Practice Free AZ-800 Exam Online Questions
You have an on-premises server named Server 1 that runs Windows Server. You have an Azure subscription that contains a virtual network named VNetl. You need to connect Server1 to VNetl by using Azure Network Adapter.
What should you use?
- A . the Azure portal
- B . Azure AD Connect
- C . Device Manager
- D . Windows Admin Center
D
Explanation:
The hybrid networking module in AZ-800 details Azure Network Adapter (ANA) as a Windows Admin Center (WAC) workflow that creates a point-to-site (P2S) VPN from an on-premises Windows Server to an Azure virtual network. The documentation states that ANA is initiated directly from Windows Admin Center, which automates provisioning of the necessary Azure resources (e.g., VPN gateway configuration and certificates) and installs/configures the VPN client on the server, establishing secure connectivity to the target VNet. The Azure portal does not install or configure the on-premises VPN client for a standalone server; Azure AD Connect is used for identity synchronization and is unrelated to network tunneling; and Device Manager is not used for configuring VPN or Azure connectivity. In practice, you add the server to WAC, open the Network tool, and select Add Azure Network Adapter, sign in to Azure, choose VNet1, and complete the wizard. This is the prescribed, streamlined method for connecting Server1 to VNet1 using Azure Network Adapter, validating Windows Admin Center as the correct choice.
You have a server named Server1 that runs Windows Server 2019 and hosts a container named Contained. Contained uses a Windows Server 2019 base image that was built by using a Docker file.
You upgrade Server1 to Windows Server 2022.
You need to ensure that Contained will run on Server1. The solution must minimize administrative effort.
What should you do?
- A . Start Contained in process isolation mode.
- B . Modify the Docker file.
- C . Start Contained in Hyper-V isolation mode.
- D . Rebuild the base image for Contained.
Topic 4, Misc Questions
You have an Azure virtual machine named VM1 that runs Windows Server.
You perform the following actions on VM1:
• Create a folder named Folder1 on volume C
• Create a folder named Folder2 on volume D.
• Add a new data disk to VM1 and create a new volume that is assigned drive letter E.
• Install an app named App1 on volume E.
You plan to resize VM1.
Which objects will present after you resize VM1?
- A . Folded and Folder2 only
- B . Folder1, volume E, and App1 only
- C . Folder1 only
- D . Folded. Folder2. App1, and volume E
D
Explanation:
In the Windows Server hybrid IaaS guidance for AZ-800 (Administering Windows Server Hybrid Core Infrastructure), resizing an Azure VM changes compute characteristics only (vCPU/memory/size family). The learning path on managing Windows Server IaaS VMs states that the VM’s OS and any attached data disks persist across stop/deallocate and resize operations, and that drive letters and file data remain intact once the VM starts again. Applications installed on those persistent disks continue to function because the underlying VHDs are unchanged. The only disk that may be transient is the temporary (ephemeral) OS cache or D: temporary disk provided by some sizes; however, managed OS disk (C:) and any managed data disks (such as D: and the newly added E:) retain their contents. Consequently, the folders created on C: and D: remain, the additional data disk that was initialized as volume E remains attached with the same drive letter, and App1 installed on E: is still present after the resize. Therefore, after resizing VM1 you will still have Folder1, Folder2, volume E, and App1, making option D correct.
SIMULATION
Task 5
you need to configure a Group Policy preference to ensure that users in the organizational unit (OU) named Server Admins have a shortcut to a folder named \srvi.contoso.comdata on their desktop when they sign in to the computers in the domain.
Objective:
Configure a Group Policy Preference to create a shortcut to \srvi.contoso.comdata on the desktop of users in the Server Admins OU.
Step-by-Step Guide: Using Group Policy Preferences to Create a Desktop Shortcut
✅ Step 1: Open Group Policy Management Console (GPMC) Log in to a DC or a management computer with RSAT installed. Open Group Policy Management (gpmc.msc).
✅ Step 2: Create a New GPO
In the GPMC console, expand the forest and the domain (e.g., contoso.com).
Right-click the OU named Server Admins and select Create a GPO in this domain, and Link it here.
Name the GPO, e.g., Desktop Shortcut for Server Admins.
✅ Step 3: Edit the GPO
Right-click the newly created GPO and select Edit.
This opens the Group Policy Management Editor.
✅ Step 4: Navigate to User Preferences In the editor, expand:
User Configuration > Preferences > Windows Settings > Shortcuts.
✅ Step 5: Create the Shortcut
Right-click Shortcuts and select New > Shortcut.
In the New Shortcut Properties window:
Action: Create
Name: Data Folder
Target Type: File System Object
Location: Desktop
Target Path: \srvi.contoso.comdata
Optionally, set an icon or description if you want.
✅ Step 6: Configure Item-Level Targeting (Optional)
If you want to limit this shortcut strictly to specific users/groups, click the Common tab.
Check Item-level targeting and configure conditions (optional).
For this scenario, linking the GPO to the Server Admins OU is usually sufficient.
✅ Step 7: Close and Update
Close the editor.
In GPMC, ensure the GPO is linked to the Server Admins OU.
Force a Group Policy Update on client computers:
On a client computer:
gpupdate /force
Or wait for the next Group Policy refresh cycle.
✅ Step 8: Verify
Log in as a user in the Server Admins OU.
The shortcut to \srvi.contoso.comdata should appear on the desktop.
Your network contains a DHCP server.
You plan to add a new subnet and deploy Windows Server to the subnet.
You need to use the server as a DHCP relay agent.
Which role should you install on the server?
- A . Network Policy and Access Services
- B . Remote Access
- C . Network Controller
- D . DHCP Server
B
Explanation:
When Windows Server is used as a DHCP Relay Agent, the feature is delivered through Routing and Remote Access Service (RRAS). The AZ-800 content explains: “The DHCP Relay Agent is a component of RRAS and is installed by adding the Remote Access role and enabling the Routing role service.” After installation, admins configure the relay interface(s) and specify the IP addresses of one or more DHCP servers to which broadcast DHCPDISCOVER messages are forwarded. The documentation further notes: “Network Policy and Access Services (NPS) provides RADIUS and policy evaluation, not DHCP relay; the DHCP Server role offers DHCP lease services, not relay.” Thus, to prepare the server that sits on the new subnet to forward DHCP requests, you must install the Remote Access role (and within it, the Routing role service), then add the DHCP Relay Agent in the RRAS console or via PowerShell.
HOTSPOT
Your network contains an Active Directory Domain Services (AD DS) domain named adatum.com.
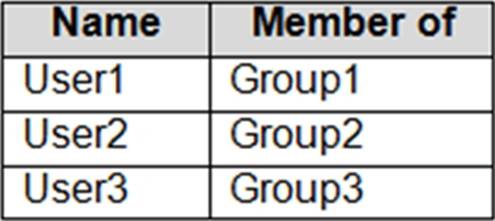
The domain contains a server named Server1 and the users shown in the following table.
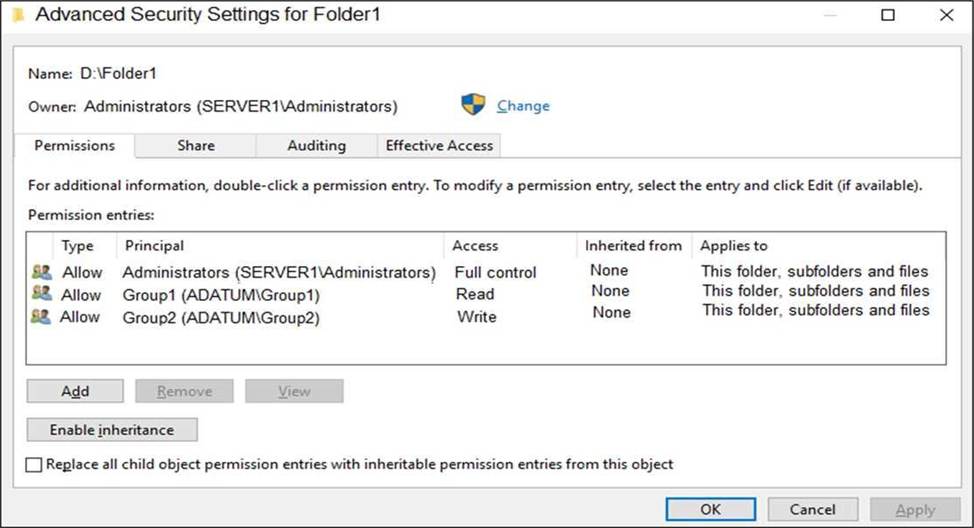
Server1 contains a folder named D:Folder1.
The advanced security settings for Folder1 are configured as shown in the Permissions exhibit. (Click the Permissions tab.)
Folder1 is shared by using the following configurations:
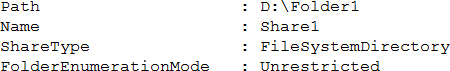
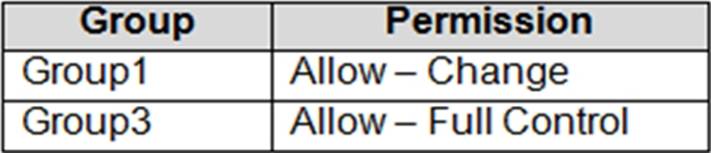
The share permissions for Share1 are shown in the following table.
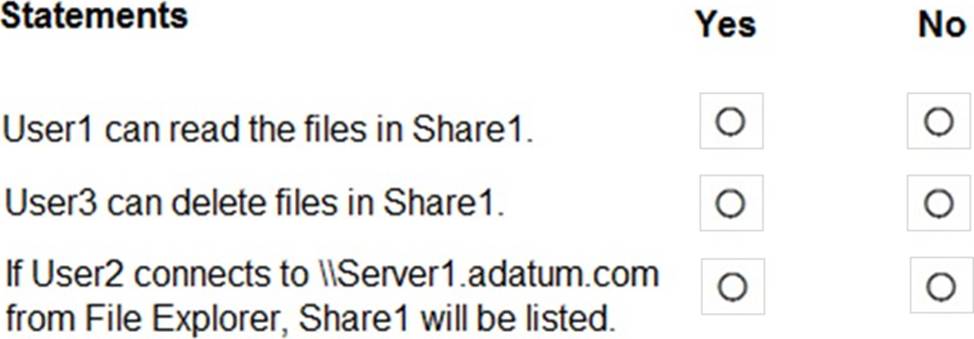
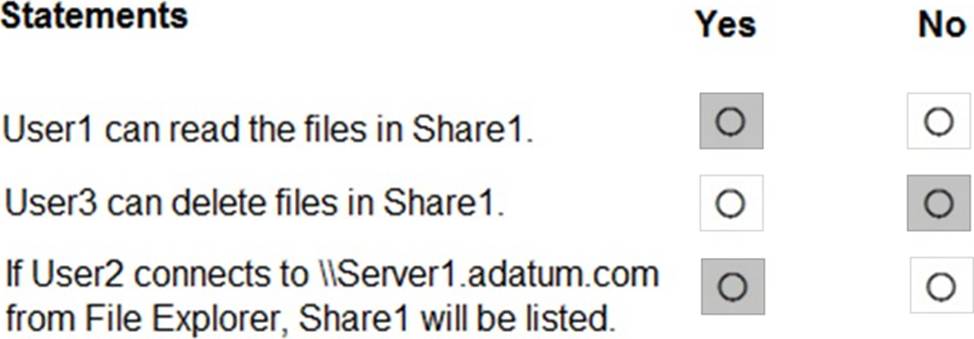
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
To access files in a shared folder, you need to be granted permissions on the folder (NTFS permissions) AND permissions on the share. The most restrictive permission of the folder permissions and share permissions apply.
Box 1: Yes
Group1 has Read access to Folder1 and Change access to Share1. Therefore, User1 can read the files in Share1.
Box 2: No
Group3 has Full Control access to Share1. However, Group3 has no permissions configured Folder1.
Therefore, User3 cannot access the files in Share1.
Box 3: Yes
Group2 has write permission to Folder1. However, Group2 has no permission on Share1. Therefore, users in Group2 cannot access files in the shared folder.
Access Based Enumeration when enabled hides files and folders that users do not have permission to access. However, Access Based Enumeration is not enabled on Share1. This is indicated by the FolderEnumerationMode C Unrestricted setting. Therefore, the share will be visible to User2 even though User2 cannot access the shared folder.
The course content for Administering Windows Server Hybrid Core Infrastructure explains the effective permission model for SMB shares: “Access to a shared folder is the most restrictive result of the Share permissions and the NTFS permissions. Share permissions control access over the network, while NTFS permissions control access to the file system itself. The effective permission is the intersection―users must have permission in both places.” It also clarifies typical rights: “Read includes viewing and opening; Change/Modify includes creating, changing, and deleting; Full Control adds the ability to change permissions and take ownership.”
Applying this: User1 is in Group1. Share1 grants Group1 = Change, and NTFS on D:Folder1 grants Group1 = Read. The intersection is Read, so User1 can read files. User3 is in Group3. Share1 grants Group3 = Full Control, but NTFS has no entry for Group3 (and no broader Allow that would include it). Without NTFS Modify/Delete, User3 cannot delete.
Regarding visibility, the share was created with FolderEnumerationMode = Unrestricted. The training states: “With Unrestricted enumeration, the share (and items) are not hidden based on access; users may see the share even if they lack permissions, though access will be denied when opened. Access-Based enumeration hides items from users without permission.” Therefore, when User2 (member of Group2) browses \Server1, Share1 will be listed, though opening it would rely on permissions.
HOTSPOT
Your on-premises network contains an Active Directory Domain Services (AD DS) domain.
The domain contains the servers shown in the following table.
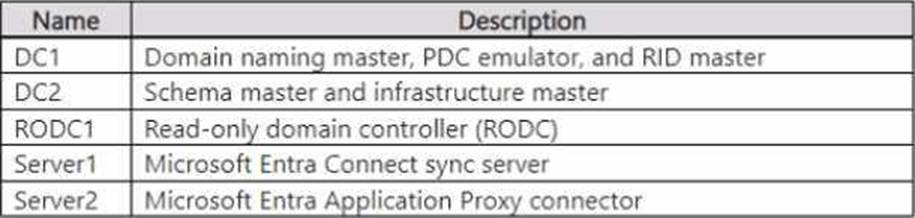
The domain controllers do NOT have internet connectivity.
You plan to implement Azure AD Password Protection for the domain.
You need to deploy Azure AD Password Protection agents.
The solution must meet the following requirements:
• All Azure AD Password Protection policies must be enforced.
• Agent updates must be applied automatically.
• Administrative effort must be minimized.
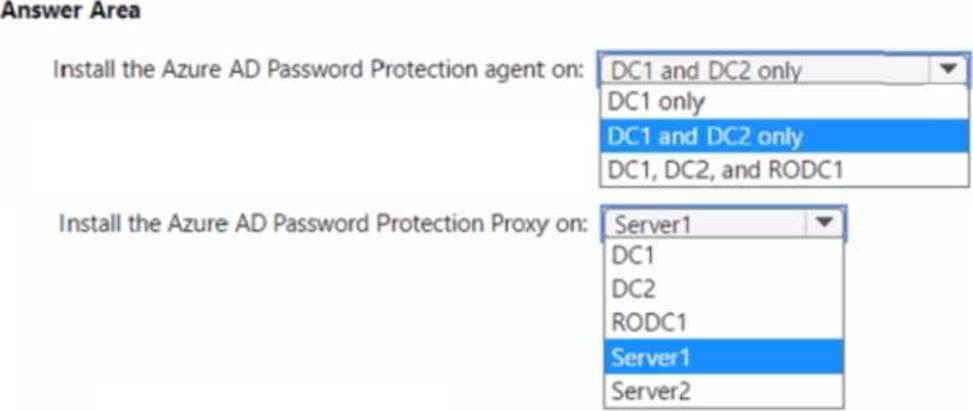
What should you do? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
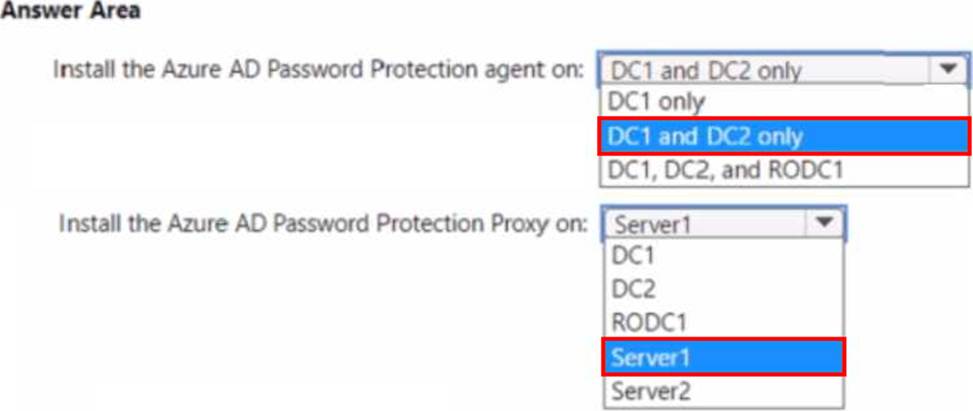
Explanation:
The Administering Windows Server Hybrid Core Infrastructure (AZ-800) guidance for Azure AD Password Protection states that enforcement occurs on writable domain controllers: “Deploy the DC agent to every writable DC in each domain where you want password policies evaluated.” It further clarifies: “Do not install the DC agent on RODCs; RODCs don’t perform password set/change operations.” Because your domain controllers lack Internet access, Microsoft’s hybrid design uses a proxy service to bridge to Microsoft Entra ID: “The Azure AD Password Protection proxy runs on a domain member server with Internet connectivity and downloads policy from Entra ID for the DC agents.” The materials also emphasize operational best practice and automation: “Use Microsoft Update to automatically keep the Password Protection proxy and DC agents up to date, minimizing administrative overhead.” Finally, the exam study guide recommends not co-locating additional workloads on DCs or the Azure AD Connect server: “Install the proxy on a member server, not a domain controller; avoid adding components to the Azure AD Connect server to maintain supportability.”
Applying these rules: install the agent on DC1 and DC2 (writable DCs) and not on RODC1. Place the proxy on an Internet-connected member server―Server2 (already an Application Proxy connector)― to meet enforcement, automatic updates, and minimal administrative effort.
HOTSPOT
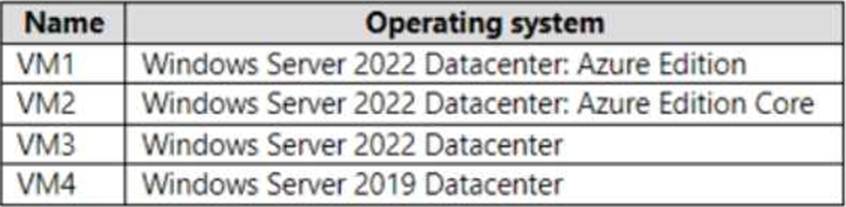
You have an Azure subscription that contains the virtual machines shown in the following table.
You plan to implement Azure Automanage for Windows Server.
You need to identify the operating system prerequisites.
Which virtual machines support Hotpatch, and which virtual machines support SMB over QUIC? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
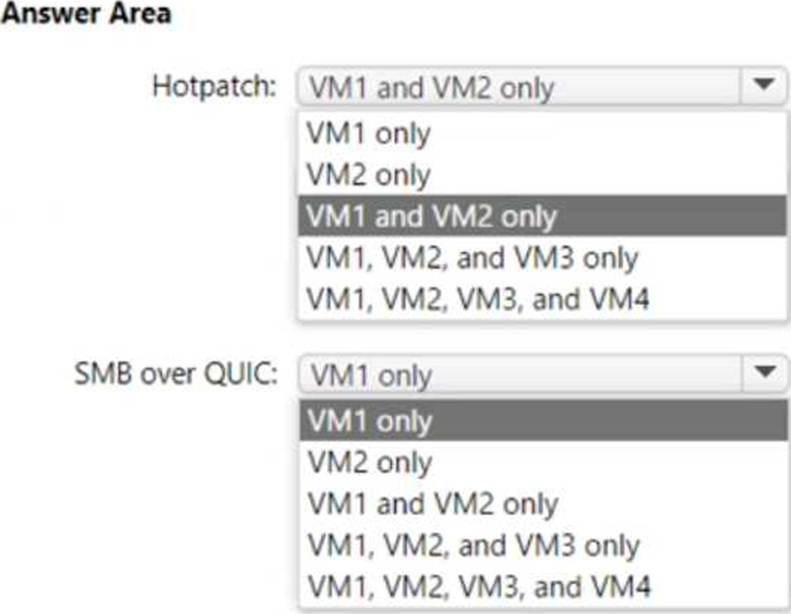
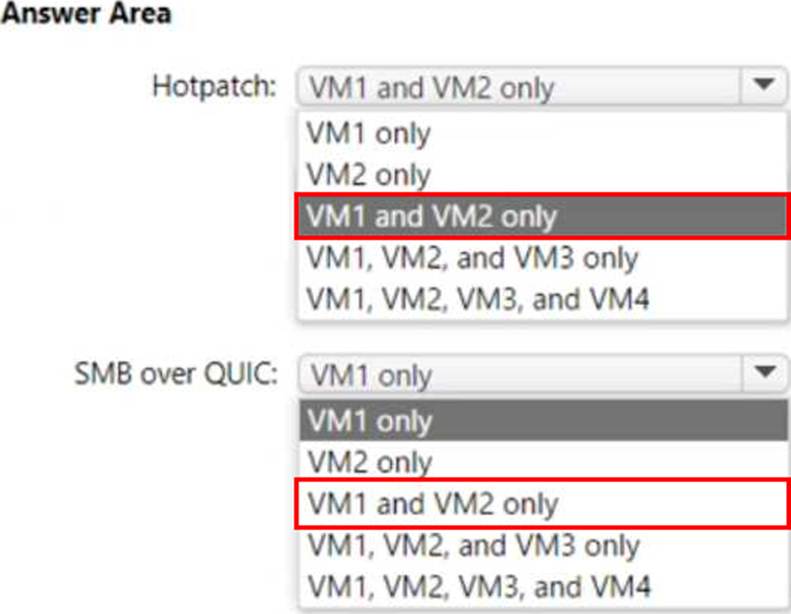
Explanation:
Hotpatch: VM1 and VM2 only
SMB over QUIC: VM1 and VM2 only
The Administering Windows Server Hybrid Core Infrastructure guidance for Azure Automanage and Windows Server 2022 features states that Hotpatch is available only for Azure VMs that run Windows Server 2022 Datacenter: Azure Edition. The materials describe Hotpatch as an Azure capability that “applies security updates to Windows Server 2022 Azure Edition without requiring a reboot in most cases,” and clarify that it is supported on both Desktop Experience and Server Core images of Azure Edition used in Azure IaaS. Therefore, only VM1 (Windows Server 2022 Datacenter: Azure Edition) and VM2 (Windows Server 2022 Datacenter: Azure Edition Core) meet the Hotpatch prerequisite. Regular Windows Server 2022 Datacenter (VM3) and Windows Server 2019 Datacenter (VM4) are not eligible for Hotpatch.
For file services, the same exam content explains that SMB over QUIC is a Windows Server 2022 feature limited to Azure Edition when acting as the SMB server endpoint: it “provides SMB encryption and TLS 1.3 over UDP (QUIC) to enable secure, VPN-less access to SMB shares” and is available on Windows Server 2022 Datacenter: Azure Edition. Consequently, only VM1 and VM2 can host SMB over QUIC. Standard Windows Server 2022 Datacenter (VM3) and Windows Server 2019 Datacenter (VM4) do not provide the SMB over QUIC server capability.
Thus, the correct selections are VM1 and VM2 only for both Hotpatch and SMB over QUIC.
You have servers that run Windows Server 2022 as shown in the following table.
Server2 contains a .NET app named App1.
You need to establish a WebSocket connection from App1 to the SQL Server instance on Server1.
The solution must meet the following requirements:
• Minimize the number of network ports that must be open on the on-premises network firewall.
• Minimize administrative effort.
What should you create first?
- A . an Azure Relay namespace
- B . an Azure VPN gateway
- C . a WFC relay connection
- D . a hybrid connection
A
Explanation:
The hybrid connectivity module details Azure Relay C Hybrid Connections for reaching on-premises services securely without inbound firewall rules. It states: “Hybrid Connections use WebSockets over outbound TCP 443 from both ends, enabling apps in Azure to connect to on-premises endpoints with no VPN and minimal firewall changes.” The setup sequence is: (1) Create an Azure Relay namespace, (2) Create a Hybrid Connection inside that namespace, and **(3) install the on-premises Hybrid Connection Manager to establish the outbound listener to Azure.” This approach meets the requirements: a WebSocket-based connection from App1 to SQL Server on Server1, minimizing open ports (only outbound 443) and administrative effort (no site-to-site VPN or complex routing). A VPN gateway would require additional configuration and more open ports; a WCF relay is a different relay type for WCF endpoints, not needed for generic TCP/WebSocket scenarios; and a hybrid connection cannot be created until a Relay namespace exists. Thus, the first object to create is an Azure Relay namespace.
