Practice Free 350-901 Exam Online Questions
What is a benefit of using continuous testing and static code analysis in a CI pipeline?
- A . They detect source code vulnerabilities as part of the standard build process.
- B . They automate code authoring based on user stories.
- C . They monitor the production environment and send alerts when errors are detected.
- D . They ensure that the product backlog is delivered to the release schedule.
What is an effective strategy for application logging?
- A . Use an FTP server for collection.
- B . Use a single vendor across the network.
- C . Use SNMP for messages.
- D . Use the appropriate logging level.
How should a web application be designed to work on a platform where up to 1000 requests per second can be served?
- A . Use algorithms like random early detection to deny excessive requests.
- B . Set a per-user limit (for example, 5 requests/minute/user) and deny the requests from the users who have reached the limit.
- C . Only 1000 user connections are allowed; further connections are denied so that all connected users can be served.
- D . All requests are saved and processed one by one so that all users can be served eventually.
Refer to the exhibit.
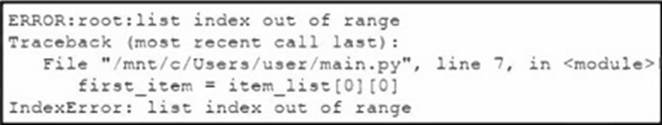
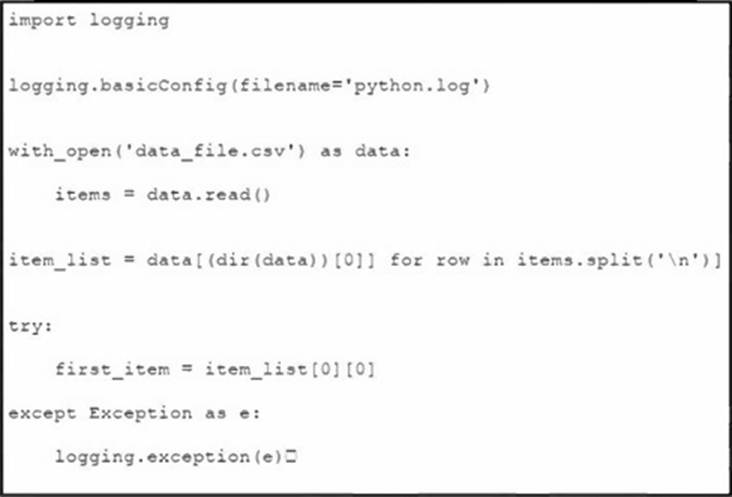
An engineer creates a script to enumerate a data list from a .csv file. The script fails and the engineer finds an error in the application log.
What is the cause of this error?
- A . The item_list statement in the script needs to be removed.
- B . The item_list statement in the script has incorrect syntax.
- C . The item_list statement in the script needs to split the data into rows.
- D . The item_list statement in the script needs to define the data range.
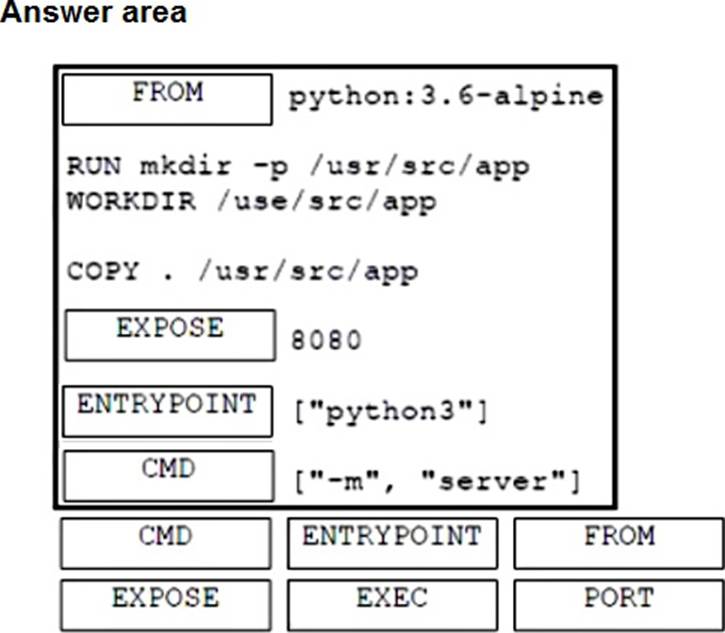
DRAG DROP
A developer must containerize a Python application to integrate into a prebuilt CD environment by creating a Docker image. It will be hosted as a web application to enable end users from accessing it remotely.
Drag and drop the code from the bottom onto the box where the code is missing in the Docker file. Not all options are used.
A developer has built a Docker image named ‘devcor12a3b456789′ using the Dockerfile named ‘devcor98b7a654321’ and now needs to containerize it.
Which command must the developer use?
- A . docker run –name devcor12a3b456789 -i -t devcorapp
- B . docker run –name devcorapp -i -t devcor12a3b456789
- C . docker build –name devcor12a3b456789 -i devcorapp
- D . docker build –name devcorapp -i devcor12a3b456789
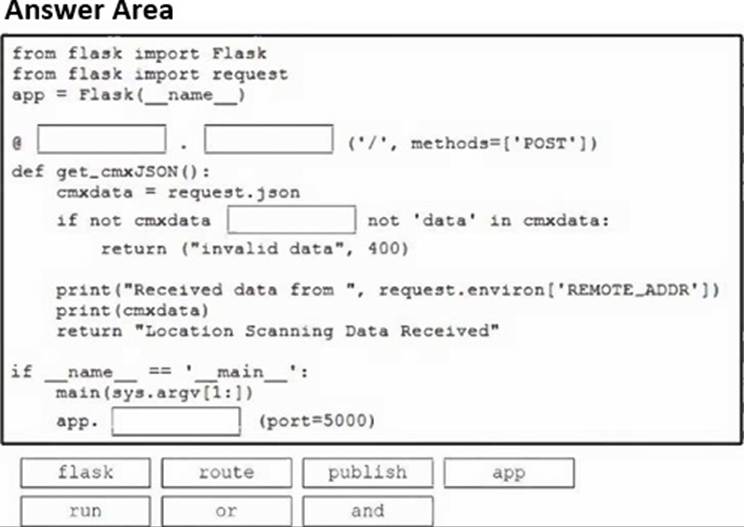
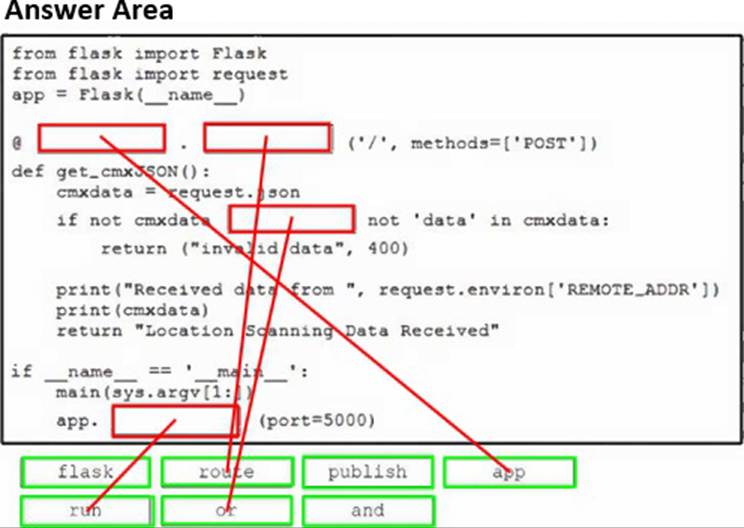
DRAG DROP
A developer is creating a Python Flask solution to leverage the Cisco Meraki Location API.
Drag and drop the code snippets from the bottom onto the blanks in the Python script to manage incoming location data. Not all options are used.
DRAG DROP
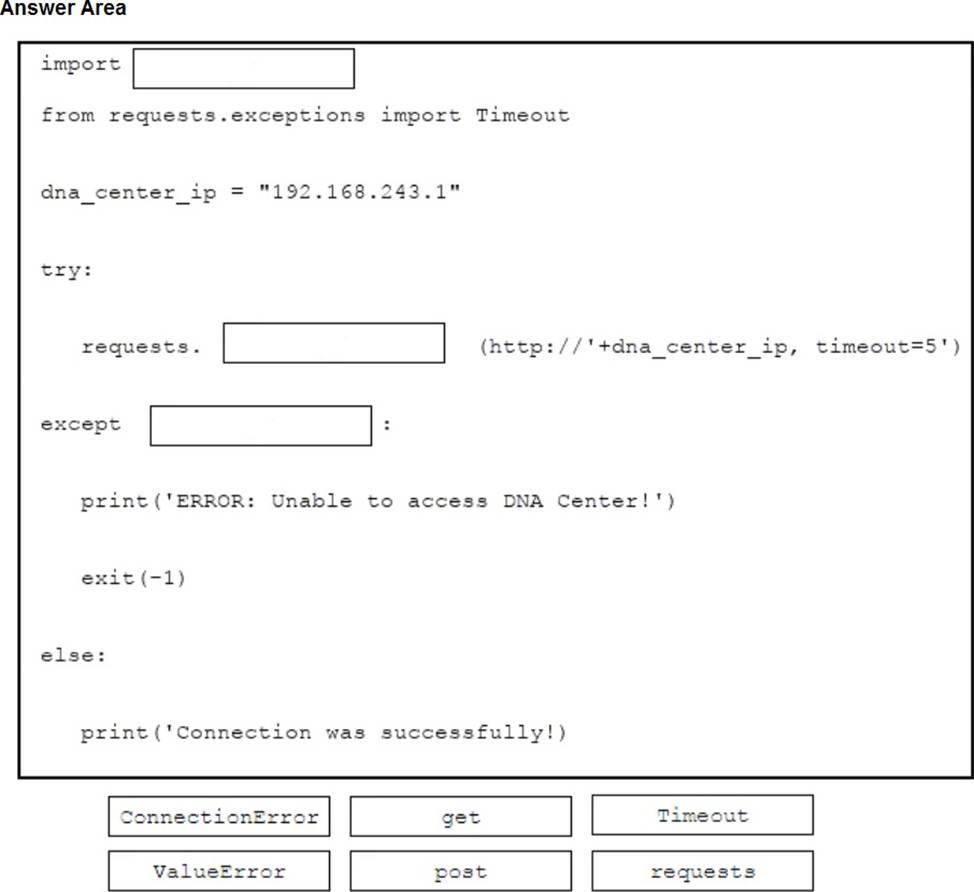
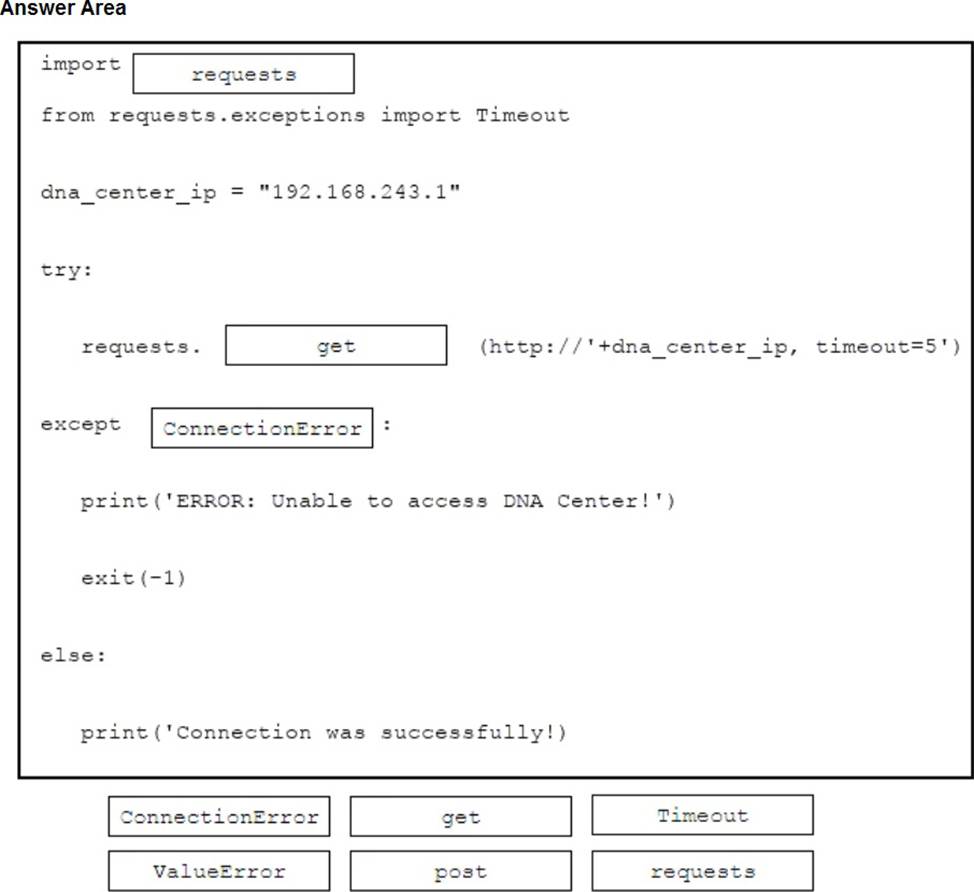
Drag and drop the code snippets from the bottom onto the blanks in the code for a Python application that needs to connect to Cisco DNA Center and then query the application for the inventory of devices on the network. The application must be resilient and ensure that it has the proper timeouts defined in the code. If a connection cannot be established to Cisco DNA Center within 5 seconds, the application should be terminated. Not all options are used.
A developer deploys a web application in a local data center that is now experiencing high traffic load from users accessing data through REST API calls.
Which approach enhances the responsiveness and performance of the API?
- A . Ensure that all read requests are clearly identified by the PUT method.
- B . Configure API payload to return errors in HTTP 200 responses.
- C . Use HTTP POST or other non-read methods for read requests when possible.
- D . Use HTTP standard authorization header to submit authentication credentials.
Refer to the exhibits.
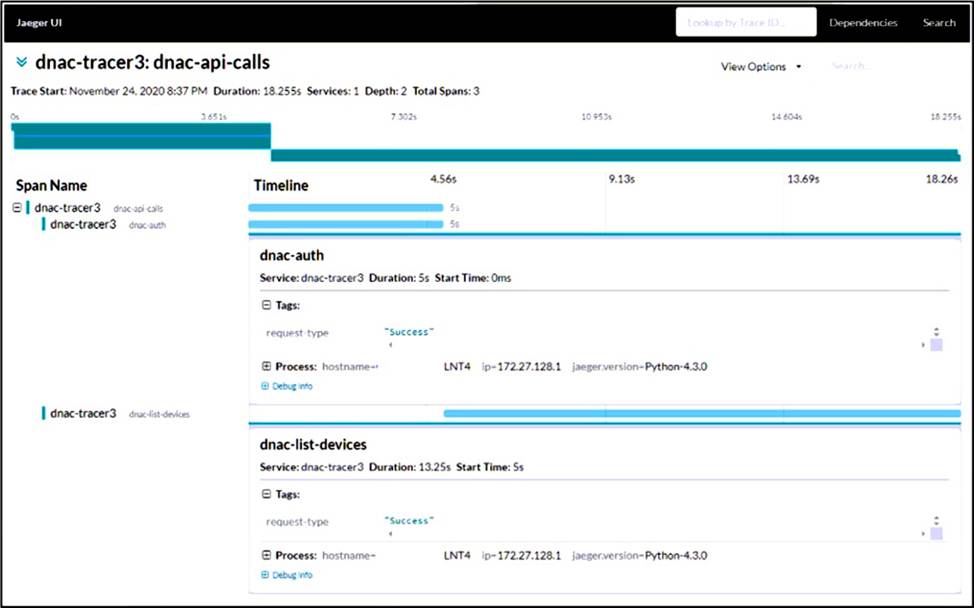
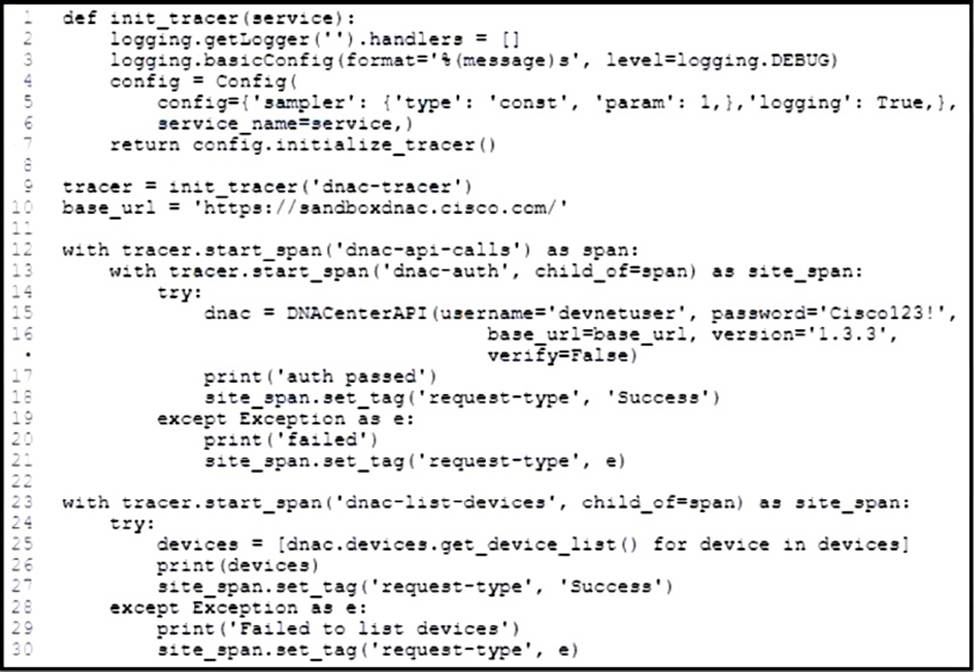
An application is developed to perform multiple API calls. The calls will be performed on the infrastructure devices. Delays in the information transfer occur when the application is executed.
What are two reasons for the issue? (Choose two.)
- A . The list devices API call is failing and does not return a result.
- B . The requests are being rate limited to prevent multiple calls causing the excessive load.
- C . One of the API calls takes roughly three times as long to complete.
- D . Listing devices takes longer than usual due to high network latency.
- E . The list devices API call is inefficient and should be refactored.
