Practice Free 400-007 Exam Online Questions
Which two characteristics are associated with 802 1s? (Choose two)
- A . 802.1s supports up to 1024 instances of 802.1
- B . 802.1 s is a Cisco enhancement to 802.1w.
- C . 802.1s provides for faster convergence over 802 1D and PVST+.
- D . CPU and memory requirements are the highest of all spanning-tree STP implementations.
- E . 802.1s maps multiple VLANs to the same spanning-tree instance
What best describes the difference between Automation and Orchestration?
- A . Automation refers to an automatic process for completing a single task and Orchestration refers to assembling and coordinating a set of tasks and conditions.
- B . Automation describes a hands-off configuration process while Orchestration refers to sets of automation tasks that require the network administrator to coordinate
- C . Automation refers to an automatic process for completing multiple tasks with conditions and Orchestration refers to executing tasks in parallel.
- D . Automation refers to scripting languages (Python. Ansible etc.) and Orchestration refers to commercial products that control configuration deployment
Which best practice ensures data security in the private cloud?
- A . Use IPsec for communication between unsecured network connection
- B . Encrypt data at rest and in transition.
- C . Use the same vendor for consistent encryption.
- D . Anonymize data ownership to comply with privacy rules.
When an SDN-based model is used to transmit multimedia traffic, which aspect should an architect consider while designing the network?
- A . QoE estimation
- B . security
- C . traffic patterns
- D . flow forwarding
The administrator of a small branch office wants to implement the Layer 2 network without running STP. The office has some redundant paths.
Which mechanism can the administrator use to allow redundancy without creating Layer 2 loops?
- A . Use double-sided VPC on both switches
- B . Use two port channels as Flex links
- C . Use fabric path with ECMP
- D . Use 802.3ad link bundling.
B
Explanation:
Reference: https://www.cisco.com/en/US/docs/switches/lan/catalyst3850/software/release/3se/consolidated_guide/b_consolidated_3850_3se_cg_chapter_01001101.html
Refer to the table.
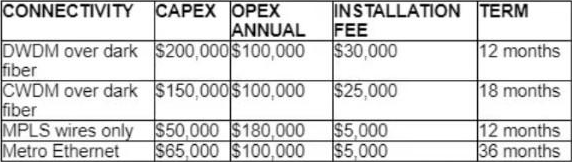
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The migration is estimated to take 20 months to complete but might extend an additional 10 months if issues arise. All connectivity options meet the requirements to migrate workloads.
Which transport technology provides the best ROI based on cost and flexibility?
- A . CWDM over dark fiber
- B . MPLS
- C . DWDM over dark fiber
- D . Metro Ethernet
Company XYZ is planning to deploy primary and secondary (disaster recovery) data center sites. Each of these sites will have redundant SAN fabrics and data protection is expected between the data center sites. The sites are 100 miles (160 km) apart and target RPO/RTO are 3 hrs and 24 hrs, respectively.
Which two considerations must Company XYZ bear in mind when deploying replication in their scenario? (Choose two.)
- A . Target RPO/RTO requirements cannot be met due to the one-way delay introduced by the distance between sites.
- B . VSANs must be routed between sites to isolate fault domains and increase overall availability.
- C . Synchronous data replication must be used to meet the business requirements
- D . Asynchronous data replication should be used in this scenario to avoid performance impact in the primary site.
- E . VSANs must be extended from the primary to the secondary site to improve performance and availability.
Which two areas of business presents a technical solution to support the company during emergency situations by understanding the data flows and using business processes to expiam how it answers to business needs and enables the business to improve’? (Choose two.)
- A . decentralized device management
- B . BYOD policy
- C . disaster recovery
- D . centralized device management
- E . business continuity
Company XYZ is migrating their existing network to IPv6 and they must plan for Layer 2 and Layer 3 devices Some of the access layer switches do not support IPv6, however, core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration.
Which migration strategy should be used in the design?
- A . The access layer switches must support IGMP snooping at a minimum. Any switches that do not support IGM snooping must be replaced.
- B . Upgrade the nonsupporting switches Otherwise, it will cause an issue with the migration.
- C . Layer 2 switches will not affect the implementation of IPv6. They can be included in the design in their current state.
- D . The access layer switches must support DHCPv6. Any switches that do not support DHCPv6 must be replaced.
You are a network designer and you must ensure that the network you design is secure.
How do you plan to prevent infected devices on your network from sourcing random DDoS attacks using forged source address?
- A . ACL based forwarding
- B . unicast RPF loose mode
- C . unicast RPF strict mode
- D . ACL filtering by destination
