Practice Free CAS-004 Exam Online Questions
A senior cybersecurity engineer is solving a digital certificate issue in which the CA denied certificate issuance due to failed subject identity validation.
At which of the following steps within the PKI enrollment process would the denial have occurred?
- A . RA
- B . OCSP
- C . CA
- D . IdP
Which of the following BEST describes a common use case for homomorphic encryption?
- A . Processing data on a server after decrypting in order to prevent unauthorized access in transit
- B . Maintaining the confidentiality of data both at rest and in transit to and from a CSP for processing
- C . Transmitting confidential data to a CSP for processing on a large number of resources without revealing information
- D . Storing proprietary data across multiple nodes in a private cloud to prevent access by unauthenticated users
C
Explanation:
Homomorphic encryption is a type of encryption method that allows computations to be performed on encrypted data without first decrypting it with a secret key. The results of the computations also remain encrypted and can only be decrypted by the owner of the private key. Homomorphic encryption can be used for privacy-preserving outsourced storage and computation. This means that data can be encrypted and sent to a cloud service provider (CSP) for processing, without revealing any information to the CSP or anyone else who might intercept the data. Homomorphic encryption can enable new services and applications that require processing confidential data on a large number of resources, such as machine learning, data analytics, health care, finance, and voting.
An internal security audit determines that Telnet is currently being used within the environment to manage network switches.
Which of the following tools should be utilized to identify credentials in plaintext that are used to log in to these devices?
- A . Fuzzer
- B . Network traffic analyzer
- C . HTTP interceptor
- D . Port scanner
- E . Password cracker
B
Explanation:
A network traffic analyzer (also known as a packet sniffer) is the best tool to identify credentials being transmitted in plaintext, such as those used in Telnet sessions. Since Telnet transmits data without encryption, a network traffic analyzer can capture the traffic between the client and the network switches, revealing sensitive information, including login credentials, in clear text. This tool helps identify insecure protocols and enables remediation by switching to encrypted alternatives like SSH. CASP+ highlights the importance of using secure protocols and tools like traffic analyzers to identify vulnerabilities in network communications.
Reference: CASP+ CAS-004 Exam Objectives: Domain 2.0 C Enterprise Security Operations (Network Traffic Analysis and Insecure Protocols)
CompTIA CASP+ Study Guide: Monitoring Network Traffic for Plaintext Credentials
A mobile device hardware manufacturer receives the following requirements from a company that wants to produce and sell a new mobile platform:
• The platform should store biometric data.
• The platform should prevent unapproved firmware from being loaded.
• A tamper-resistant, hardware-based counter should track if unapproved firmware was loaded.
Which of the following should the hardware manufacturer implement? (Select three).
- A . ASLR
- B . NX
- C . eFuse
- D . SED
- E . SELinux
- F . Secure boot
- G . Shell restriction
- H . Secure enclave
C,F,H
Explanation:
To meet the mobile platform security requirements, the manufacturer should implement the following technologies:
eFuse: This hardware feature helps track and prevent unauthorized firmware by physically "blowing"
fuses to record events, such as firmware tampering, making it impossible to revert to older, unapproved firmware.
Secure boot: This ensures that only trusted and authorized firmware can be loaded during the boot process, preventing malicious or unauthorized software from running.
Secure enclave: A secure enclave is used to store sensitive information like biometric data in a hardware-isolated environment, protecting it from tampering or unauthorized access.
These three solutions provide the tamper resistance, secure firmware validation, and protection of sensitive data required for the platform. CASP+ emphasizes the use of hardware-based security features for protecting sensitive information and enforcing secure boot processes in embedded and mobile systems.
Reference: CASP+ CAS-004 Exam Objectives: Domain 3.0 C Enterprise Security Architecture (Secure Hardware and Firmware Protection)
CompTIA CASP+ Study Guide: Hardware Security Features (eFuse, Secure Boot, Secure Enclave)
A security analyst detected a malicious PowerShell attack on a single server. The malware used the Invoke-Expression function to execute an external malicious script. The security analyst scanned the disk with an antivirus application and did not find any IOCs. The security analyst now needs to deploy a protection solution against this type of malware.
Which of the following BEST describes the type of malware the solution should protect against?
- A . Worm
- B . Logic bomb
- C . Fileless
- D . Rootkit
C
Explanation:
Reference: https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/tracking-detecting-and-thwarting-powershell-based-malware-and-attacks
An organization recently experienced a ransomware attack. The security team leader is concerned about the attack reoccurring. However, no further security measures have been implemented.
Which of the following processes can be used to identify potential prevention recommendations?
- A . Detection
- B . Remediation
- C . Preparation
- D . Recovery
C
Explanation:
Preparation is the process that can be used to identify potential prevention recommendations after a security incident, such as a ransomware attack. Preparation involves planning and implementing security measures to prevent or mitigate future incidents, such as by updating policies, procedures, or controls, conducting training or awareness campaigns, or acquiring new tools or resources. Detection is the process of discovering or identifying security incidents, not preventing them. Remediation is the process of containing or resolving security incidents, not preventing them. Recovery is the process of restoring normal operations after security incidents, not preventing them.
Verified Reference:
https://www.comptia.org/blog/what-is-incident-response
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A review of the past year’s attack patterns shows that attackers stopped reconnaissance after finding a susceptible system to compromise. The company would like to find a way to use this information to protect the environment while still gaining valuable attack information.
Which of the following would be BEST for the company to implement?
- A . A WAF
- B . An IDS
- C . A SIEM
- D . A honeypot
D
Explanation:
Reference: https://www.kaspersky.com/resource-center/threats/what-is-a-honeypot
During a review of events, a security analyst notes that several log entries from the FIM system identify changes to firewall rule sets. While coordinating a response to the FIM entries, the analyst receives alerts from the DLP system that indicate an employee is sending sensitive data to an external email address.
Which of the following would be the most relevant to review in order to gain a better understanding of whether these events are associated with an attack?
- A . Configuration management tool
- B . Intrusion prevention system
- C . Mobile device management platform
- D . Firewall access control list
- E . NetFlow logs
E
Explanation:
NetFlow logs provide visibility into network traffic patterns and volume, which can be analyzed to detect anomalies, including potential security incidents. They can be invaluable in correlating the timing and nature of network events with security incidents to better understand if there is an association.
An IT department is currently working to implement an enterprise DLP solution. Due diligence and best practices must be followed in regard to mitigating risk.
Which of the following ensures that authorized modifications are well planned and executed?
- A . Risk management
- B . Network management
- C . Configuration management
- D . Change management
D
Explanation:
Change management is a systematic approach to dealing with the transition or transformation of an organization’s goals, processes, or technologies. In the context of implementing a Data Loss Prevention (DLP) solution and ensuring that authorized modifications are well-planned and executed, change management is critical. It ensures that changes are introduced in a controlled and coordinated manner to minimize the impact on service quality and mitigate risks associated with the changes.
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper
mobile settings are applied to managed devices:
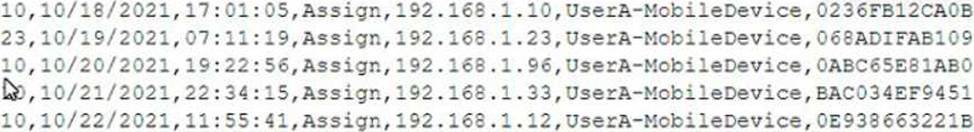
Which of the following mobile configuration settings is the mobile administrator verifying?
- A . Service set identifier authentication
- B . Wireless network auto joining
- C . 802.1X with mutual authentication
- D . Association MAC address randomization
B
Explanation:
Wireless network auto joining is the mobile configuration setting that the mobile administrator is verifying by reviewing the mobile device DHCP logs. Wireless network auto joining is a feature that allows mobile devices to automatically connect to a predefined wireless network without requiring user intervention or authentication. This can be useful for corporate or trusted networks that need frequent access by mobile devices. The DHCP logs show that the mobile devices are assigned IP addresses from the wireless network with SSID “CorpWiFi”, which indicates that they are auto joining this network.
Reference: [CompTIA CASP+ Study Guide, Second Edition, page 420]
