Practice Free AZ-305 Exam Online Questions
You have an Azure AD tenant.
You plan to deploy Azure Cosmos DB databases that will use the SQL API.
You need to recommend a solution to provide specific Azure AD user accounts with read access to the Cosmos DB databases.
What should you include in the recommendation?
- A . a resource token and an Access control (1AM) role assignment
- B . certificates and Azure Key Vault
- C . master keys and Azure Information Protection policies
- D . shared access signatures (SAS) and Conditional Access policies
You have an app named App1 that uses two on-premises Microsoft SQL Server databases named DB1 and DB2.
You plan to migrate DB1 and DB2 to Azure.
You need to recommend an Azure solution to host DB1 and DB2.
The solution must meet the following requirements:
• Support server-side transactions across DB1 and DB2.
• Minimize administrative effort to update the solution.
What should you recommend?
- A . two SQL Server databases on an Azure virtual machine
- B . two Azure SQL databases on different Azure SQL Database servers
- C . two Azure SQL databases in an elastic pool
- D . two Azure SQL databases on the same Azure SQL Database managed instance
D
Explanation:
When both the database management system and client are under the same ownership (e.g. when SQL Server is deployed to a virtual machine), transactions are available and the lock duration can be controlled.
Reference: https://docs.particular.net/nservicebus/azure/understanding-transactionality-in-azure
HOTSPOT
You have an Azure Load Balancer named LB1 that balances requests to five Azure virtual machines.
You need to develop a monitoring solution for LB1.
The solution must generate an alert when any of the following conditions are met:
✑ A virtual machine is unavailable.
✑ Connection attempts exceed 50,000 per minute.
Which signal should you include in the solution for each condition? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
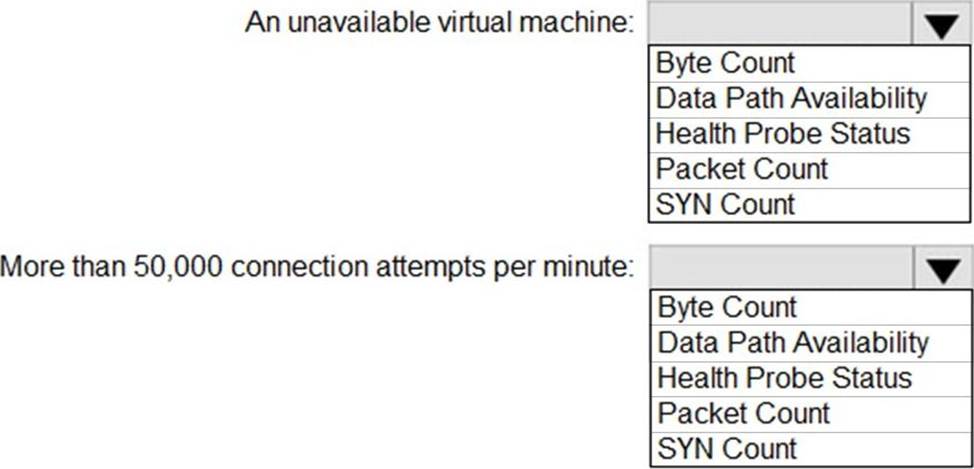
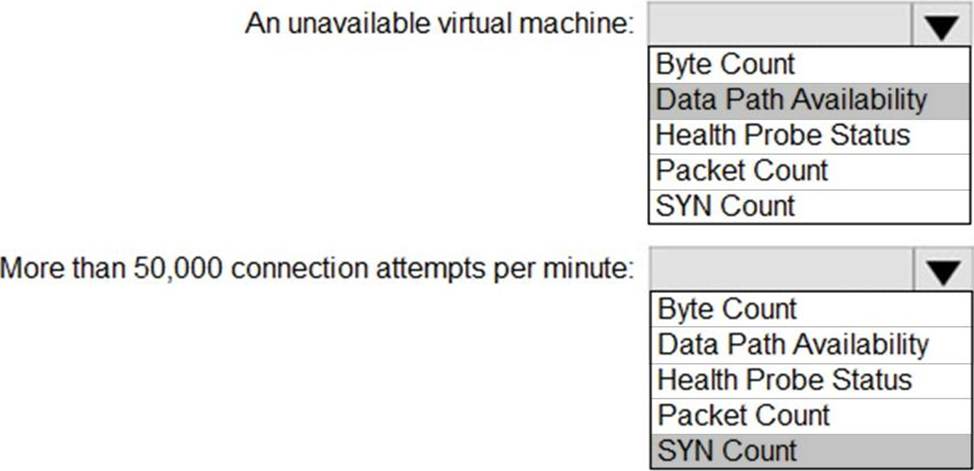
Explanation:
Box 1: Data path availability
Standard Load Balancer continuously exercises the data path from within a region to the load balancer front end, all the way to the SDN stack that supports your VM. As long as healthy instances remain, the measurement follows the same path as your application’s load-balanced traffic. The data path that your customers use is also validated. The measurement is invisible to your application and does not interfere with other operations.
Note: Load balancer distributes inbound flows that arrive at the load balancer’s front end to backend pool instances. These flows are according to configured load-balancing rules and health probes. The backend pool instances can be Azure Virtual Machines or instances in a virtual machine scale set.
Box 2: SYN count
SYN (synchronize) count: Standard Load Balancer does not terminate Transmission Control Protocol (TCP) connections or interact with TCP or UDP packet flows. Flows and their handshakes are always between the source and the VM instance. To better troubleshoot your TCP protocol scenarios, you can make use of SYN packets counters to understand how many TCP connection attempts are made. The metric reports the number of TCP SYN packets that were received.
Reference: https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-standard-diagnostics
You ate designing a SQL database solution. The solution will include 20 databases that will be 20 GB each and have varying usage patterns. You need to recommend a database platform to host the databases.
The solution must meet the following requirements:
• The compute resources allocated to the databases must scale dynamically.
• The solution must meet an SLA of 99.99% uptime.
• The solution must have reserved capacity.
• Compute charges must be minimized.
What should you include in the recommendation?
- A . 20 databases on a Microsoft SQL server that runs on an Azure virtual machine
- B . 20 instances of Azure SQL Database serverless
- C . 20 databases on a Microsoft SQL server that runs on an Azure virtual machine in an availability set
- D . an elastic pool that contains 20 Azure SQL databases
D
Explanation:
Azure SQL Database elastic pools are a simple, cost-effective solution for managing and scaling multiple databases that have varying and unpredictable usage demands. The databases in an elastic pool are on a single server and share a set number of resources at a set price. Elastic pools in Azure SQL Database enable SaaS developers to optimize the price performance for a group of databases within a prescribed budget while delivering performance elasticity for each database.
Guaranteed 99.995 percent uptime for SQL Database
Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/database/elastic-pool-overview
https://azure.microsoft.com/en-us/pricing/details/sql-database/elastic/
https://www.azure.cn/en-us/support/sla/virtual-machines/
https://techcommunity.microsoft.com/t5/azure-sql/optimize-price-performance-with-compute-auto-scaling-in-azure/ba-p/966149
You have an Azure subscription. The subscription has a blob container that contains multiple blobs. Ten users in the finance department of your company plan to access the blobs during the month of April. You need to recommend a solution to enable access to the blobs during the month of April only.
Which security solution should you include in the recommendation?
- A . shared access signatures (SAS)
- B . access keys
- C . conditional access policies
- D . certificates
A
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/storage/common/storage-sas-overview
You have an Azure subscription that contains 100 virtual machines in the North Europe Azure region.
You replicate the virtual machines to the West Europe region by using Azure Site Recovery.
You plan to perform disaster recovery testing once a month. The testing will be performed during an eight-hour period, during which the virtual machines will be accessed, and their functionality validated. The virtual machines will be shut down when testing is not being performed.
You need to estimate the costs of the Site Recovery solution per month.
Which costs should the estimate include?
- A . the virtual machine compute costs for only eight hours, the virtual machine storage costs for the entire month, and the Site Recovery license costs per protected virtual machine for the entire month
- B . the virtual machine compute costs for the entire month, the virtual machine storage costs for all the hours each month, and the Site Recovery license costs per protected virtual machine for the entire month
- C . the virtual machine compute costs for only eight hours, the virtual machine storage costs for only eight hours, and the Site Recovery license costs per protected virtual machine for only eight hours
- D . the virtual machine compute costs for only eight hours, the virtual machine storage costs for only eight hours, and the Site Recovery license costs per protected virtual machine for the entire month
HOTSPOT
You are designing a software as a service (SaaS) application that will enable Microsoft Entra users to create and publish online surveys. The SaaS application will have a front-end web app and a back-end web API. The web app will rely on the web API to handle updates to customer surveys.
You need to design an authorization flow for the SaaS application.
The solution must meet the following requirements:
• To access the back-end web API, the web app must authenticate by using OAuth 2 bearer tokens.
• The web app must authenticate by using the identities of individual users.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct collection is worth one point.
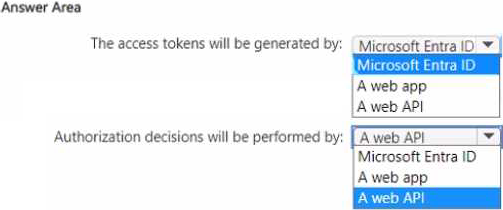
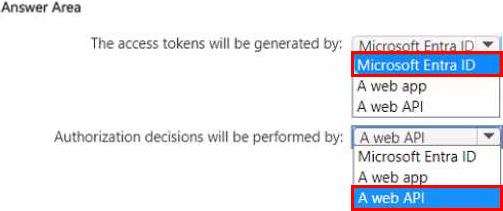
HOTSPOT
You have several Azure App Service web apps that use Azure Key Vault to store data encryption keys.
Several departments have the following requests to support the web app:
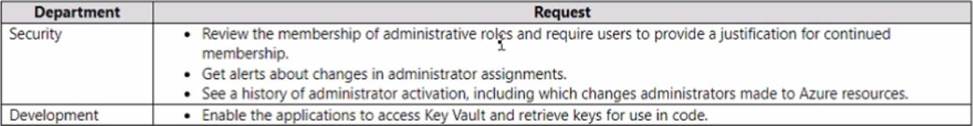
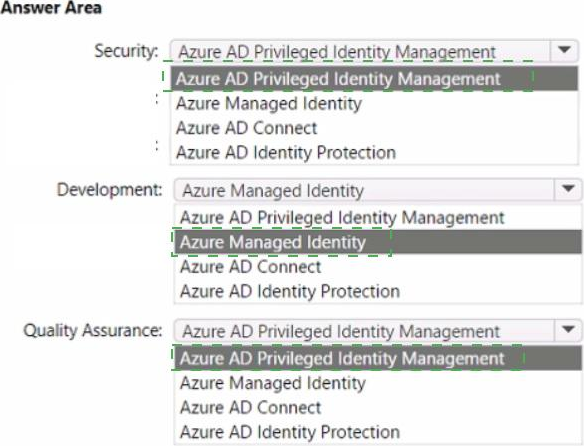
Which service should you recommend for each department’s request? To answer, configure the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Topic 1, Litware, Inc
Case Study
Overview
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview. General Overview
Litware, Inc. is a medium-sized finance company.
Overview. Physical Locations
Litware has a main office in Boston.
Existing Environment. Identity Environment
The network contains an Active Directory forest named Litware.com that is linked to an Azure Active Directory (Azure AD) tenant named Litware.com. All users have Azure Active Directory Premium P2 licenses.
Litware has a second Azure AD tenant named dev.Litware.com that is used as a development environment.
The Litware.com tenant has a conditional acess policy named capolicy1. Capolicy1 requires that when users manage the Azure subscription for a production environment by
using the Azure portal, they must connect from a hybrid Azure AD-joined device.
Existing Environment. Azure Environment
Litware has 10 Azure subscriptions that are linked to the Litware.com tenant and five Azure subscriptions that are linked to the dev.Litware.com tenant. All the subscriptions are in an Enterprise Agreement (EA).
The Litware.com tenant contains a custom Azure role-based access control (Azure RBAC) role named Role1 that grants the DataActions read permission to the blobs and files in Azure Storage.
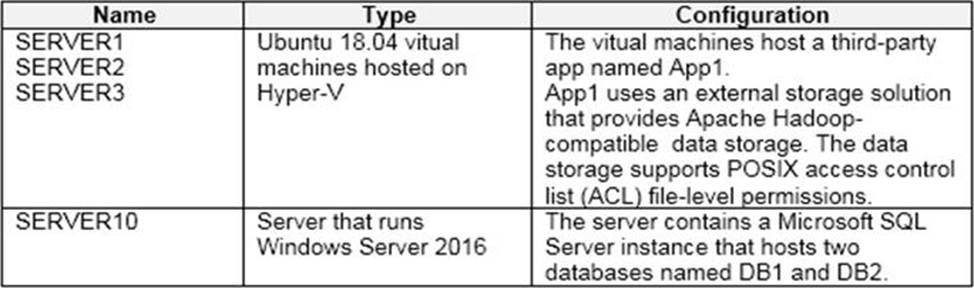
Existing Environment. On-premises Environment
The on-premises network of Litware contains the resources shown in the following table.
Existing Environment. Network Environment
Litware has ExpressRoute connectivity to Azure.
Planned Changes and Requirements. Planned Changes
Litware plans to implement the following changes:
✑ Migrate DB1 and DB2 to Azure.
✑ Migrate App1 to Azure virtual machines.
✑ Deploy the Azure virtual machines that will host App1 to Azure dedicated hosts.
Planned Changes and Requirements. Authentication and Authorization Requirements
Litware identifies the following authentication and authorization requirements:
✑ Users that manage the production environment by using the Azure portal must connect from a hybrid Azure AD-joined device and authenticate by using Azure Multi-Factor Authentication (MFA).
✑ The Network Contributor built-in RBAC role must be used to grant permission to all the virtual networks in all the Azure subscriptions.
✑ To access the resources in Azure, App1 must use the managed identity of the virtual machines that will host the app.
✑ Role1 must be used to assign permissions to the storage accounts of all the Azure subscriptions.
✑ RBAC roles must be applied at the highest level possible.
Planned Changes and Requirements. Resiliency Requirements
Litware identifies the following resiliency requirements:
✑ Once migrated to Azure, DB1 and DB2 must meet the following requirements:
– Maintain availability if two availability zones in the local Azure region fail.
– Fail over automatically.
– Minimize I/O latency.
✑ App1 must meet the following requirements:
– Be hosted in an Azure region that supports availability zones.
– Be hosted on Azure virtual machines that support automatic scaling.
– Maintain availability if two availability zones in the local Azure region fail.
Planned Changes and Requirements. Security and Compliance Requirements
Litware identifies the following security and compliance requirements:
✑ Once App1 is migrated to Azure, you must ensure that new data can be written to the app, and the modification of new and existing data is prevented for a period of three years.
✑ On-premises users and services must be able to access the Azure Storage account that will host the data in App1.
✑ Access to the public endpoint of the Azure Storage account that will host the App1 data must be prevented.
✑ All Azure SQL databases in the production environment must have Transparent Data Encryption (TDE) enabled.
✑ App1 must not share physical hardware with other workloads.
Planned Changes and Requirements. Business Requirements
Litware identifies the following business requirements:
✑ Minimize administrative effort.
✑ Minimize costs.
HOTSPOT
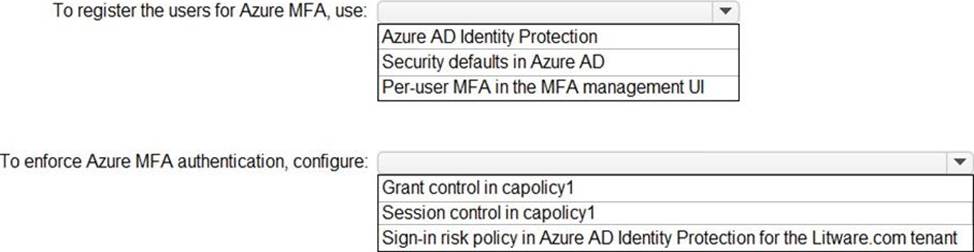
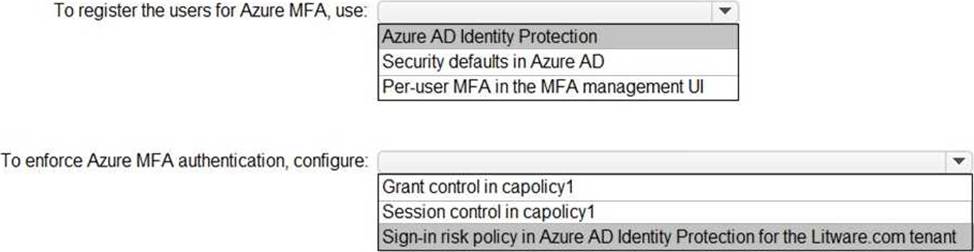
You need to ensure that users managing the production environment are registered for Azure MFA and must authenticate by using Azure MFA when they sign in to the Azure portal. The solution must meet the authentication and authorization requirements.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Azure AD Identity Protection
Azure AD Identity Protection helps you manage the roll-out of Azure AD Multi-Factor Authentication (MFA) registration by configuring a Conditional Access policy to require MFA registration no matter what modern authentication app you are signing in to.
Scenario: Users that manage the production environment by using the Azure portal must connect from a hybrid Azure AD-joined device and authenticate by using Azure Multi-Factor Authentication (MFA).
Box 2: Sign-in risk policy…
Scenario: The Litware.com tenant has a conditional access policy named capolicy1. Capolicy1 requires that when users manage the Azure subscription for a production environment by using the Azure portal, they must connect from a hybrid Azure AD-joined device.
Identity Protection policies we have two risk policies that we can enable in our directory.
Sign-in risk policy
User risk policy
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-mfa-policy
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-risk-policies
Topic 2, Fabrikam, inc Case Study A
Overview:
Existing Environment
Fabrikam, Inc. is an engineering company that has offices throughout Europe. The company has a main office in London and three branch offices in Amsterdam Berlin, and Rome.
Active Directory Environment:
The network contains two Active Directory forests named corp.fabnkam.com and rd.fabrikam.com. There are no trust relationships between the forests. Corp.fabrikam.com is a production forest that contains identities used for internal user and computer authentication. Rd.fabrikam.com is used by the research and development (R&D) department only. The R&D department is restricted to using on-premises resources only.
Network Infrastructure:
Each office contains at least one domain controller from the corp.fabrikam.com domain.
The main office contains all the domain controllers for the rd.fabrikam.com forest.
All the offices have a high-speed connection to the Internet.
An existing application named WebApp1 is hosted in the data center of the London office. WebApp1 is used by customers to place and track orders. WebApp1 has a web tier that uses Microsoft Internet Information Services (IIS) and a database tier that runs Microsoft SQL Server 2016. The web tier and the database tier are deployed to virtual machines that run on Hyper-V.
The IT department currently uses a separate Hyper-V environment to test updates to WebApp1.
Fabrikam purchases all Microsoft licenses through a Microsoft Enterprise Agreement that includes Software Assurance.
Problem Statement:
The use of Web App1 is unpredictable. At peak times, users often report delays. At other times, many resources for WebApp1 are underutilized.
Requirements:
Planned Changes:
Fabrikam plans to move most of its production workloads to Azure during the next few years.
As one of its first projects, the company plans to establish a hybrid identity model, facilitating an upcoming Microsoft Office 365 deployment All R&D operations will remain on-premises.
Fabrikam plans to migrate the production and test instances of WebApp1 to Azure.
Technical Requirements:
Fabrikam identifies the following technical requirements:
• Web site content must be easily updated from a single point.
• User input must be minimized when provisioning new app instances.
• Whenever possible, existing on premises licenses must be used to reduce cost.
• Users must always authenticate by using their corp.fabrikam.com UPN identity.
• Any new deployments to Azure must be redundant in case an Azure region fails.
• Whenever possible, solutions must be deployed to Azure by using platform as a service (PaaS).
• An email distribution group named IT Support must be notified of any issues relating to the directory synchronization services.
• Directory synchronization between Azure Active Directory (Azure AD) and corp.fabhkam.com must not be affected by a link failure between Azure and the on premises network.
Database Requirements:
Fabrikam identifies the following database requirements:
• Database metrics for the production instance of WebApp1 must be available for analysis so that database administrators can optimize the performance settings.
• To avoid disrupting customer access, database downtime must be minimized when databases are migrated.
• Database backups must be retained for a minimum of seven years to meet compliance requirement
Security Requirements:
Fabrikam identifies the following security requirements:
* Company information including policies, templates, and data must be inaccessible to anyone outside the company
* Users on the on-premises network must be able to authenticate to corp.fabrikam.com if an Internet link fails.
* Administrators must be able authenticate to the Azure portal by using their corp.fabrikam.com credentials.
* All administrative access to the Azure portal must be secured by using multi-factor authentication.
* The testing of WebApp1 updates must not be visible to anyone outside the company.
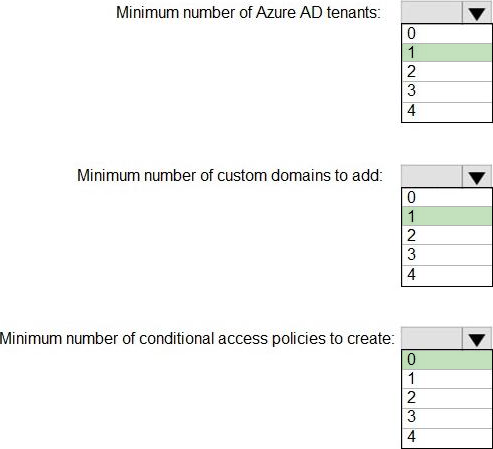
HOTSPOT
To meet the authentication requirements of Fabrikam, what should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
1
1
0
