Practice Free 350-901 Exam Online Questions
Refer to the exhibit.
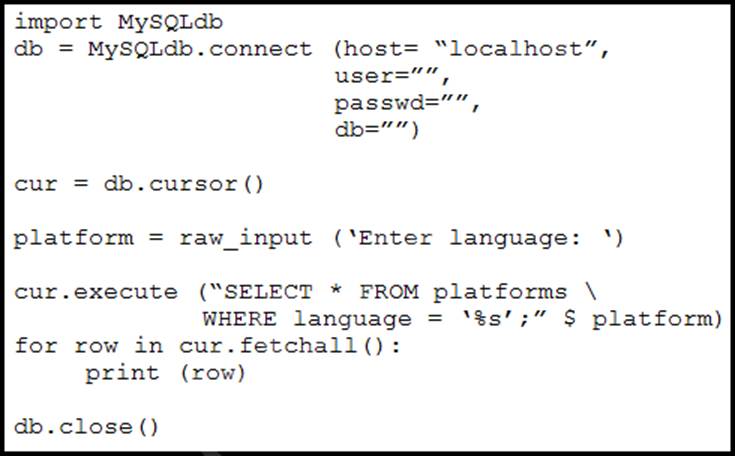
Which action should be performed to avoid an SQL injection attack?
- A . Validate the input on the platform variable.
- B . Develop a denial of service response plan.
- C . Encrypt the password that is used to connect to the database.
- D . Compile the Python file instead of allowing live interpretation.
There is a requirement to securely store unique usernames and passwords. Given a valid username, it is also required to validate that the password provided is correct.
Which action accomplishes this task?
- A . Encrypt the username, hash the password, and store these values.
- B . Hash the username, hash the password, and store these values.
- C . Encrypt the username, encrypt the password, and store these values.
- D . Hash the username, encrypt the password, and store these values.
An engineer developed an application to be used as a file server using Python. The application was placed in a Kubernetes pod and must be accessible from outside the network utilizing an HTTPS service.
Which command must be used to enable the required access?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
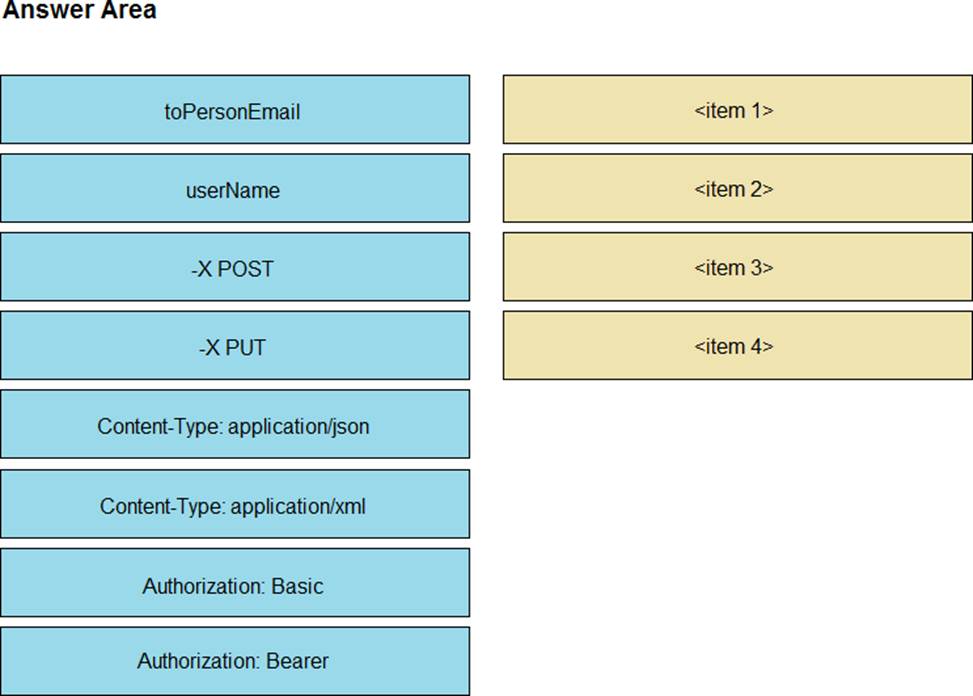
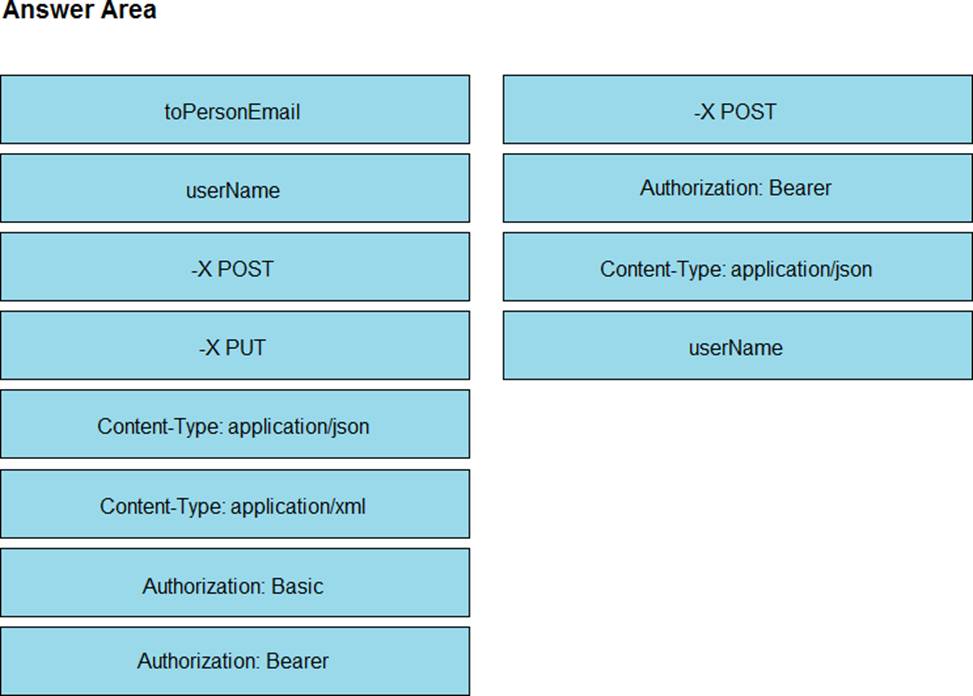
DRAG DROP
Refer to the exhibit.
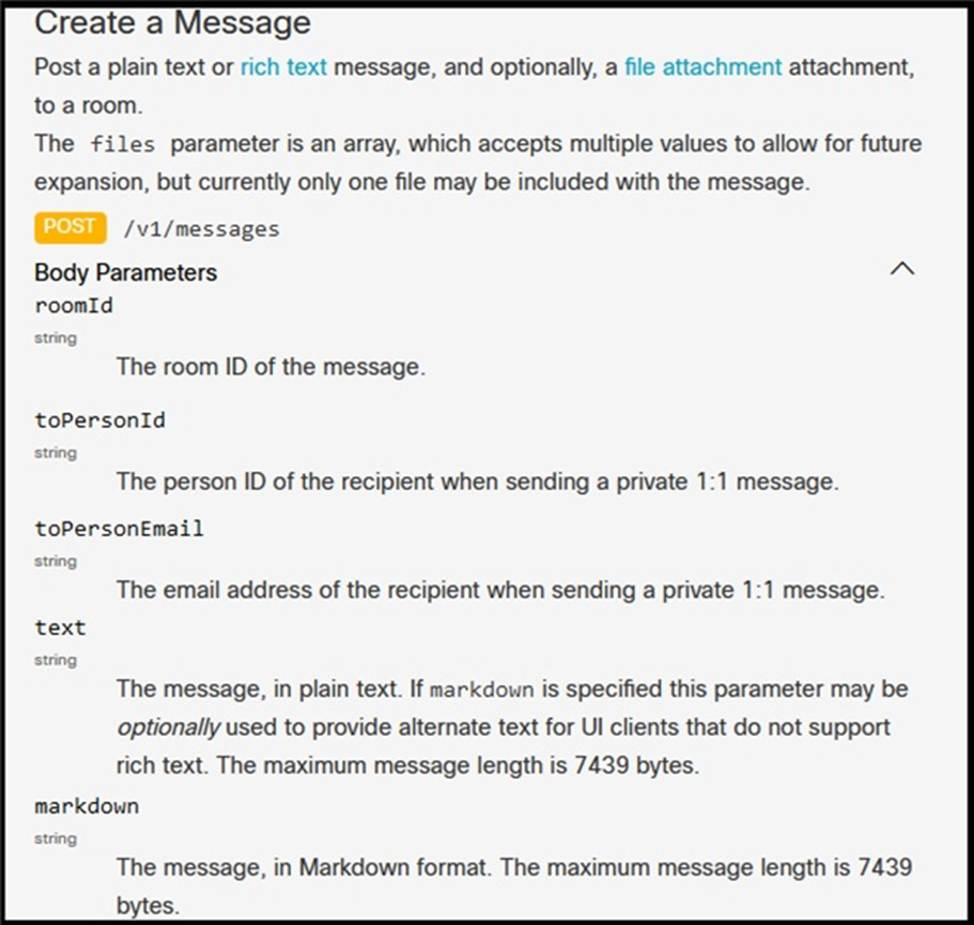

A system administrator has installed a Linux-based alarm system in their home that can execute a Bash shell script when an intruder is detected.
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a chat-ops script that will notify of alarms via the Webex REST API. Not all code snippets are used.
Which database type should be used to store data received from model-driven telemetry?
- A . BigQuery database
- B . Time series database
- C . NoSQL database
- D . PostgreSQL database
Refer to the exhibit.
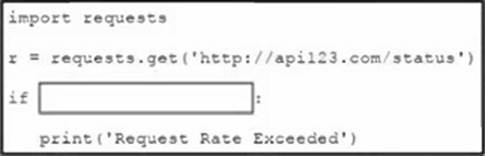
A Python script needs to catch errors when the API request is rate limited and print "Request Rate Exceeded" to stdout.
Which code snippet must be placed in the blank in the code to complete the script?
- A . requests.exceptions.URLNotFound
- B . requests.exceptions.NotExist
- C . r.staus_code == 429
- D . r.response == 429
Refer to the exhibit.
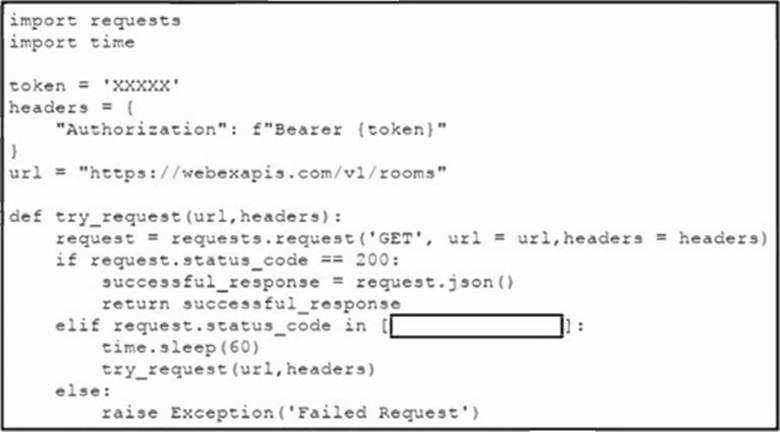
An engineer creates a function that gathers information from the Cisco Webex RESTful API. To enable increased durability, the engineer needs to implement a retry mechanism that pauses the script and retries the request if specific response codes are received.
Which code snippet must be placed in the blank in the code to meet this requirement?
- A . 400,403,409,504
- B . 403,404,409,429
- C . 400,404,502,503
- D . 429,502,503,504
Which model does model-driven telemetry use to transfer monitoring data to a logging server?
- A . SNMP
- B . push
- C . ICMP
- D . pull
Refer to the exhibit.
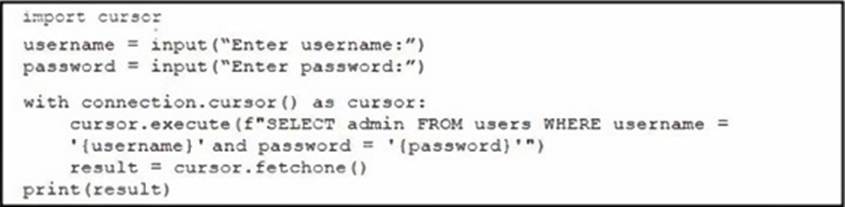
A network engineer writes Python code for a web application to query an SQL database. The code is vulnerable to SQL injection attacks.
Which command must the engineer enter into the username input to exploit the vulnerability?
- A . ‘’; –‘
- B . ; select true; –‘
- C . ‘’; select true; –‘
- D . ’and password =1
A developer deployed a web application in a local data center that is experiencing high traffic load from users that access data through REST API calls. Caching helps to enhance the responsiveness and performance of the API usage.
Which approach must be used to improve cache performance?
- A . Ensure that all read requests are clearly identified by the PUT method.
- B . Implement surrogate key tagging to purge requests.
- C . Use HTTP POST or other non-read methods for read requests when it is possible.
- D . Configure the API payload to return errors in HTTP 200 responses.
