Practice Free 350-901 Exam Online Questions
Which two encryption principles should be applied to secure APIs? (Choose two.)
- A . Use temporary files as part of the encryption and decryption process.
- B . Use encrypted connections to protect data in transit.
- C . Reuse source code that contain existing UUIDs.
- D . Embed keys in code to simplify the decryption process.
- E . Transmit authorization information by using digitally signed payloads.
In an event-driven architecture-based system, what is a characteristic of the subscribers of a topic?
- A . They have access to all the messages in a topic.
- B . The message is channeled by recognizing the message’s function.
- C . They route each incoming message to its destination.
- D . The messages received must be stamped with information that identifies the sender.
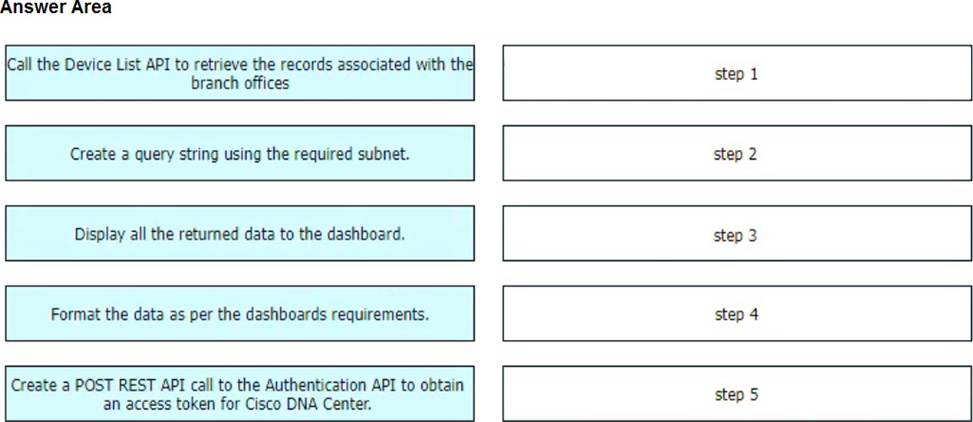
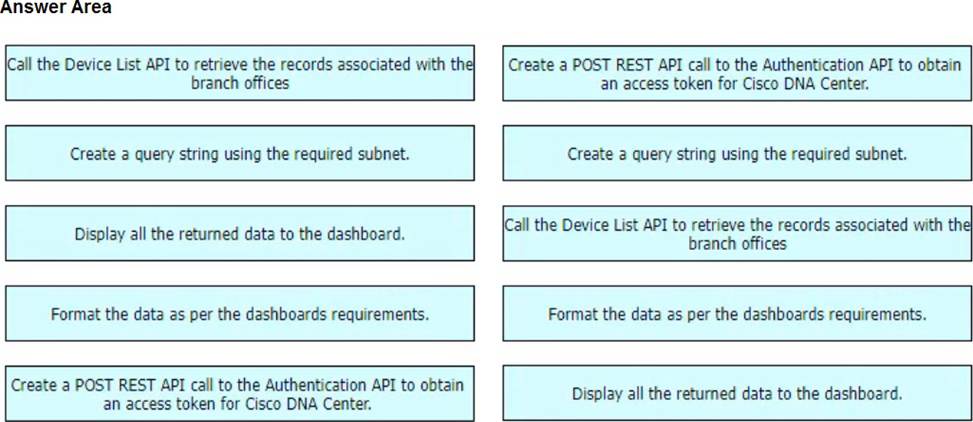
DRAG DROP
Drag and drop the steps from the left into the order on the right to provide a custom dashboard to display the version of code that is installed in a network subnet using the Cisco DNA Center API.
What is a reason to choose global load-balancing instead of local load-balancing?
- A . Allow requests to be distributed and served in a round-robin fashion.
- B . Load-balance across the infrastructure based on workload.
- C . Promote greater security to the application.
- D . Better serve users based on their location.
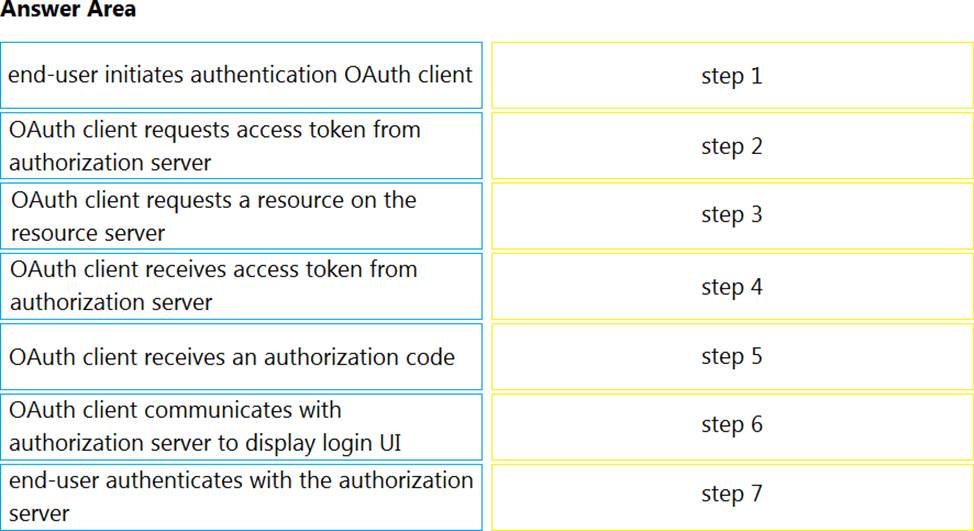
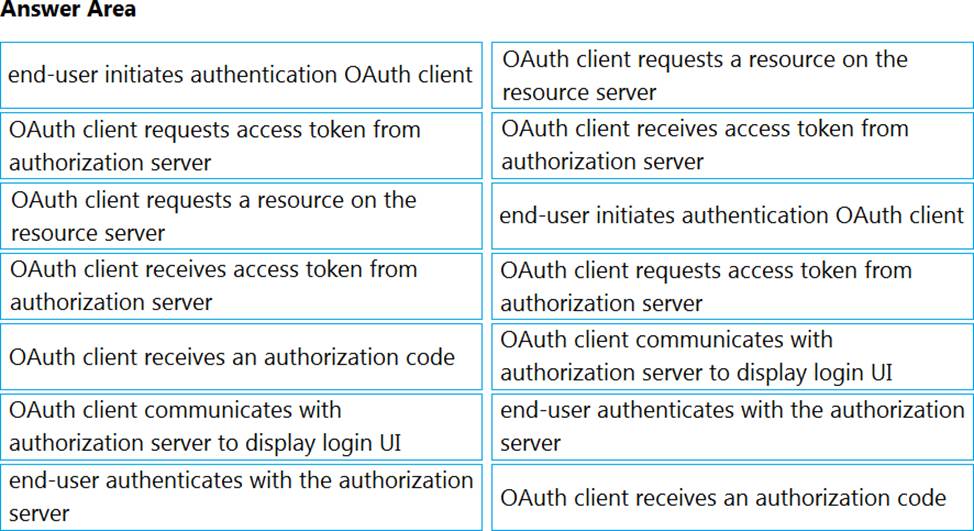
DRAG DROP
Drag and drop the steps on the left into the order on the right for an end-user to access an OAuth2 protected resource using the ‘Authorization Code Grant’ flow.
Which two methods are API security best practices? (Choose two.)
- A . Use tokens after the identity of a client has been established.
- B . Use the same operating system throughout the infrastructure.
- C . Use encryption and signatures to secure data.
- D . Use basic auth credentials over all internal API interactions.
- E . Use cloud hosting services to manage security configuration.
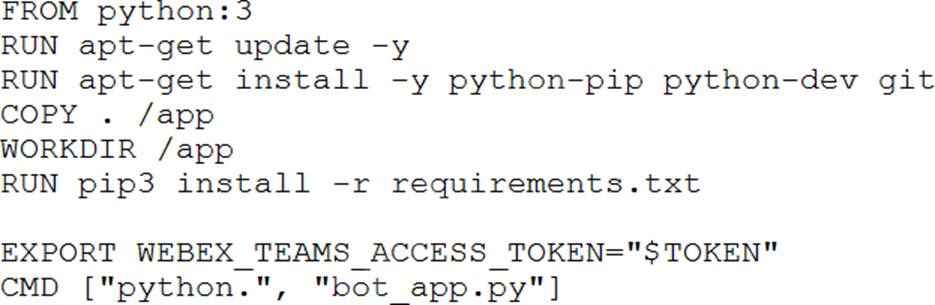
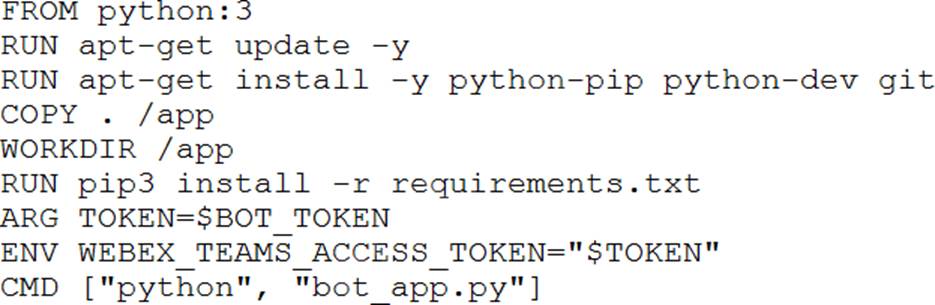
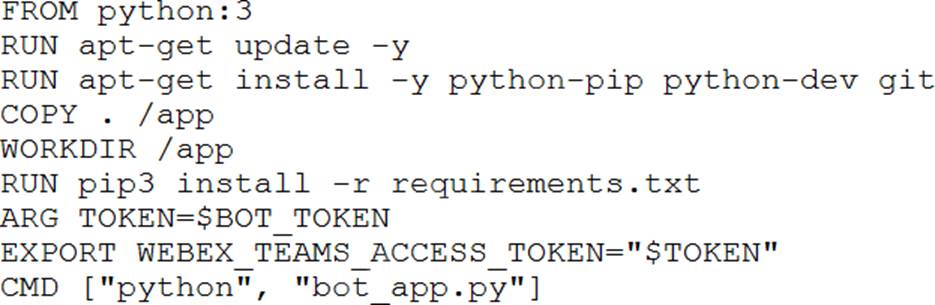
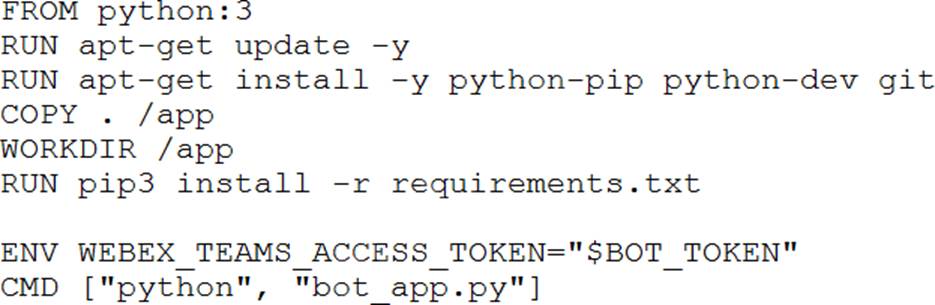
The access token for a Webex bot has been stored in an environment variable using the command: export bot_token=6bec40cf957de397561557a4fac9ea0
The developer now wants to containerize the Python application which will interact with the bot, and will use this build command to add the token to the build image: docker build –build-arg BOT_TOKEN=$bot_token
Which Dockerfile should be used to build the Docker image so that the bot access token is available as an environment variable?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
While working with the Webex API, on an application that uses end-to-end encryption, a webhook has been received.
What must be considered to read the message?
- A . Webhook information cannot be used to read the message because of end-to-end encryption. The API key is needed to decrypt the message.
- B . Webhook returns the full unencrypted message. Only the body is needed to query the API.
- C . Webhook returns a hashed version of the message that must be unhashed with the API key.
- D . Webhook returns message identification. To query, the API is needed for that message to get the decrypted information.
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the code to retrieve the audit logs that were created after a specific date. Not all options are used.
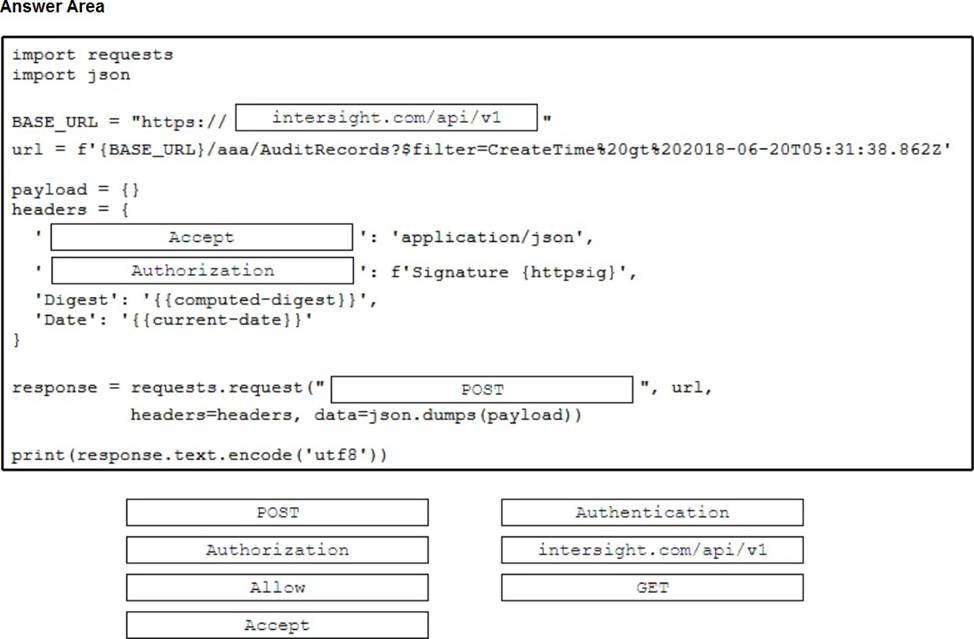
Refer to the exhibit.
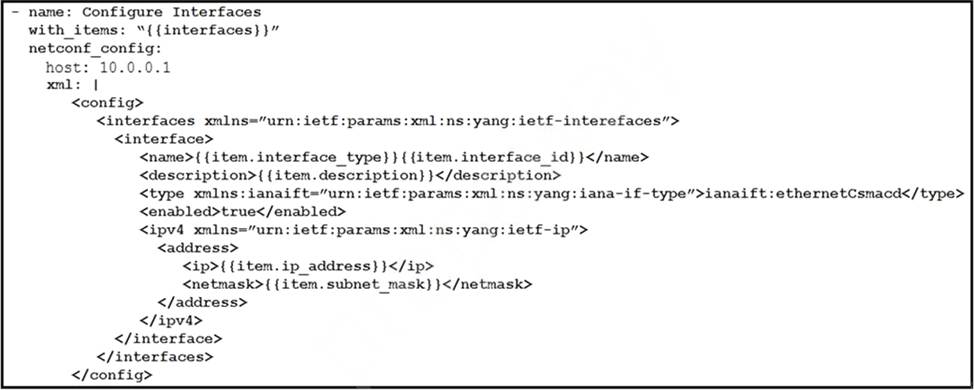
The Ansible playbook is using the netconf_module to configure an interface using a YANG model.
As part of this workflow, which YANG models augment the interface?
- A . ietf-interfaces and ietf-ip
- B . iana-if-type and ietf-interfaces
- C . ietf-ip and openconfig-interface
- D . ietf-ip and iana-if-type
