Practice Free 350-901 Exam Online Questions
DRAG DROP
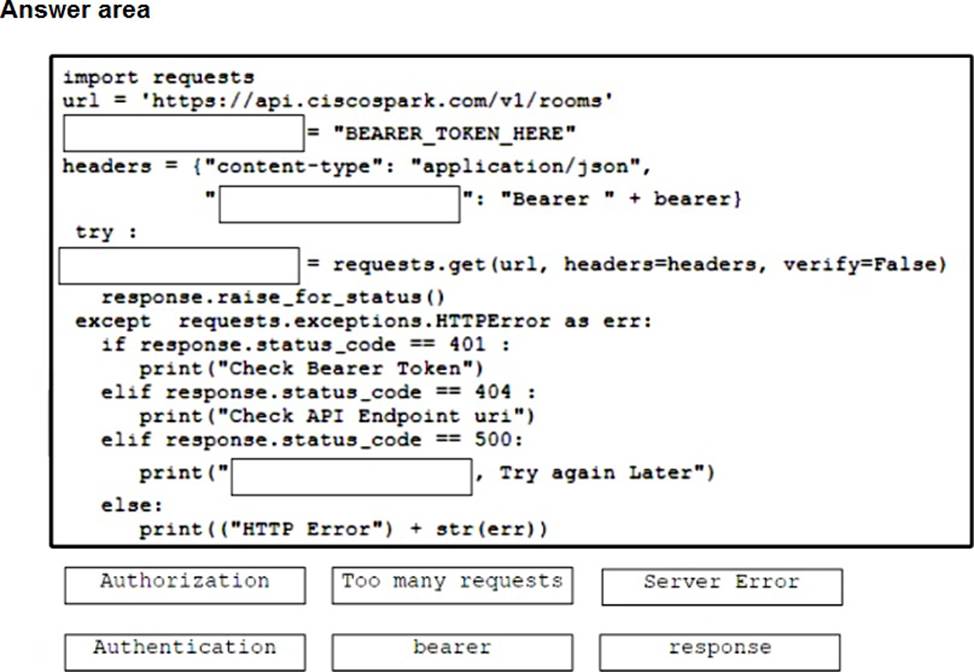
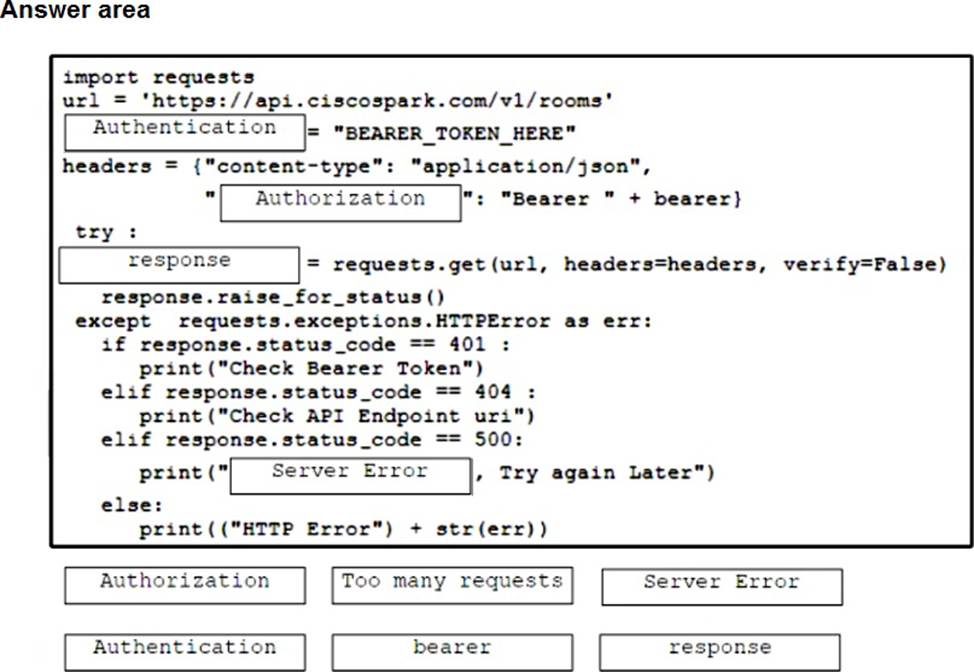
A developer is creating a Python script to use the Webex REST API to list joined spaces and handle and print the errors it receives.
Drag and drop the code from the bottom onto the box where the code is missing to complete the script. Not all options are used.
A custom dashboard of the network health must be created by using Cisco DNA Center APIs. An existing dashboard is a RESTful API that receives data from Cisco DNA Center as a new metric every time the network health information is sent from the script to the dashboard.
Which set of requests creates the custom dashboard?
- A . POST request to Cisco DNA Center to obtain the network health information, and then a GET request to the dashboard to publish the new metric
- B . GET request to Cisco DNA Center to obtain the network health information, and then a PUT request to the dashboard to publish the new metric
- C . GET request to Cisco DNA Center to obtain the network health information, and then a POST request to the dashboard to publish the new metric
- D . PUT request to Cisco DNA Center to obtain the network health information, and then a POST request to the dashboard to publish the new metric
DRAG DROP
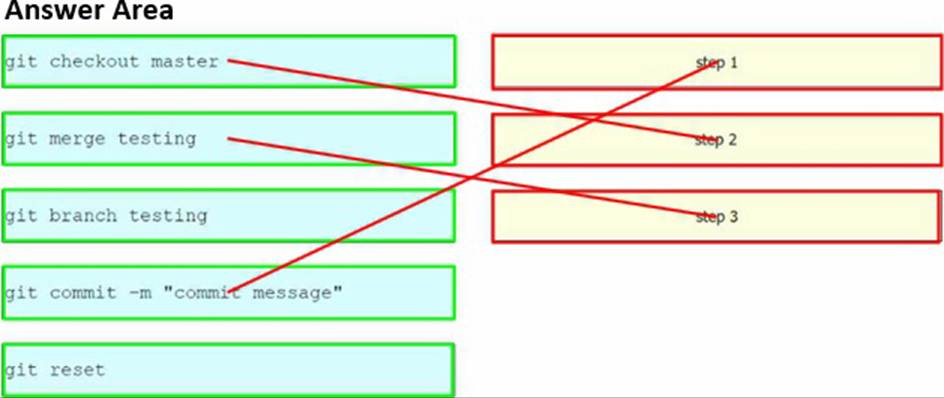
Refer to the exhibit.
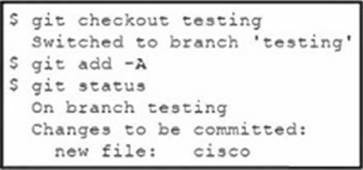
A new file named cisco is added to a branch named testing, but it has not been committed.
Drag and drop the Git commands from the left into the order on the right to merge the testing branch, with the new cisco file, into the master branch. Not all options are used.

Refer to the exhibit.
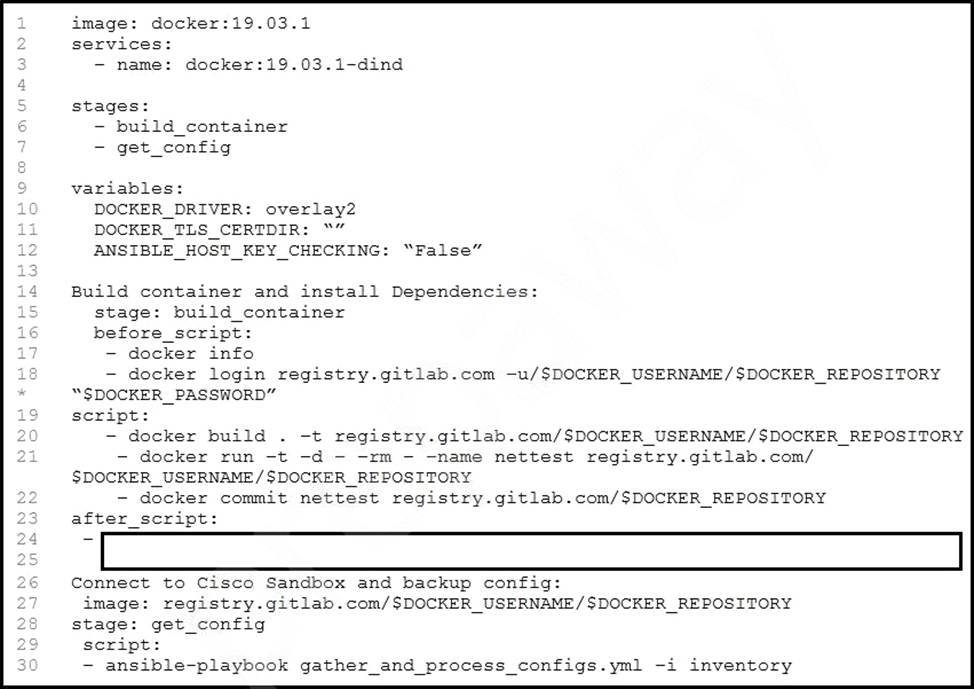
A developer wants to automatically deploy infrastructure for a containerized application. A .gitlab-ci.yml file must describe a pipeline that builds a container based on a supplied Dockerfile and executes an Ansible playbook on the configured container.
What must be added where the code is missing to complete the script?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
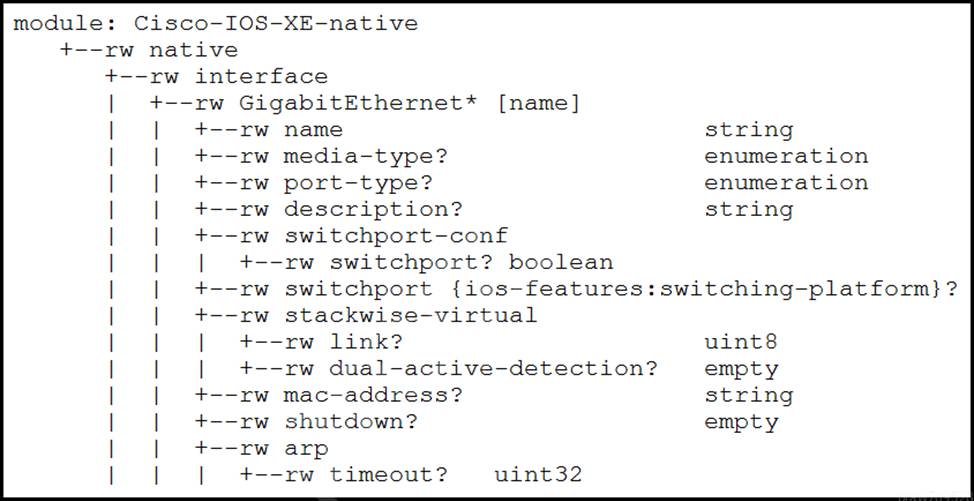
Interface Loopback 1 must be created with IP address 10.30.0.1/ 24 in a Cisco IOS XE device using RESTCONF. The schema that is defined by the exhibit must be used.
Which body and URI should be used for this operation?
A)
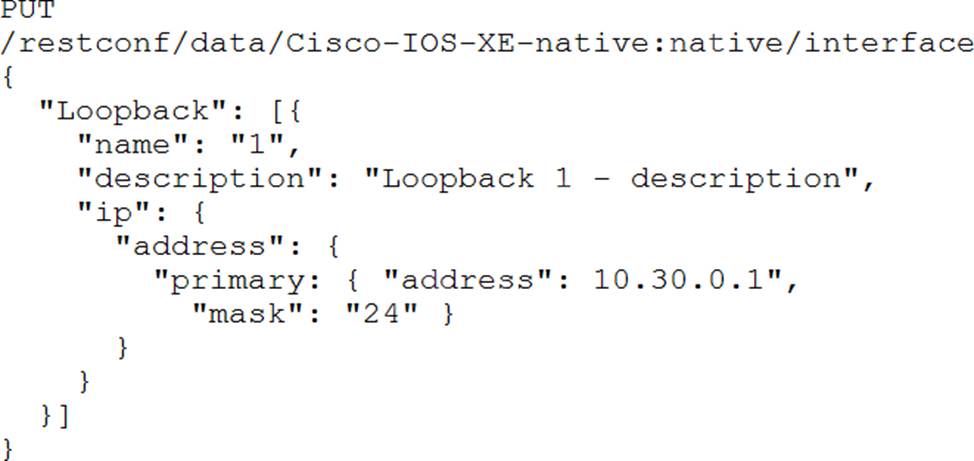
B)
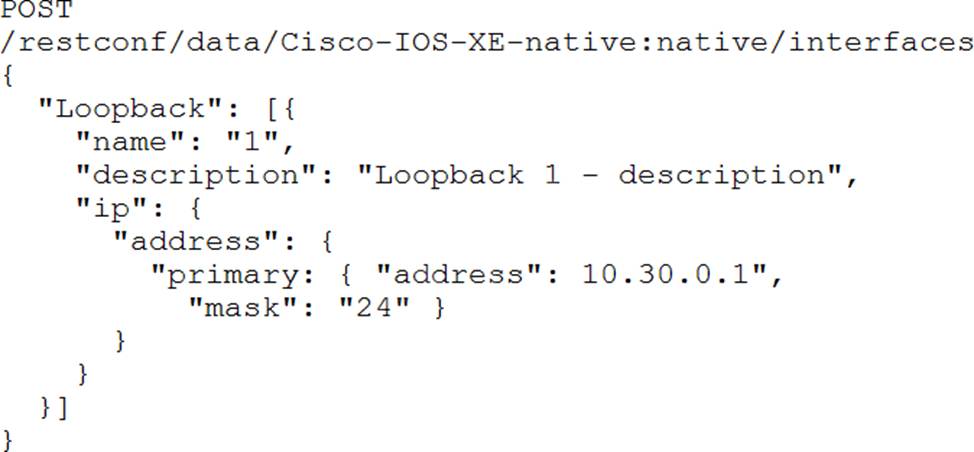
C)
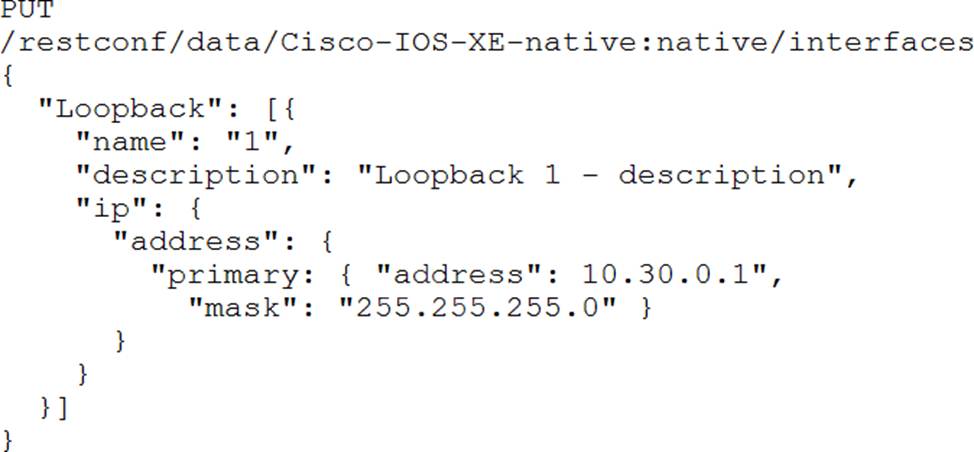
D)
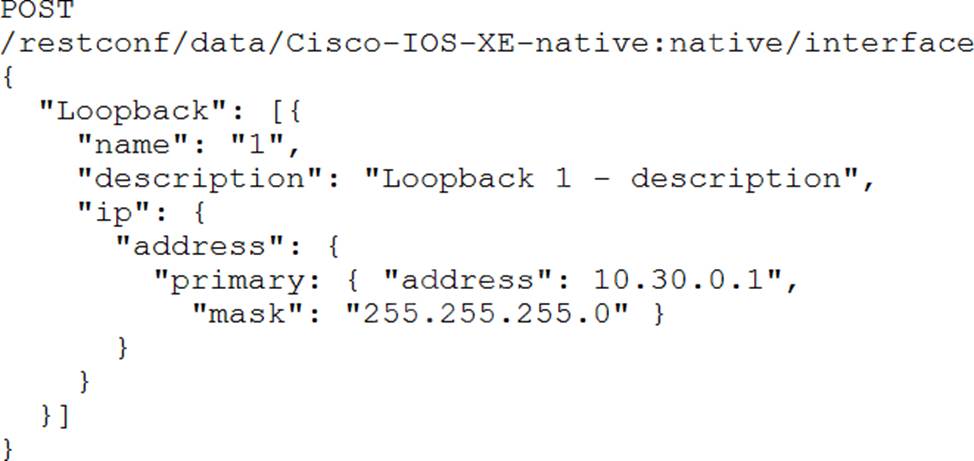
- A . Option A
- B . Option B
- C . Option C
- D . Option D
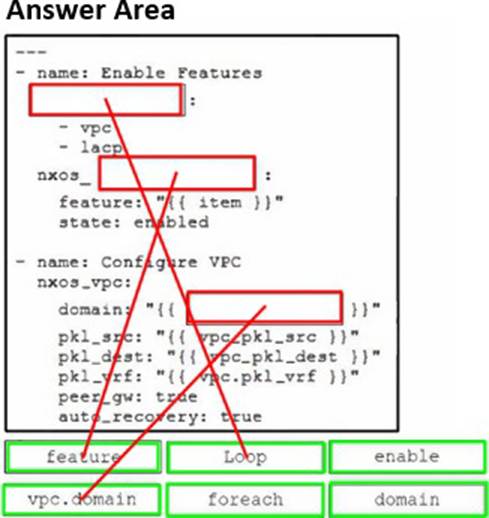
DRAG DROP
Refer to the exhibit.
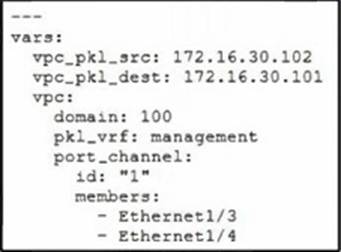
Drag and drop the code snippets from the bottom onto the blanks in the code to complete the playbook for creation of an Ansible role that configures VPC on a Cisco Nexus switch. Not all options are used.
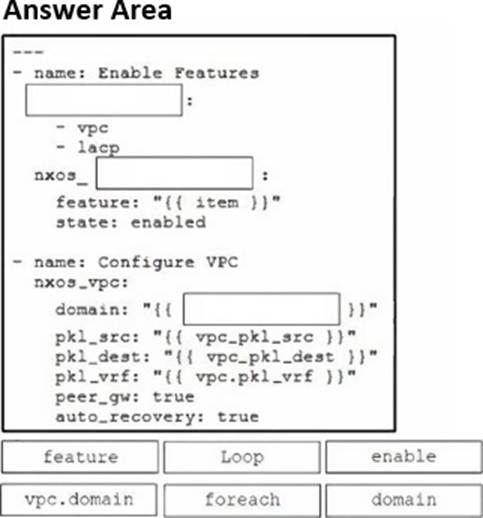
Refer to the exhibit.
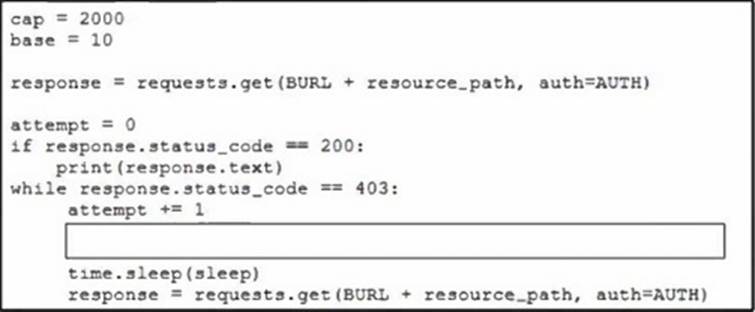
The Python code is used to retrieve data from a web API.
Which code snippet must be placed onto the blank in the code to add exponential backoff with jitter?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A local Docker container with a Container ID of 391441516e7a is running a Python application.
Which command is used to connect to a bash shell in the running container?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
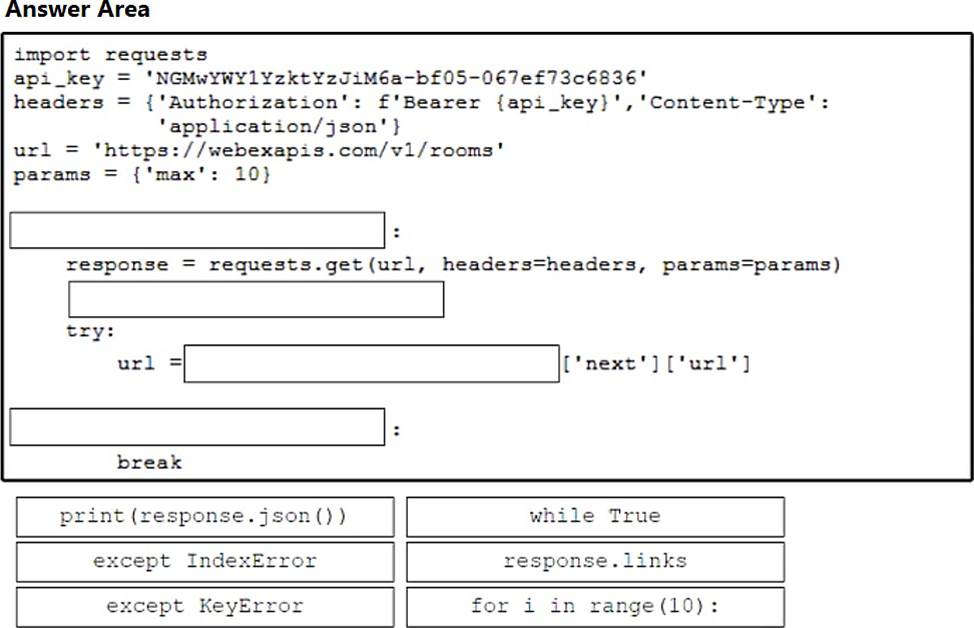
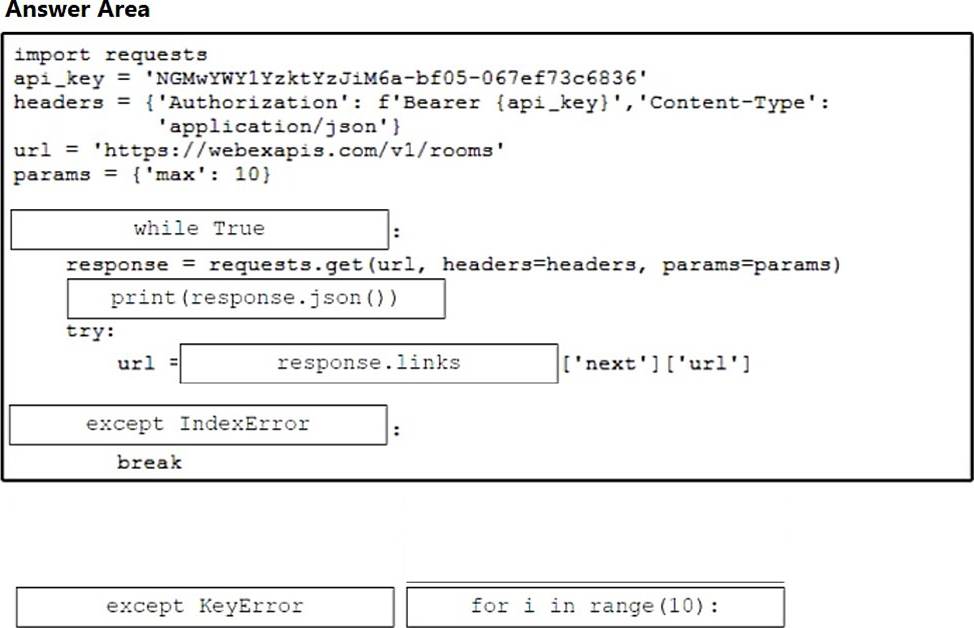
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of all the Cisco Webex rooms using pagination and the Webex API. Not all options are used.
What is the purpose of the OAuth2 three-legged authorization code grant flow?
- A . Obtain a refresh token for extending the validity of the access token.
- B . Secure authorization between a user, a client application, and a resource server.
- C . Encrypt API communication between the client and server by using HTTPS.
- D . Allow the usage of multifactor authentication during token acquisition.
