Practice Free 400-007 Exam Online Questions
Which three components are part of the foundational information security principles of the CIA triad? (Choose three.)
- A . cryptography
- B . confidentiality
- C . C. authorization
- D . identification
- E . integrity
- F . availability
Which solution component helps to achieve comprehensive threat protection and compliance for migration to multicloud SDX architectures?
- A . system-oriented architecture
- B . OSASE architecture
- C . platform-oriented architecture
- D . SASE architecture
What is the most important operational driver when building a resilient and secure modular network design?
- A . Reduce the frequency of failures requiring human intervention
- B . Minimize app downtime
- C . Increase time spent on developing new features
- D . Dependencies on hardware or software that is difficult to scale
Which two factors must be considered while calculating the RTO? (Choose two )
- A . importance and priority of individual systems
- B . maximum tolerable amount of data loss that the organization can sustain
- C . cost of lost data and operations
- D . how often backups are taken and how quickly these can be restored
- E . steps needed to mitigate or recover from a disaster
The General Bank of Greece plans to upgrade its legacy end-of-life WAN network with a new flexible, manageable, and scalable solution. The mam requirements are ZTP support, end-to-end encryption application awareness and segmentation. The CTO states that the main goal of the bank is CAPEX reduction.
Which WAN technology should be used for the solution?
- A . SD-branch
- B . DMVPN with PfR
- C . managed SD-WAN
- D . SD-WAN
An enterprise solution team is performing an analysis of multilayer architecture and multicontroller SDN solutions for multisite deployments. The analysis focuses on the ability to run tasks on any controller via a standardized interface.
Which requirement addresses this ability on a multicontroller platform?
- A . Deploy a root controller to gather a complete network-level view.
- B . Use the East-West API to facilitate replication between controllers within a cluster.
- C . Build direct physical connectivity between different controllers.
- D . Use OpenFlow to implement and adapt new protocols.
Which two pain points are the most common for container technology adoption? (Choose two)
- A . Performance
- B . Security
- C . Cost
- D . Container deployment
- E . Skilled staff
- F . Compliance
Which two characteristics apply to firewall transparent mode operations in a firewall solution design? (Choose two.)
- A . Changes in the existing IP addressing and subnets are required
- B . The firewall can participate actively on spanning tree.
- C . Multicast traffic can traverse the firewall.
- D . OSPF adjacencies can be established through the firewall
- E . The firewall acts like a router hop in the network.
DRAG DROP
An enterprise organization currently provides WAN connectivity to their branch sites using MPLS technology, and the enterprise network team is considering rolling out SD-WAN services for all sites.
With regards to the deployment planning, drag and drop the actions from the left onto the corresponding steps on the right.
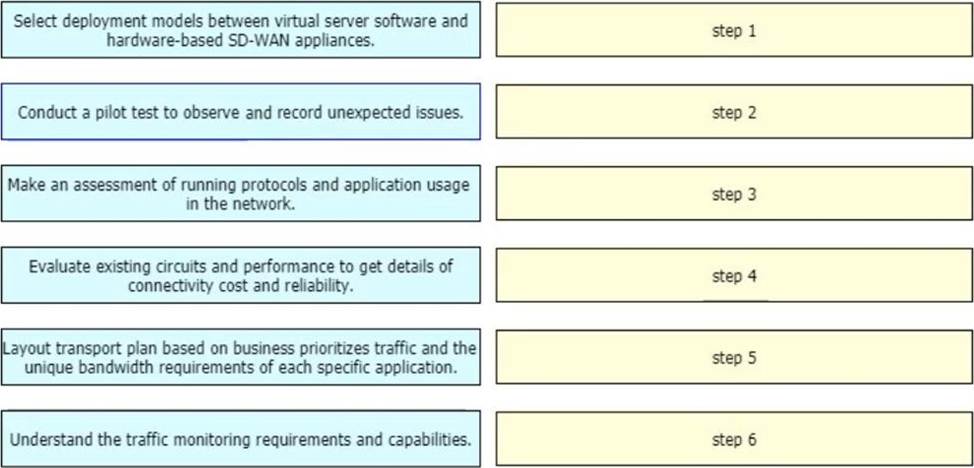
Explanation:
Table
Description automatically generated with medium confidence
Which two technologies enable multilayer segmentation? (Choose two.)
- A . policy-based routing
- B . segment routing
- C . data plane markings
- D . firewalls
- E . filter lists
