Practice Free 350-901 Exam Online Questions
Refer to the exhibit.
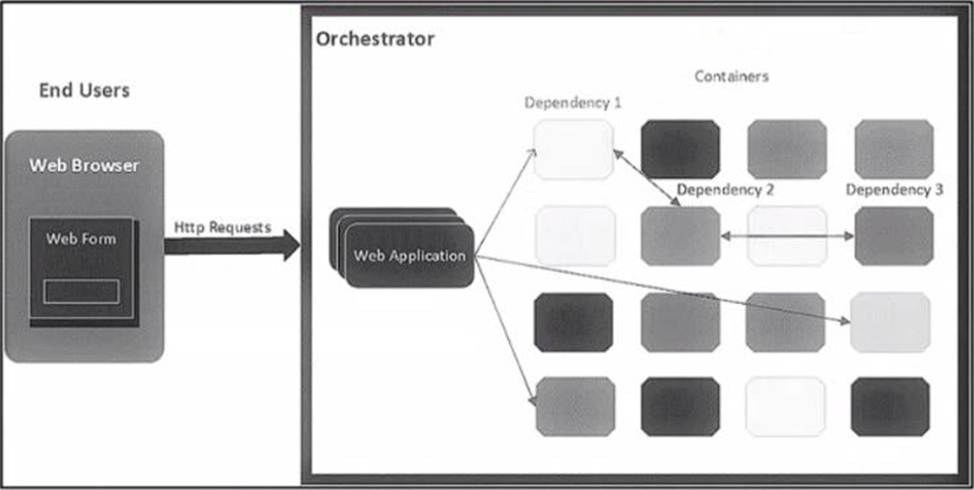
The application follows a containerized microservices architecture that has one container per microservice. The microservices communicate with each other by using REST APIs. The double-headed arrows in the diagram display chains of synchronous HTTP calls needed for a single user request.
Which action ensures the resilience of the application in the scope of a single user request?
- A . Implement retries with exponential backoff during HTTP API calls.
- B . Set up multiple instances of each microservice in active/active mode by using the Orchestrator.
- C . Redesign the application to be separated into these three layers: Presentation, API, and Data.
- D . Create two virtual machines that each host an instance of the application and set up a cluster.
Which two actions must be taken when an observable microservice application is developed? (Choose two.)
- A . Know the state of a single instance of a single service.
- B . Place “try/except” statement in code.
- C . Place log statements in the code.
- D . Use distributed tracing techniques.
- E . Deploy microservice to multiple datacenters.
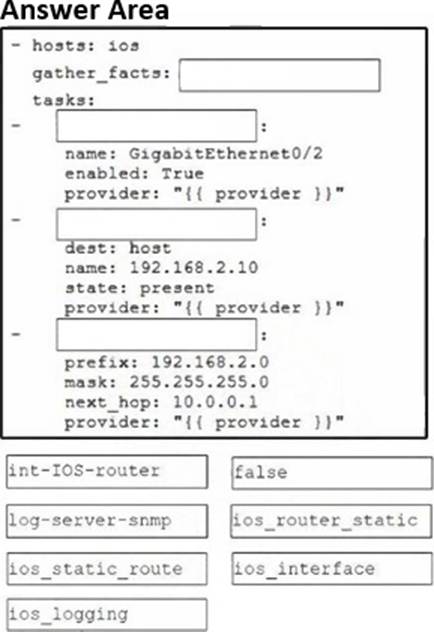
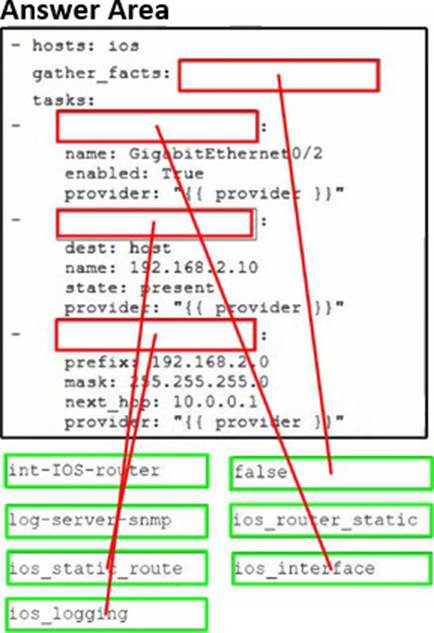
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the code to create an Ansible playbook.
The playbook must apply the configurations in a Cisco IOS 15.6 router:
• Enable the GigabitEthernet0/2 interface.
• Enable host logging for destination 192.168.2.10.
• Add a static route that has a prefix of 192.168.2.0, a mask of 255.255.255.0, and a next hop of 10.0.0.1.
Not all options are used.
Which process decouples PII from a set of data and provides anonymity, but allows identification of the person to whom the data belongs under strictly controlled cases?
- A . data anonymization
- B . data de-identification
- C . data split
- D . data encryption
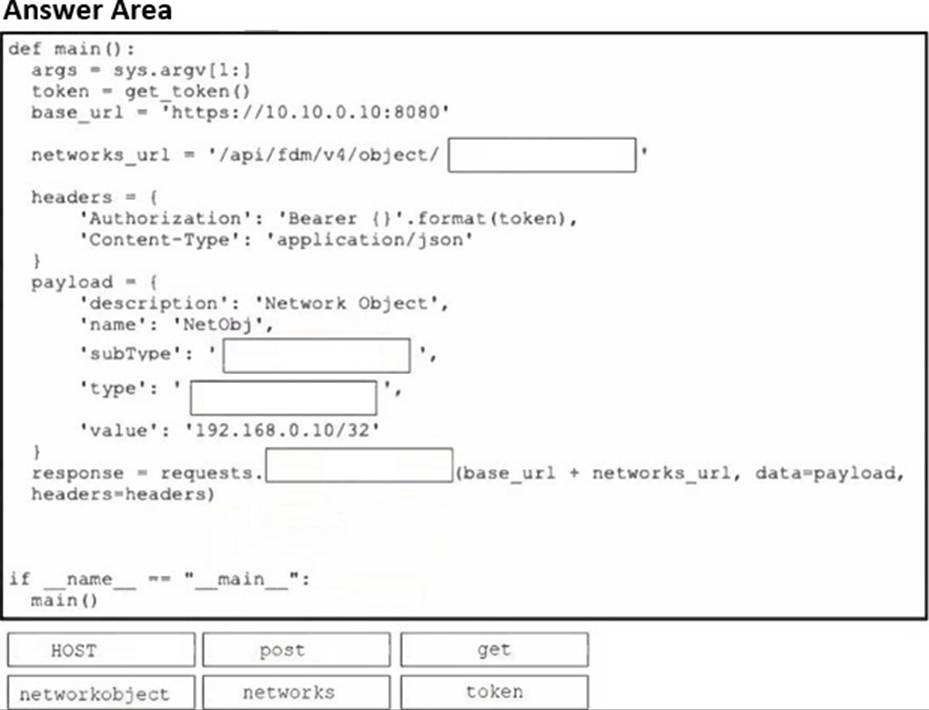
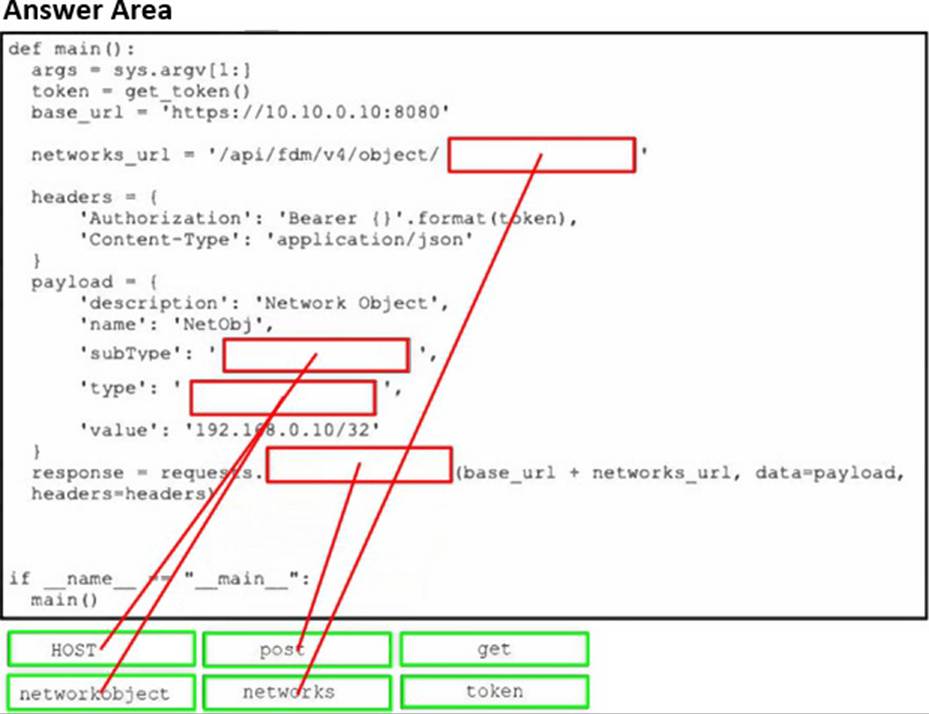
DRAG DROP
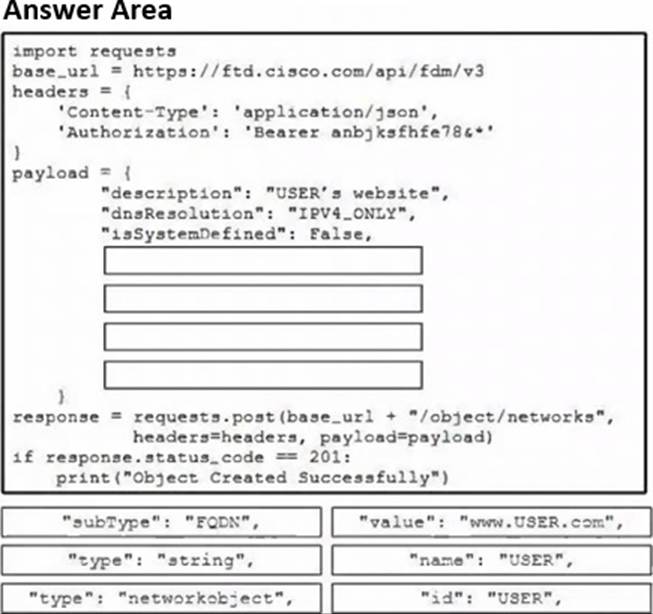
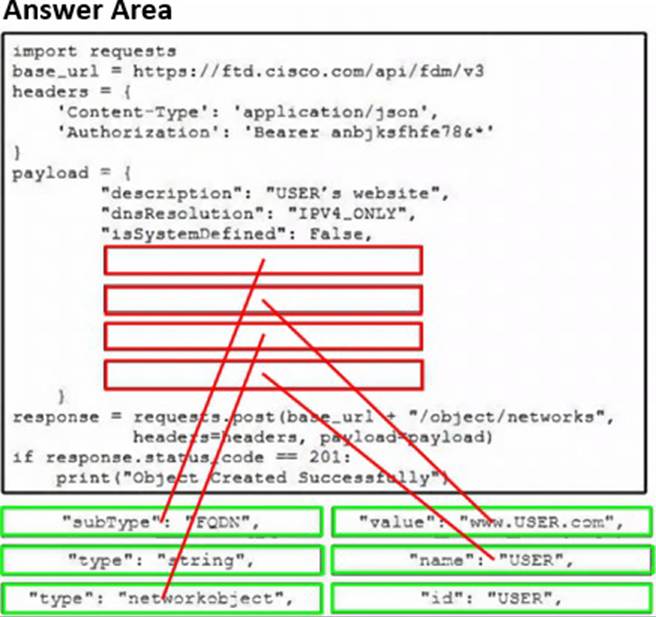
Refer to the exhibit.
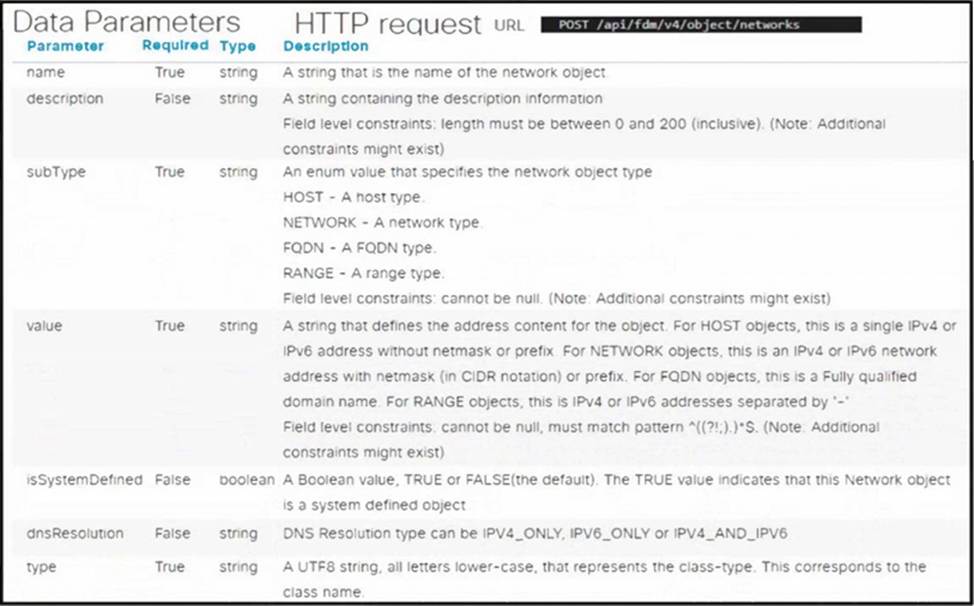
Drag and drop the code snippets from the bottom onto the blanks in the code to construct a Python script that creates a new network object in FDM. Not all options are used.
A timeframe custom dashboard must be developed to present data collected from Cisco Meraki. The dashboard must include a wireless health alert count.
What needs to be built as a prerequisite?
- A . A publicly available HTTP server to receive Meraki Webhooks from the Meraki Scanning API.
- B . A publicly available HTTP server to receive Meraki Webhooks from the Meraki Dashboard API.
- C . A daemon to consume the Wireless Health endpoint of the Meraki Dashboard API.
- D . A daemon to consume the Wireless Health endpoint of the Meraki Scanning API.
Refer to the exhibit.

An engineer needs to encrypt communication between two servers using self-signed certificates.
Which code snippet must be placed in the blank in the code to complete the generation of the .crt certificate file?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
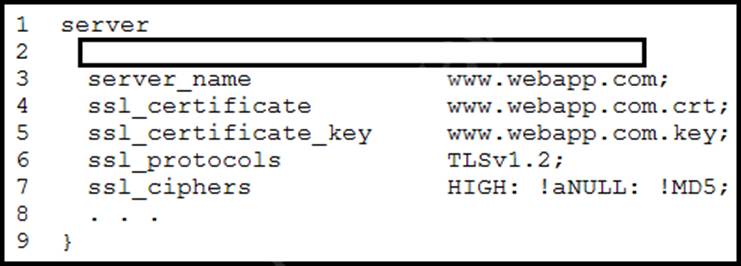
A developer must configure an SSL certificate for an nginx web server.
Which code must be added on the script to accomplish this configuration?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Which interface provides an IOx application on a Catalyst 9000 Series switch access to the network?
- A . GigabitEthernet 1/0/1
- B . AppGigabitEthernet 1/0/1
- C . AppLoopback 1
- D . Loopback 1
DRAG DROP
Refer to the exhibit.
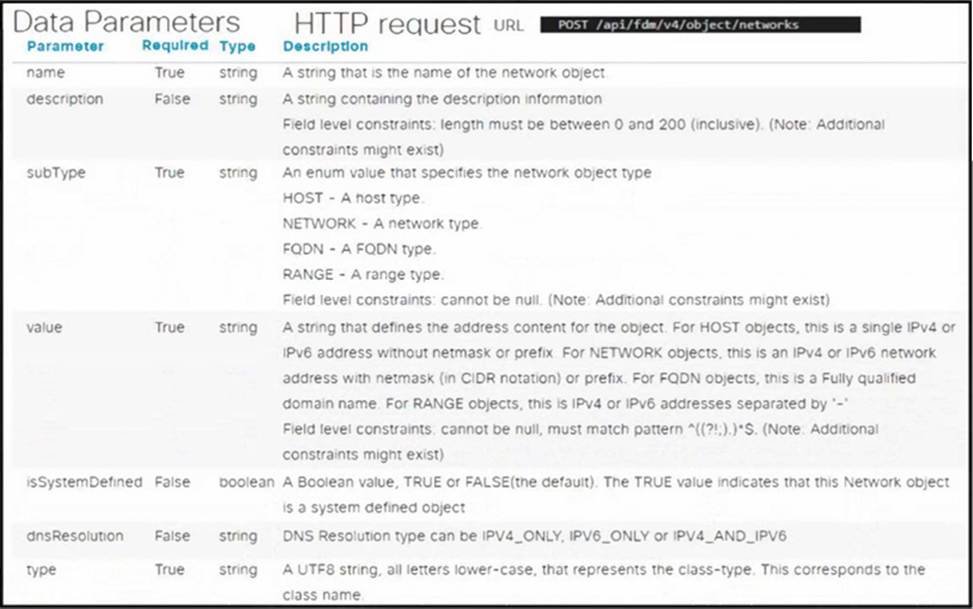
Drag and drop the code snippets from the bottom onto the blanks in the Python script to create a network object using the Cisco Firepower Device Management API. Not all options are used.