/changes.
- B . Conduct the entire penetration test again.
- C . Harden the targeted systems.
- D . Ensure a host-based IPS is in place.
A
Explanation:
Rescanning ensures all identified vulnerabilities have been resolved and no additional changes introduced new issues. This step is critical for verifying remediation effectiveness before moving systems back into production, aligning with CASP+ objective 5.1, which involves verifying security measures during testing and evaluation phases.
During a recent security incident investigation, a security analyst mistakenly turned off the infected machine prior to consulting with a forensic analyst. upon rebooting the machine, a malicious script that was running as a background process was no longer present. As a result, potentially useful evidence was lost.
Which of the following should the security analyst have followed?
- A . Order of volatility
- B . Chain of custody
- C . Verification
- D . Secure storage
A
Explanation:
Order of volatility is a procedure that a computer forensics examiner must follow during evidence collection. It refers to the order in which digital evidence is collected, starting with the most volatile and moving to the least volatile. Volatile data is data that is not permanent and is easily lost, such as data in memory when you turn off a computer. The security analyst should have followed the order of volatility to preserve the most fragile evidence first, such as the malicious script running as a background process, before turning off the infected machine.
Verified Reference:
https://www.computer-forensics-recruiter.com/order-of-volatility/
https://www.sans.org/blog/best-practices-in-digital-evidence-collection/
https://blogs.getcertifiedgetahead.com/order-of-volatility/
A security architect is tasked with securing a new cloud-based videoconferencing and collaboration platform to support a new distributed workforce.
The security architect’s key objectives are to:
• Maintain customer trust
• Minimize data leakage
• Ensure non-repudiation
Which of the following would be the BEST set of recommendations from the security architect?
- A . Enable the user authentication requirement, enable end-to-end encryption, and enable waiting rooms.
- B . Disable file exchange, enable watermarking, and enable the user authentication requirement.
- C . Enable end-to-end encryption, disable video recording, and disable file exchange.
- D . Enable watermarking, enable the user authentication requirement, and disable video recording.
B
Explanation:
Disabling file exchange can help to minimize data leakage by preventing users from sharing sensitive documents or data through the videoconferencing platform. Enabling watermarking can help to maintain customer trust and ensure non-repudiation by adding a visible or invisible mark to the video stream that identifies the source or owner of the content. Enabling the user authentication requirement can help to secure the videoconferencing sessions by verifying the identity of the participants and preventing unauthorized access.
Verified Reference:
https://www.rev.com/blog/marketing/follow-these-7-video-conferencing-security-best-practices
https://www.paloaltonetworks.com/blog/2020/04/network-video-conferencing-security/
https://www.megameeting.com/news/best-practices-secure-video-conferencing/
