Practice Free 350-901 Exam Online Questions
Which Git command enables the developer to revert back to f414f31 commit to discard changes in the current working tree?
- A . git reset –hard f414f31
- B . git reset checkout –hard f414f31
- C . git reset –soft f414f31
- D . git checkout f414f31
An application is developed in order to communicate with Cisco Webex. For reporting, the application must retrieve all the messages sent to a Cisco Webex room on a monthly basis.
Which action calls /v1/messages directly?
- A . Set up a webhook that has messages as the resource type and store the results locally.
- B . Utilize the pagination functionality by defining the max property.
- C . Recursively call the /v1/messages endpoint by using the before Message property.
- D . Filter the response results by specifying the created property in the request.
An engineer wants to design an application that meets these requirements:
• maintainable and adaptable to ensure future expansion
• written using object-oriented programming
• must account for an increased variety of subclasses
Which design principle should the engineer use?
- A . single responsibility
- B . interface segregation
- C . high availability
- D . rate limiting
Refer to the exhibit.
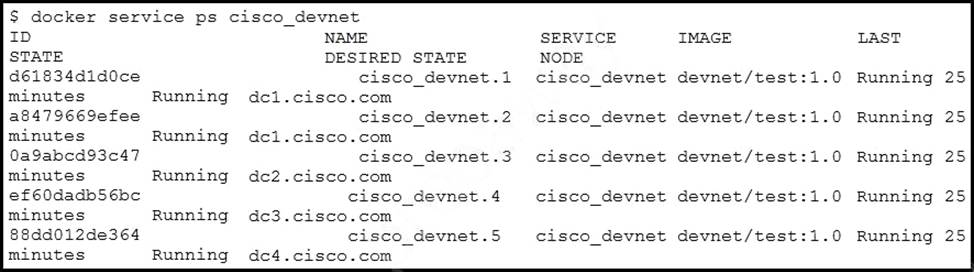
The cisco_devnet Docker swarm service runs across five replicas. The development team tags and imports a new image named devnet/ test:1.1 and requests that the image be upgraded on each container. There must be no service outages during the upgrade process.
Which two design approaches must be used? (Choose two.)
- A . Enable parallel upgrades by using the docker service update command.
- B . Ensure that the service is hosted behind a VIP with no session persistence.
- C . Ensure that the service replicas are set to a minimum of 5.
- D . Update the restart policy of the containers to restart upon failure.
- E . Implement rolling upgrades by using the docker service update command.
An architect must optimize traffic that targets a popular API endpoint. Currently, the application downloads a large file hourly, but often the file is unchanged and the download causes unnecessary load and delays.
Which cURL command must be used to determine the last modified date of the file and to optimize the API usage?
- A . curl -H ‘Cache-Control: no-cache’ request
- B . curl HEAD request
- C . curl –silent request
- D . curl GET request
What is a characteristic of a monolithic architecture?
- A . It is an application with multiple independent parts.
- B . New capabilities are deployed by restarting a component of the application.
- C . A service failure can bring down the whole application.
- D . The components are platform-agnostic.
A software team is designing a monitoring solution for a cloud-native application.
The solution enables:
• effective monitoring
• easy troubleshooting and maintenance
• reduction in time it takes to resolve issues
• breaks down silos between different teams
Which observability tracing design pattern should be used in the application design?
- A . factory pattern based on OpenTelemetry
- B . exception based on OpenTracing
- C . observer based on OpenTracing
- D . distributed based on OpenTelemetry
What is the function of dependency management?
- A . separating code into modules that execute independently
- B . utilizing a single programming language/framework for each code project
- C . automating the identification and resolution of code dependencies
- D . managing and enforcing unique software version names or numbers
DRAG DROP
Refer to the exhibit.
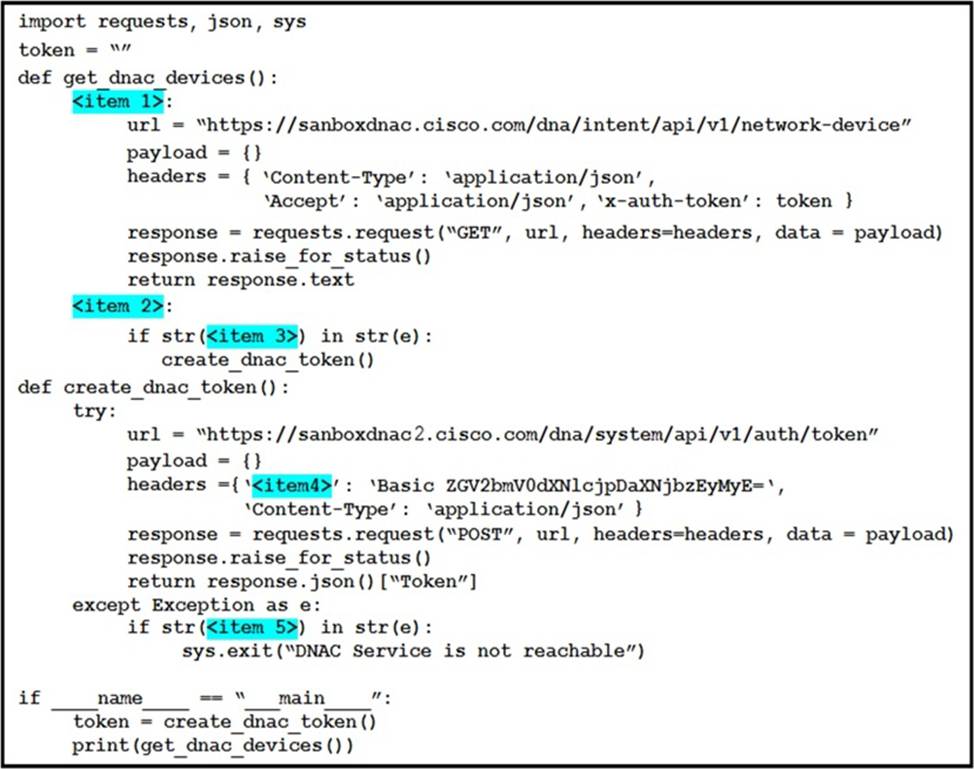
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.
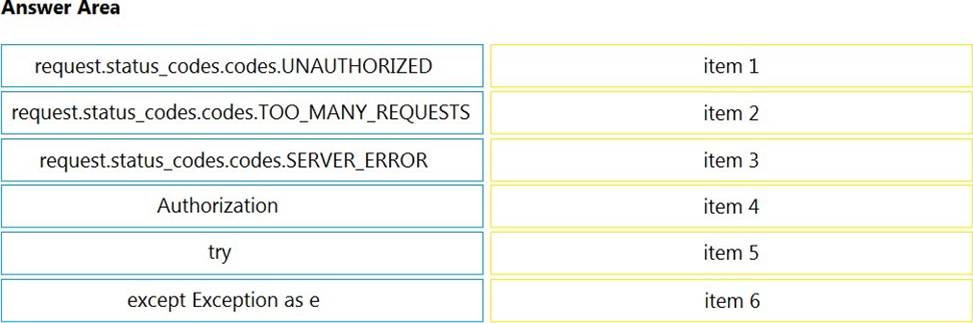
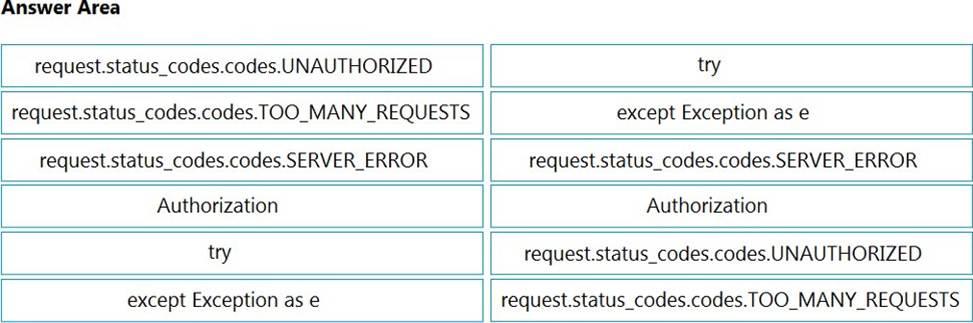
DRAG DROP
Refer to the exhibit.
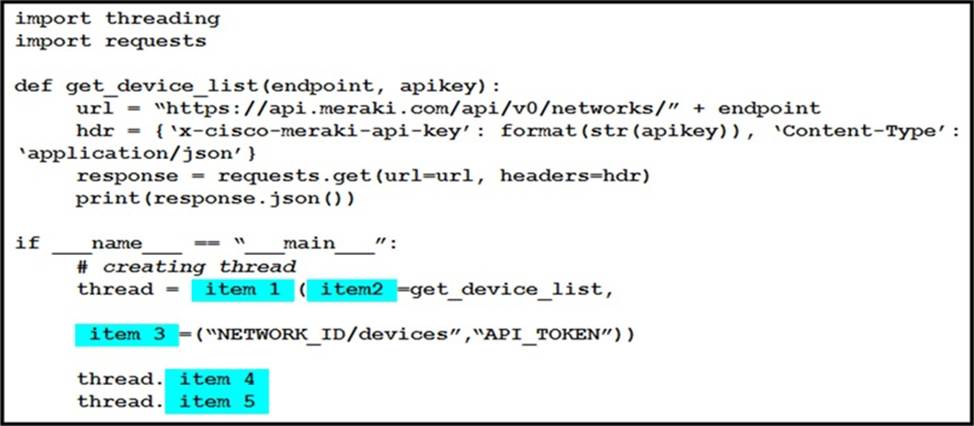
Python threading allows a developer to have different parts of a program run concurrently and simplify a design.
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a thread instance.


