Practice Free AZ-800 Exam Online Questions
You have an Azure virtual machine named VM1 that has a private IP address only.
You configure the Windows Admin Center extension on VM1.
You have an on-premises computer that runs Windows 11. You use the computer for server management.
You need to ensure that you can use Windows Admin Center from the Azure portal to manage VM1.
What should you configure?
- A . an Azure Bastion host on the virtual network that contains VM1.
- B . a VPN connection to the virtual network that contains VM1.
- C . a network security group 1NSG) rule that allows inbound traffic on port 443.
- D . a private endpoint on the virtual network that contains VM1.
B
Explanation:
According to the official documentation for Administering Windows Server Hybrid Core Infrastructure, using Windows Admin Center (WAC) within the Azure portal to manage virtual machines requires specific network pathing depending on the IP configuration of the target VM. For a virtual machine like VM1 that is configured with only a private IP address, the management traffic originates from the browser on the administrator’s local computer and must be able to reach that private IP address directly.
The primary requirement for this scenario is that the management PC must have access to the virtual network (VNet) that is connected to the VM. As specified in the study guides, when managing a VM via its private IP, you must establish a hybrid connectivity solution such as a VPN connection (either Point-to-Site or Site-to-Site) or Azure ExpressRoute. This bridge allows the on-premises Windows 11 computer to route traffic into the Azure Virtual Network’s private address space. Without this underlying network connectivity, the browser-based WAC gateway―which is hosted as an extension on the VM―cannot communicate with the portal interface.
While Azure Bastion (Option A) provides secure RDP and SSH access, the Windows Admin Center extension specifically requires network-level routing from the client to the private IP for its portal-integrated management features. Network Security Group (NSG) rules (Option C) are necessary to allow traffic on specific ports (like 443 for the WAC service), but they do not provide the routing necessary to cross the boundary between an on-premises network and an Azure VNet. Similarly,
Private Endpoints (Option D) are intended for accessing Azure PaaS services rather than providing a management path for IaaS VMs. Therefore, configuring a VPN connection is the verified mandatory step to satisfy the connectivity requirements for WAC in this hybrid context.
HOTSPOT
Your on-premises network contains an Active Directory Domain Services (AD DS) domain.
You plan to sync the domain with a Microsoft Entra tenant by using Microsoft Entra Connect cloud sync.
You need to meet the following requirements:
• Install the software required to sync the domain and Microsoft Entra ID.
• Enable password hash synchronization.
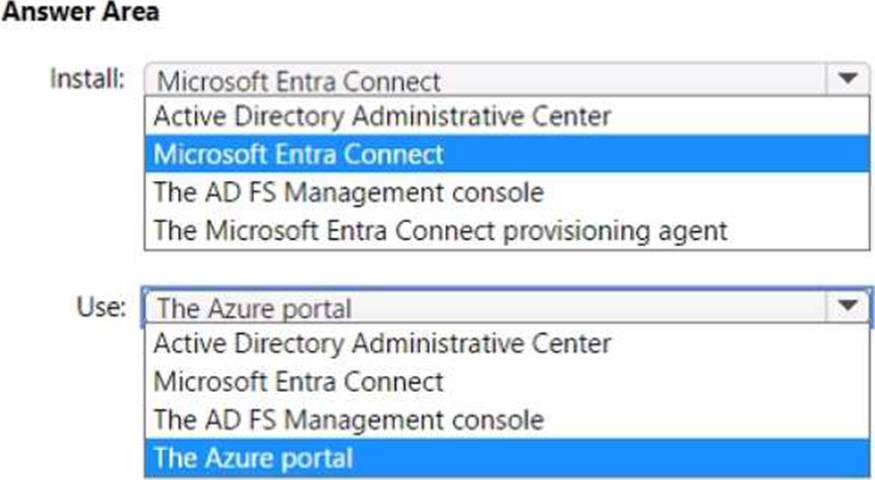
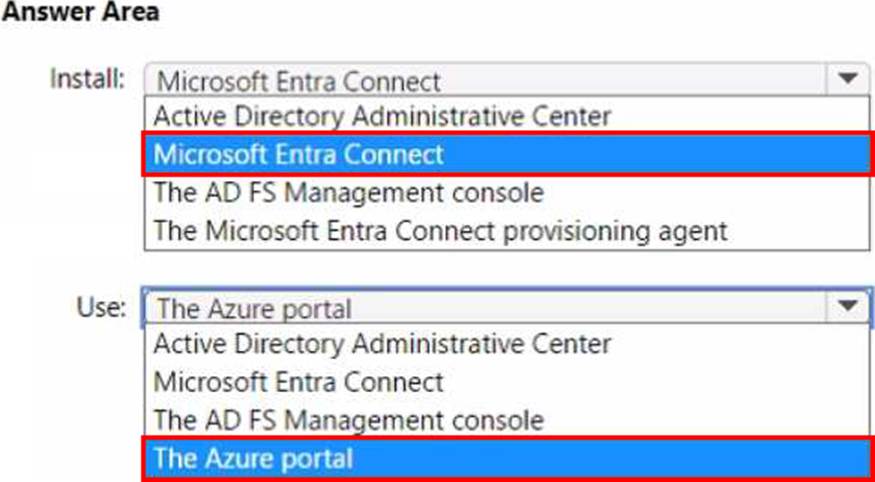
What should you install, and what should you use to enable password hash synchronization? To answer, select the appropriate options in the answer area.
Explanation:
In a cloud-sync deployment, Microsoft’s hybrid identity guidance for Administering Windows Server Hybrid Core Infrastructure specifies that you do not install the full Microsoft Entra (Azure AD) Connect server. Instead, cloud sync “uses a lightweight agent―called the Microsoft Entra Connect provisioning agent―installed on one or more Windows Server computers that can reach your AD DS domain controllers.” The agent handles directory read operations and securely communicates with the cloud provisioning service. The study material further states that all configuration―including creating sync configurations, scoping filters, and enabling features such as Password Hash Synchronization (PHS)―is performed in the Microsoft Entra admin experience: “Cloud sync is configured in the Azure portal; you create a cloud sync configuration, select the on-premises AD forest, and enable password hash synchronization so password hashes are synchronized to Microsoft Entra ID.”
Because you are using Microsoft Entra Connect cloud sync, the correct software to install on-premises is the Microsoft Entra Connect provisioning agent (not the full Microsoft Entra Connect server or ADFS tools). And to enable PHS for cloud sync, you use the Azure portal (Microsoft Entra admin center) to turn on Password hash synchronization within the cloud sync configuration. This meets both requirements: installing the proper agent for cloud sync and enabling PHS centrally in the portal.
Your network contains an Active Directory domain named contoso.com.
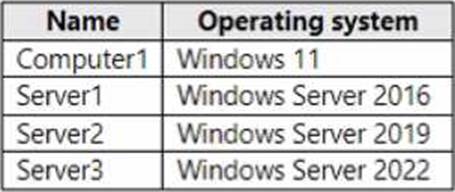
The domain contains the computers shown in the following table.
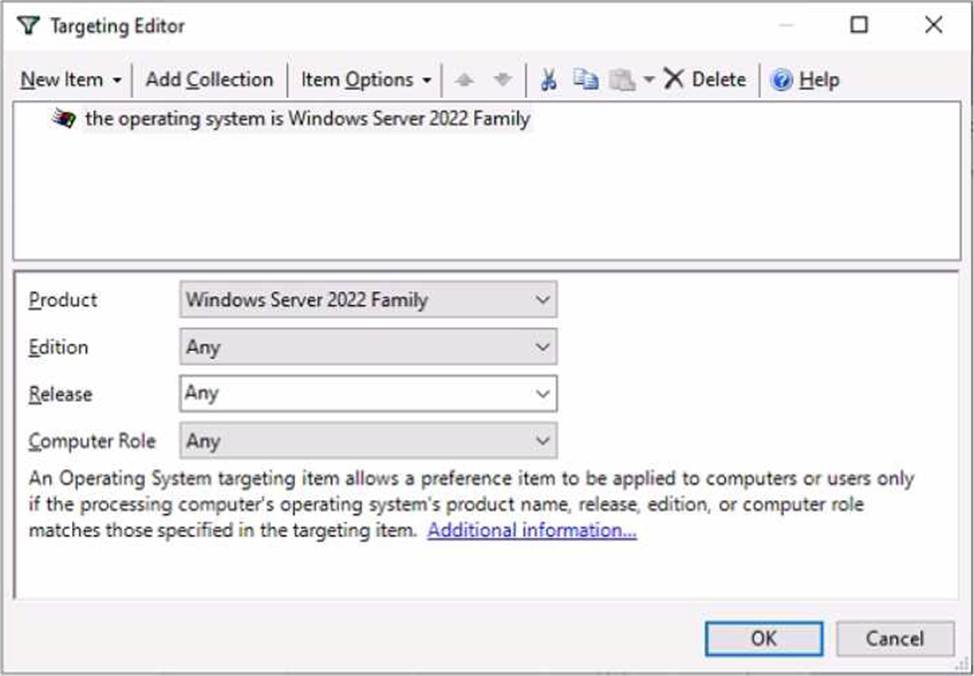
On Server3, you create a Group Policy Object (GPO) named GP01 and link GPOI to contoso.com. GP01 includes a shortcut preference named Shortcut1 that has item-level targeting configured as shown in the following exhibit.
To which computer will Shortcut1 be applied?
- A . Server3 only
- B . Computer1 and Server3 only
- C . Server2 and Server3 only
- D . Server1, Server2, and Server3 only
A
Explanation:
Group Policy Preferences support Item-Level Targeting (ILT), allowing a preference item to apply only when the target computer meets specified criteria, such as operating system family and version. The AZ-800 study content notes that when a GPO is linked at the domain level, scope is all domain computers, but ILT on a specific preference item restricts that item to clients that match the ILT filter; non-matching clients still process the GPO but skip the filtered item. In the Targeting Editor shown, the condition is “the operating system is Windows Server 2022 Family.” Among the listed machines: Computer1 (Windows 11), Server1 (Windows Server 2016), Server2 (Windows Server 2019), and Server3 (Windows Server 2022). Only Server3 satisfies the ILT. Therefore, the shortcut preference Shortcut1 is applied only to Server3.
Your network contains a single-domain Active Directory Domain Services (AD DS) forest named conto.com.
The forest contains the servers shown in the following exhibit table.
You plan to install a line-of-business (LOB) application on Server1. The application will install a custom windows services.
A new corporate security policy states that all custom Windows services must run under the context of a group managed service account (gMSA). You deploy a root key.
You need to create, configure, and install the gMSA that will be used by the new application.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . On Server1, run the install-ADServiceAccount cmdlet.
- B . On DC1, run the New-ADServiceAccount cmdlet.
- C . On DC1, run the Set_ADComputer cmdlet.
- D . ON DC1, run the Install-ADServiceAccount cmdlet.
- E . On Server1, run the Get-ADServiceAccount cmdlet.
B,C
Explanation:
The AZ-800 objectives for securing Windows Server services with group Managed Service Accounts (gMSAs) specify a two-stage process: (1) Create the gMSA in AD DS, and (2) install (make usable) the gMSA on the member server that will run the service. The documentation outlines: first ensure a KDS root key is present (done), then on a domain controller run New-ADServiceAccount to create the gMSA, define SPNs as needed, and set PrincipalsAllowedToRetrieveManagedPassword to include the target server(s). Next, on each server that will use the account, install the account by running Install-ADServiceAccount, and then configure the Windows service to run under the gMSA (accountname$ with “Service accounts” logon). Running Install-ADServiceAccount on a DC is incorrect because the account must be installed on the workload host (Server1). Set-ADComputer is not required for gMSA deployment, and Get-ADServiceAccount merely queries objects and does not create or install them. Therefore, the correct actions are B (create the gMSA on DC1) and A (install the gMSA on Server1).
Your network contains an Active Directory Domain Services (AD DS) forest.
The forest contains the servers shown in the following table.
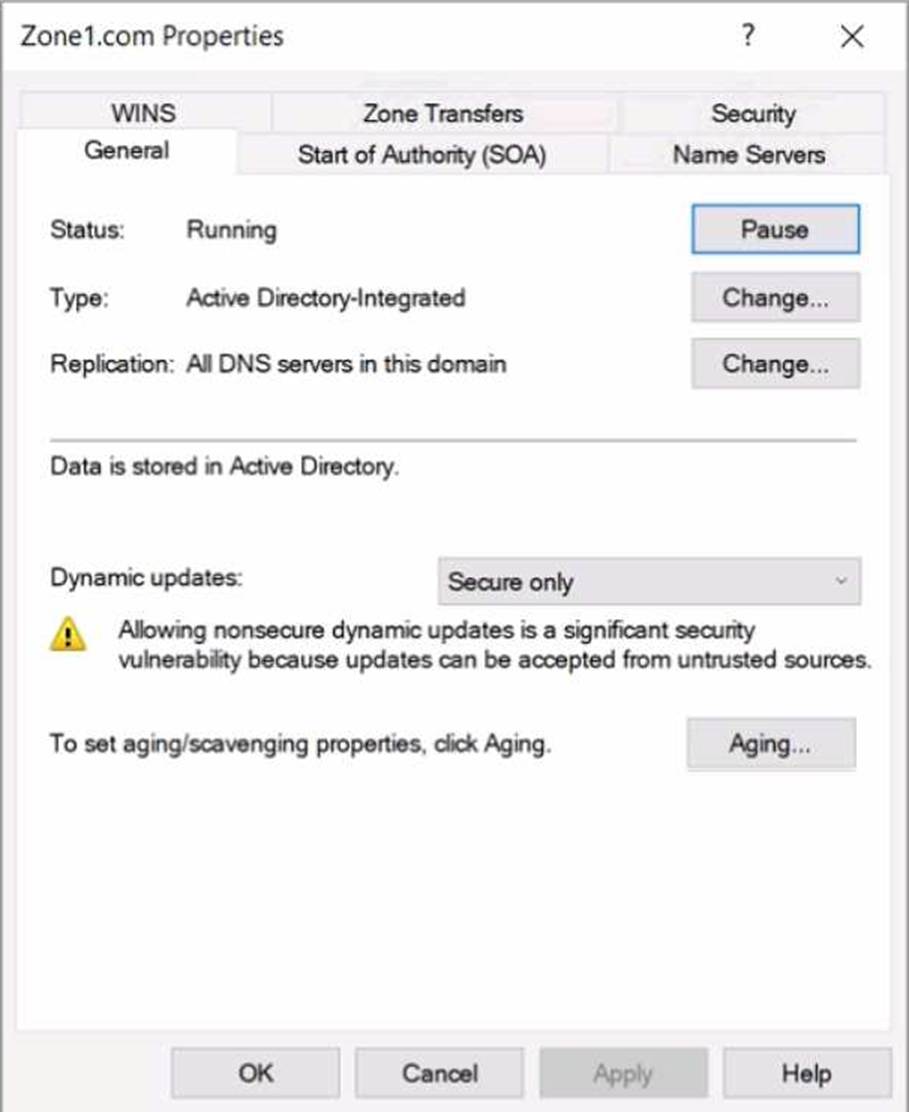
On Server1, you create a DNS zone named Zone1.com as shown in the following exhibit.
To which DNS servers is Zone1.com replicated?
- A . Server2 only
- B . Server2 and Server3 only
- C . Setver2 and Sen/er4 only
- D . Server2. Server3, and Server4 only
- E . Server2, Server3, Server4, and Server5
A
Explanation:
In the Windows Server DNS guidance within Administering Windows Server Hybrid Core Infrastructure, an Active DirectoryCintegrated zone stores its data in AD DS and replicates based on the replication scope selected in the zone’s properties. The option “All DNS servers in this domain” replicates the zone to the DomainDNSZones application partition of that domain, which is held only on domain controllers that run the DNS Server role in the same domain. The materials emphasize two key points: (1) AD-integrated zones can be hosted only on DNS servers that are also domain controllers, and (2) replication scope set to “this domain” does not cross to other domains or child domains.
Given the server list: Server1 and Server2 are DCs with DNS in contoso.com; Server3 is DNS-only (not a DC) in contoso.com; Server4/Server5 are in east.contoso.com (a different domain). Therefore, with the scope set to All DNS servers in this domain, replication targets only the other DNS-enabled DCs in contoso.com. Since you created the zone on Server1, it will replicate to Server2 only; Server3 cannot host AD-integrated zones, and Server4/Server5 are in a different domain and are not in scope.
HOTSPOT
You have an on-premises DNS server named Server1 that runs Windows Server. Server 1 hosts a DNS zone named fabrikam.com
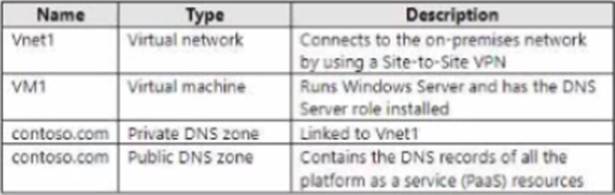
You have an Azure subscription that contains the resources shown in the following table.
Explanation:
In the Administering Windows Server Hybrid Core Infrastructure guidance for name resolution with Azure Private DNS, Microsoft describes the split-horizon scenario where you host contoso.com both as a Public DNS zone and as an Azure Private DNS zone linked to a virtual network. The documentation explains that Azure Private DNS “is resolvable only from within the VNet” and that the special Azure DNS virtual IP 168.63.129.16 is the target used by workloads inside the VNet to resolve private zone records. For hybrid resolution from on-premises, the guidance states that you deploy a DNS forwarder/proxy VM in the VNet (a Windows Server DNS role is acceptable) and configure it with a conditional forwarder for the private zone that forwards to 168.63.129.16. Then, on the on-premises DNS servers, you create a conditional forwarder for the same zone that points to the DNS forwarder VM in Azure across the Site-to-Site VPN. This pattern ensures on-premises queries for contoso.com resolve the private zone records via Azure, while public Internet clients continue to use the public DNS zone.
Consequently:
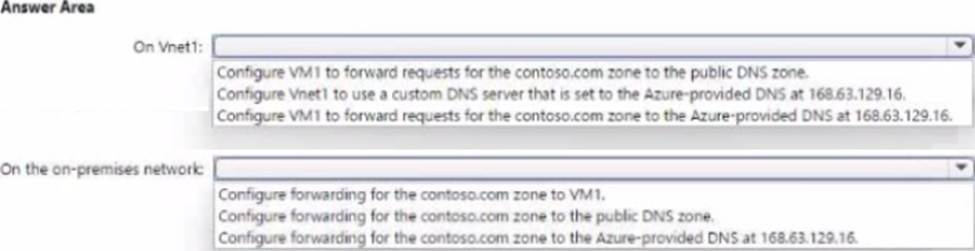
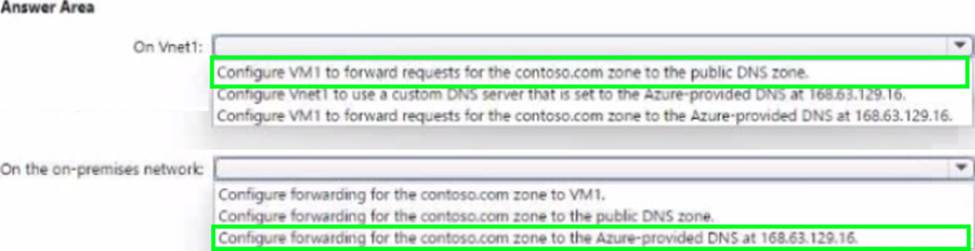
On VNet1, VM1 (DNS server) must forward contoso.com queries to 168.63.129.16.
On the on-premises DNS, configure a conditional forwarder for contoso.com to VM1.
Setting VNet DNS to the Azure-provided IP is unnecessary (it’s the default for Azure VMs) and forwarding to the public zone would bypass the private zone, which is not desired.
HOTSPOT
You need to meet the technical requirements for VM1.
Which cmdlet should you run first? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
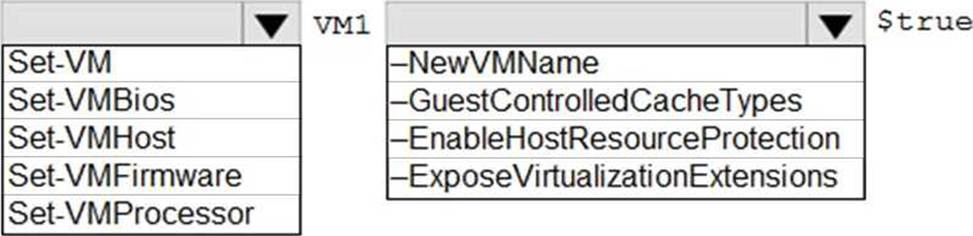
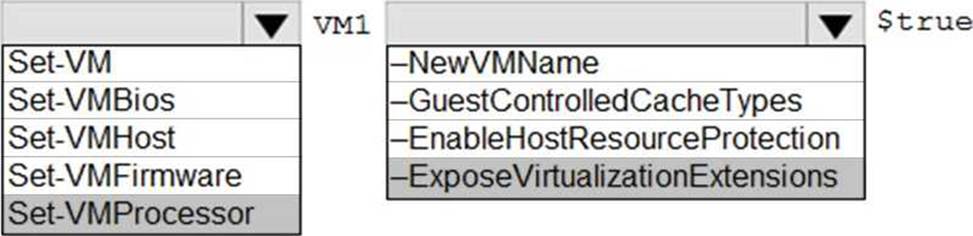
In the Administering Windows Server Hybrid Core Infrastructure objectives for managing Hyper-V, enabling nested virtualization is the required step when you must “run virtual machines inside a virtual machine.” The referenced guidance states that Hyper-V on a VM is supported only when the host exposes hardware virtualization features to the guest. The prescriptive step is: “Turn off the VM and run Set-VMProcessor -VMName <VMName> -ExposeVirtualizationExtensions $true to enable nested virtualization.” The module further notes that this action “passes through Intel VT-x/AMD-V to the guest so the guest OS can install the Hyper-V role and create VMs.” It also clarifies that “the setting is applied on the parent host for the target VM and requires the VM to be powered off before the change is committed.”
Because the technical requirement says “Ensure that you can run virtual machines on VM1”, VM1 must be able to host Hyper-V while itself running as a VM on Server2. The first and essential cmdlet is therefore Set-VMProcessor with the -ExposeVirtualizationExtensions switch set to $true against VM1. Other optional settings (for example, MAC spoofing on the vNIC or static memory) may be configured later if needed, but exposing virtualization extensions is the enabling prerequisite that satisfies the requirement.
You have an Azure virtual machine named VM1 that runs Windows Server.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You need to ensure that you can use the Azure Policy guest configuration feature to manage VM1.
What should you do?
- A . Add the PowerShell Desired State Configuration (DSC) extension to VM1.
- B . Configure VM1 to use a user-assigned managed identity.
- C . Configure VM1 to use a system-assigned managed identity.
- D . Add the Custom Script Extension to VM1.
C
Explanation:
Reference: The Administering Windows Server Hybrid Core Infrastructure materials covering Microsoft Defender for Cloud and Azure Policy guest configuration explain that guest configuration policies use a guest configuration extension and a managed identity on the VM to retrieve policy artifacts and report compliance. The text emphasizes: “When using Azure Policy guest configuration (audit or deployIfNotExists/modify), the virtual machine must have a managed identity enabled. The platform uses the VM’s managed identity to securely access content and to send compliance data.” It further clarifies that installing DSC or Custom Script extensions is not required to enable the Azure Policy guest configuration feature; the policy assignment deploys the needed guest configuration extension automatically when the VM has an identity. A system-assigned managed identity is the simplest least-privilege option because its lifecycle is tied to the VM and it requires no separate credential management. Hence, enabling a system-assigned managed identity on VM1 fulfills the prerequisite for Azure Policy guest configuration to manage the server.
HOTSPOT
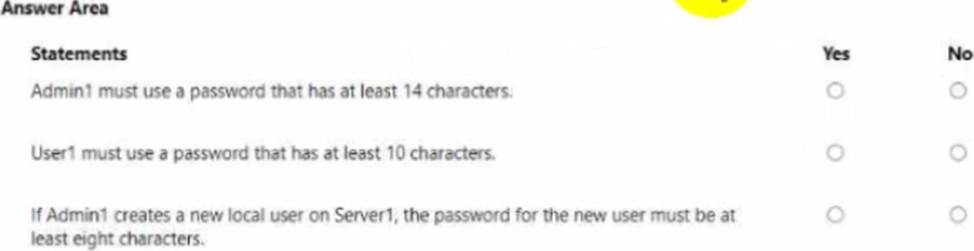
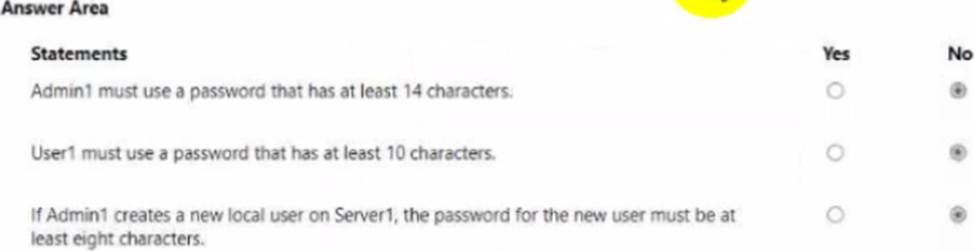
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
No
Yes
Yes
In Administering Windows Server Hybrid Core Infrastructure, Microsoft states that the domain password policy for domain user accounts is determined by the GPO that wins at the domain root (commonly the Default Domain Policy). GPOs linked to OUs do not change the domain password policy for user accounts in those OUs; they only affect local accounts on computers within those OUs unless Fine-Grained Password Policies (PSOs) are used and scoped to users/groups. The case shows Default Domain Policy in contoso.com sets Minimum password length = 10. Therefore, both Admin1 (a domain user in ContosoOU1) and User1 (in ContosoOU3) fall under the 10-character minimum; the OU-linked GPO1 (14) does not override the domain password policy for their domain accounts → Admin1: No, User1: Yes.
For member servers and local accounts, the documentation explains that password policy settings in a GPO linked to the OU containing the computer apply to that computer’s local Security Accounts Manager (SAM). In the scenario, Server1 resides in Member Servers and GPO2 linked to Member Servers specifies Minimum password length = 8. Thus, when Admin1 creates a local account on Server1, the enforced minimum is 8 characters → Yes. This approach follows least privilege and standard precedence: domain-level for domain accounts, OU-linked GPOs for local accounts, unless PSOs are explicitly defined.
Your network contains an Active Directory Domain Services (AD DS) domain named contoso.com.
The domain contains the servers shown in the following table.
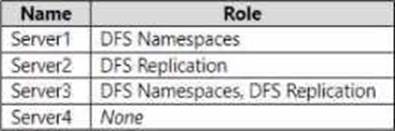
You need to create a Distributed File System (DFS) namespace that will contain the following:
• A domain-based namespace named \contoso.comPublic
• A folder named Finance
Which servers can you configure as folder targets for the Finance folder?
- A . Setver3 only
- B . Server2 and Servers only
- C . Server1 and Server3 only
- D . Server1, Server2, and Server 3 only
- E . Server1, Server2, Server3, and Server4
E
Explanation:
In the Administering Windows Server Hybrid Core Infrastructure materials for DFS, Microsoft explains that a DFS Namespace presents a virtual tree of folders, and each folder can have one or more folder targets. A folder target is simply “a UNC path to a shared folder that contains the actual data.” The guide emphasizes that folder targets do not need the DFS Namespaces role installed; the role is only required on namespace servers that host the namespace itself. Likewise, DFS Replication (DFSR) is optional―you enable it only when you want to keep the contents of multiple folder targets synchronized. The text states that “any SMB share on any Windows server (or cluster) can be used as a folder target,” and that “DFSR is used to replicate the data between folder targets but is not a prerequisite for configuring a target.”
Applying this to the scenario: you are creating a domain-based namespace \contoso.comPublic and a folder Finance. The namespace servers must have the DFS Namespaces role (e.g., Server1/Server3), but folder targets for Finance can reside on any server hosting an SMB share, regardless of whether the DFS Namespaces or DFS Replication roles are installed. Therefore, Server1, Server2, Server3, and Server4 can all be configured as folder targets for the Finance folder.
