Practice Free AZ-305 Exam Online Questions
HOTSPOT
You have a resource group named RG1 that contains the objects shown in the following table.
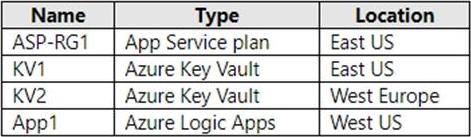
You need to configure permissions so that App1 can copy all the secrets from KV1 to KV2. App1 currently has the Get permission for the secrets in KV1.
Which additional permissions should you assign to App1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
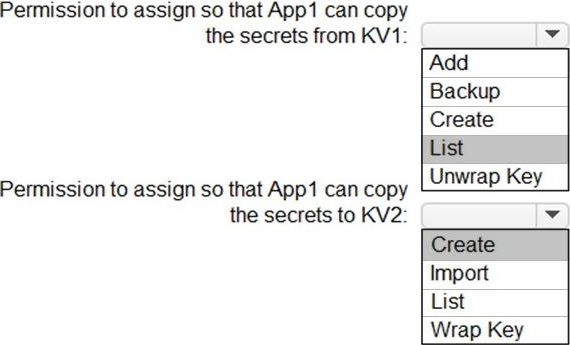
Explanation:
Box 1: List
Get: Gets the specified Azure key vault.
List: The List operation gets information about the vaults associated with the subscription.
Box 2: Create
Create Or Update: Create or update a key vault in the specified subscription.
Reference: https://docs.microsoft.com/en-us/rest/api/keyvault/
You are developing a sates application that will contain several Azure cloud services and handle different components of a transaction. Different cloud services will process customer orders, billing, payment inventory, and shipping.
You need to recommend a solution to enable the cloud services to asynchronously communicate transaction information by using XML messages.
What should you include in the recommendation?
- A . Azure Data Lake
- B . Azure Notification Hubs
- C . Azure Queue Storage
- D . Azure Service Fabric
HOTSPOT
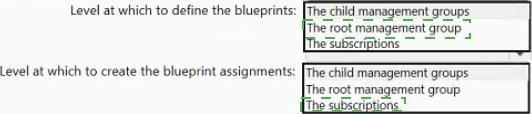
You plan to create an Azure environment that will contain a root management group and 10 child management groups. Each child management group will contain five Azure subscriptions. You plan to have between 10 and 30 resource groups in each subscription.
You need to design an Azure governance solution.
The solution must meet the following requirements:
• Use Azure Blueprints to control governance across all the subscriptions and resource groups.
• Ensure that Blueprints-based configurations are consistent across all the subscriptions and resource groups.
• Minimize the number of blueprint definitions and assignments.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

Explanation:
HOTSPOT
You have the Azure resources shown in the following table.
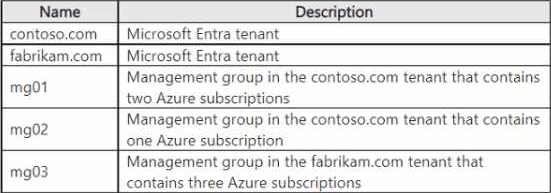
You need to recommend a virtual network management solution that uses Azure Virtual Network Manager.
The solution must meet the following requirements:
• Minimize the number of network managers.
• Minimize administrative effort when assigning the network group membership.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
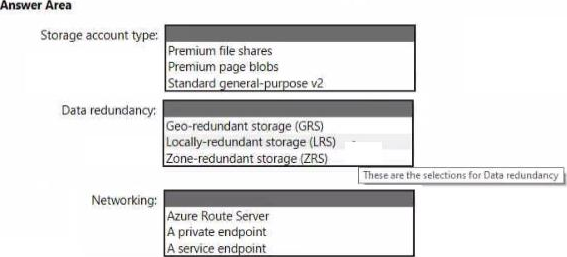
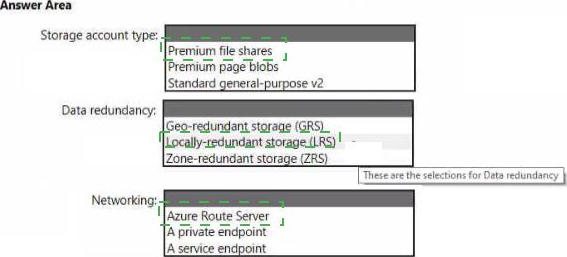
You are designing an application that will use Azure Linux virtual machines to analyze video files. The files will be uploaded from corporate offices that connect to Azure by using ExpressRoute.
You plan to provision an Azure Storage account to host the files.
You need to ensure that the storage account meets the following requirements:
• Supports video files of up to 7 TB
• Provides the highest availability possible
• Ensures that storage is optimized for the large video files
• Ensures that files from the on-premises network are uploaded by using ExpressRoute
How should you configure the storage account? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You ate designing a SQL database solution. The solution will include 20 databases that will be 20 GB each and have varying usage patterns. You need to recommend a database platform to host the databases.
The solution must meet the following requirements:
• The compute resources allocated to the databases must scale dynamically.
• The solution must meet an SLA of 99.99% uptime.
• The solution must have reserved capacity.
• Compute charges must be minimized.
What should you include in the recommendation?
- A . 20 databases on a Microsoft SQL server that runs on an Azure virtual machine
- B . 20 instances of Azure SQL Database serverless
- C . 20 databases on a Microsoft SQL server that runs on an Azure virtual machine in an availability set
- D . an elastic pool that contains 20 Azure SQL databases
D
Explanation:
Azure SQL Database elastic pools are a simple, cost-effective solution for managing and scaling multiple databases that have varying and unpredictable usage demands. The databases in an elastic pool are on a single server and share a set number of resources at a set price. Elastic pools in Azure SQL Database enable SaaS developers to optimize the price performance for a group of databases within a prescribed budget while delivering performance elasticity for each database.
Guaranteed 99.995 percent uptime for SQL Database
Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/database/elastic-pool-overview
https://azure.microsoft.com/en-us/pricing/details/sql-database/elastic/
https://www.azure.cn/en-us/support/sla/virtual-machines/
https://techcommunity.microsoft.com/t5/azure-sql/optimize-price-performance-with-compute-auto-scaling-in-azure/ba-p/966149
Your company, named Contoso, Ltd., implements several Azure logic apps that have HTTP triggers.
The logic apps provide access to an on-premises web service.
Contoso establishes a partnership with another company named Fabrikam. IncL
Fabrikam does not have an existing Azure Active Directory (Azure AD) tenant and uses third-party OAuth 2.0 identity management to authenticate its users.
I Developers at Fabrikam plan to use a subset of the logic apps to build applications that will integrate with the on-premises web service of Contoso.
You need to design a solution to provide the Fabrikam developers with access to the logic apps.
The solution must meet the following requirements:
• Requests to the logic apps from the developers must be limited to lower rates than the requests from the users at Contoso.
• The developers must be able to rely on their existing OAuth 2.0 provider to gain access to the logic apps.
• The solution must NOT require changes to the logic apps.
• The solution must NOT use Azure AD guest accounts.
What should you include in the solution?
- A . Azure AD business-to-business (B2B)
- B . Azure AD Application Proxy
- C . Azure Front Door
- D . Azure API Management
D
Explanation:
API Management helps organizations publish APIs to external, partner, and internal developers to unlock the potential of their data and services.
You can secure API Management using the OAuth 2.0 client credentials flow.
Reference:
https://docs.microsoft.com/en-us/azure/api-management/api-management-key-concepts
https://docs.microsoft.com/en-us/azure/api-management/api-management-features
https://docs.microsoft.com/en-us/azure/api-management/api-management-howto-protect-backend-with-aad#enable-oauth-20-user-authorization-in-the-developer-console
HOTSPOT
You need to design an Azure policy that will implement the following functionality:
• For new resources, assign tags and values that match the tags and values of the resource group to which the resources are deployed.
• For existing resources, identify whether the tags and values match the tags and values of the resource group that contains the resources.
• For any non-compliant resources, trigger auto-generated remediation tasks to create missing tags and values.
The solution must use the principle of least privilege.
What should you include in the design? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
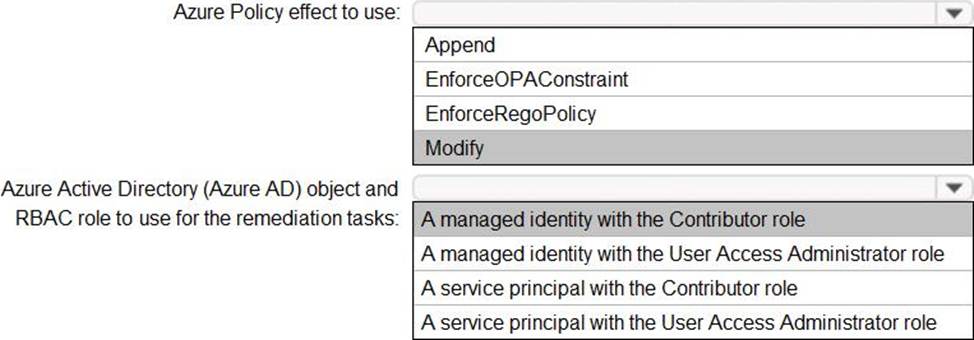
Box 1: Modify
Modify is used to add, update, or remove properties or tags on a resource during creation or update. A common example is updating tags on resources such as costCenter. Existing non-compliant resources can be remediated with a remediation task. A single Modify rule can have any number of operations.
Box 2: A managed identity with the Contributor role Managed identity
How remediation security works: When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity. Azure Policy creates a managed identity for each assignment, but must have details about what roles to grant the managed identity.
Contributor role
The Contributor role grants the required access to apply tags to any entity.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
https://docs.microsoft.com/en-us/azure/governance/policy/how-to/remediate-resources
https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/tag-resources
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects#modify
You migrate App1 to Azure. You need to ensure that the data storage for App1 meets the security and compliance requirement
What should you do?
- A . Create an access policy for the blob
- B . Modify the access level of the blob service.
- C . Implement Azure resource locks.
- D . Create Azure RBAC assignments.
A
Explanation:
Scenario: Once App1 is migrated to Azure, you must ensure that new data can be written to the app, and the modification of new and existing data is prevented for a period of three years.
As an administrator, you can lock a subscription, resource group, or resource to prevent other users in your organization from accidentally deleting or modifying critical resources. The lock overrides any permissions the user might have.
Reference: https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/lock-resources
You have an Azure subscription.
You need to recommend an Azure Kubernetes service (AKS) solution that will use Linux nodes.
The solution must meet the following requirements:
• Minimize the time it takes to provision compute resources during scale-out operations.
• Support autoscaling of Linux containers.
• Minimize administrative effort.
Which scaling option should you recommend?
- A . Virtual Kubetet
- B . cluster autoscaler
- C . virtual nodes
- D . horizontal pod autoscaler
C
Explanation:
https://docs.microsoft.com/en-us/azure/aks/virtual-nodes
