Practice Free 350-901 Exam Online Questions
How do end-to-end encryption principles apply to APIs?
- A . The owners of the service are prevented from accessing data that is being transferred.
- B . Sensitive information is protected against backdoor attacks.
- C . The API data is protected against man-in-the-middle attacks.
- D . Both endpoints that are using the API resources are hardened against hacking.
Refer to the exhibit.
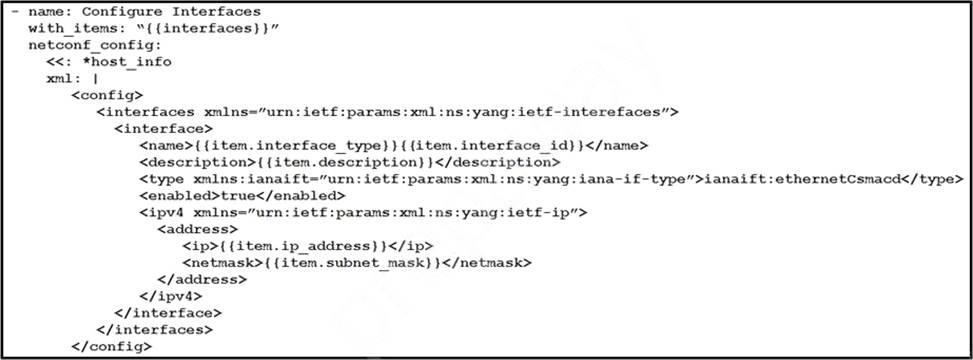
As part of the Ansible playbook workflow, several new interfaces are being configured using the netconf_config module. The task references the interface variables that are unique per device.
In which directory is the YAML file with these variables found?
- A . host_vars directory
- B . home directory
- C . group_vars directory
- D . current working directory
Which two design considerations should be considered when building a Cisco Meraki dashboard out of available APIs? (Choose two.)
- A . If the API key is shared, it cannot be regenerated.
- B . The API requests require the key and the user credentials.
- C . API call volume is rate-limited to five calls per second per organization.
- D . The API version does not need to be specified in the URL.
- E . Access to the API must first be enabled by using the settings for an organization.
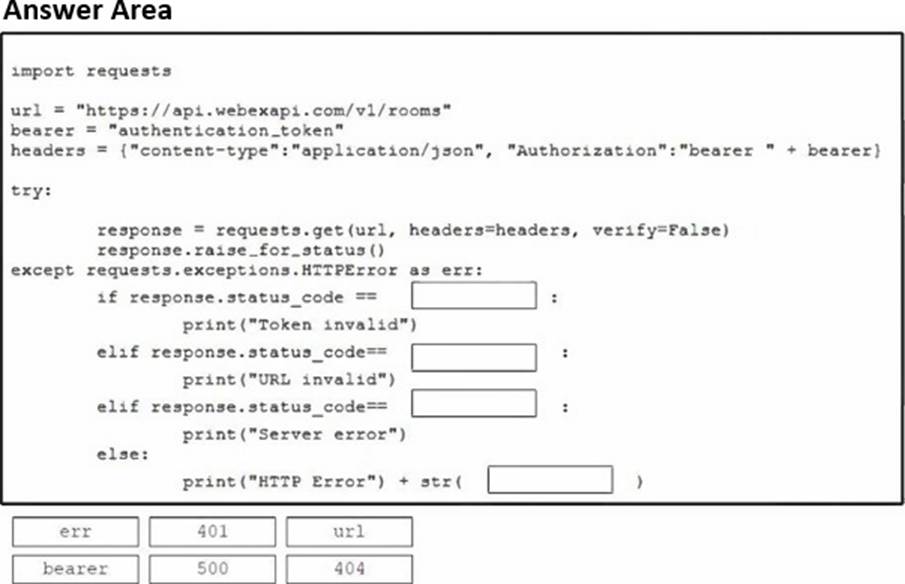
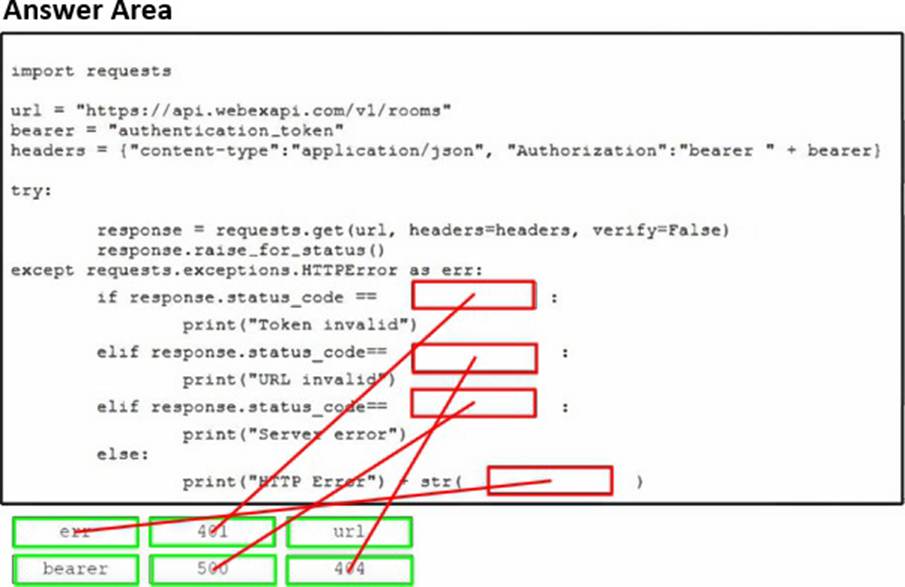
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the Python script to list all the joined spaces by using the Cisco Webex API. Not all options are used.
Which two strategies are used to protect personally identifiable information? (Choose two.)
- A . Encrypt data in transit.
- B . Encrypt hash values of data.
- C . Encrypt data at rest.
- D . Only hash usernames and passwords for efficient lookup.
- E . Only encrypt usernames and passwords for efficient lookup.
Refer to the exhibit.
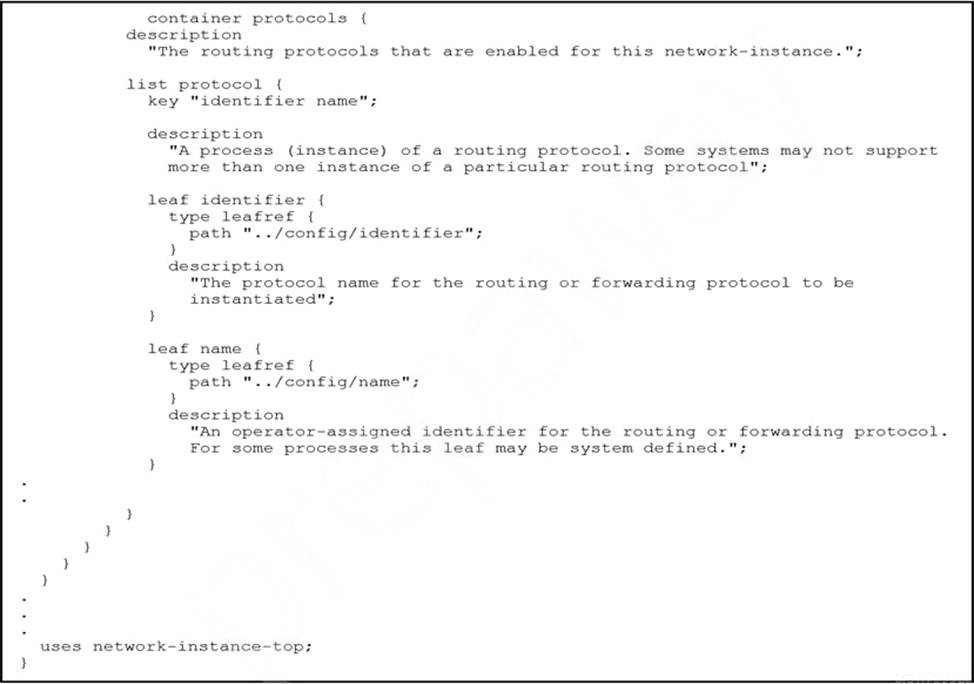
Which URI string retrieves configured static routes in a VRF named CUSTOMER from a RESTCONF-enabled device?
A)
![]()
B)
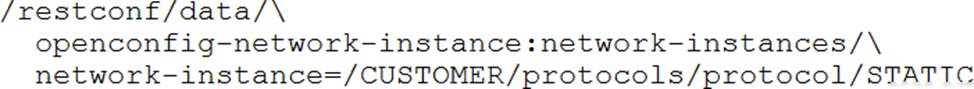
C)
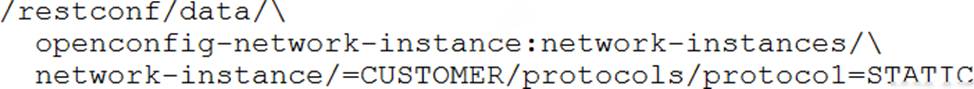
D)
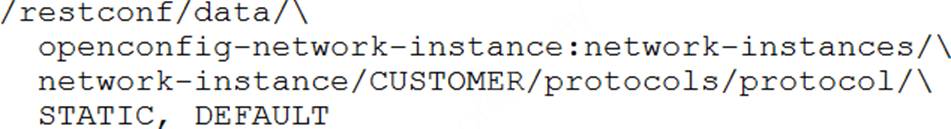
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Which telemetry transport option allows the desired configuration of metrics to be centrally maintained on the collector?
- A . poll
- B . pull
- C . dial-out
- D . dial-in
Which command is used to enable application hosting on a Cisco IOS XE device?
- A . iox
- B . application-hosting
- C . iox-service
- D . app-hosting
Refer to the exhibit.
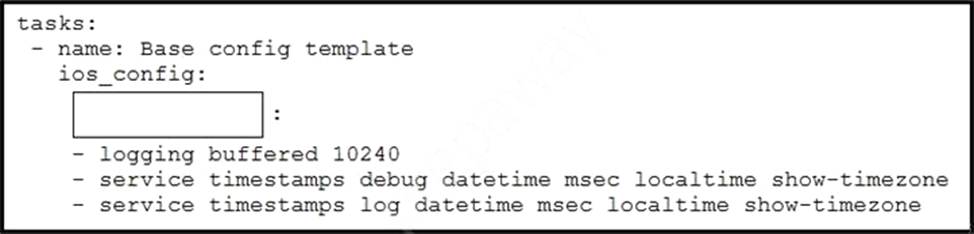
Which word is missing from this Ansible playbook shown, to allow the Cisco IOS XE commands for router configuration to be pushed after the playbook is executed?
- A . input
- B . lines
- C . commands
- D . config
DRAG DROP
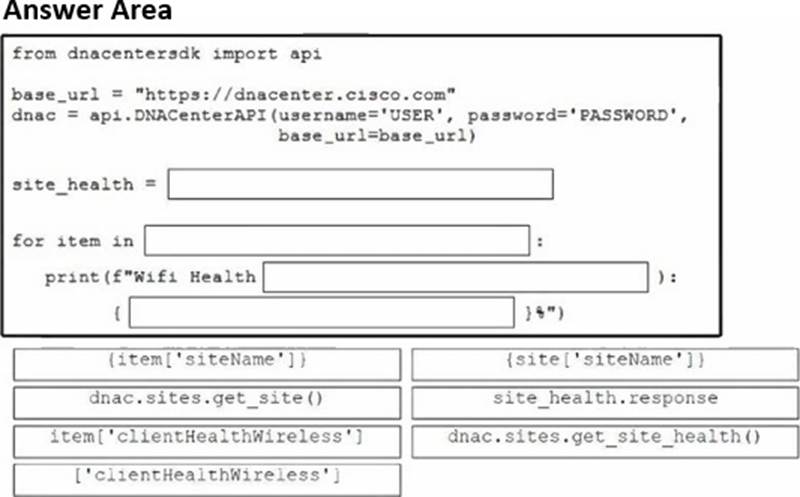
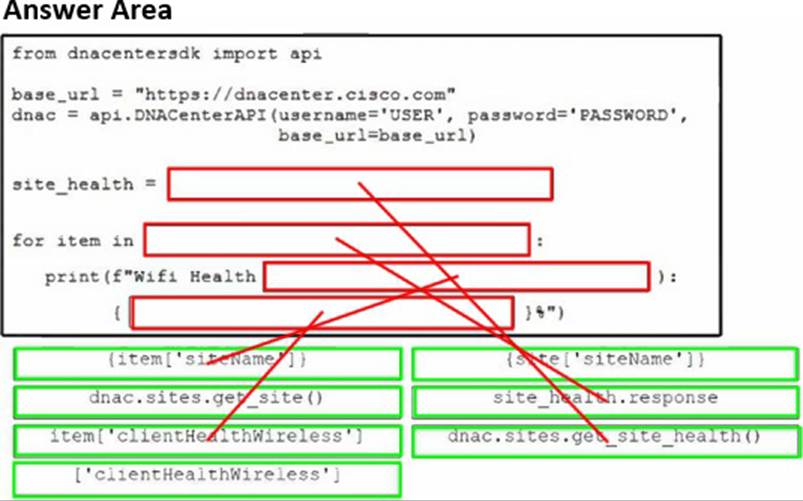
Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve and display wireless health information from the Cisco Catalyst Center (formerly DNA Center) API. Not all options are used.