Practice Free 400-007 Exam Online Questions
Which two foundational aspects of loT are still evolving and being worked on by the industry at large? (Choose two)
- A . WiFi protocols
- B . Regulatory domains
- C . Low energy Bluetooth sensors
- D . loT consortia
- E . Standards
Which two descriptions of CWDM are true? (Choose two)
- A . typically used over long distances, but requires optical amplification
- B . uses the 850nm band
- C . allows up to 32 optical earners to be multiplexed onto a single fiber
- D . shares the same transmission window as DWDM
- E . Passive CWDM devices require no electrical power
What are two design constraints in a standard spine and leaf architecture? (Choose two.)
- A . Spine switches can connect to each other.
- B . Each spine switch must connect to every leaf switch.
- C . Leaf switches must connect to each other.
- D . Endpoints connect only to the spine switches.
- E . Each leaf switch must connect to every spine switch.
An engineer is designing the QoS strategy for Company XYZ. Based on initial analysis, a lot of scavenger type of traffic is traversing the network’s 20Mb Internet link toward the service provider. The new design must use a QoS technique that limits scavenger traffic to 2 Mbps, which helps avoid oversubscription of the link during times of congestion.
Which QoS technique can be used to facilitate this requirement?
- A . class-based traffic policing
- B . LLQ
- C . CBWFQ
- D . class-based traffic shaping
Two routers R1 and R2 are directly connected through an Ethernet link. Both routers are running OSPF over the Ethernet link and OSPF has been registered with BFD. R1 has been set up to transmit BFD at a 50 ms interval, but R2 can receive only at a 100 ms rate due to platform limitations.
What does this mean?
- A . After the initial timer exchange. R2 sets its transmission rate to the R1 Desired Min TX interval
- B . After the initial timer exchange. R1 sets its transmission rate to the R2 Required Min RX interval
- C . Timers renegotiate indefinitely, so the timer exchange phase never converges
- D . R2 sets the P-bit on all BFD control packets until R2 sends a packet with the F-bit set
Which two points must network designers consider when designing a new network design or when evaluating an existing network design to help them understand the high-level design direction with regards to the security aspects? (Choose two)
- A . Consider Business objectives and goals
- B . Consider organization’s security policy standards
- C . Consider for only multi-site networks
- D . Consider for only new network technologies and components
A key to maintaining a highly available network is building in the appropriate redundancy to protect against failure. This redundancy is carefully balanced with the inherent complexity of redundant systems.
Which design consideration is relevant for enterprise WAN use cases when it comes to resiliency?
- A . Design in a way that expects outages and attacks on the network and its protected resources
- B . The design approach should consider simple and centralized management aspect
- C . Design in a way that it simplifies and improves ease of deployment
- D . Design automation tools wherever it is appropriate for greater visibility
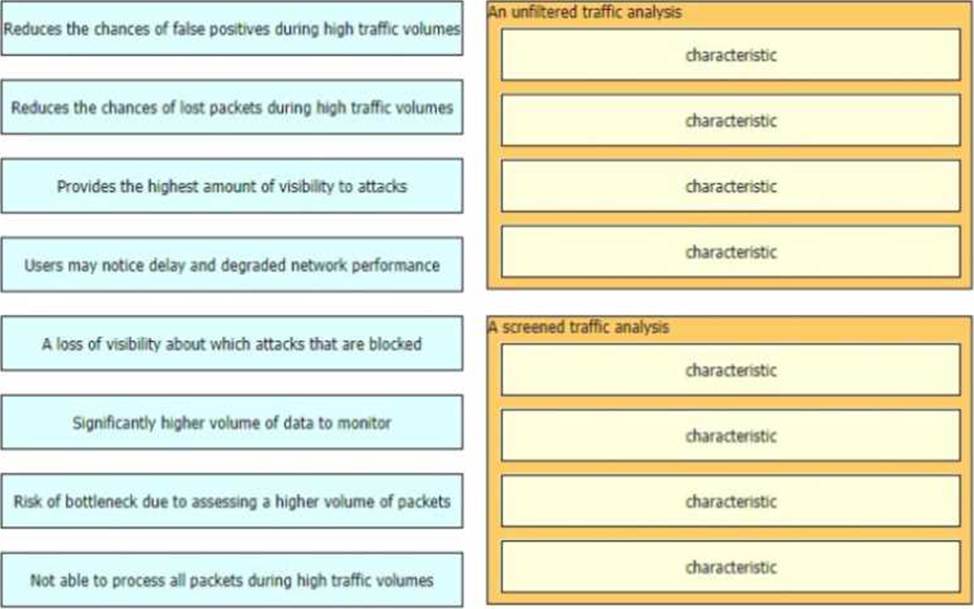
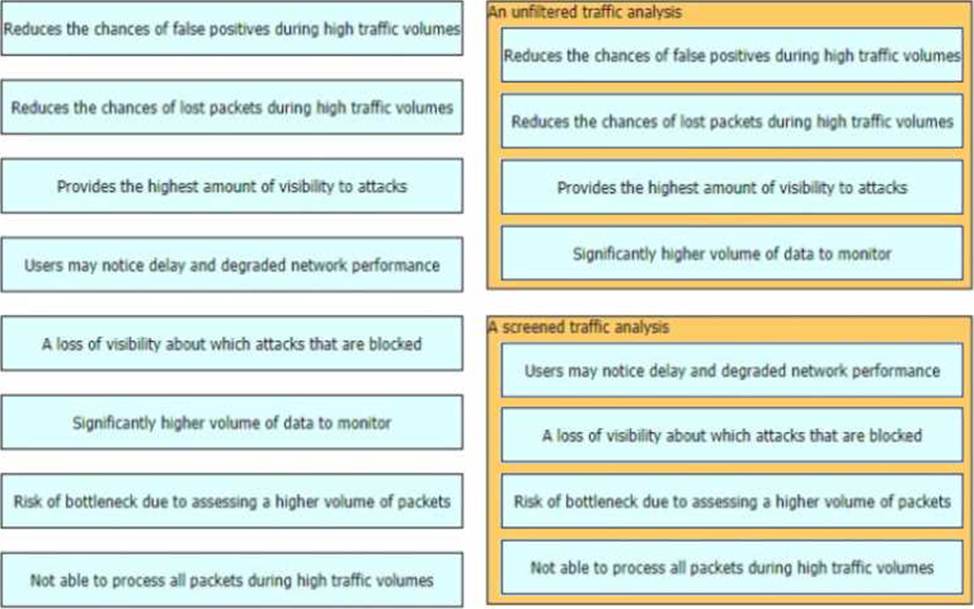
DRAG DROP
When a detection system for protecting a network from threats sourced from the Internet is designed there are two common deployment methods, where the system is placed differently relative to the perimeter firewall
• An unfiltered detection system examines the raw Internet data streams before it reaches the firewall
• A screened detection solution which monitors traffic that is allowed through the firewall Both have
its advantages and disadvantages drag and drop the characteristics on the left to the corresponding category on the right in no particular order.
Company XYZ is running SNMPv1 in their network and understands that it has some flaws. They want to change the security design to implement SNMPv3 in the network.
Which network threat is SNMPv3 effective against?
- A . man-in-the-middle attack
- B . masquerade threats
- C . DDoS attack
- D . brute force dictionary attack
Which technology is an open-source infrastructure automation tool that automates repetitive tasks for users who work in networks such as cloud provisioning and intraservice orchestration?
- A . Ansible
- B . Contrail
- C . Java
- D . Jinja2
