Practice Free 400-007 Exam Online Questions
Refer to the exhibit.
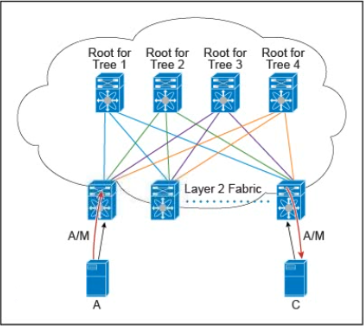
There are multiple trees in the Cisco FabricPath All switches in the Layer 2 fabric share the same view of each tree.
Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two)
- A . A specific (S.G) traffic is not load-balanced
- B . All trees are utilized at the same level of the traffic rate
- C . Every leaf node assigns the specific (S.G) to the same tree.
- D . A specific (S.G) multicast traffic is load-balanced across all trees due to better link utilization efficiency.
- E . The multicast traffic is generally load-balanced across all trees
Most security monitoring systems use a signature-based approach to detect threats.
In which two instances are systems based on Network Behavior Anomaly Detection better than signature-based systems when it comes to detecting security threat vectors’? (Choose two.)
- A . malware detection
- B . encrypted threat traffic
- C . spyware detection
- D . intrusion threat detection
- E . new zero-day attacks
When designing a WAN that will be carrying real-time traffic, what are two important reasons to consider serialization delay? (Choose two)
- A . Serialization delays are invariable because they depend only on the line rate of the interface
- B . Serialization delays are variable because they depend on the line rate of the interface and on the type of the packet being serialized.
- C . Serialization delay is the time required to transmit the packet on the physical media.
- D . Serialization delays are variable because they depend only on the size of the packet being serialized
- E . Serialization delay depends not only on the line rate of the interface but also on the size of the packet
A network uses an SDN architecture with switches and a centralized controller.
What should be on the switches but not on the controller?
- A . control plane functions
- B . a southbound interface
- C . data plane functions
- D . a northbound interface
Refer to the exhibit.
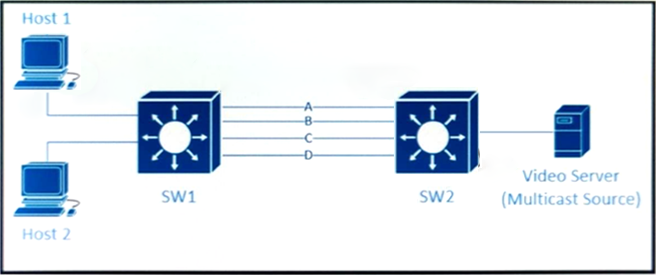
Traffic was equally balanced between Layer 3 links on core switches SW1 and SW2 before an introduction of the new video server in the network. This video server uses multicast to send video streams to hosts and now one of the links between core switches is over utilized.
Which design solution solves this issue?
- A . Add more links between core switches.
- B . Aggregate links Layer 2 link aggregation.
- C . Apply a more granular load- balancing method on SW1.
- D . Apply a more granular load-balancing method on SW2.
- E . Filter IGMP joins on an over -utilized link.
You are designing an Out of Band Cisco Network Admission Control. Layer 3 Real-IP Gateway deployment for a customer.
Which VLAN must be trunked back to the Clean Access Server from the access switch?
- A . authentication VLAN
- B . user VLAN
- C . untrusted VLAN
- D . management VLAN
Company XYZ wants to implement an IPS device to detect and block well-known attacks against their network They want a design solution where all packets that are forwarded to the network are checked against a signature database before being allowed through This check must be done with the minimum effect on performance.
Which design is recommended?
- A . Deploy an IPS behind the firewall in promiscuous mode
- B . Deploy an IPS in front of the firewall in promiscuous mode
- C . Deploy an IPS behind the firewall in in-line mode
- D . Deploy and IPS in front of the firewall in in-line mode
A green data center is being deployed and a design requirement is to be able to readily scale server virtualization.
Which IETF standard technology can provide this requirement?
- A . data center bridging
- B . unified fabric
- C . Transparent Interconnection of Lots of Links
- D . fabric path
Company XYZ wants design recommendations for Layer 2 redundancy (using Layer 2 technologies) The company wants to prioritize flexibility and scalability elements in the new design.
Which two technologies help meet these requirements? (Choose two)
- A . Avoid stretching VLANs across switches
- B . Use switch clustering at the distnbution layer where possible
- C . Configure DHCP snooping on the switches
- D . Use Unidirectional Link Detection
- E . Use root guard
Refer to the diagram.
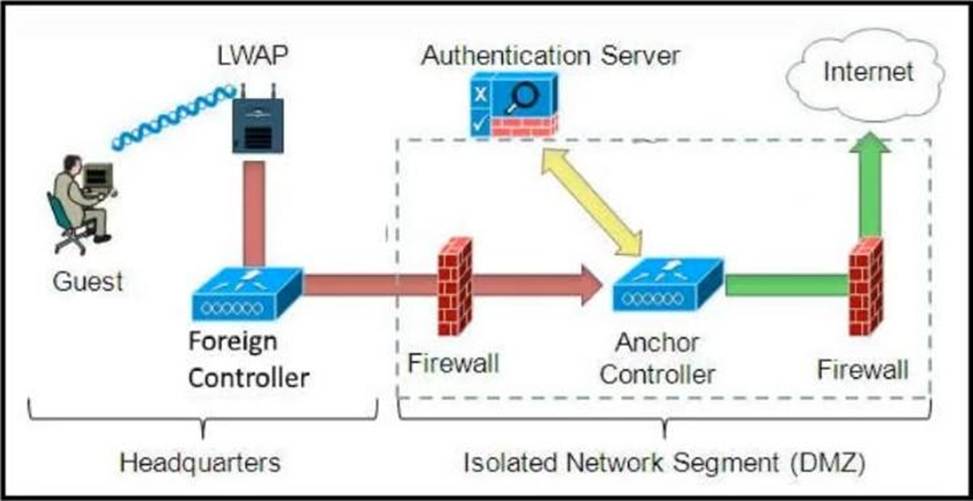
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
- A . Send packets from the foreign controller to the anchor controller via Layer 3 MPLS VPN or VRF-Lite
- B . Send packets without encapsulation to the anchor controller over the routed network.
- C . Encapsulate packets into an EoIP tunnel and send them to the anchor controller.
- D . Send packets from the foreign controller to the anchor controller via IPinIP or IPsec tunnel.
