Practice Free AZ-104 Exam Online Questions
You create an App Service plan named plan1 and an Azure web app named webapp1. You discover that the option to create a staging slot is unavailable. You need to create a staging slot for plan1.
What should you do first?
- A . From webapp1, modify the Application settings.
- B . From webapp1, add a custom domain.
- C . From plan1, scale up the App Service plan.
- D . From plan1, scale out the App Service plan.
C
Explanation:
The app must be running in the Standard, Premium, or Isolated tier in order for you to enable multiple deployment slots. If the app isn’t already in the Standard, Premium, or Isolated tier, you receive a message that indicates the supported tiers for enabling staged publishing. At this point, you have the option to select Upgrade and go to the Scale tab of your app before continuing.
Scale up: Get more CPU, memory, disk space, and extra features like dedicated virtual machines (VMs), custom domains and certificates, staging slots, autoscaling, and more.
Scale out: Increase the number of VM instances that run your app. You can scale out to as many as 30 instances
Reference:
https://docs.microsoft.com/en-us/azure/app-service/deploy-staging-slots
https://docs.microsoft.com/en-us/azure/app-service/manage-scale-up
HOTSPOT
You manage two Azure subscriptions named Subscription 1 and Subscription2.
Subscription! has following virtual networks:

The virtual networks contain the following subnets:
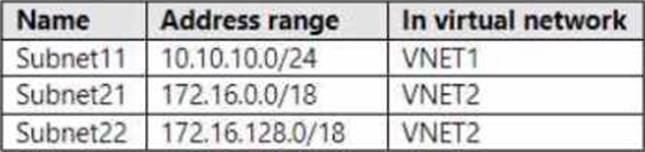
Subscnption2 contains the following virtual network:
– Name: VNETA
• Address space: 10.10.128.0/17
• Region: Canada Central
VNETA contains the following subnets:

For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have an Azure virtual machine named VM1 and an Azure key vault named Vault1. On VM1, you plan to configure Azure Disk Encryption to use a key encryption key (KEK) You need to prepare Vault! for Azure Disk Encryption.
Which two actions should you perform on Vault1? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Create a new key.
- B . Select Azure Virtual machines for deployment
- C . Configure a key rotation policy.
- D . Create a new secret.
- E . Select Azure Disk Encryption for volume encryption
A,C
Explanation:
To prepare Vault1 for Azure Disk Encryption, you need to perform the following actions on Vault1:
Create a new key. A key encryption key (KEK) is an encryption key that is used to encrypt the encryption secrets before they are stored in the key vault. You can create a new KEK by using the Azure CLI, the Azure PowerShell, or the Azure portal1. You can also import an existing KEK from another source, such as a hardware security module (HSM)2. The KEK must be a 2048-bit RSA key or a 256-bit AES key3.
Select Azure Disk Encryption for volume encryption. This is an advanced access policy setting that enables Azure Disk Encryption to access the keys and secrets in the key vault. You can select this setting by using the Azure CLI, the Azure PowerShell, or the Azure portal4. You must also enable access to Microsoft Trusted Services if you have enabled the firewall on the key vault.
HOTSPOT
You have an Azure subscription that contains the virtual networks shown in the following table.

You have the virtual machines shown in the following table.
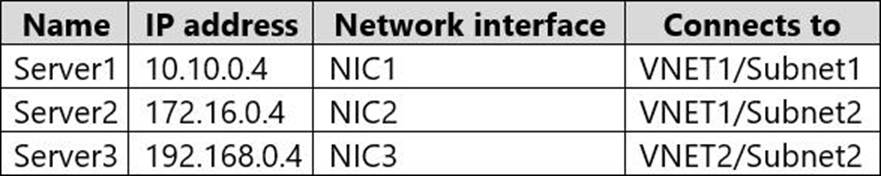
You have the virtual network interfaces shown in the following table.
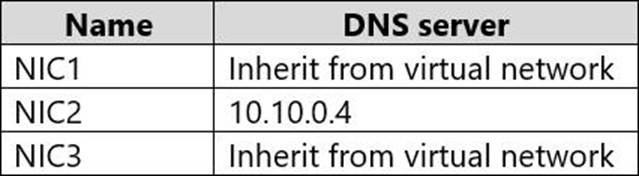
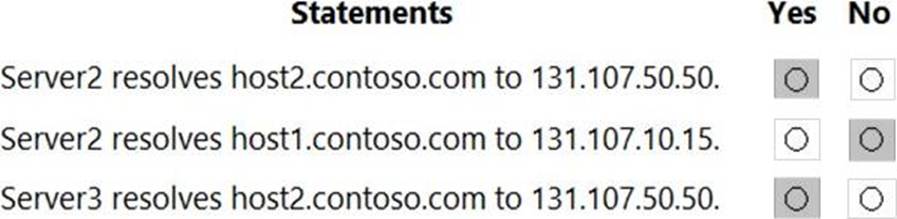
Server1 is a DNS server that contains the resources shown in the following table.
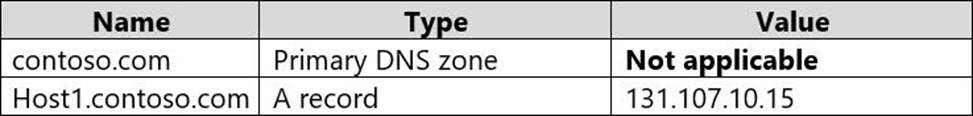
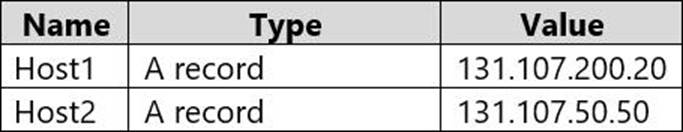
You have an Azure private DNS zone named contoso.com that has a virtual network link to VNET2 and the records shown in the following table.
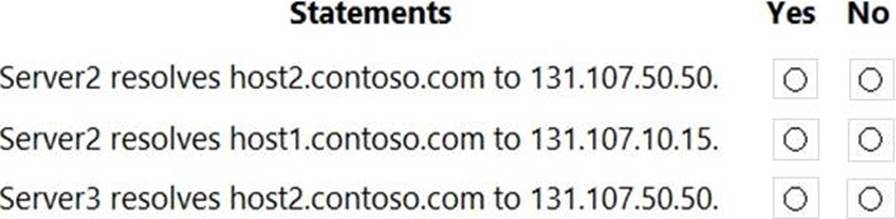
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have an Azure virtual machine named VM1.
Azure collects events from VM1.
You are creating an alert rule in Azure Monitor to notify an administrator when an error is logged in the System event log of VM1.
You need to specify which resource type to monitor.
What should you specify?
- A . metric alert
- B . Azure Log Analytics workspace
- C . virtual machine
- D . virtual machine extension
B
Explanation:
Azure Monitor can collect data directly from your Azure virtual machines into a Log Analytics workspace for analysis of details and correlations. Installing the Log Analytics VM extension for Windows and Linux allows Azure Monitor to collect data from your Azure VMs.
Azure Log Analytics workspace is also used for on-premises computers monitored by System Center Operations Manager.
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-collect-azurevm
HOTSPOT
You have an Azure subscription that contains the resources in the following table.
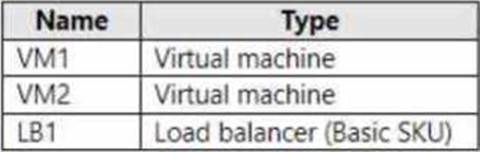
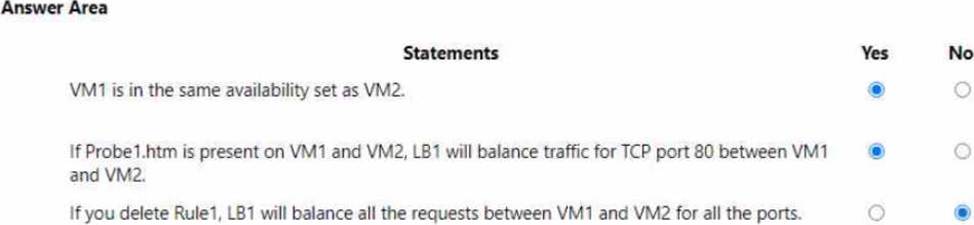
You install the Web Server (IIS) server role on VM1 and VM2. and then add VM1 and VM2 to LB1.
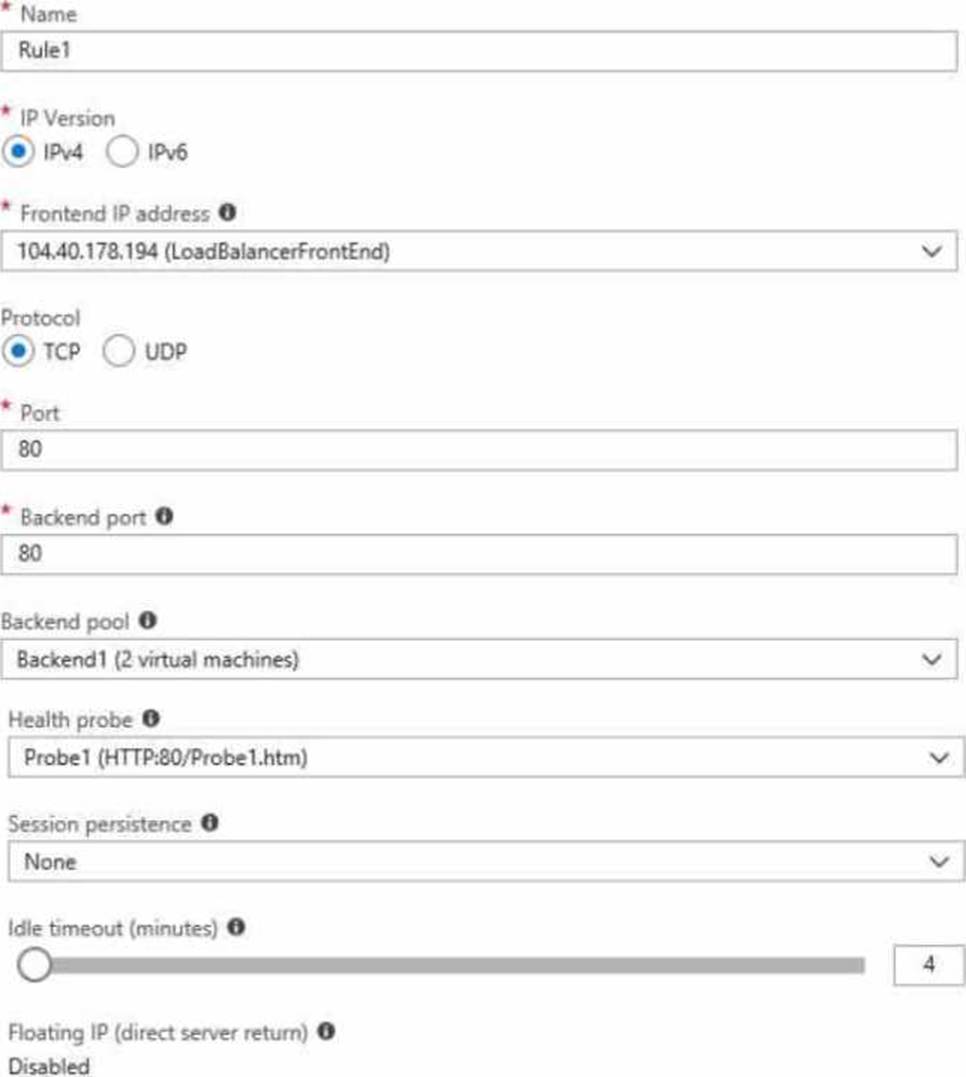
LB1 is configured as shown in the LB1 exhibit. (Click the LB1 tab.)

Rule1 is configured as shown in the Rule1 exhibit (Click the Rule1 tab.)
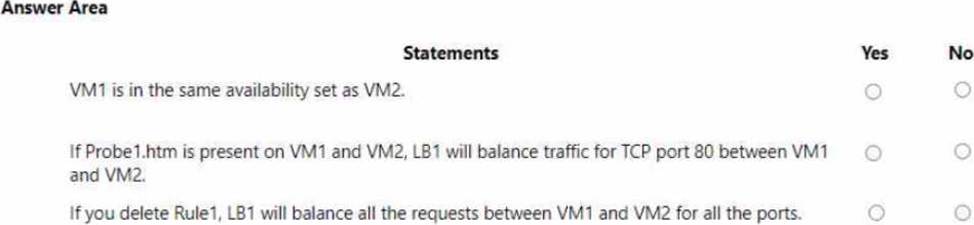
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You have 100 Azure virtual machines.
You need to quickly identify underutilized virtual machines that can have their service tier changed to a less expensive offering.
Which blade should you use?
- A . Metrics
- B . Customer insights
- C . Monitor
- D . Advisor
D
Explanation:
The Advisor dashboard displays personalized recommendations for all your subscriptions. You can apply filters to display recommendations for specific subscriptions and resource types.
The recommendations are divided into five categories:
Reliability (formerly called High Availability): To ensure and improve the continuity of your business-critical applications. For more information, see Advisor Reliability recommendations.
Security: To detect threats and vulnerabilities that might lead to security breaches. For more information, see Advisor Security recommendations.
Performance: To improve the speed of your applications. For more information, see Advisor Performance recommendations.
Cost: To optimize and reduce your overall Azure spending. For more information, see Advisor Cost recommendations.
Operational Excellence: To help you achieve process and workflow efficiency, resource manageability and deployment best practices. . For more information, see Advisor Operational Excellence recommendations.
You have an Azure DNS zone named adatum.com. You need to delegate a subdomain named research.adatum.com to a different DNS server in Azure.
What should you do?
- A . Create an PTR record named research in the adatum.com zone.
- B . Create an NS record named research in the adatum.com zone.
- C . Modify the SOA record of adatum.com.
- D . Create an A record named *. research in the adatum.com zone
B
Explanation:
https://docs.microsoft.com/en-us/azure/dns/delegate-subdomain
HOTSPOT
You plan to deploy five virtual machines to a virtual network subnet.
Each virtual machine will have a public IP address and a private IP address.
Each virtual machine requires the same inbound and outbound security rules.
What is the minimum number of network interfaces and network security groups that you require? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.


Explanation:
Box 1: 5
A public and a private IP address can be assigned to a single network interface.
Box 2: 1
You can associate zero, or one, network security group to each virtual network subnet and network interface in a virtual machine. The same network security group can be associated to as many subnets and network interfaces as you choose.
Reference: https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-network-interface-addresses
HOTSPOT
You plan to deploy five virtual machines to a virtual network subnet.
Each virtual machine will have a public IP address and a private IP address.
Each virtual machine requires the same inbound and outbound security rules.
What is the minimum number of network interfaces and network security groups that you require? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.


Explanation:
Box 1: 5
A public and a private IP address can be assigned to a single network interface.
Box 2: 1
You can associate zero, or one, network security group to each virtual network subnet and network interface in a virtual machine. The same network security group can be associated to as many subnets and network interfaces as you choose.
Reference: https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-network-interface-addresses
