Practice Free AZ-800 Exam Online Questions
You have an on-premises Active Directory Domain Services (AD DS) domain that syncs with an Azure Active Directory (Azure AD) tenant Group writeback is enabled in Azure AD Connect.
The AD DS domain contains a server named Server1 Server 1 contains a shared folder named share1.
You have an Azure Storage account named storage2 that uses Azure AD-based access control. The storage2 account contains a share named shared
You need to create a security group that meets the following requirements:
• Can contain users from the AD DS domain
• Can be used to authorize user access to share 1 and share2
What should you do?
- A . in the AD DS domain, create a universal security group
- B . in the Azure AD tenant create a security group that has assigned membership
- C . in the Azure AD Tenant create a security group that has dynamic membership.
- D . in the Azure AD tenant create a Microsoft 365 group
B
Explanation:
The hybrid identity guidance for Windows Server and Azure emphasizes using Azure AD (Microsoft Entra ID) security groups for unified authorization across Azure Files (Azure Storage with Azure AD-based access control) and on-premises SMB shares―when Group writeback is enabled in Azure AD Connect. The documented pattern is: create the group in Azure AD with assigned membership so you can grant Azure roles/share permissions to storage2share2 using Azure AD identities. Because Group writeback is enabled, that Azure AD security group is written back to on-premises AD DS as a universal security group, allowing you to use the same group on NTFS/share permissions for Server1Share1. Members can be synchronized AD DS users; adding them in Azure AD (assigned membership) ensures predictable inclusion for both resources.
Creating the group only in AD DS (Option A) can sync to Azure, but the hybrid guidance highlights Azure-originated groups with writeback when you want one source to drive both cloud and on-prem authorization and to ensure compatibility with Azure Files’ Azure AD-based access checks. Dynamic membership (Option C) is unnecessary here and may not align with file access scenarios. Microsoft 365 groups (Option D) are not intended for file share ACLs/RBAC in this context. Thus, the verified solution is to create an Azure AD security group with assigned membership, taking advantage of group writeback for on-premises use.
HOTSPOT
You have a Windows Server 2022 container host named Host1 that has the Subsystem for Linux installed and the container images shown in the following table.
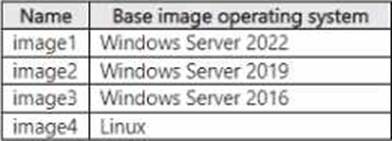
You need to deploy the images to Host1. The solution must maximize the isolation of the containers.
Which images can you run by using process isolation, and which images can you run by using Hyper-V isolation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
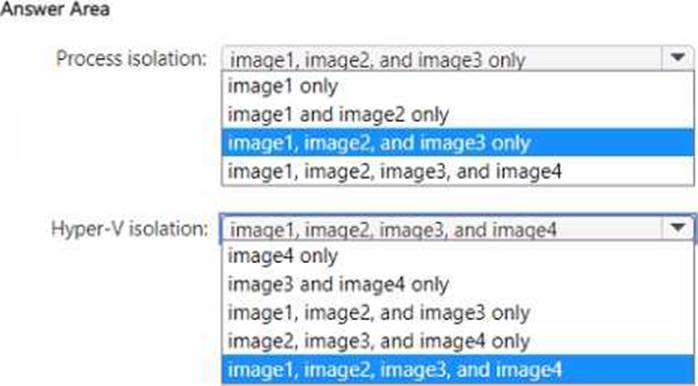
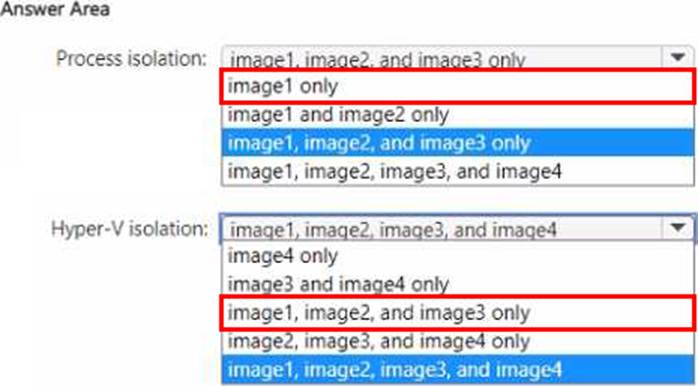
Process isolation: image1 only
Hyper-V isolation: image1, image2, image3, and image4
The Administering Windows Server Hybrid Core Infrastructure materials explain two Windows container isolation modes. For process isolation, the guide states that Windows Server containers share the host’s kernel and therefore require kernel/OS-version compatibility: “Process-isolated Windows containers run directly on the host and use the host’s kernel; the container image must match the host OS version/build.” Because Host1 is Windows Server 2022, only a Windows Server 2022 container image can be run with process isolation. Thus, among the images shown, image1 (Windows Server 2022) is the only one eligible for process isolation; 2019 and 2016 images have kernel mismatches and cannot run in that mode.
The same materials describe Hyper-V isolation as running each container inside a lightweight utility VM: “Hyper-VCisolated containers get their own kernel inside a special VM, removing the kernel version dependency on the host.” This mode “allows running different Windows versions than the host” and, when LCOW/WSL is present, it “enables running Linux containers on Windows” by supplying a Linux kernel within the utility VM. Since Host1 has the Subsystem for Linux installed, Hyper-V isolation can run Windows Server 2022, 2019, 2016 container images and also Linux containers. Therefore, to maximize isolation, you can run image1, image2, image3, and image4 with Hyper-V isolation, while process isolation is limited to image1 only.
SIMULATION
Task 10
You use a Group Policy preference to map \dd.contoso.cominstal1 as drive H for all users. If a user already has an existing drive mapping for H. the new drive mapping must take precedence.
Step 1: Open Group Policy Management Console Open the Group Policy Management Console (GPMC) on a machine that has administrative privileges over the domain.
Step 2: Create or Edit a GPO Create a new Group Policy Object (GPO) or edit an existing one that applies to the users who need the drive mapping.
Step 3: Navigate to Drive Mappings In the GPO Editor, navigate to:
User Configuration -> Preferences -> Windows Settings -> Drive Maps
Step 4: New Drive Mapping Right-click on Drive Maps and select New -> Mapped Drive.
Step 5: Configure Drive Mapping In the New Drive Properties window, configure the following settings:
Action: Select Replace. This action will overwrite any existing mappings with the same drive letter.
Location: Enter the UNC path \dd.contoso.cominstal1.
Drive Letter: Choose H: from the drop-down menu.
Reconnect: Check this option if you want the drive mapping to persist across logon sessions.
Label As: Optionally, provide a label for the drive mapping.
Hide/Show this drive: Set according to your preference.
Hide/Show all drives: Set according to your preference.
Step 6: Common Tab Go to the Common tab and configure the following:
Run in logged-on user’s security context (user policy option): Check this option.
Item-level targeting: Click on Targeting and set up any specific criteria if needed.
Step 7: Apply the GPO Click Apply and then OK to save the drive mapping configuration.
Step 8: Link the GPO Link the GPO to an Organizational Unit (OU) or domain that contains the users who should receive the drive mapping.
Step 9: Update Group Policy Instruct users to log off and log back on, or use the gpupdate /force command to refresh Group Policy on their computers.
HOTSPOT
You have a server named Server1 that runs Windows Server and has the Hyper-V server role installed.
You need 10 limit which Hyper-V module cmdlets helpdesk users can use when administering Server 1 remotely.
You configure Just Enough Administration (JEA) and successfully build the role capabilities and session configuration files.
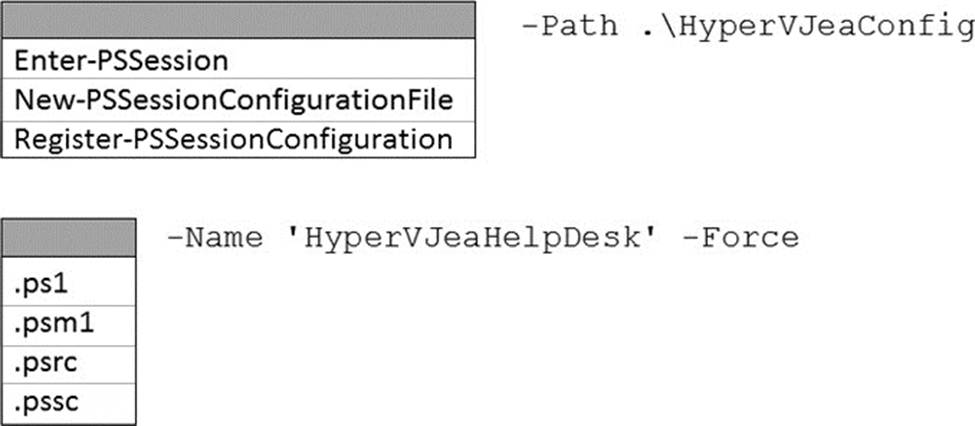
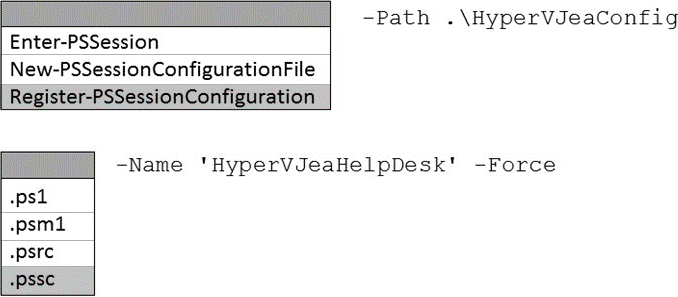
How should you complete the PowerShell command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
In Just Enough Administration (JEA), you restrict what remote users can do by publishing a PowerShell session endpoint that references a session configuration file and one or more role capability files. The AZ-800 “Administering Windows Server Hybrid Core Infrastructure” materials explain that a JEA deployment follows this order: (1) create role capability files (.psrc) in a module’s RoleCapabilities folder to enumerate allowed cmdlets, functions, and parameters; (2) author a session configuration file (.pssc)―typically with New-PSSessionConfigurationFile―that maps users or groups to the role capabilities; and (3) register the endpoint with Register-PSSessionConfiguration, supplying the .pssc path and a Name for the endpoint. Only after registration can helpdesk users connect to the constrained endpoint.
Critically, among the listed cmdlets, Register-PSSessionConfiguration is the one that accepts -Name and -Path to a .pssc file, which matches the prompt (-Path .hypervJeaConfig __ -Name ‘hypervJeaHelpDesk’ -Force). Enter-PSSession is for connecting to an already published endpoint, and New-PSSessionConfigurationFile creates the .pssc but does not publish it. Likewise, file types .ps1 (script), .psm1 (module), and .psrc (role capability) are not valid for the -Path parameter when registering an endpoint. Therefore, the correct completion is: Register-PSSessionConfiguration -Path .hypervJeaConfig.pssc -Name ‘hypervJeaHelpDesk’ -Force.
HOTSPOT
Your company has offices in Boston and Montreal. The offices are connected by using a 10-Mbps WAN link that is often saturated.
The office in Boston contains the following:
• An Active Directory Domain Services (AD DS) domain controller named DC1.
• A server named Server1 that runs Windows Server and has the File Server role installed
The office in Montreal contains 20 client computers that run Windows 10 Montreal does NOT have any servers.
The company plans to deploy a new line of business (LOB) application to all the client computers. The installation source files for the application are in \ServerApps.
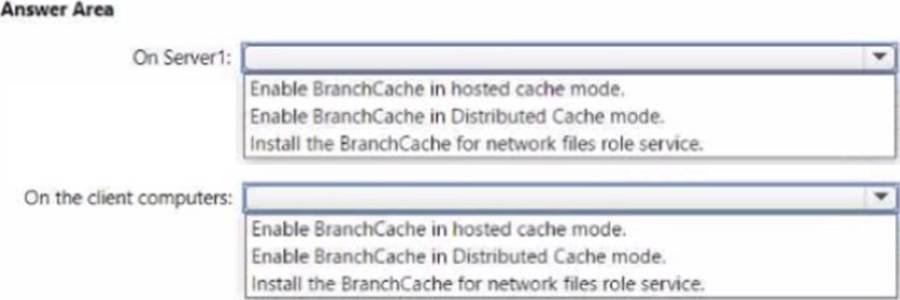
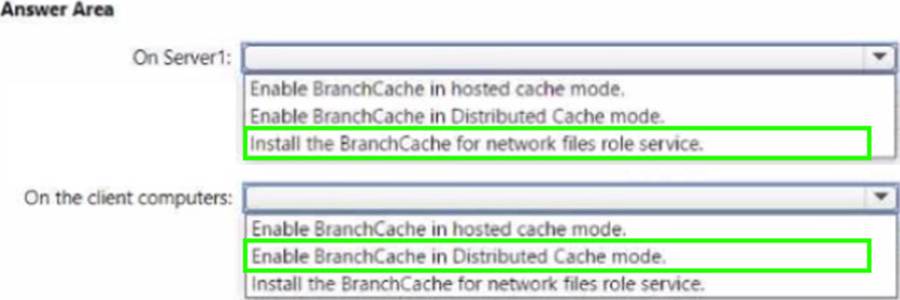
Explanation:
The Administering Windows Server Hybrid Core Infrastructure materials explain that BranchCache reduces WAN utilization by caching content that clients request from a remote content server. There are two modes: Hosted Cache and Distributed Cache. Hosted Cache “requires a server in the branch office configured as a hosted cache server,” while Distributed Cache “uses a peer-to-peer cache among Windows clients and does not require any servers in the branch.” For SMB shares, the content server (the file server at the main site) must have the “BranchCache for Network Files” role service installed so that it can advertise hashes and support BranchCache for file content. Client computers in the branch are then configured to Enable BranchCache in Distributed Cache mode so they can cache and retrieve content from each other, minimizing repeated downloads across the WAN.
In this scenario, Montreal has no servers, so Hosted Cache is not suitable. Installing BranchCache for Network Files on Server1 (the Boston file server hosting \Server1Apps) and enabling Distributed Cache on the 20 Windows 10 clients in Montreal meets the requirement to reduce WAN saturation during the LOB app deployment and subsequent updates while requiring no additional branch infrastructure.
SIMULATION
Task 3
You need to create 3 user named Admin1 in contoso.com. Admin1 must be able to back up and restore files on SRV1. The solution must use principle of the least privilege.
Objective:
Create a user named Admin1 in contoso.com.
Admin1 must be able to back up and restore files on SRV1.
Follow the principle of least privilege.
Step-by-Step Guide
✅ Step 1: Create the User Account
Log in to a Domain Controller (e.g., DC1) with appropriate admin rights.
Open Active Directory Users and Computers (dsa.msc).
In the contoso.com domain:
Right-click the Users container or another OU where you want to create the account.
Select New > User.
Enter the following:
First name: Admin1
User logon name: Admin1
Click Next and set a password (ensure it meets the domain’s password policy).
Configure password options (e.g., User must change password at next logon, if required).
Click Finish.
✅ Step 2: Grant Backup and Restore Rights on SRV1
By default, Backup Operators have the ability to back up and restore files (without giving full admin rights).
Log in to SRV1 (the target server).
Open Computer Management (compmgmt.msc).
In the left pane, expand:
System Tools > Local Users and Groups > Groups.
Find and double-click the Backup Operators group.
Click Add.
In the Select Users, Computers, Service Accounts, or Groups window:
Type Admin1.
Click Check Names to resolve the user.
Click OK to add Admin1 to the group.
Click OK again to close the Backup Operators group properties.
✅ Step 3: Verify Access
Log in as Admin1 on SRV1 and test performing backup and restore operations using tools like Windows Server Backup.
Since Backup Operators can back up and restore data but do not have full administrative privileges, this follows the least privilege principle.
✅ Additional Notes
If you prefer using PowerShell, you can add the user to the group like this on SRV1:
Add-LocalGroupMember -Group "Backup Operators" -Member "contosoAdmin1"
DRAG DROP
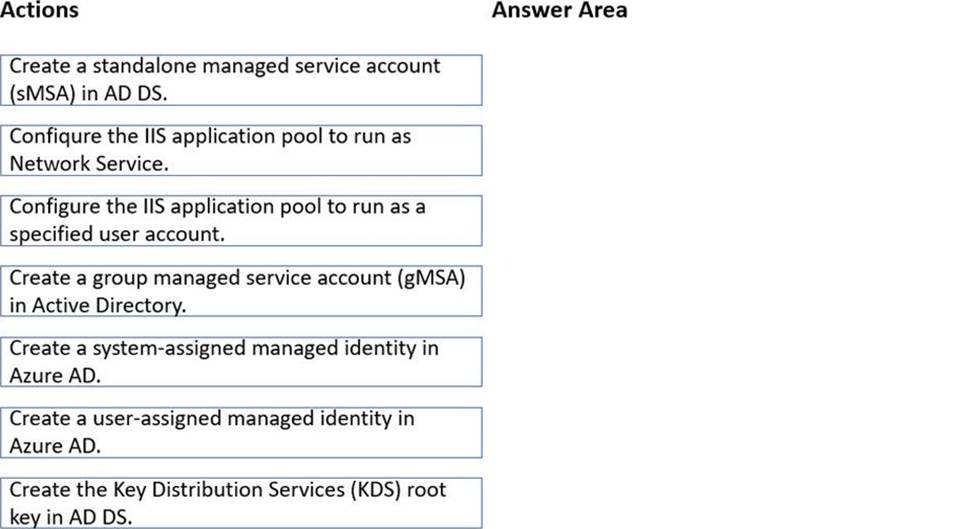
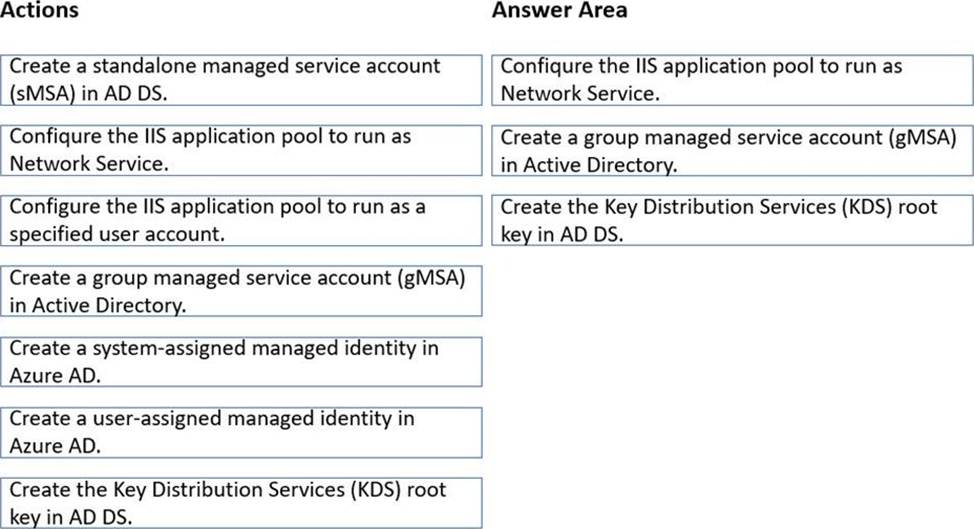
Which three actions should you perform in sequence to meet the security requirements for Webapp1? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Explanation:
In the Administering Windows Server Hybrid Core Infrastructure materials (AZ-800), Microsoft explains that Group Managed Service Accounts (gMSAs) are designed for services running on multiple servers and “provide automatic password management, simplified SPN management, and the ability to delegate the management to other administrators.” The guidance further states that before you can create any gMSA, “the domain must have a KDS root key so that the Key Distribution Service can generate and rotate strong, unique passwords for gMSAs on a schedule.” After the KDS root key is created, “use New-ADServiceAccount to create the gMSA and grant the computers (e.g., web servers) permission to retrieve the account password.” For IIS, the course notes specify that a gMSA can be used for app pools: “Configure the IIS application pool identity to a custom account and specify the gMSA name (ending with ‘$’) without a password; the password is managed automatically by AD and rotates by policy (for example, every 30 days).”
Mapping these requirements to the scenario: Webapp1 runs on WEB1 and WEB2 and must use the same service account with an automatic 30-day password change. Therefore, the correct sequence is: create the KDS root key, create the gMSA, and then set the IIS application pool to run under that account. This fulfills the security requirement while allowing both web servers to share the same, automatically-rotated credentials.
You have an on-premises Active Directory Domain Services (AD DS) domain that syncs with an Azure Active Directory (Azure AD) tenant
You have several Windows 10 devices that are Azure AD hybrid-joined.
You need to ensure that when users sign in to the devices, they can use Windows Hello for Business.
Which optional feature should you select in Azure AD Connect?
- A . Device writeback
- B . Group writeback
- C . Password writeback
- D . Directory extension attribute sync
- E . Azure AD app and attribute filtering
A
Explanation:
The Windows Server Hybrid Core Infrastructure materials explain that Windows Hello for Business (WHfB) in a hybrid environment relies on Azure AD registration and corresponding device objects in on-premises AD DS. Azure AD Connect provides the Device writeback optional feature, which “writes Azure AD device objects back to AD DS as msDS-Device objects so on-premises domain controllers and policies can recognize and evaluate the device during authentication.” The guide further notes that for hybrid-joined Windows 10/11 devices, enabling Device writeback “allows on-premises authentication stacks and Conditional Access decisions to use the registered device and its key material (key trust or certificate trust), enabling WHfB sign-in on domain-joined devices.” Other options do not meet the requirement: Password writeback is used for self-service password reset, Group writeback returns Microsoft 365 groups to AD DS, and Directory extension attribute sync simply synchronizes custom attributes. Therefore, to ensure users can sign in with Windows Hello for Business on Azure AD hybrid-joined devices, select Device writeback in Azure AD Connect.
You have an on-premises Active Directory Domain Services (AD DS) domain that syncs with an Azure Active Directory (Azure AD) tenant. You plan deploy 100 new Azure virtual machines that will run Windows Server. You need to ensure that each new virtual machine is joined to the AD DS domain.
What should you use?
- A . Azure AD Connect
- B . a Group Policy Object (GPO)
- C . an Azure Resource Manager (ARM) template
- D . an Azure management group
C
Explanation:
Reference: In Administering Windows Server Hybrid Core Infrastructure (AZ-800) guidance on deploying and managing Windows Server IaaS VMs, Microsoft emphasizes automating domain join during provisioning by using Azure VM extensions within an Azure Resource Manager (ARM) template. The supported method for joining Azure VMs to an on-premises AD DS domain is the Json AD Domain Extension (Microsoft.Compute/virtualMachines/extensions). In the ARM template, you provide parameters such as the AD DS domain name, OUPath (optional), User (a domain account with join rights), Password (as a secure parameter), Restart (true/false), and Options. When the VM is created, the extension executes on first boot and performs the classic AD DS domain join, ensuring every newly deployed VM is joined consistently and at scale.
By contrast, Azure AD Connect (A) only synchronizes identities between AD DS and Azure AD; it does not join Windows Server computers to AD DS. A GPO (B) can configure domain-joined computers after they are in the domain, but it cannot join non-domain systems. Azure management groups (D) provide governance and hierarchy for subscriptions and policies, not machine domain-join operations. Therefore, to ensure that 100 newly deployed Windows Server VMs are automatically joined to the on-premises AD DS domain during deployment, the verified and supported approach is to use an ARM template with the Json AD Domain Extension.
HOTSPOT
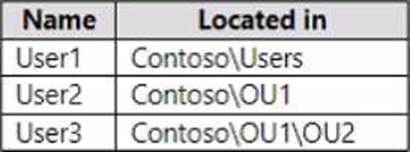
Your network contains an Active Directory Domain Services (AD DS) domain named contoso.com.
The domain contains the users shown in the following table.
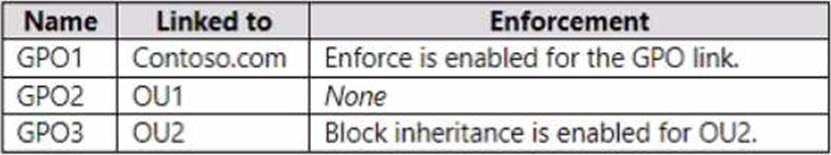
The domain has the Group Policy Objects (GPOs) shown in the following table.
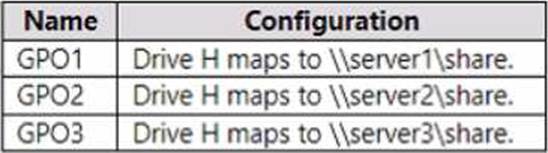
The GPOs are configured to map a drive named H as shown in the following table.
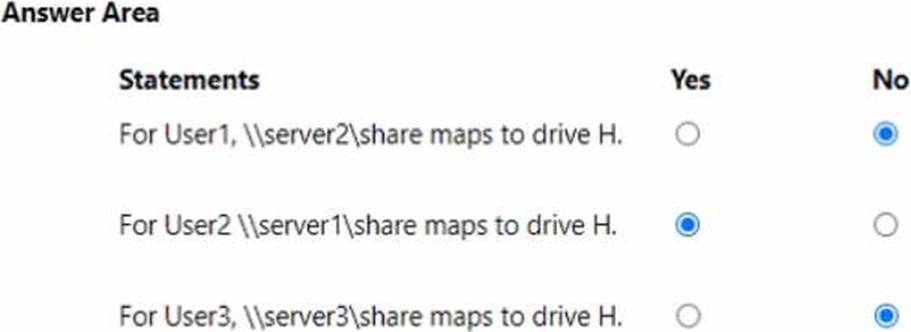
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
For User1, \server2share maps to drive H.: No
For User2, \server1share maps to drive H.: Yes
For User3, \server3share maps to drive H.: No
The Administering Windows Server Hybrid Core Infrastructure materials explain that Group Policy is processed in the order Local → Site → Domain → OU, with the last applied policy normally taking precedence. Two modifiers change this behavior: Enforced (No override) on a GPO link and Block inheritance on a container/OU. The guide states that an Enforced link “prevents child containers from overriding settings in that GPO,” while Block inheritance “prevents higher-level GPOs from applying except those marked Enforced.”
Applying these rules:
User1 (ContosoUsers) is not in OU1, so GPO2 (drive H to \server2share) does not apply. Only domain-level GPOs apply to the Users container; thus, the statement for \server2share is No.
User2 (OU1) receives GPO1 (Domain, Enforced) and GPO2 (OU1). Because GPO1 is Enforced, its mapping (H → \server1share) cannot be overridden by GPO2, so the statement is Yes.
User3 (OU1OU2) is in OU2, which has Block inheritance. This blocks higher GPOs except those Enforced, so GPO1 still applies and GPO2 is blocked. Although GPO3 (OU2) also applies, the Enforced domain GPO (GPO1) takes precedence over conflicting lower-level settings, so H: remains \server1share, making the statement about \server3share No.
