Practice Free AZ-104 Exam Online Questions
DRAG DROP
You have an Azure subscription that contains a storage account.
You have an on-premises server named Server1 that runs Window Server 2016. Server1 has 2 TB of data.
You need to transfer the data to the storage account by using the Azure Import/Export service.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order. NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.
Explanation:
At a high level, an import job involves the following steps:
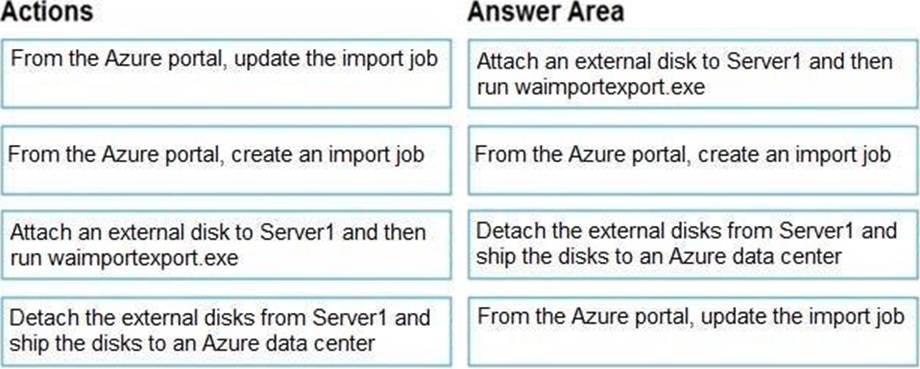
Step 1: Attach an external disk to Server1 and then run waimportexport.exe
Determine data to be imported, number of drives you need, destination blob location for your data in Azure storage.
Use the WAImportExport tool to copy data to disk drives. Encrypt the disk drives with BitLocker.
Step 2: From the Azure portal, create an import job.
Create an import job in your target storage account in Azure portal. Upload the drive journal files.
Step 3: Detach the external disks from Server1 and ship the disks to an Azure data center.
Provide the return address and carrier account number for shipping the drives back to you.
Ship the disk drives to the shipping address provided during job creation.
Step 4: From the Azure portal, update the import job
Update the delivery tracking number in the import job details and submit the import job.
The drives are received and processed at the Azure data center.
The drives are shipped using your carrier account to the return address provided in the import job.
Reference: https://docs.microsoft.com/en-us/azure/storage/common/storage-import-export-service
HOTSPOT
You have an Azure subscription.
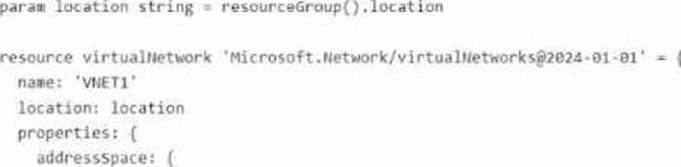
You plan to deploy the following file named File1.bicep.
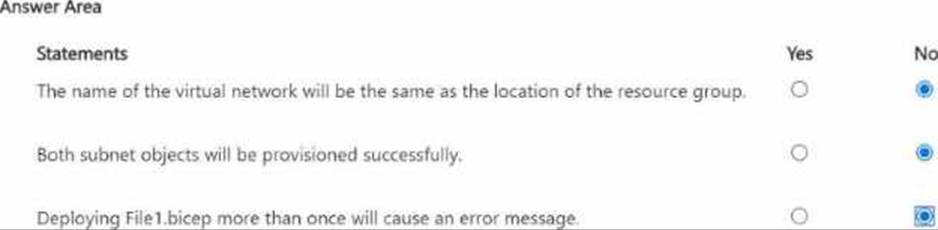
HOTSPOT
You have an Azure subscription that contains a user named User1 and a storage account named storage 1.
The storage1 account contains the resources shown in the following table.
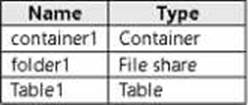
User1 is assigned the following roles for storage 1:
• Storage Blob Data Reader
• Storage Table Data Contributor
• Storage File Data SMB Share Contributor
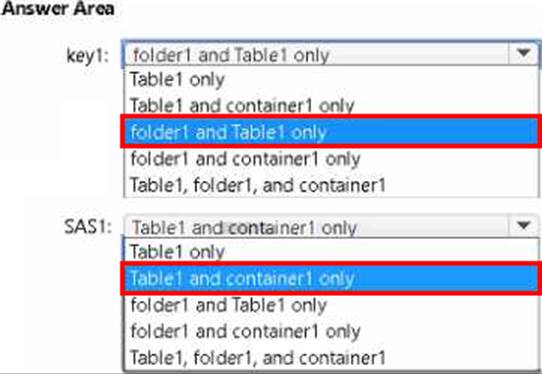
For storage1, you create a shared access signature (SAS) named SAS1 that has the settings shown in the following exhibit. (Click the Exhibit tab.)
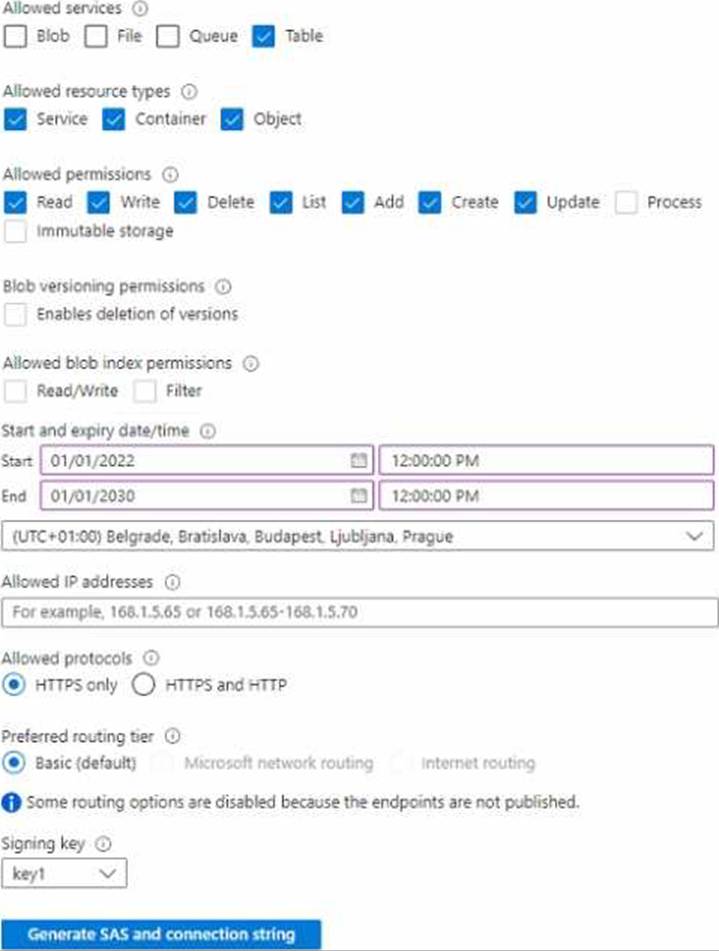
To which resources can User1 write by using SAS1 and key1? To answer, select the appropriate options in the answer area.
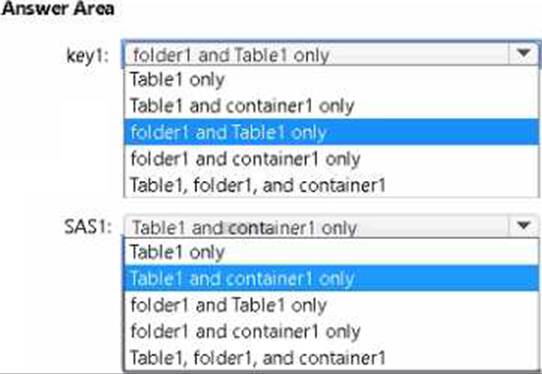
HOTSPOT
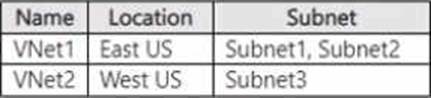
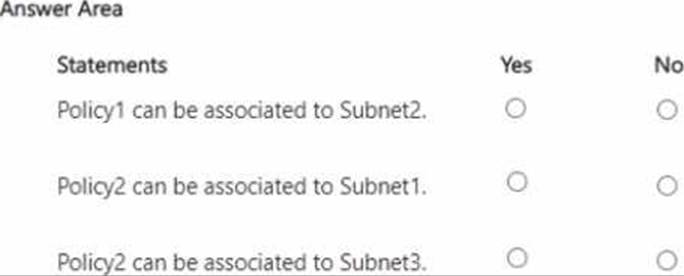
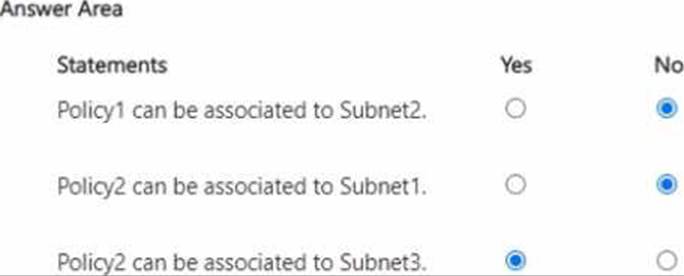
You have an Azure subscription that contains the virtual networks shown in the following table.
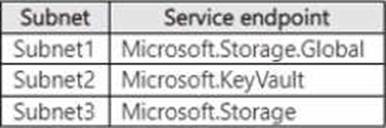
You add a service endpoint to each subnet as shown in the following table.
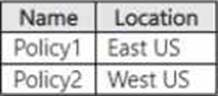
You create the service endpoint policies shown in the following table.
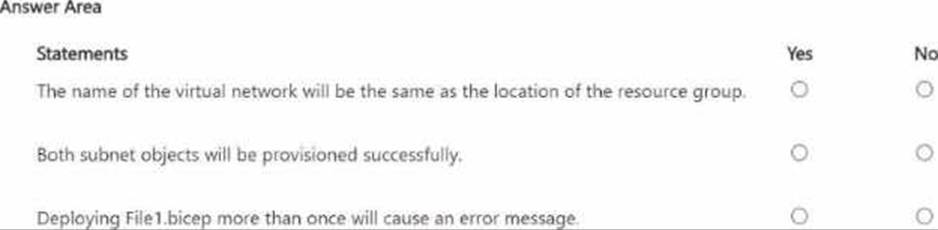
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You plan to move a distributed on-premises app named App1 to an Azure subscription.
After the planned move, App1 will be hosted on several Azure virtual machines.
You need to ensure that App1 always runs on at least eight virtual machines during planned Azure maintenance.
What should you create?
- A . one virtual machine scale set that has 10 virtual machines instances
- B . one Availability Set that has three fault domains and one update domain
- C . one Availability Set that has 10 update domains and one fault domain
- D . one virtual machine scale set that has 12 virtual machines instances
A
Explanation:
A virtual machine scale set is a group of identical virtual machines that are centrally managed, configured, and updated1. A virtual machine scale set can automatically increase or decrease the number of virtual machine instances in response to demand or a defined schedule2. A virtual machine scale set also provides high availability and fault tolerance by distributing the virtual machine instances across multiple fault domains and update domains3.
A fault domain is a logical group of underlying hardware that share a common power source and network switch. A fault domain can fail due to hardware or software failures, power outages, or network interruptions4. A virtual machine scale set can have up to five fault domains in a region. An update domain is a logical group of underlying hardware that can undergo maintenance or be rebooted at the same time. An update domain can be affected by planned events, such as OS updates, application updates, or configuration changes4. A virtual machine scale set can have up to 20 update domains in a region.
By creating a virtual machine scale set that has 10 virtual machine instances, you can ensure that App1 always runs on at least eight virtual machines during planned Azure maintenance. This is because the default configuration of a virtual machine scale set is to have five fault domains and five update domains. This means that at any given time, only one fault domain or one update domain can be unavailable due to maintenance or failure. Therefore, at least eight out of 10 virtual machine instances will be available to run App1.
An availability set is another option for providing high availability and fault tolerance for your virtual machines. An availability set is a logical grouping of two or more virtual machines that are deployed across multiple fault domains and update domains. However, an availability set does not provide automatic scaling of resources or load balancing of traffic. You need to manually create and manage the number of virtual machine instances in an availability set.
Therefore, a virtual machine scale set is a better option than an availability set for your scenario. To create a virtual machine scale set, you can follow these steps: Sign in to the Azure portal.
Select Create a resource > Compute > Virtual machine scale set.
On the Basics tab, enter a name for your scale set, select your subscription and resource group, select Windows Server 2019 as the image type, and enter a username and password for the administrator account.
On the Instance details tab, select the region where you want to deploy your scale set, select the size of the virtual machine instances, and enter 10 as the initial instance count.
On the Scaling tab, configure the scaling policy for your scale set based on metrics or schedule. On the Load balancing tab, configure the load balancer for your scale set to distribute traffic across the instances.
On the Management tab, configure the diagnostics settings, automatic OS upgrades, extensions, and backup options for your scale set.
On the Advanced tab, configure the availability zone, proximity placement group, accelerated networking, host group, and custom script extension options for your scale set. On the Tags tab, optionally add tags to your scale set resources.
On the Review + create tab, review your settings and select Create.
You have an Azure subscription that contains an Azure Storage account.
You plan to create an Azure container instance named container1 that will use a Docker image namedImage1. Image1 contains a Microsoft SQL Server instance that requires persistent storage.
You need to configure a storage service for Container1.
What should you use?
- A . Azure Files
- B . Azure Blob storage
- C . Azure Queue storage
- D . Azure Table storage
A
Explanation:
https://azure.microsoft.com/en-us/blog/persistent-docker-volumes-with-azure-file-storage/
HOTSPOT
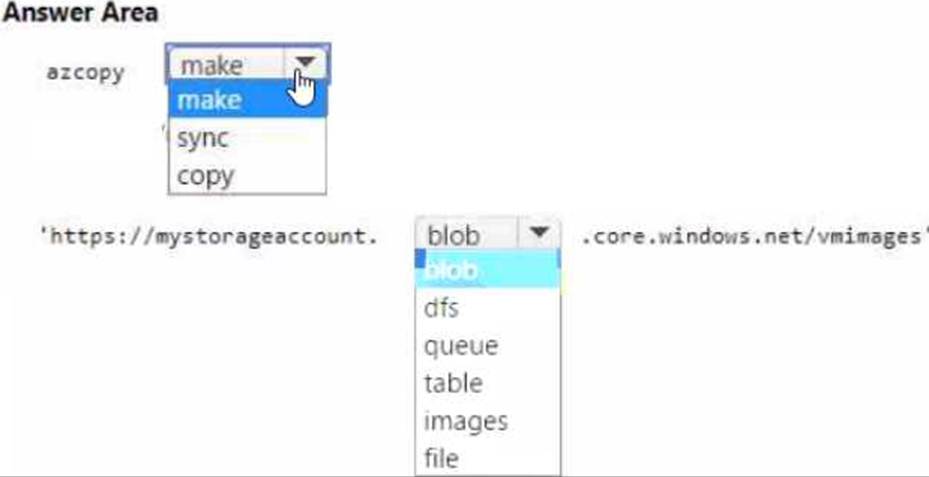
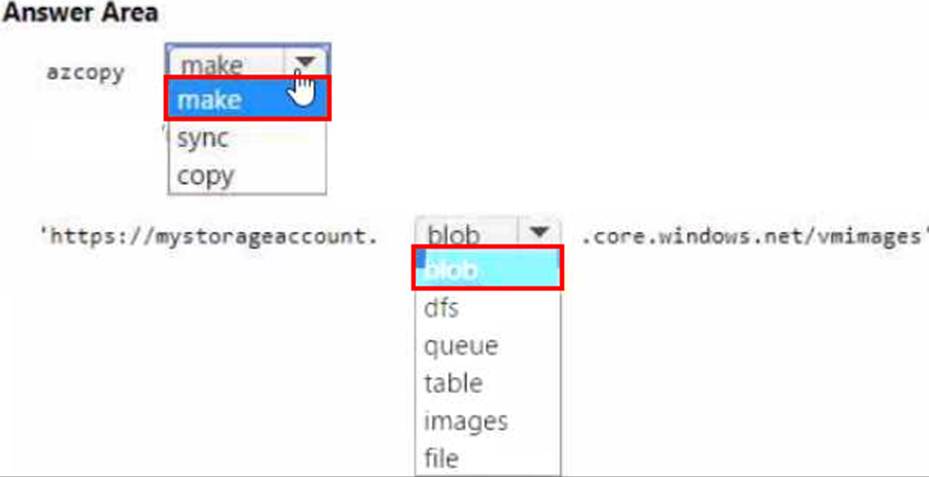
You have an Azure subscription that contains an Azure Storage account.
You plan to copy an on-premises virtual machine image to a container named vmimages.
You need to create the container for the planned image.
Which command should you run? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
HOTSPOT
You have an Azure subscription.
You create the following file named Deploy.json.
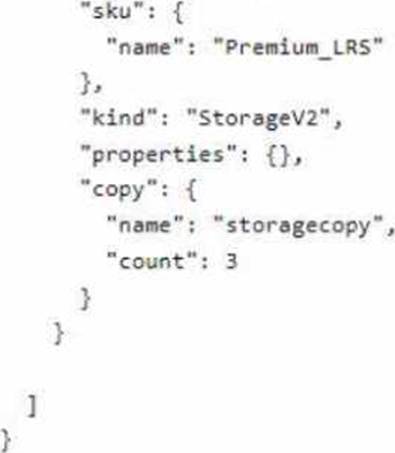
You connect to the subscription and run the following commands.
![]()
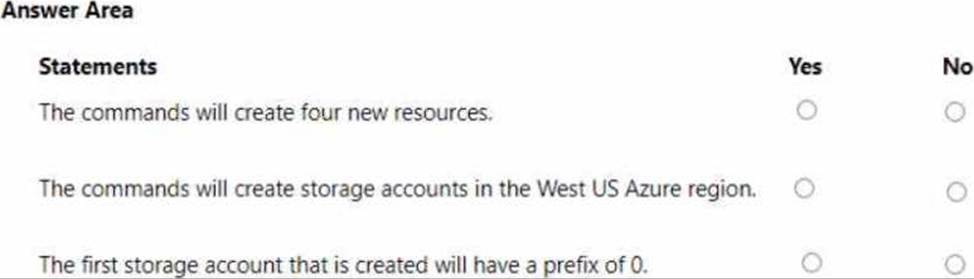
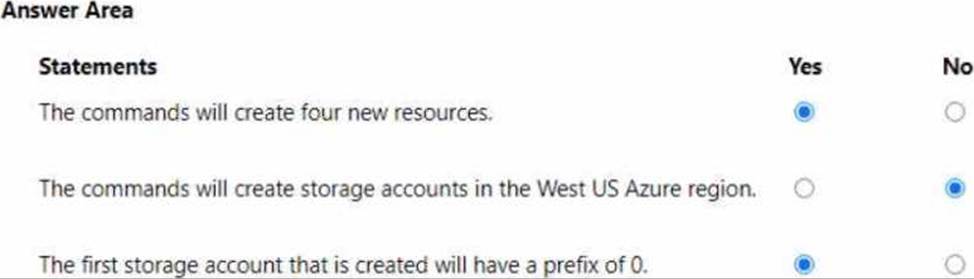
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
You have an Azure subscription.
You create the following file named Deploy.json.

You connect to the subscription and run the following commands.
![]()
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.


HOTSPOT
You have an Azure subscription.
You create the following file named Deploy.json.

You connect to the subscription and run the following commands.
![]()
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.


